A Kubernetes controller that watches for the expiration of Kubernetes Secrets and raises events accordingly.
This project is a Kubernetes Operator built with Kubebuilder. It introduces a new Custom Resource Definition (CRD) SecretWithExpiry into the Kubernetes API, which is like a regular Secret but with an added expiry date.
You’ll need a Kubernetes cluster to run against. You can use KIND to get a local cluster for testing, or run against a remote cluster.
Note: Your controller will automatically use the current context in your kubeconfig file (i.e. whatever cluster kubectl cluster-info shows).
Install the CRDs into a cluster:
git clone https://github.com/devops-360-online/k8s-secret-expiry-controller.git
cd k8s-secret-expiry-controller
kubectl apply -k config/crd
kubectl apply -k config/defaultCreate a new file named secretWithExpiry.yaml with the following contents:
apiVersion: expiry.devops-360.online/v1
kind: SecretWithExpiry
metadata:
name: example-secretwithexpiry
spec:
secretName: my-secret
expiryDate: "2023-06-30T00:00:00Z"Replace "2023-06-30T00:00:00Z" with the actual expiry date you want for your secret. The date must be in the format YYYY-MM-DDTHH:MM:SSZ.
Then, apply this file:
kubectl apply -f secretWithExpiry.yamlTo view the events associated with a SecretWithExpiry object:
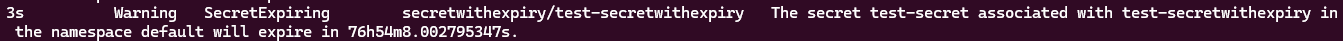
kubectl describe secretwithexpiry example-secretwithexpiryThis command will output a description of the SecretWithExpiry object, including a list of recent events. The events will show if the secret has expired, is about to expire in less than 7 days, or if the expiry date has been updated.
Or
kubectl get eventsmake docker-build docker-push IMG=<some-registry>/k8s-secret-expiry-controller:tagkubectl apply -k config/defaultTo delete the CRDs from the cluster:
make uninstallUnDeploy the controller from the cluster:
make undeployThis project welcomes contributions. Please feel free to submit pull requests for bug fixes, improvements or new features.
This project aims to follow the Kubernetes Operator pattern. It uses Controllers, which provide a reconcile function responsible for synchronizing resources until the desired state is reached on the cluster.
Install the CRDs into the cluster:
make installRun your controller (this will run in the foreground, so switch to a new terminal if you want to leave it running):
make runNOTE: You can also run this in one step by running: make install run
If you are editing the API definitions, generate the manifests such as CRs or CRDs using:
make manifestsNOTE: Run make --help for more information on all potential make targets.
More information can be found via the Kubebuilder Documentation.
This project is licensed under the MIT License. See the LICENSE file for details.