- Application platforms like Pivotal Cloud Foundry provide excellent, automated Operating System and Middleware CVE patching. But, your application dependency trees are a significant security vulnerability risk.
- Snyk provides developer and operator friendly tools for identifying application security vulnerabilities.
- For Node.js, Snyk can automatically apply security patches during development(snyk wizard) or during deployment(cf push).
- For IT Operators, Snyk can go one step further and fail the deployment(cf push) of vulnerable applications. This feature supports Java and Node.
- All build and deploy commands live in
pwsBuildDeploy.sh. This is a polyglot demo that builds spring-boot 1.x-2.x, node, react and struts 1.x based projects - You will need to have node and maven installed to build the demo projects
- The
manifest.ymlfile can be used to do a normalcf pushof all built demo projects. This demo will work on any PCF environment that has the node, staticfile and java buildpack. - You may need to edit environment variable entries in
manifest.yml. This demo does not use SCS or any other service registry. All microservice endpoints are wired up via env entries in the manifest. - You may need to edit environment variable entries in
./web-gui/src/config.json. The web gui has web links to your snyk dashboard and cloud foundry apps manager. The default setting for snyk dashboard is:https://app.snyk.io/org/pivotal-demo/. The default setting for apps manager is:https://console.run.pivotal.io/
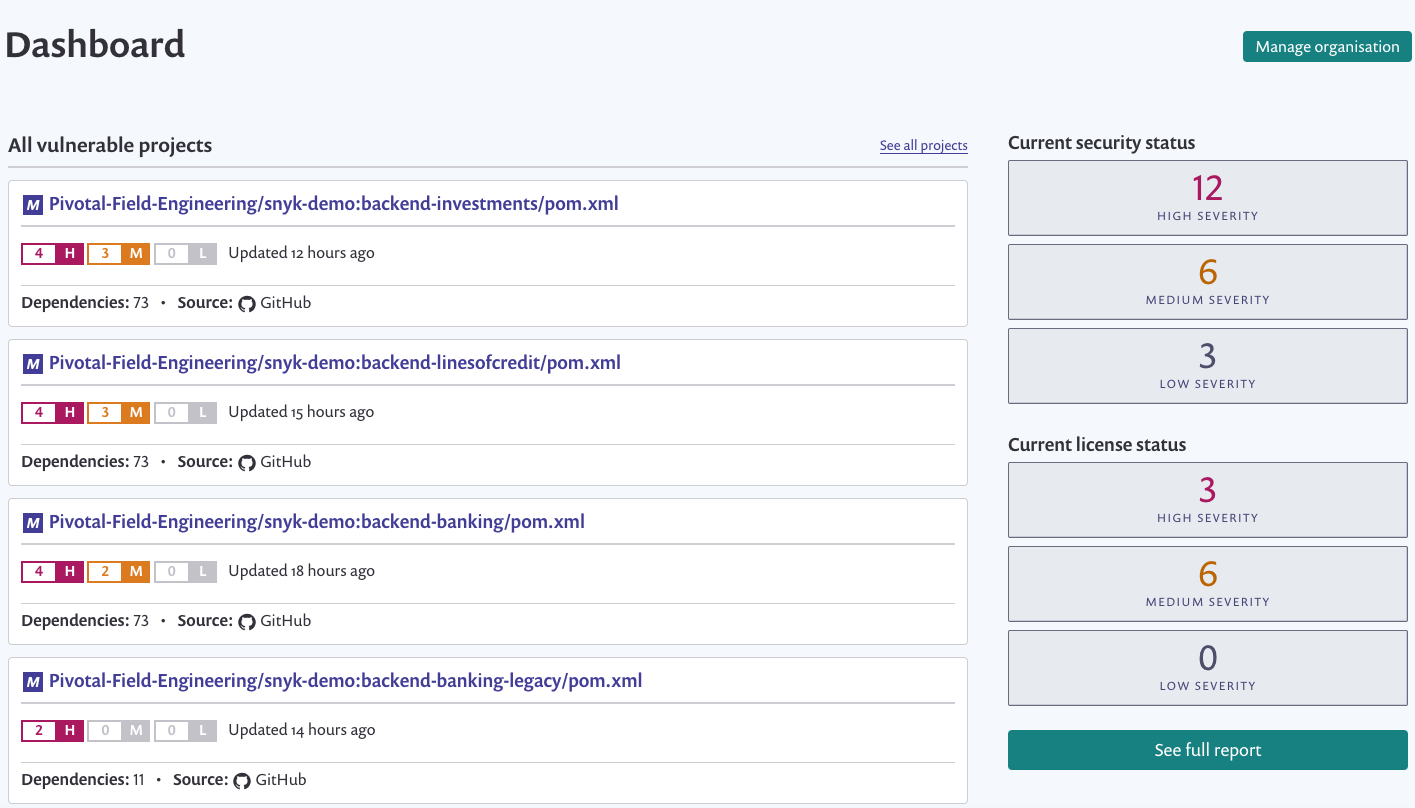
- Setup Github integration and make sure that all 6 projects are listed in your Dashboard.
- [OPTIONAL] Repeat previous step for PWS or Cloud Foundry integration. This will allow you to show vulnerabilities of deployed apps, independent of SCM scanning. Very useful for platform operators.
- Before running the demo script, build and deploy all projects using
./pwsBuildDeploy.shor similar commands. - Open web-gui URL and verify that clicking on the snyk image takes you to the correct snyk dashboard.
- In web-gui URL make sure that the pivotal cloud foundry image takes you to the correct apps manager console
- Install the snyk cli
- Verify the snyk cli works by running
snyk test backend-banking-legacy. You should see some interesting vulnerabilities.
- Open the web-gui and Sign-On using any User ID. No password is needed. If the user id starts with '1' the super special struts 1.x microservice will be invoked. Otherwise, it's a spring-boot 1.x endopoint.
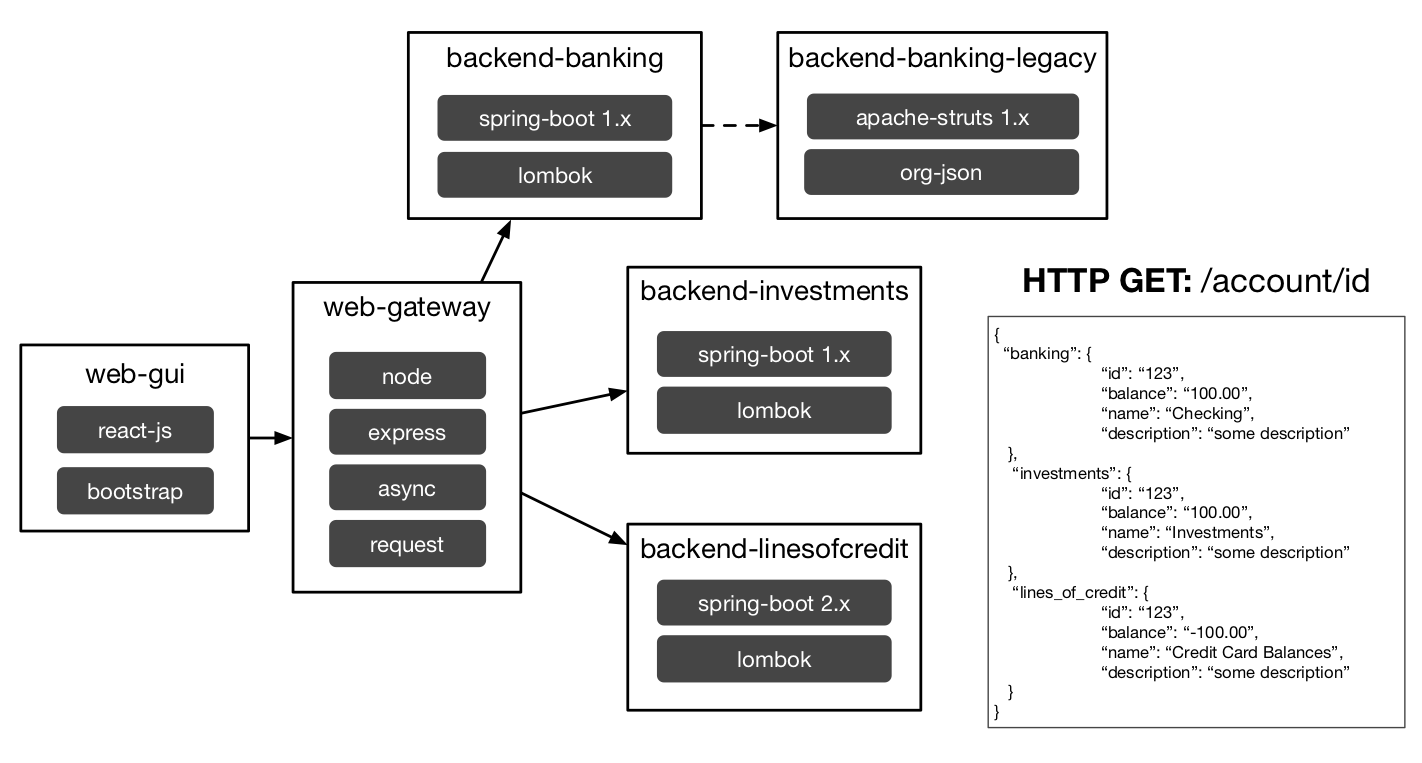
- Briefly explain that each account summary box is a JSON response from a different microservice. The account summary descriptions will tell you which apps are spring boot 1.x, 2.x or struts 1.x. There is a node web gateway that makes 3 async HTTP GET calls and combines the results for the web gui.
- Click any
Detailsbutton. This will log you out, essentially resetting the GUI. - Click on the
Architecturebutton. Explain the web-gui -> bff -> microservice based architecture. Key frameworks in use for each service are listed in the diagram. Re-emphasize the different vulnerability challenges with modern apps because of deep npm and maven dependency trees. These issues exist even when the app is super simple. - Click on the Snyk image. It will open a new tab window and take you to the snyk dashboard. Explain the various vulnerabilities in the applications.
- Explain that Snyk can scan both source code repos(github) and deployed apps in cloud foundry spaces.
- If you have more time, go a little deeper into how Snyk can help you not only see but address vulnerabilities.
- Open a terminal window and
cd snyk-demo - Run
snyk test backend-banking-legacy. Explain that the CLI shows the same data as the dashboard. - Run
cd web-gatewaythensnyk wizard. Explain how Snyk can automitically remediate some issues with node based apps. - Run
snyk test. If there are still HIGH issues, runsnyk wizardandsnyk testagain. Explain how Snyk automatically remediated all HIGH issues. - Run
gulp test. Explain that the integration test still passes. REQUIRES LOCAL RUNNING:backend-banking,backend-investmentsandbackend-linesofcredit - Set
SNYK_TOKENenvironment variableSNYK_TOKEN=YOUR_API_TOKEN. To retrieve your token in Snyk Dashboard click on: Account Settings -> API token -> Show - Set your SNYK_TOKEN enviornment variable for the
backend-banking-legacyapp:cf set-env fnb-backend-banking-legacy SNYK_TOKEN $SNYK_TOKEN - Run
cf push -f ./manifest-special.yml. This will attempt to pushbackend-banking-legacyby using the Snyk java buildpack. This push should fail b/c of HIGH level vulnerabilities. - Explain how the CLI and snyk buildpacks can be used in CI pipelines to protect production.
- If
gulp testfails runnpm i -g gulp-cli - To reset your node_modules, delete
node_modulesfolder and runnpm install - It helps to git revert
package.jsonandpackage-lock.jsonin between demo runs. This will add back vulnerabilities that get fixed onsnyk wizard
mvn clean installfails, install/configure apache maven
npm startfails, install react-scripts
- backend-banking-legacy - OPTIONAL: Deploy backend-banking-legacy.war to tomcat. Runs on PORT:8080
- backend-banking - Run BankingApplication.java. Runs on PORT:8083. You will need to
export BACKEND_BANKING_LEGACY_URL=http://localhost:8080/backend-banking-legacyto access the legacy service. - backend-investments - Run InvestmentsApplication.java. Runs on PORT:8081
- backend-linesofcredit - Run LinesOfCreditApplication.java. Runs on PORT:8082
- web-gateway -
node app.js. Runs on PORT: 3001 - web-gui -
npm start. Runs on PORT: 3000