Writing debugger for Windows (x86-64). Debugger uses
- Capstone framework to disassembly code.
- DbgHelp to get symbols for windows API (.pdb symbols not supported yet)
Tested on Windows 7 (6.1.7601 SP1) with GCC 7.3.0 and CMake 3.14.7 for MinGW produced binaries.
Debugger can contain bugs because it's just side project to learn new things and that's the reason it was built.
You'll need CMake and MinGW (tested) or MSVC (should work)
Compile on Windows with MinGW compiler
git clone --recurse-submodules https://github.com/domin568/MalDbg
mkdir build
cd build
cmake -G "MinGW Makefiles" ..
mingw32-make
maldbg <exe>
help
Show help information.
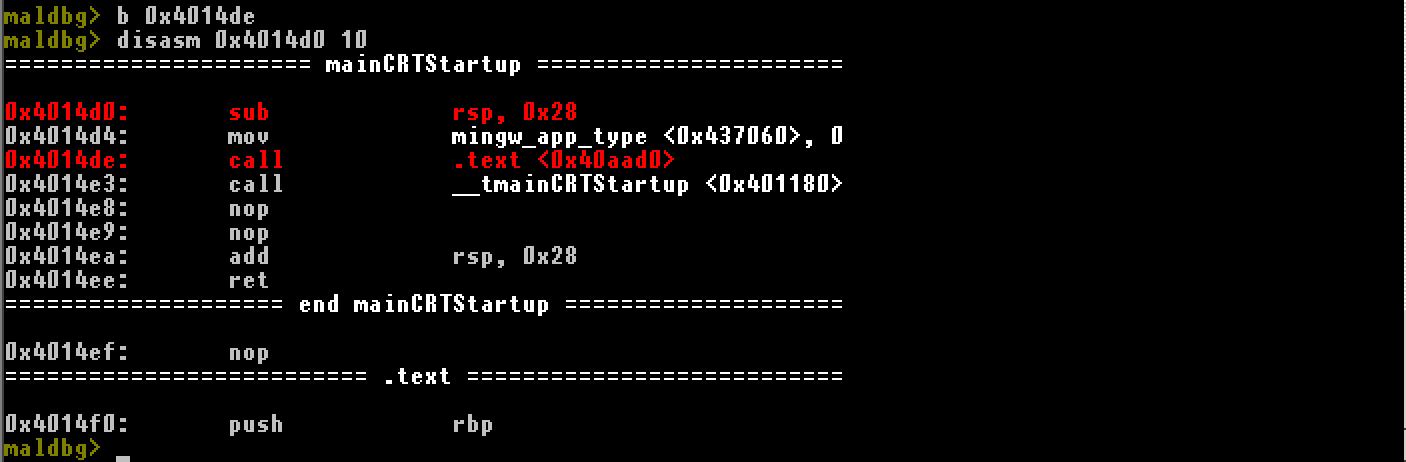
b, bp, br, breakpoint <hexadecimal address>
Breakpoint at specified hexadecimal address. 0x is optional.
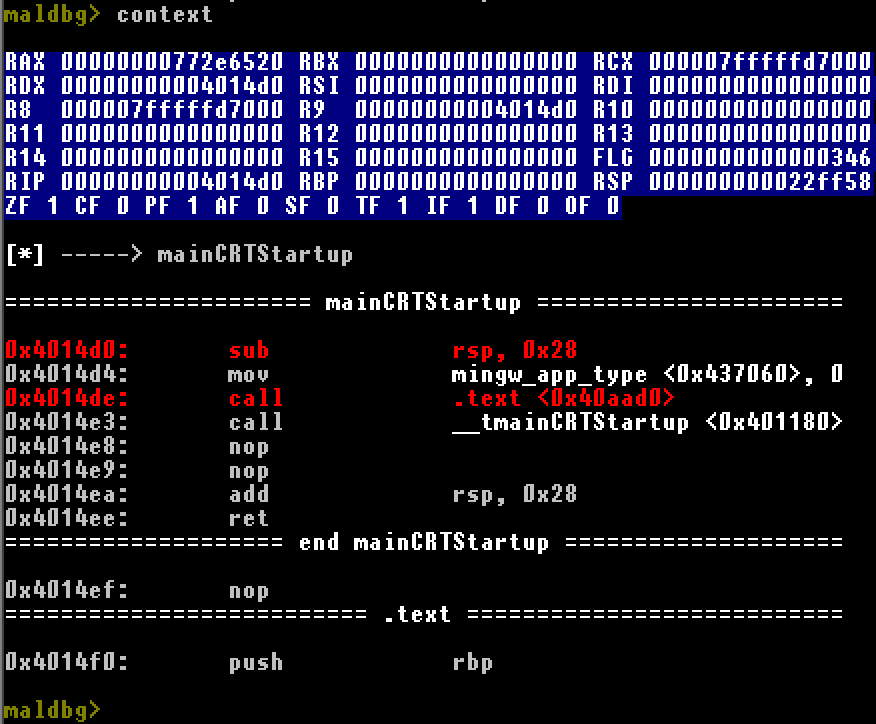
context
Shows current state of execution (registers, disassembly, function name if symbol available).
disasm, disassembly <hexadecimal address> <instruction count>
Disassemblies specified number of instructions at specified address.
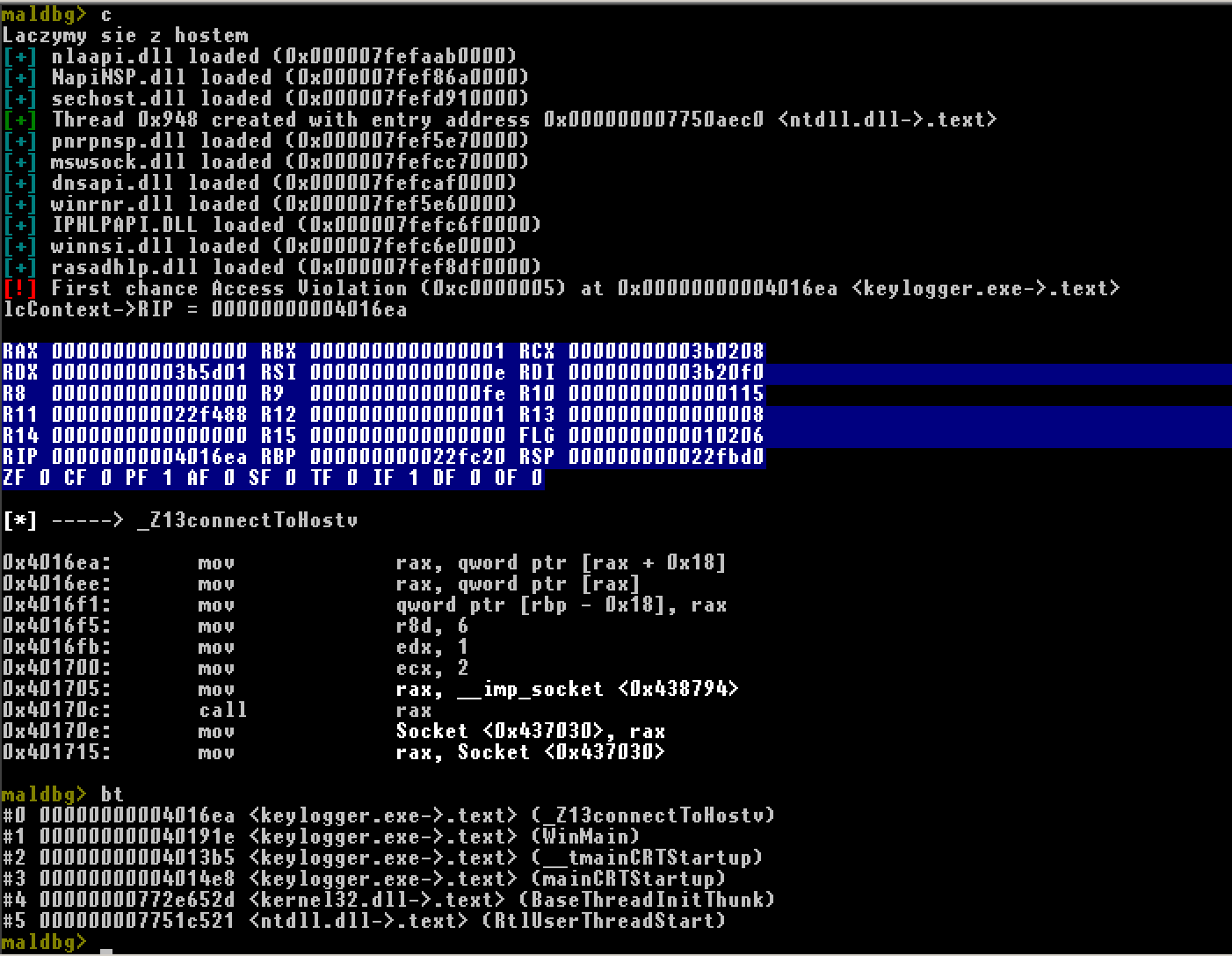
c, continue
Continue process.
e, exit
Exit from debugger. CTRL-C not yet interrupts debugged execution, just exiting.
si, step in, s i
Step one instruction into.
ni, next instruction, n i
Step one instruction further in current frame
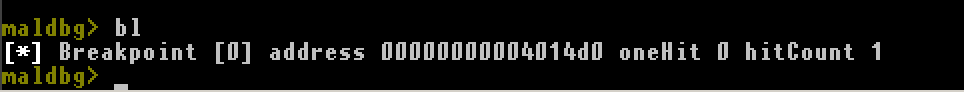
bl, show breakpoints, breakpoint list, b l, b list, breakpoint l
Show active breakpoints, their type and hit count.
bd, b delete, breakpoint delete <index/address>
Delete breakpoint by index (providing decimal number) or by address (providing hexadecimal address).
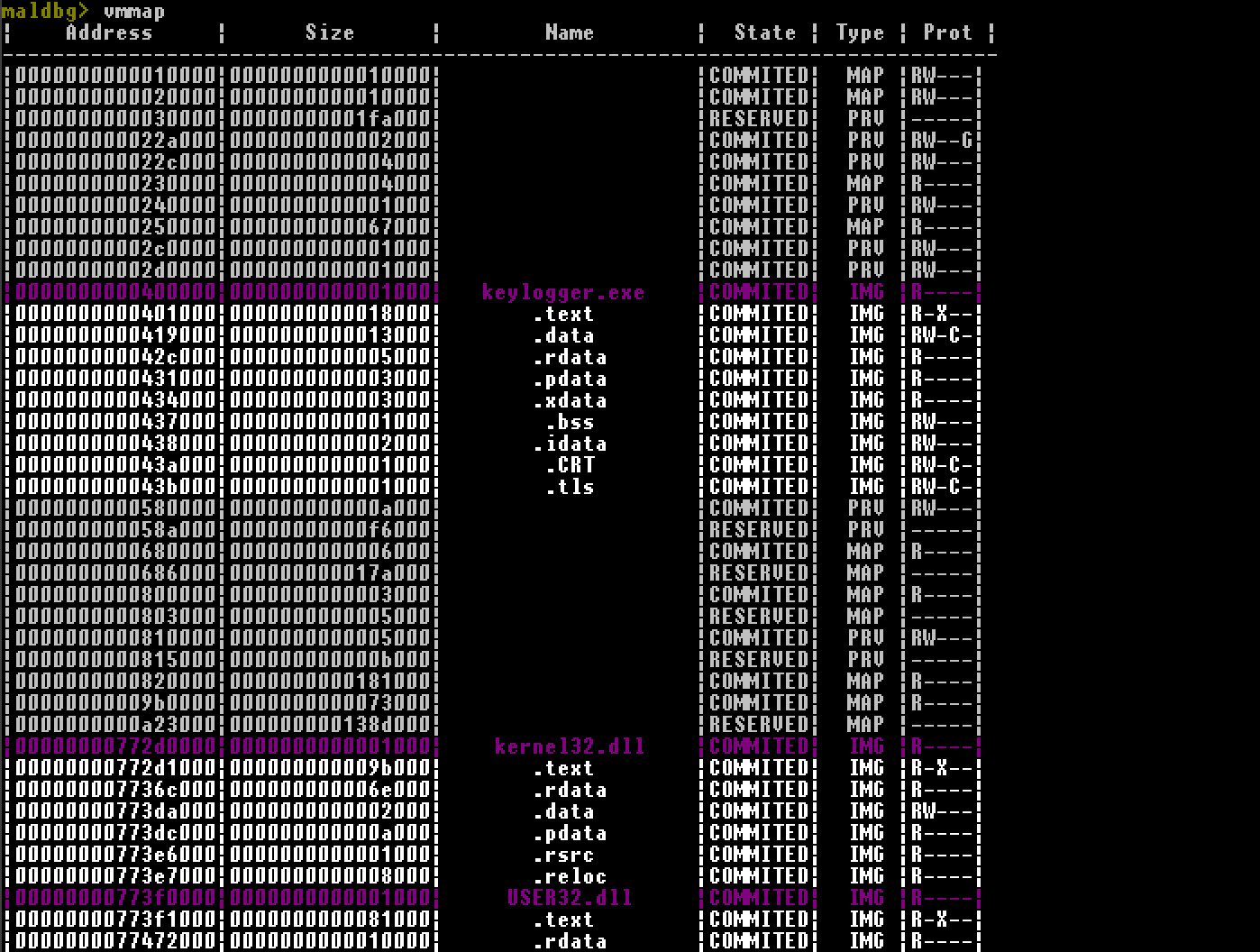
vmmap, memory mappings, map
Show map of whole virtual memory for this process including modules and their sections names.
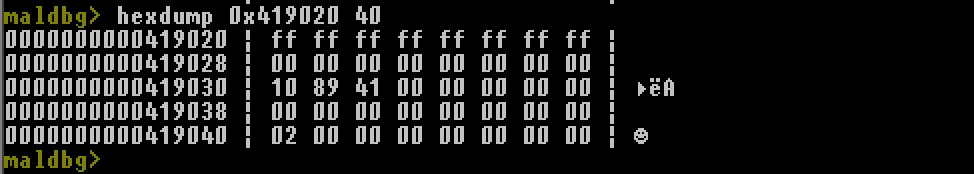
hexdump, h, hex <address> <size>
Print 8 byte width hexdump with ASCII at specified address of given size.
sr, set register <register> <hex value>
Sets register (rax, rcx, rflags...) with desired value.
write memory, wm <hex address> <size decimal> <hex value>
Write integer value at specified address up to 8 bytes.
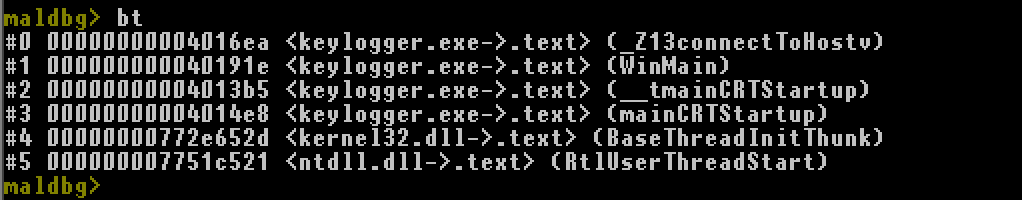
backtrace, bt
Show current call stack of current thread.
- Provide information about debugger events and exceptions raised.
- Prepared program structure for automating commands (like gdb script) soon.
- Ability to disassembly instructions at specified address.
- Shows context of actual thread after each interrupt of execution.
- Ability to manually set breakpoints (one hit also).
- Automatic breakpoint at entrypoint of loaded PE file.
- Colored output for cmd.exe.
- Next instruction and step in commands.
- Show actual breakpoints with their hit count.
- Delete breakpoints by index or by address.
- Map of virtual memory for current process.
- vmmap shows also names of modules and their sections.
- Setting registers with desired values.
- Printiing hexdump of memory.
- Writing integer values to memory (up to 8 bytes)
- Call stack with additional information.
- COFF symbols produced by MinGW parsing, showing them in disassembly and backtracing.
- callstack. ☑
- vmmap with names (need to parse PE files). ☑
- parse IAT to get function names if symbols not available
- parse .pdb
- test with MSVC compiled binaries