This tool was originally created to quickly generate certificate chains for local development and testing. The generated files are especially useful when testing code that deals with certificate chains and their verification.
- goimports go install golang.org/x/tools/cmd/goimports@latest
- gofumpt go install mvdan.cc/gofumpt@latest
- golangci-lint or task install/lint
- trivy or task install/trivy
Binaries for Linux, Windows and Mac are available as tarballs on the release page.
If you have go installed.
go install github.com/dimaunx/gencert@latestsh -c "$(curl -sL https://taskfile.dev/install.sh)" -- -d -b /usr/local/bin
git clone https://github.com/dimaunx/gencert.git
cd gencert
task build
gencert create -hgencert create -vAbove command is equivalent to:
gencert create -v --path ca01 --ca-cn ca01 --ca-days 365 --int-num 1 --int-hierarchy forest --int-days 364 --cert-cn test.example.com --cert-days 363The command will generate in a local ca01 folder a root CA, intermediate CA, one leaf client/server certificate
and export the CA chain to a file in PEM format. The chain file will not include the client/server certificate,
only root and intermediate CA certificates.
The chain can be verified with:
openssl verify -CAfile ca01/ca-chain.cert ca01/test.example.com.certThe folder will also contain CA private keys. These keys can be used to generate more certificates with openssl
command if required. It is recommended to sign the leaf certificate with the intermediate keys and not with the
root certificate keys.
openssl req -new -nodes -out ca01/test.local.csr -newkey rsa:2048 -keyout ca01/test.local.key -subj '/C=US/L=Los Angeles/O=Example/OU=Example/CN=test.local'
cat > ca01/test.local_v3_ext << EOF
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = test.test.local
DNS.2 = www.test.local
IP.1 = 192.168.1.1
IP.2 = 192.168.2.1
EOF
openssl x509 -req -in ca01/test.local.csr -CA ca01/ca01-int01.cert -CAkey ca01/ca01-int01.key -CAcreateserial -out ca01/test.local.cert -days 7 -sha256 -extfile ca01/test.local_v3_ext
openssl x509 -noout -text -in ca01/test.local.cert # view the certificate
openssl verify -CAfile ca01/ca-chain.cert ca01/test.local.cert # verify chaingencert create --path ca02 --ca-cn ca02 --ca-days 7 --int-num 2 --int-hierarchy ladder --int-days 6 --cert-cn test.test.com --cert-days 5- --path - Location for the generated files, relative to the folder that the
gencertbinary was executed from. - --ca-cn - Root CA common name.
- --ca-days - Root CA duration in days.
- --int-num - Number of intermediate certificates to generate. If
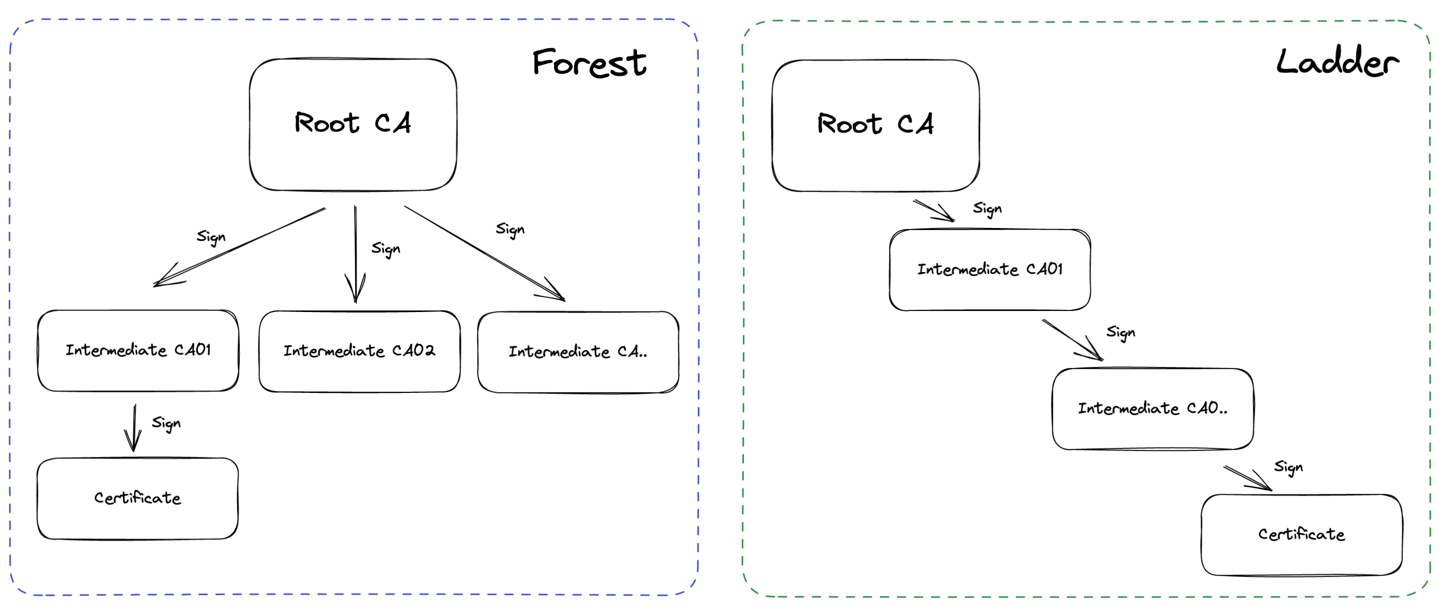
0is used no intermediates will be generated. - --int-hierarchy - Can be
forestorladder.laddermeans that each intermediate (if more than one requested) will be signed by a previous intermediate.forestmeans that all intermediates are signed by the same root CA. - --int-days - Intermediate certificates duration in days.
- --cert-cn - Client/Server leaf certificate common name.
- --cert-days - Client/Server leaf certificate duration in days.
The chain can be verified with:
openssl verify -CAfile ca02/ca-chain.cert ca02/test.test.com.certtask -ltask test
task covertask linttask gofumpttask goimportstask trivy