Furious is a fast, lightweight, portable network scanner.
I haven't done any proper performance testing, but a SYN scan of a single host, including all known ports (~6000) will typically take in the region of 4 seconds. On the same machine, nmap took 98 seconds and produced exactly the same results.
You'll need to install libpcap.
- On Linux, install
libpcapwith your package manager - On OSX,
brew install libpcap - On Windows, install WinPcap
Then just:
go get -u github.com/liamg/furious
Use the specified scan type. The options are:
| Type | Description |
|---|---|
syn |
A SYN/stealth scan. Most efficient scan type, using only a partial TCP handshake. Requires root privileges. |
connect |
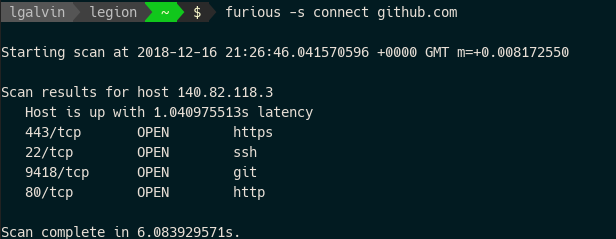
A less detailed scan using full TCP handshakes, though does not require root privileges. |
device |
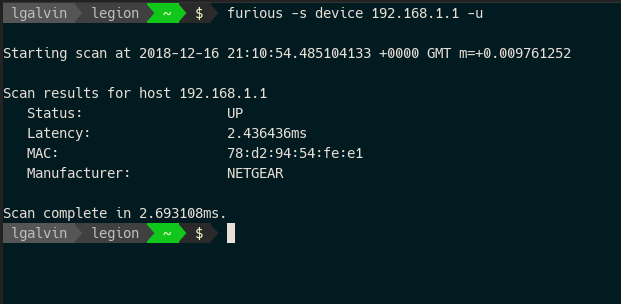
Attempt to identify device MAC address and manufacturer where possible. Useful for listing devices on a LAN. |
The default is a SYN scan.
Scan the specified ports. Defaults to a list of all known ports as provided by IANA.
Ports may be specified using a comma delimited list, and ranges are also allowed.
For example:
--ports 22,80,443,8080-8082
...will scan 22, 80, 443, 8080, 8081, and 8082.
The network timeout to apply to each port being checked. Default is 1000ms.
The number of worker routines to use to scan ports in parallel. Default is 1000 workers.
Only show output for hosts that are confirmed as up.
Output version information and exit.
Furious can be used to:
Scan a single host:
furious 192.168.1.4
Scan a whole CIDR:
furious 192.168.1.0/24
furious -s connect 8.8.8.8 192.168.1.1/24 google.com
sudo -E furious -s syn 192.168.1.1
furious -s connect 192.168.1.1
furious -s device 192.168.1.1/24 -u
If you installed using go, your user has the environment variables required to locate go programs, but root does not. You need to:
sudo env "PATH=$PATH" furious
They're not in my experience, but with default arguments furious scans nearly six times as many ports as nmap does by default.