RhoAias(/ˈroʊ/ - /ˈaɪ.əs/) is a library for reverse proxy and intranet penetration, that can be deployed directly as a standalone application or embedded as a dependency library in your dotnet application.
English | 简体中文
- Support
HTTPreverse proxy, which can forward requests based on the location level. - The client can be started without configuration, and the configuration can be delivered from the server dashboard
- Support
TCP/UDPport forwarding, which can be SSH connected to the private network - Support
k8s-ingress. The client can be deployed as a k8s-ingress so that ingress traffic can be forwarded to the intranet k8s cluster. - Support ACME-based
HTTPScertificate and certificate renewal - Support
Metricsmonitoring, which can be connected to OpenTelemetry-based monitoring tools, such asPrometheus - Support data stream
compression(compression algorithm supports gzip, snappy, etc.) - Support
WAF(web application firewall), which can defend against script and bot attacks
RhoAias can be used in many scenarios, and the following is a set of use case diagrams to quickly understand the use cases of RhoAias.
Forward all HTTP requests from the public network to the intranet by the paths.
RhoAias can forward requests to different ENV servers by the paths.
RhoAias supports load balancing across clients.
NOTE: Load balancing for a single client doesn't make sense.
RhoAias client can be deployed as a k8s-ingress.
RhoAias can expose internal network ports to the public.
You need to prepare a machine with a public IP address and make sure that the machine has the Docker environment installed.
services:
rhoaias-server:
container_name: rhoaias-server
image: chaldea/rhoaias-server
restart: always
network_mode: host
environment:
RhoAias__Server__Bridge: 8024 # Client connection port
RhoAias__Server__Http: 80 # HTTP request forwarding port
RhoAias__Server__Https: 443 # HTTPS request forwarding port
volumes:
- rhoaias_server_data:/app/data # Data store directory
- rhoaias_server_certs:/app/certs # HTTPS cert store directory
volumes:
rhoaias_server_data:
rhoaias_server_certs:Due to port forwarding requires listening on any port, so you need to enable the host network mode like network_mode: host.
Save that configuration to docker-compose.yml,then exec
docker compose up -dDetermine that the ports on the docker container are reachable, If the port is unreachable, check your firewall configuration.
Server Environment Variables
| Variable Name | Default Value | Description |
|---|---|---|
| RhoAias__Server__Bridge | 8024 | The client connection port, and the Dashboard access port. |
| RhoAias__Server__Http | 80 | HTTP request port. |
| RhoAias__Server__Https | 443 | HTTPS request port. |
| RhoAias__Dashboard__UserName | admin | Dashboard default username. |
| RhoAias__Dashboard__Password | 123456Aa | Dashboard default password. |
| RhoAias__Dashboard__CreateDefaultUser | true | Whether to create a default user. |
| RhoAias__Dashboard__CreateDefaultClient | true | Whether to generate a default client key. |
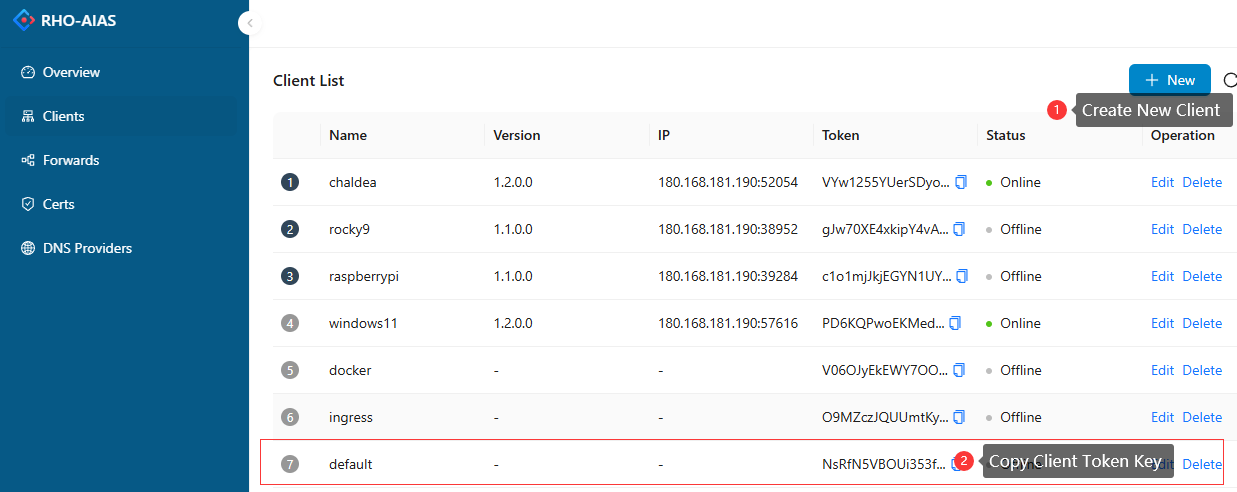
After the server starts, enter the Dashboard(http://{public-ip}:8024) with the default username and password. The dashboard will auto generate a default client key, which you can also manually create in the client list page.
RhoAias provides a variety of client deployment methods, such as docker, service, k8s-ingress etc.
Create a docker configuration file docker-compose.yml on your intranet machine.
services:
rhoaias-client:
container_name: rhoaias-client
image: chaldea/rhoaias-client
restart: always
environment:
# your public server url address
RhoAias__Client__ServerUrl: http://{server-ip}:8024
# The token key that you created on the Dashboard
RhoAias__Client__Token: PCv11vMiZkigHfnzcMLTFgThen execute the command and ensure the client's status on the server dashboard page is online.
docker compose up -dClient Environment Variables
| Variable Name | Description |
|---|---|
| RhoAias__Client__ServerUrl | Server url address. |
| RhoAias__Client__Token | Client TokenKey |
You can download the client binary program on the Release page.
Runs as console:
rhoaias-client -s http://{server-ip}:8024 -t PCv11vMiZkigHfnzcMLTFg| Startup Parameters | Description |
|---|---|
| -s, --server | Server url address. |
| -t, --token | Client TokenKey |
If you want to run the client as a system service:
- On the windows, you can use nssm
- On the linux, you can use systemd
In your K8s cluster, create a namespace:
kubectl create namespace rho-aiasApply the deployment configuration file.
kubectl apply -f https://github.com/chaldea/rho-aias/blob/main/kubernetes/ingress-controller.yaml -n rho-aiasCheck if the Deployment was created.
kubectl get deploymentsRhoAias can be installed via the helm tool, and the chart is located in the ./kubernetes/ingress-rho-aias directory.
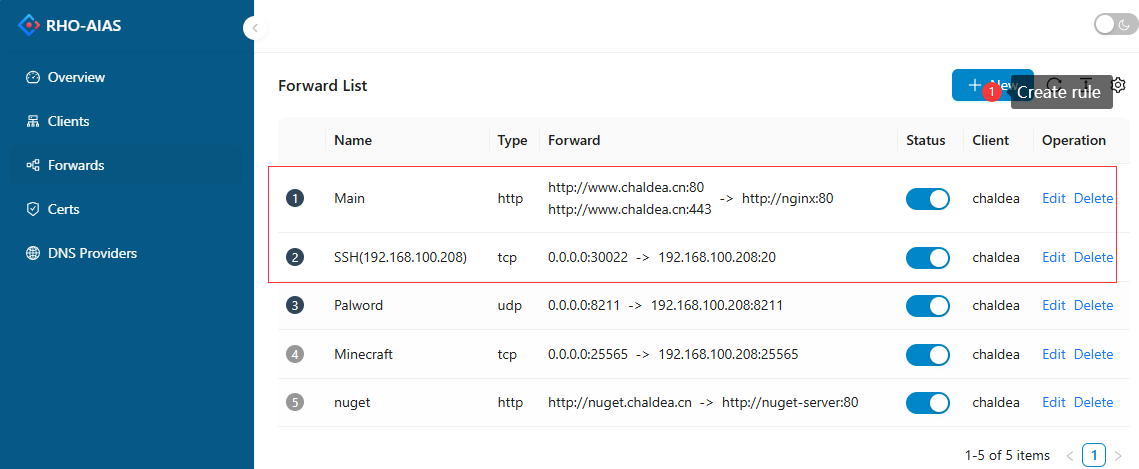
In the forwarding list of the Dashboard, you can create different types of forwarding rules for a specified client, and all requests that meet the rules will be forwarded to the intranet where the client is located.
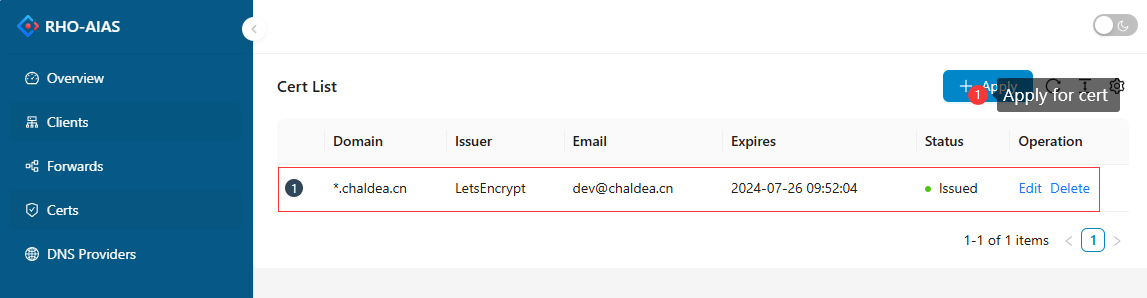
Normally, a website requires an HTTPS certificate to keep the site secure. RhoAias has a built-in https certificate manager, you can apply for a free https certificate based on the ACME protocol. The certificate will be automatically renewed upon expiration.
Let'sEncrypt supports both single-domain(eg: a.sample.com) and wildcard domain(eg: *.sample.com) certificates. A wildcard domain certificate must be supported by DNS provider. When you apply for a wildcard domain certificate, you need to provide the configuration of the DNS provider.
NOTE: Wildcard domain certificate include single-domain certificate, and if you have a DNS provider API, we recommend that you use wildcard domain certificate.
RhoAias can be added directly to the current project as a nuget package.
dotnet add package Chaldea.Fate.RhoAiasFor details, please refer to the development documentation.
If you would like to contribute, feel free to create a Pull Request, or give us Bug Report.