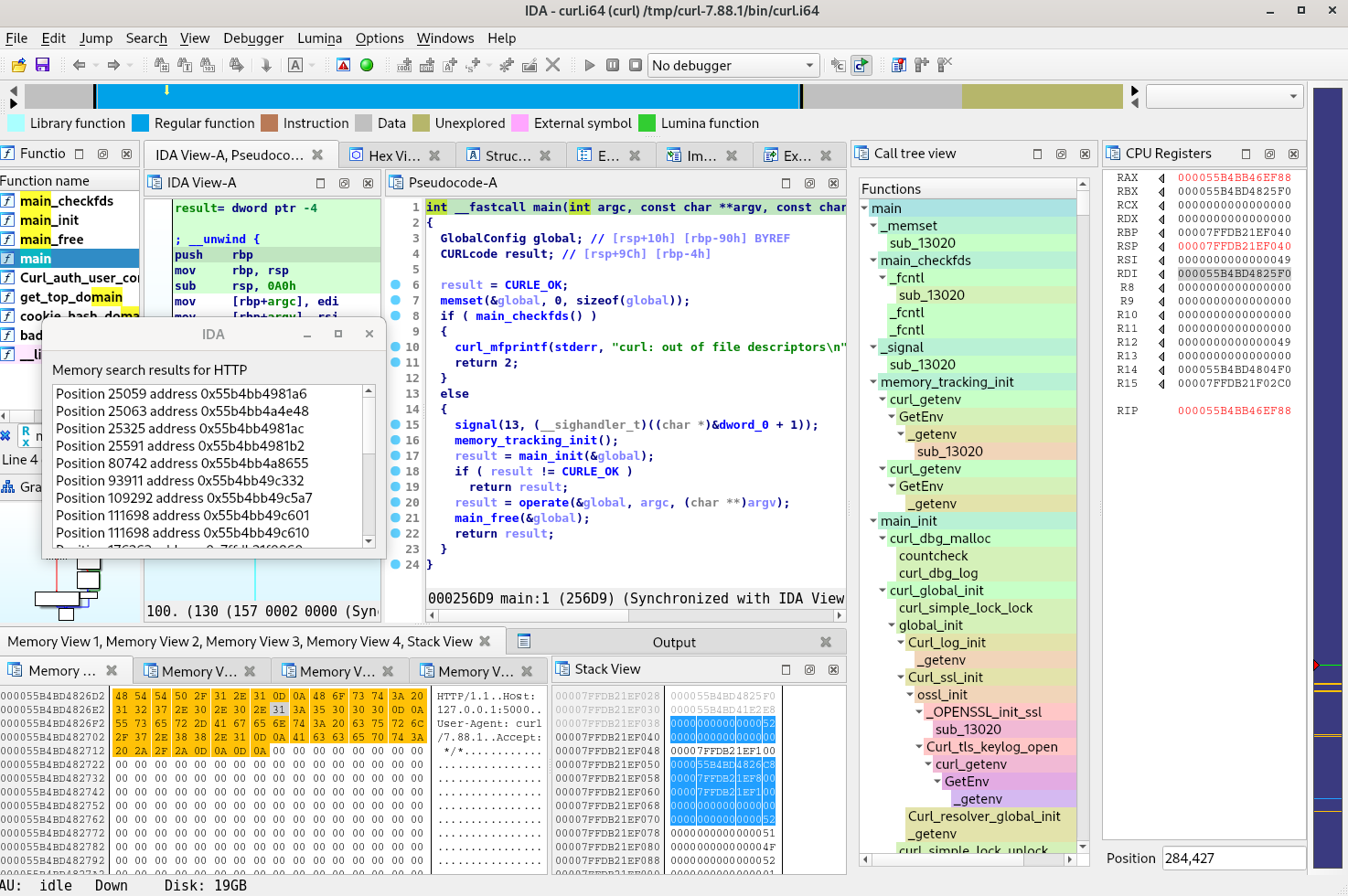
Multi-platform trace generation with Frida, combined with a modified version of the Tenet plugin for exploration.
Blogpost on the Synacktiv website
General use case : Tracing the execution of a specific function in a userland process, on a Frida-compatible system (Tested on Linux/Android/iOS/Windows).
This repository contains our customized fork of Tenet in the tenet subdirectory. As explained in the README, we did not do a pull request (yet) because our new features break some of the legacy features.
Our custom version is required for use with this tracer, but can still process traces from other Tenet tracers.
This repository needs to be cloned using the recursive flag :
git clone --recursive https://github.com/synacktiv/frinet.git
Compatible with Windows, Linux, Android & iOS
Fully supported architecture :
- arm64
- x64
Partially supported architectures (slower and less precise memory tracking, but usually good enough) :
- arm
- x86
Python3 and Frida
pip install frida
usage: python3 trace.py [-h] [-v] [-D DEVICE] [-U] [-R] [-H HOST] [-m]
[-a ARGS] [-e] [-s] [-E END]
{spawn,attach} ... process module addr
positional arguments:
{spawn,attach}
spawn Spawn process
attach Attach to process
process attach:[process name or PID]; spawn:[binary path or
package name]
module module name to instrument
addr entrypoint function address
optional arguments:
-h, --help show this help message and exit
-v, --verbose verbose output
-D DEVICE, --device DEVICE
connect to device with the given ID
-U, --usb connect to USB device
-R, --remote connect to remote frida server
-H HOST, --host HOST connect to remote frida server on host
-m, --multirun do not unhook after first execution
-a ARGS, --args ARGS comma-separated argument list for spawn (including
binary name) : "/bin/sh,-c,ls"
-e, --exclude exclude all other modules (memory tracing will be
inaccurate)
-s, --slow use slower JS implementation (multiarch)
-E END, --end END specify end address instead of function exit (-1 to
never end)
python3 trace.py spawn [BIN_PATH] [MODULE_NAME] [FUNC_ADDR] -a [ARGS]
python3 trace.py spawn /bin/ls ls 0x1234 -a '/bin/ls,-la'
This will trace one execution of the function at address 0x1234, until it returns.
It is also possible to specify an end address with "-E", or trace multiple executions with "-m".
python3 trace.py attach [PROCNAME_OR_PID] [MODULE_NAME] [FUNC_ADDR] -U
python3 trace.py attach sh sh 0x1234 -U
IDA Pro (tested on Version 8.3.230608 Linux x86_64 but should work in most recent versions compatible with Tenet legacy)
cp tenet/plugins/tenet_plugin.py ~/.idapro/plugins
cp -R tenet/plugins/tenet ~/.idapro/plugins
Then, in IDA after loading the correct binary :
File -> Load file -> Tenet trace file
For more information, see the README.md from our Tenet fork, as well as the original author's blogpost about the tool :
- https://github.com/hexa-synacktiv/tenet/blob/master/README.md
- http://blog.ret2.io/2021/04/20/tenet-trace-explorer/
Some new features have been added to the Tenet plugin. The compressed trace format feature has been removed for now, as it needs to be modified to handle the added features.
Most notably :
- The Call tree view window gives a clickable indented overview of the whole execution trace.
- The Seach bytes feature is available in the Memory views context menu, and does the search in both space and time