| page_type | languages | products | |||
|---|---|---|---|---|---|
sample |
|
|
The sample is a native Android application that uses the Azure Communication Services Android client libraries to build a calling experience that features both voice and video calling. The application uses a server-side component to provision access tokens that are then used to initialize the Azure Communication Services client library. To configure this server-side component, feel free to follow the Trusted Service with Azure Functions tutorial.
Additional documentation for this sample can be found on Microsoft Docs. See this sample's wiki to see updated information on known issues
- Start a new group call
- Join an existing group call
- Join an existing Teams Meeting (For instructions: Teams Tenant Interoperability)
- Render remote participant video streams dynamically
- Switch layout between different call cases: only-local video view, one-on-one call view and group call with multiple participants
- Turning local video stream from camera on/off
- Mute/unmute local microphone audio
- An Azure account with an active subscription. Create an account for free.
- An OS running Android Studio.
- A deployed Communication Services resource. Create a Communication Services resource.
- An Authentication Endpoint that will return the Azure Communication Services Token. See example
- Open Android Studio and select
Open an Existing Project. - Select folder
AzureCalling. - Expand app/assets to update
appSettings.properties. Set the value for the keycommunicationTokenFetchUrlto be the URL for your Authentication Endpoint.
- Build/Run in Android Studio
For simple demonstration purposes, this sample uses a publicly accessible endpoint by default to fetch an Azure Communication token. For production scenarios, it is recommended that the Azure Communication token is returned from a secured endpoint.
With additional configuration, this sample also supports connecting to an Azure Active Directory (AAD) protected endpoint so that user login is required for the app to fetch an Azure Communication Services access token. See steps below:
-
Enable Azure Active Directory authentication in your app.
-
Go to your registered app overview page under Azure Active Directory App Registrations. Take note of the
Package name,Signature hash,MSAL Configutaion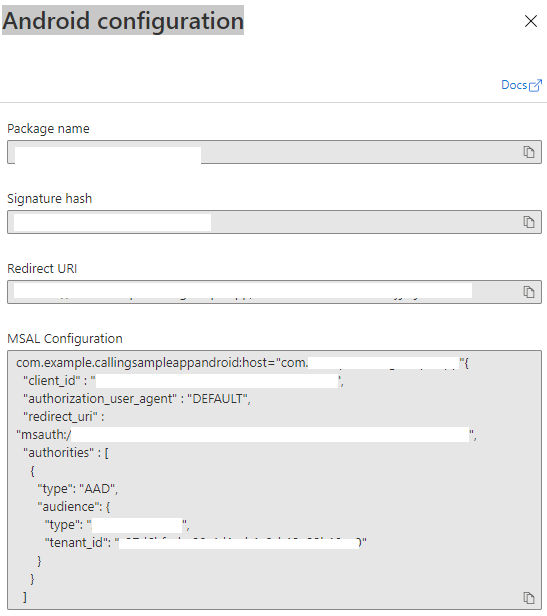
-
Edit
AzureCalling/app/src/main/assets/appSettings.propertiesand setisAADAuthEnabledto enable Azure Active Directory -
Edit
AndroidManifest.xmland setandroid:pathto keystore signature hash. (Optional. The current value uses hash from bundled debug.keystore. If different keystore is used, this must be updated.)<activity android:name="com.microsoft.identity.client.BrowserTabActivity"> <intent-filter> <action android:name="android.intent.action.VIEW" /> <category android:name="android.intent.category.DEFAULT" /> <category android:name="android.intent.category.BROWSABLE" /> <data android:host="com.azure.samples.communication.calling" android:path="/Signature hash" <!-- do not remove /. The current hash in AndroidManifest.xml is for debug.keystore. --> android:scheme="msauth" /> </intent-filter> </activity>
-
Copy MSAL Android configuration from Azure portal and paste to
AzureCalling/app/src/main/res/raw/auth_config_single_account.json. Include "account_mode" : "SINGLE"{ "client_id": "", "authorization_user_agent": "DEFAULT", "redirect_uri": "", "account_mode" : "SINGLE", "authorities": [ { "type": "AAD", "audience": { "type": "AzureADMyOrg", "tenant_id": "" } } ] } -
Edit
AzureCalling/app/src/main/assets/appSettings.propertiesand set the value for the keycommunicationTokenFetchUrlto be the URL for your secure Authentication Endpoint. -
Edit
AzureCalling/app/src/main/assets/appSettings.propertiesand set the value for the keyaadScopesfromAzure Active DirectoryExpose an APIscopes
- Azure Communication Calling Features - To learn more about the calling Android sdk -Azure Communication Android Calling SDK
Please refer to the wiki for known issues related to this sample.