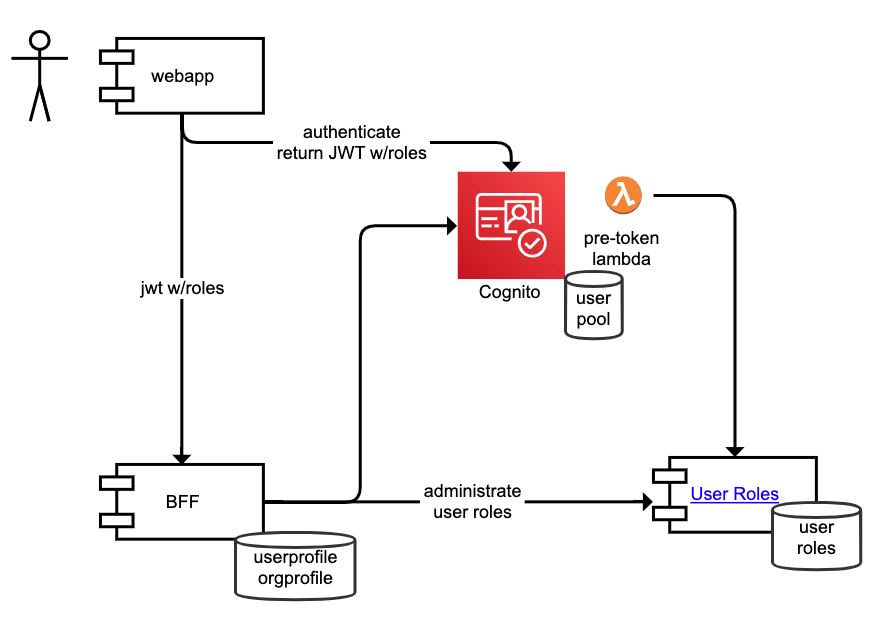
A generic service featuring RBAC (Role Based Access Control).
Can be used in conjunction with e.g. AWS Cognito and a pretoken generation trigger lambda to add custom claims to an identity token.
Note that this repo only contains the User Roles service
| Endpoint | What |
|---|---|
| PUT /userroles/{userId} | create or update user roles for user |
| GET /userroles/{userId} | get user roles for user |
| DELETE /userroles/{userId} |
NB! Currently no support for post, but can be implemented later.
{
"userId": "userId123",
"userroles": [
{
"applicationName": "application1",
"orgId": "orgId1",
"roleName": "orgOwner"
},
{
"applicationName": "application2",
"orgId": "orgId2",
"roleName": "orgAdmin"
},
{
"applicationName": "application2",
"orgId": "orgId3",
"roleName": "orgMember",
"roleValue": "{"boards": [1,2,3]}"
},
{
"roleName": "admin"
}
]
}
| Endpoint | What |
|---|---|
| GET /userroles | List all users |
| GET /userroles?orgId={orgId1} | List users with access to a given organization |
| GET /userroles?roleName=admin | List users with a given role |
| GET /userroles?roleName={roleName}&orgId={orgId2} | List users with a given role |
-
Start the database
docker-compose up -d
-
Build and run the application
All of these will skip tests to be quick.
-
Option 1: In IDE
Run the
Mainfile. -
Option 2: Via Maven
./build-and-run.sh
-
Option 3: Package and run with the actual Docker image
# See the script for details. ./build-and-run-docker.sh
-
-
Access the service at http://localhost:8080/health
To only check linting (no tests etc):
mvn spotless:checkTo format (does not fail on lint errors):
mvn spotless:apply