Just a working Fork
Fork of the now archived repository. The last set of destructive changes have been reverted, which seem to have arisen as a result of dissatisfaction. The bottom line is that this fork contains all necessary files for building and compiled binaries and ready to use docker images.
See the secure vps for a simple complete and secure sample.
Version 3 contains the last original open source version before archiving minus the latest changes that limited functionality [1] [2].
Version 4 is like version 3, but with the possibility to tunnel TCP ports and ranges. Example:
inlets client --url=wss://dev.example.com --token="<mytoken>" \
--upstream=dev.example.com=nginx:80,tcp:5432=192.168.145.131:5432,tcp:7000=192.168.145.50:8800-8810Original Readme
inlets is a Cloud Native Tunnel written in Go
Expose your local endpoints to the Internet or within a remote network, without touching firewalls.
Intro
inlets ® is how you connect services between different networks. You won't have to think about managing firewalls, NAT or VPNs again. Services can be tunnelled securely over a websocket and accessed on a remote network privately, or exposed on the Internet using an exit-server (5-10USD / mo).
Why do we need this project? Similar tools such as ngrok and Argo Tunnel from Cloudflare are closed-source, have limits built-in, can work out expensive, and have limited support for arm/arm64, Docker and Kubernetes. Ngrok's domain is also often banned by corporate firewall policies meaning it can be unusable. Other open-source tunnel tools are designed to only set up a single static tunnel.
With inlets you can set up your own self-hosted tunnel, copy over the static binary and start tunnelling traffic without any arbitrary limits or restrictions. When used with TLS, inlets can be used with most corporate HTTP proxies.
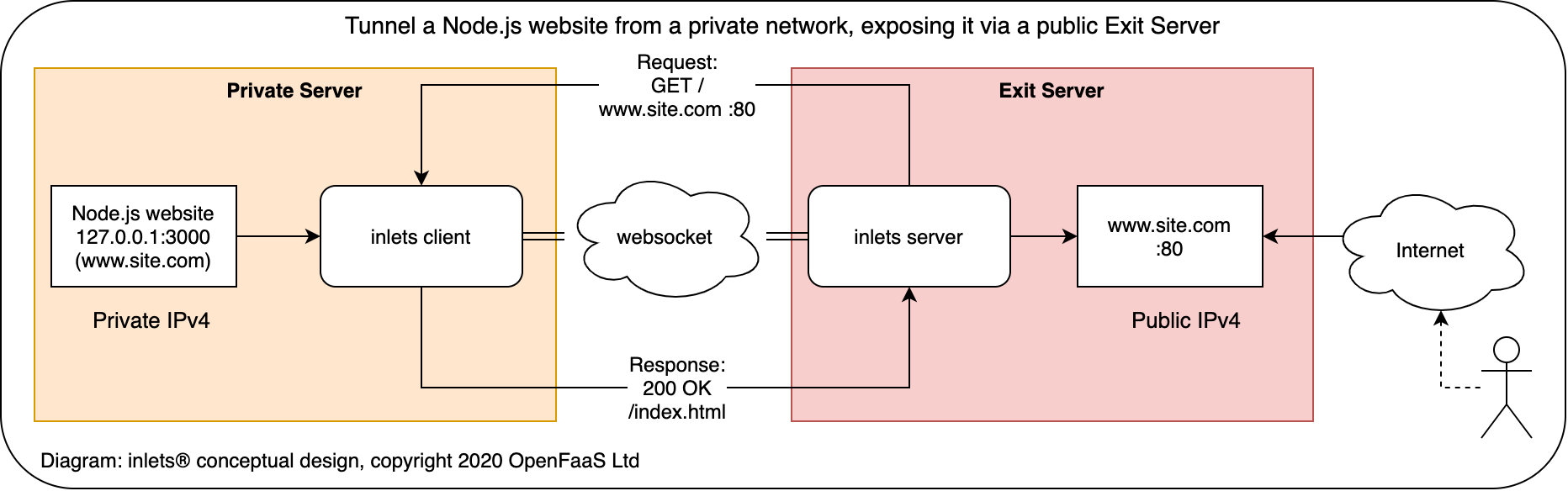
Conceptual diagram for inlets
Do you use inlets? Sponsor the author
Alex is the maintainer of inlets, if you use the project in some way, support it by becoming a sponsor on GitHub.

You can become a sponsor as an individual or as a corporation, check out the tiers to find which is right for you.
About inlets OSS
inlets OSS uses a websocket to create a tunnel between a client and a server. The server is typically a machine with a public IP address, and the client is on a private network with no public address.
inlets OSS is for hobbyists only and has no guarantee or warranty of any kind.
For a commercially-supported solution, see inlets PRO, which has secure defaults and thorough testing.
Private or public tunnels?
- A private tunnel is where you start a tunnel to a server and only expose it on the server's LAN address (this can replace the use-cases where you would use a VPN or Kubernetes federation)
- A public tunnel is where you expose the private service to users via the server's public IP
Features
- Tunnel HTTP or websockets
- Expose multiple sites on same port through the use of DNS entries and a
Hostheader - Upgrade to link encryption using TLS for websockets (
wss://) with an external add-on or inlets PRO - Shared authentication token for the client and server
- Automatic reconnects for when the connection drops
Distribution:
- Binaries and Docker images for multiple architecture - Intel and ARM
- Dockerfile
- systemd unit file for client/server
inlets PRO has a native Kubernetes LoadBalancer integration through the inlets-operator.
Going to production with inlets PRO
The following features / use-cases are covered by inlets PRO:
- Tunnel L4 TCP traffic such as websockets, databases, reverse proxies, remote desktop, VNC and SSH
- Tunnel L7 HTTPS / REST traffic - with automated Let's Encrypt support
- Expose multiple ports from the same client - i.e. 80 and 443
- Kubernetes helm charts, YAML and Operator
- Automated TLS for the control-plane
- Commercial services & support
- Documentation, blog posts, tutorials and videos
inlets projects
inlets is a Cloud Native Tunnel and is listed on the Cloud Native Landscape under Service Proxies.
- inlets PRO - Secure HTTP(s) and TCP tunnels with automated TLS encryption. Replaces inlets OSS
- inlets-operator - Public IPs for your private Kubernetes Services and CRD using inlets PRO
- inletsctl - The fastest way to create self-hosted exit-servers using inlets PRO
- inlets - Cloud Native Tunnel for HTTP only - no tutorials, automation, TLS, TCP or Kubernetes integration available. Superseded by inlets PRO
Get inlets OSS
You can install the CLI with a curl utility script, brew or by downloading the binary from the releases page. Once installed you'll get the inlets command.
Install the CLI
Note:
inletsis made available free-of-charge, but you can support its ongoing development and sign up for updates through GitHub Sponsors 💪
Utility script with curl:
# Install to local directory
curl -sLS https://get.inlets.dev | sh
# Install to /usr/local/bin/
curl -sLS https://get.inlets.dev | sudo shNote: the
brewdistribution is maintained by the brew team, so it may lag a little behind the GitHub release.
Binaries are made available on the releases page for Linux (x86_64, armhf & arm64), Windows (experimental), and for Darwin (MacOS). You will also find SHA checksums available if you want to verify your download.
Windows users are encouraged to use git bash to install the inlets binary.
inlets PRO
inlets PRO superceds the original inlets OSS project and includes: commercial support, automation, secure defaults, and HTTPS/TCP tunnels.
In "A tale of two networks" Alex Ellis and Johan Siebens explore blog posts, use-cases and show demos of inlets PRO.
A tale of two networks - demos and use-cases for inlets tunnels
Quickstart tutorial
You can run inlets between any two computers with connectivity, these could be containers, VMs, bare metal or even "loop-back" on your own laptop.
Try the quickstart tutorial now on your local computer.
Documentation & tutorials
inlets and inlets PRO have their own documentation site:
Official docs: docs.inlets.dev
- Docs: inlets PRO Kubernetes charts, operator and manifests
- Tutorial: Get a LoadBalancer for your private Kubernetes cluster with inlets-operator
- Docs: Quickstart tutorial on your laptop
See also: advanced usage of inlets including Docker, Kubernetes, multiple-services, and binding to private IPs
What are people saying about inlets?
Read community tutorials, the launch posts on Hacker News, and send a PR if you have written about inlets or inlets PRO:
You can share about inlets using
@inletsdev,#inletsdev, andhttps://inlets.dev.
Do you use inlets or inlets PRO?
Add an entry to the ADOPTERS.md file with your use-case.
Disclaimer
Developers wishing to use inlets within a corporate network are advised to seek approval from their administrators or management before using the tool. By downloading, using, or distributing inlets, you agree to the LICENSE terms & conditions. No warranty or liability is provided.
Development
See CONTRIBUTING.md
Other Kubernetes port-forwarding tooling
kubectl port-forward- built into the Kubernetes CLI, forwards a single port to the local computer.- inlets PRO - exit-server automation, multiple ports, TCP and automatic Let's Encrypt
- kubefwd - Kubernetes utility to port-forward multiple services to your local computer.
- kurun - Run main.go in Kubernetes with one command, also port-forward your app into Kubernetes.
inlets® is a registered trademark of OpenFaaS Ltd. All rights reserved, registered company in the UK: 11076587