| ❗ Warning |
|---|
| It is important that you know what you're doing, this guide is here to help you but it may contain some error. We are not responsible for any damage caused by following this tutorial. |
Just a little script to automate the logging process as well as the validation of the attendance record, because I keep forgetting to confirm my attendance although I'm in class.
This tutorial is the result of the program Project for Industry & Innovation for master II student by ESILV and in collaboration with Risk&Co. It was written by Eliott AILLERIE, Alexis BOURDIN, Thomas NGO and Lucas WITVOET. The project team was under the supervision of Juliette DESORMONTS, Cybersecurity consultant at Risk&co and Walter PERETTI, Head of the IT, IOT & Security Department at ESILV.
For this article, we'll use Ubuntu 20.04 and KVM to virtualize our Windows 7 machine (analysis machine).
Here is the link to the Capev2 Github and the official documentation.
- First start by updating your repository.
$ sudo apt update- Then install python3 and pip for python3 if it's not already done.
$ sudo apt install python3
$ sudo apt install python3-pip- Install Pillow for python with the latest, this version can change . Take a look at Pillow changelog's to see what's the latest version.
$ python3 -m pip install Pillow==9.0.0Once CAPEv2 is installed, we need virtual machine to run the different malware.This machine is also called the Guest Machine. You can also use Virtualbox but it's recommended to use KVM as it's less unlikely to be detected as a VM by the malware. Quoting CAPE lead developer :
We strongly NOT recommend to use VirtualBox due to be super easy to detect by malware, use KVM as suggested in readme for amazing performance and anti-*
Like the cape2.sh we'll use doomedraven script and add the permission before executing it.
$ wget https://raw.githubusercontent.com/doomedraven/Tools/master/Virtualization/kvm-qemu.shWhen executing the scrip DO NOT FORGET to REPLACE USERNAME by your own USERNAME.
$ sudo ./kvm-qemu.sh all <username> | tee kvm-qemu.logThis installation will take some time, when finished reboot your computer.
$ sudo shutdown -r nowWe will use the script cape.sh to install it with all the optimization.
$ wget https://raw.githubusercontent.com/doomedraven/Tools/master/Sandbox/cape2.shWe have to change the permission in order for the script to be executable :
$ sudo chmod a+x cape2.shWe can then execute the script and add tee command to get a log file of the installation. This installation will take a certain time.
$ sudo ./cape2.sh base cape | tee cape2-installation.logThen we modify the to allow MITRE ATT&CK technics and strategy to be prompt.
$ sudo chown -R cape:cape /opt/CAPEv2/data/To finalise the installation of volatility, you will have to check if the windows symbols folder is present in volatility and if so, download it.
$ ls cd /usr/local/lib/python3.8/dist-packages/volatility3/symbolsOtherwise, if it's not present :
$ sudo wget https://downloads.volatilityfoundation.org/volatility3/symbols/windows.zip -O /usr/local/lib/python3.8/dist-packages/volatility3/symbols/windows.zip
$ cd /usr/local/lib/python3.8/dist-packages/volatility3/symbols/
$ sudo unzip windows.zip
$ sudo rm windows.zipThen we modify the rights on the downloaded files :
$ sudo chmod 777 windows/*Once the installation finished reboot your machine :
$ sudo shutdown -r nowAs mentioned in the official documentation : For analysis purposes you are recommended Windows 7 with User Access Control disable even if CAPE supports Windows 10 too.
First run virt-manager and create a new virtual machine chosing your Windows 7 iso file. You can follow this tutorial to install a VM using KVM.
$ sudo virt-manager-
Install Python 3.6 in the Windows 7 VM. Don't forget to include Python in PATH. Don't install a newer version of Python.
-
Install Pillow latest version, the same as on your host computer with the command :
pip3 install Pillow==9.0.0We might want to install additional software such as browsers, PDF readers, office suites, etc for fully functional features. Remember to disable the “auto-update” or “check for updates” feature of any additional software.
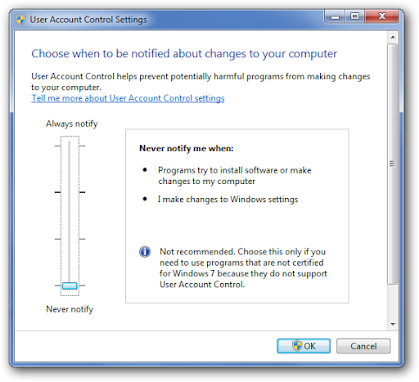
- Disable UAC : Head into Control Panel and type UAC into the search box, or do it from the start menu. Then drag the slider down to the bottom.
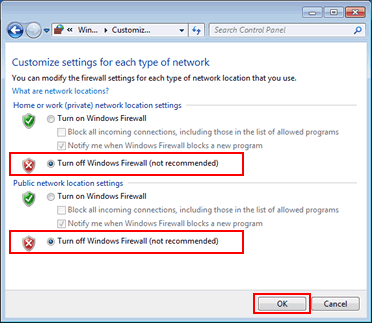
- Disable Firewall
- Disable Windows AutoUpdate
It's recommended to set the VM to host-only network but we didn't experimented this. You can find some leads here.
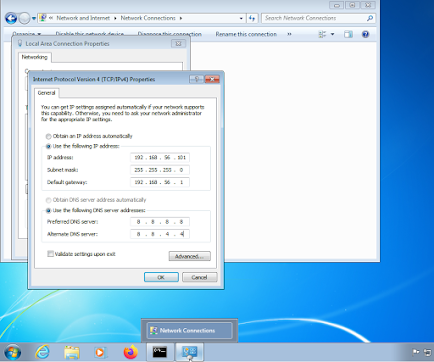
Configure the network with your own IP address and gateway, here for example we have:
- IP address:192.168.56.101
- Subnet mask:255.255.255.0
- Default gateway:192.168.56.1
- Preferred DNS server:8.8.8.8
- Alternate DNS server:8.8.4.4
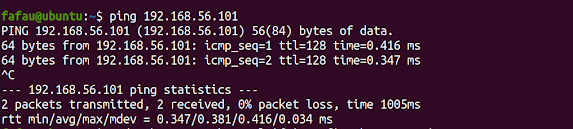
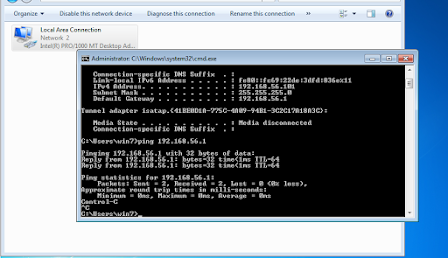
Make sure both the guest (Win7) and host (Ubuntu) can be ping each other :
Open a command prompt as Administrator, and run :
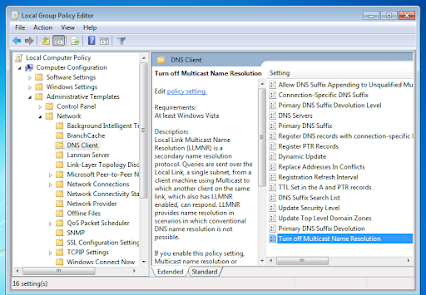
netsh interface teredo set state disabledOpen the Group Policy editor. Then navigate to Computer Configuration > Administrative Templates > Network > DNS Client, and open Turn off Multicast Name Resolution.
Set the policy to enabled :
Open the Group Policy. Then navigate to Computer Configuration > Administrative Templates > System > Internet Communication Management, and open Restrict Internet Communication.
Set the policy to enabled :
![Enable Restrict Internet Communication]./images/network_connectivity_disabling.png "Enable Restrict Internet Communication")
Download the agent here. Copy the file into the Win7 VM.
Running (double click) the agent.py will launch the HTTP server which will be listening for connections.
If you want the script to be launched at Windows’ boot, just place the file in the Startup folder. The All Users startup folder should be C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup.
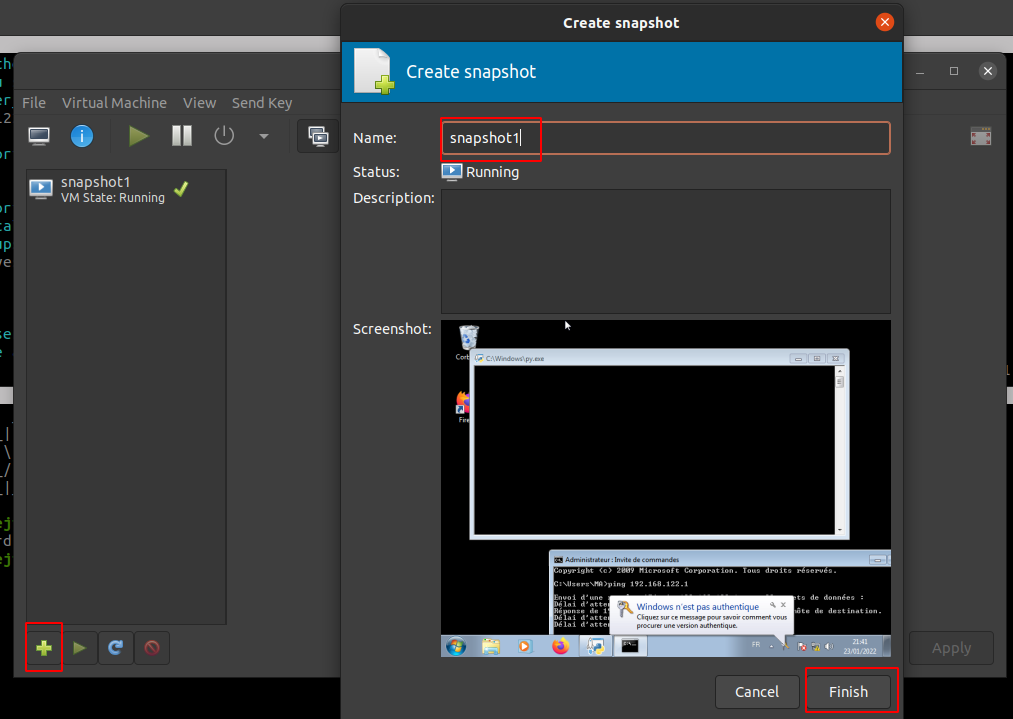
After start agent.py and minimize it, create a snapshot with the name "Snapshot1".
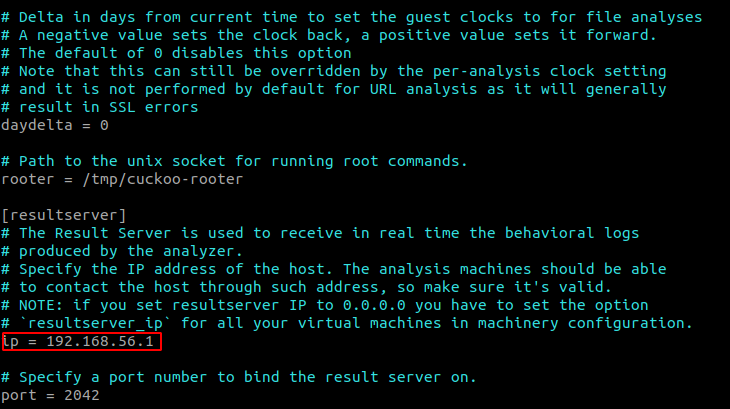
Don't forget to read the configurations documentation to understand the configurations as yours might be different with my configuration. Important files to be configured in /opt/CAPEv2/conf:
- cuckoo.conf
- Change the IP address
-
auxiliary.conf
- Configure with your own requirement
-
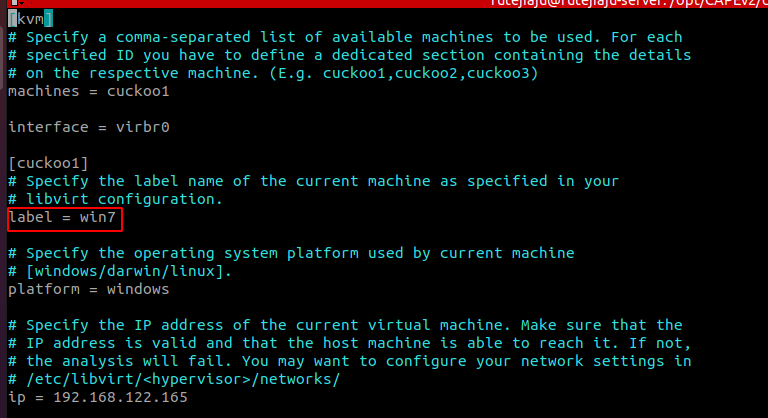
kvm.conf
- Change label, ip, snapshot name
-
memory.conf
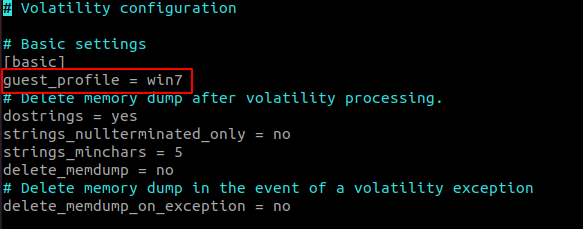
- Change the guest_profile to your VM name , here win7
-
reporting.conf
- Configure with your own requirement
-
web.conf
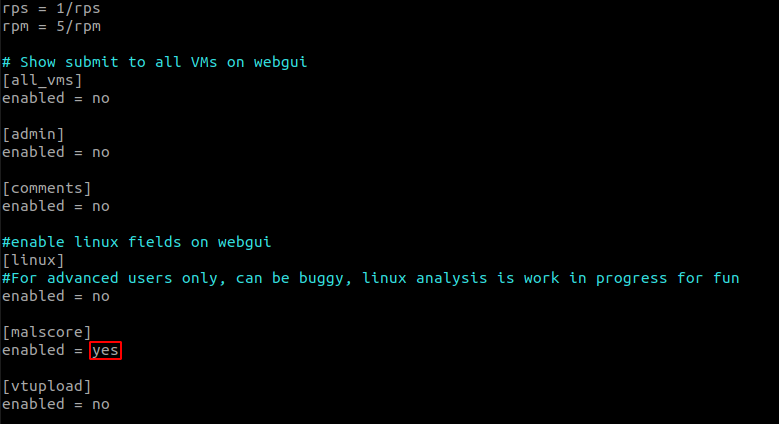
- If you'd like you can enable scoring :
First you have to make last installations in order to allow the replay of HTTP and HTTPS requests :
$ cd /opt/CAPEv2/utils
$ sudo python3 community.py -cr
$ sudo pip3 install -U git+https://github.com/CAPESandbox/httpreplayThen we just have to run cuckoo :
$ cd /opt/CAPEv2/
$ sudo python3 cuckoo.pyFor web, in a new tab, run these command :
$ cd /opt/CAPEv2/web
$ sudo python3 manage.py migrate
$ sudo python3 manage.py runserver 0.0.0.0:8090If you want CAPE to process the information you should run :
sudo python3 process.py -p7 autoIf get an error on this command, try to lower the number of parallels threads used with the flag -pX and X equal to the number of threads used.
You can choose the way you want to install OpenCTI on the official wiki.
It is recommended to use Docker, you can follow the official OpenCTI docker installation instructions.
MISP developed a Docker container, you can deploy it following the Github installation instructions.
If you wish to install MISP on your machine, you can follow the official installation instructions of MISP.
We will use the CAPE connector developed by OpenCTI team. Add the code of the Connector docker-compose.yml content to your OpenCTI docker-compose .
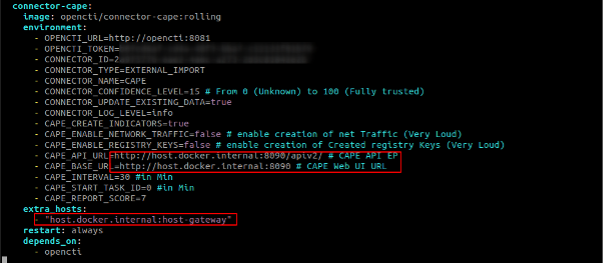
❗Warning :
You will probably encounter network problem saying API is not reachable. Indeed your CAPE instance is running on your machine and your OpenCTI instance on docker. This docker has his own internal network. In order to bypass those network problem, you should add host.gateway parameter to your docker-compose file. You can change the host.docker.internal to whatever you'd like.
The functionality to transfer data to MISP is already built into CAPE. There is a MISP section in the reporting.conf file that allows you to enter the parameters of the MISP instance to be connected.

Like CAPE, we will use MISP official connector developed by OpenCTI.
As mentioned in the github connector README :
Enabling this connector could be done by launching the Python process directly after providing the correct configuration in the config.yml file or within a Docker with the image opencti/connector-misp:latest. We provide an example of docker-compose.yml file that could be used independently or integrated to the global docker-compose.yml file of OpenCTI.
You could encounter the same network problem as for Cape Connexion. Be sure your docker container are on the same network if your use MISP with docker. Otherwise if you had manually deployed MISP add the host.gateway argument in your docker-compose.yml.
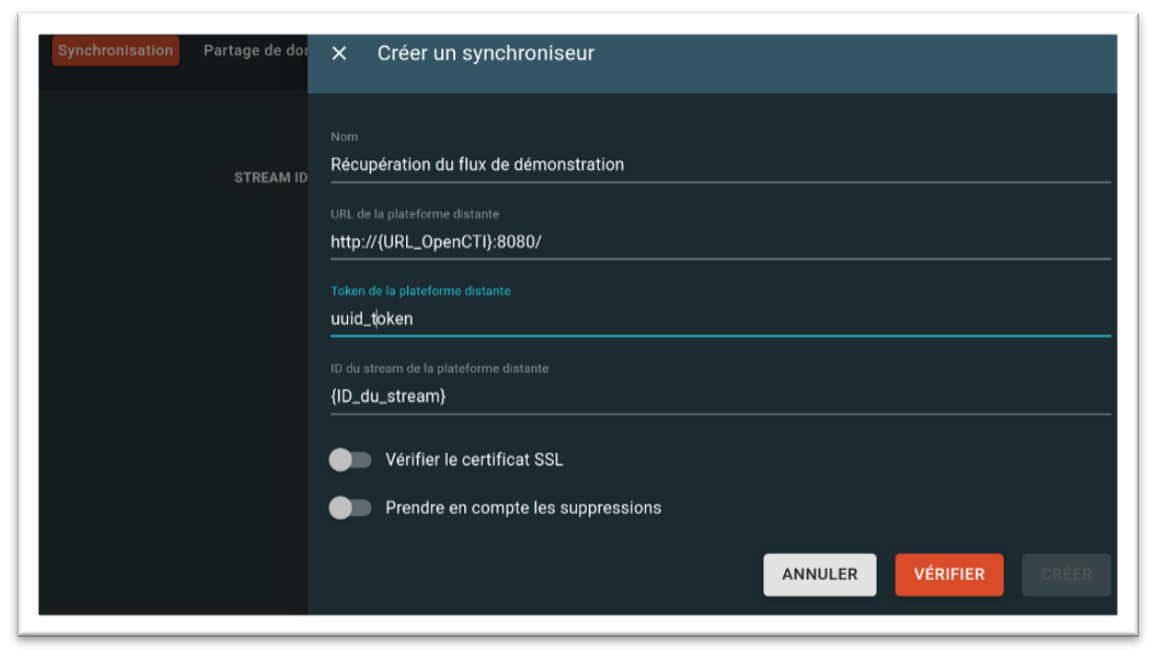
It is possible to retrieve this stream by creating a synchroniser. All you need is the URL of the OpenCTI instance, an authentication token and the ID of the stream you want to retrieve.
Once the stream has been created, all that remains is to start or stop it.
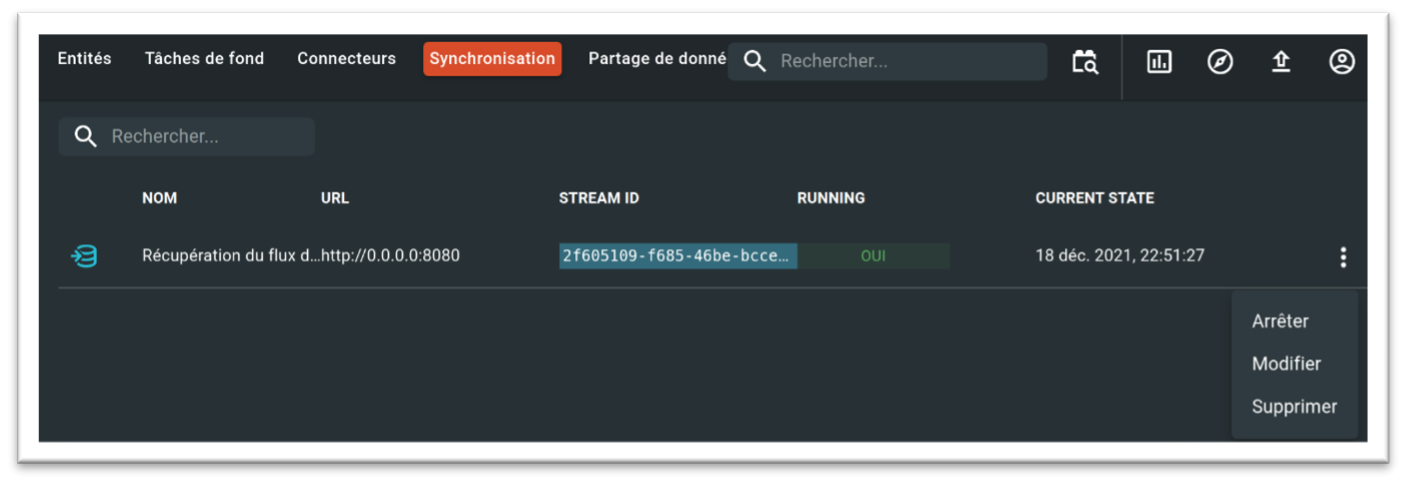
There are others methods, please refer to this article on data sharing with OpenCTI.
- CAPE v2 installation by NetBySec
- CAPE v2 official documentation
- CAPE installation tutorial by CTechmat
- OpenCTI wiki
- OpenCTI data sharing article by Luatix