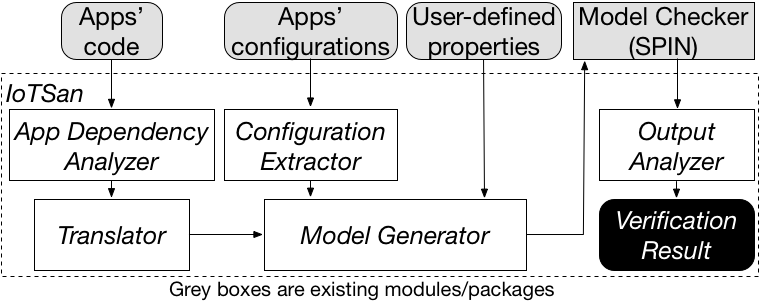
In this repository you will find the detailed technical report and protype code of IoTSan, a model-checking-based tool used to verify the safety of IoT systems.
This work is published at The 14th International Conference on emerging Networking EXperiments and Technologies (CoNEXT '18).
IoTSan is developed based on Bandera and its code structure is as following:
- The "App Dependency Analyzer" module and "Translator" (Groovy to Java) module are at "IoTSan/src/edu/ksu/cis/bandera/jjjc/gparser/"
- The "Model Generator" module is at "IoTSan/src/edu/ksu/cis/bandera/spin/"
- The "Configuration Extractor" module is at "IoTSan/src/configextractor" (This module is not yet integrated into IoTSan at this initial version).
Note: This is the initial version of IoTSan, which does not include all of the modules mentioned in the paper. I will update this repository with additional modules.
-
Create an Eclipse project and clone this repository (you can find the instructions here).
-
Make sure to include all the files (e.g., Lexer.data) in your project.
-
Install Groovy plugin on Eclipse following the instructions at here
-
Add all libraries (.jar files) in the "IoTSan/lib" folder.
-
Create the folder "input/smartapps" at the root directory of your porject. You then need to put the source code of apps and their configuration files in this folder. Note that you should give good names to app files since they will become the names of apps in the resulting modeled system.
-
Run the "IotSan.java" as "Java Application". The resulting Promela model code will be generated and stored at ".../IoTSan/output/IotSanOutput/birc".
-
Append the safety property in LTL format to the end of each output file.
-
Run the verification with SPIN using the following command in a terminal:
spin -search -DVECTORSZ=36736 -DSAFETY -DBITSTATE -E -NOBOUNDCHECK -NOFAIR -NOCOMP -n -w36 <Promela file>. For example:spin -search -DVECTORSZ=36736 -DSAFETY -DBITSTATE -E -NOBOUNDCHECK -NOFAIR -NOCOMP -n -w36 SmartThings0.prom -
If any violation is detected, the file "SmartThing0.prom.trail" will be created by SPIN. Use the following command to get counter-example log:
spin -p -replay SmartThings0.prom > log.txt -
Get a filtered logs by using:
grep -v 'allEvtsHandled' log.txt | grep -v 'generatedEvent.EvtType = g_' | grep -E 'generatedEvent.EvtType =|ST_Command.EvtType =|BroadcastChans|Handle|assert|location.mode' > filterLog.txt
Note that you need to install SPIN by following instructions here before using this tool.
Please refer to the directory "IoTSan/samples/" for examples of app source code, config files, and log files.
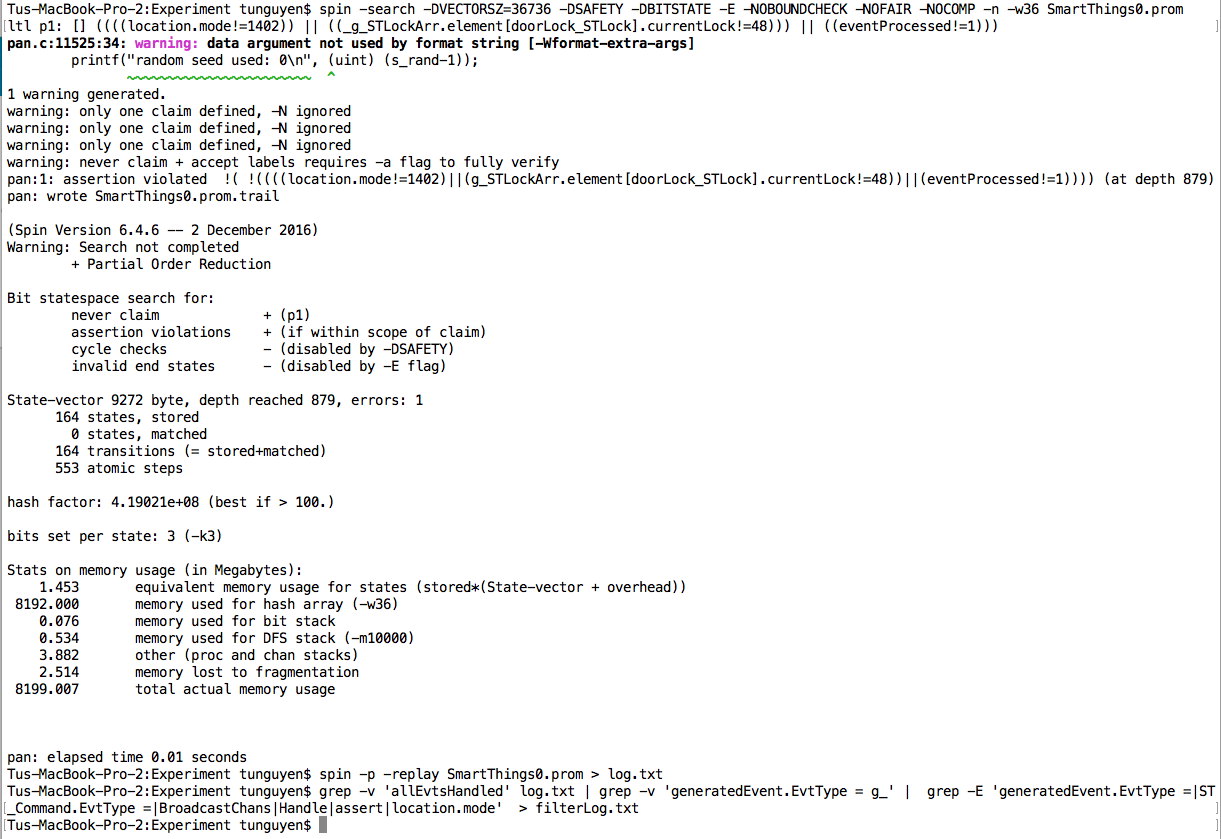
Here is the snapshot of a verification run:
If you use the source code, please cite the following paper:
Dang Tu Nguyen, Chengyu Song, Zhiyun Qian, Srikanth V. Krishnamurthy, Edward J. M. Colbert, and Patrick McDaniel, "IotSan: Fortifying the Safety of IoT Systems," In Proc. of the 14th International Conference on emerging Networking EXperiments and Technologies (CoNEXT '18)