Idea to create a easy-to-use wrapper over tinc vpn.
node 1
sudo tinc-boot run
node 2
follow command from previous operation
node 1
sudo tinc-boot -t MYSECRET run
node 2
sudo tinc-boot run -t MYSECRET --join http://<node1>:8665
Use (--ufw) to open port on ufw-based systems automatically
tinc-boot run --ufw ...Required opened default ports:
<port>/udp,<port>/tcp- port defined as--tinc-portor generated intinc.conf8665/tcp- port defined as-p --portfor boot protocol18655/tcp (tinc interface)- internal port for communication. Only for interface defined intinc.conf
Tinc VPN - is full-mesh, auto-healing, time-proofed VPN system without single point of failure, with high-throughput and serious cryptography. All nodes in a Tinc network are fully equal. New nodes discovering full topology through any entry point. Node may interact with each other even if they don't have direct connections.
Tinc is a great and have a lot of features. It's ideal for a complicated situations (China, Russia and others). I really admire the project.
But... it's pain to configure and maintain.
Pain to create a new node. Pain to add new node to network.
Minimal configuration for a first public node:
- 2 files (tinc.conf, hostfile),
- 1 script (tinc-up),
- 2 directories (net, hosts),
- 1 command execution (key generation).
(let's not count service initialization and other common stuff)
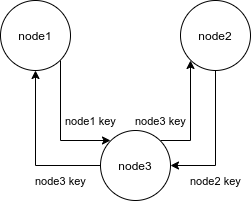
Second node adds key exchange (+1 operation if we will use rsync, or +2 operations if manually).
Next new public nodes require increasing number of additional operations (+N operations, where N is a number of public nodes).
To be honest, to just to connect to the network an only single key exchange operation required: with any public node. Than tincd will discover all other nodes.
But after your node disconnect/reboot and in case of death of your entry node you will be no more able to connect to other alive nodes (because they don't know your key and your node don't know theirs).
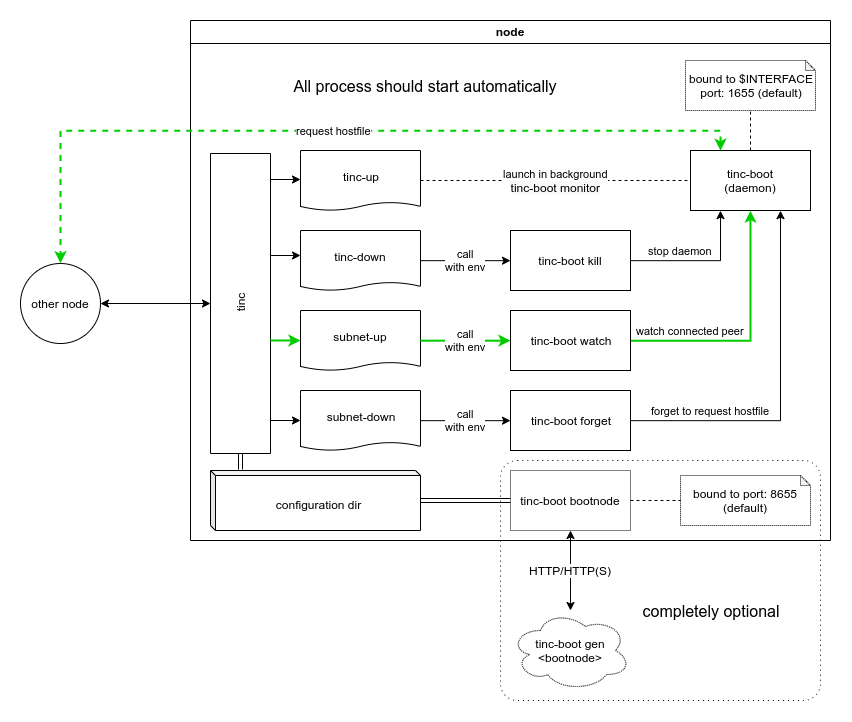
Tinc-boot - is a all-in-one tool with zero dependency (except tinc of course), that aims to achieve:
- one-line node initialization
- automatic keys distribution
- simplified procedure to add new node to existent net
With simple UI (available on your VPN address with port 1655 by default)
Donating always welcome
- ETH:
0xA4eD4fB5805a023816C9B55C52Ae056898b6BdBC - BTC:
bc1qlj4v32rg8w0sgmtk8634uc36evj6jn3d5drnqy
- (recommended) look at releases page and download
- one line shell command:
curl -L https://github.com/reddec/tinc-boot/releases/latest/download/tinc-boot_linux_amd64.tar.gz | sudo tar -xz -C /usr/local/bin/ tinc-boot
-
build from source
go get -v github.com/reddec/tinc-boot/cmd/... -
Ansible galaxy:
ansible-galaxy install reddec.tinc_boot -
From bintray repository for most debian-based distribution (
trusty,xenial,bionic,buster,wheezy):
sudo apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv-keys 379CE192D401AB61
echo "deb https://dl.bintray.com/reddec/debian {distribution} main" | sudo tee -a /etc/apt/sources.list
sudo apt install tinc-boot- Arch Linux in
AUR package
tinc-boot-git:yaourt -S tinc-boot-git
- go 1.13+
- Available by
--helpfor all commands - Available in MANUAL.md
- Linux
tincd 1.10.xxbash- (recommended)
systemd
- Ubuntu 18.04 x64
- Archlinux (Q1 2019) x64
- Manjaro (Q1 2019) x64
Should work on all major linux systems, except generated helpers useful only for systemd-based OS.
Download/build binary to /usr/local/bin/tinc-boot.
sudo tinc-boot gen --standalone -a <PUBLIC ADDRESS>
and follow recommendations
--standalonemeans that it's a first node, no need for keys exchange-a <address>sets public address of node (if exists); could be used several times
Will generate all required files under /etc/tinc/dnet.
sudo tinc-boot bootnode --service --token <SECRETTOKEN>
and follow recommendations
--servicegenerates systemd file to/etc/systemd/system/tinc-boot-{net}.service--dirlocation of tinc configuration--tokenset's authorization token that will be used by clients
sudo tinc-boot gen --token <SECRETTOKEN> <PUBLIC ADDRESS>:8655
Don't forget add
-a <NODE ADDRESS>if applicable
and follow recommendations
Non-primary platform, limited support, but should work
Tested only for x64
Requirements:
- Tinc for Windows: download on official site
- Install TAP driver!:
- Go to
C:\Program Files(x86)\tinc\tap-win64 - As administrator run
addtap.bat
- Rename generated network adapter to the name of the network (
dnetby-default)
Usage:
- Launch command line As administrator
- Navigate to the directory with
tinc-boot.exe - With black-magic,
tinc-boot.exe /helpcommand and instructions for normal OS (*Nix) generate config