I created this project as a solution for the Auror Project Challenge - 2, by Sudarshan Pisupati.
The challenge requires the following Active Directory environment setup :
There will be 3 machines in this lab:
- 1 Domain Controller
- 1 Server which is designated the “crown jewel” server
- 1 machine where you will test your solution designated as your own machine
Create and distribute security groups and members:
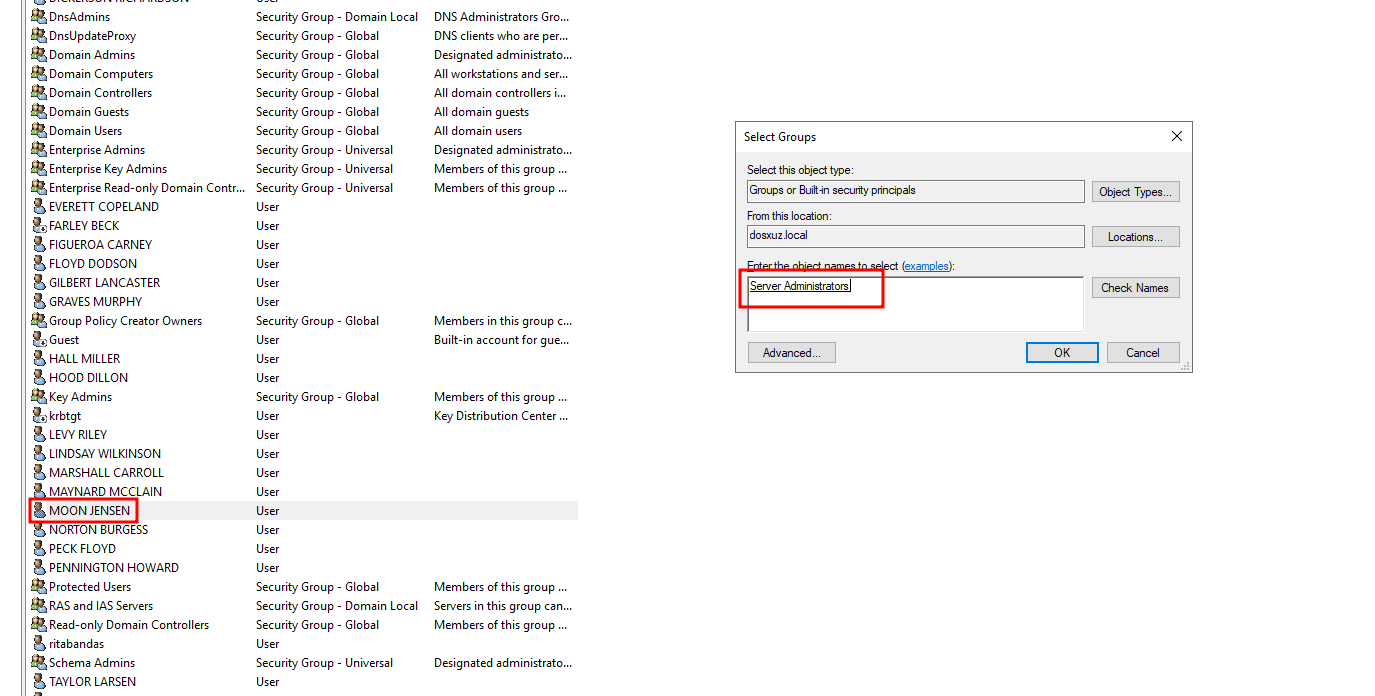
- “Server Administrators” is local administrator on crown jewel server - has 5 members
- “Server Maintenance” has RDP rights - has 5 members. 2 members are also Server Administrators.
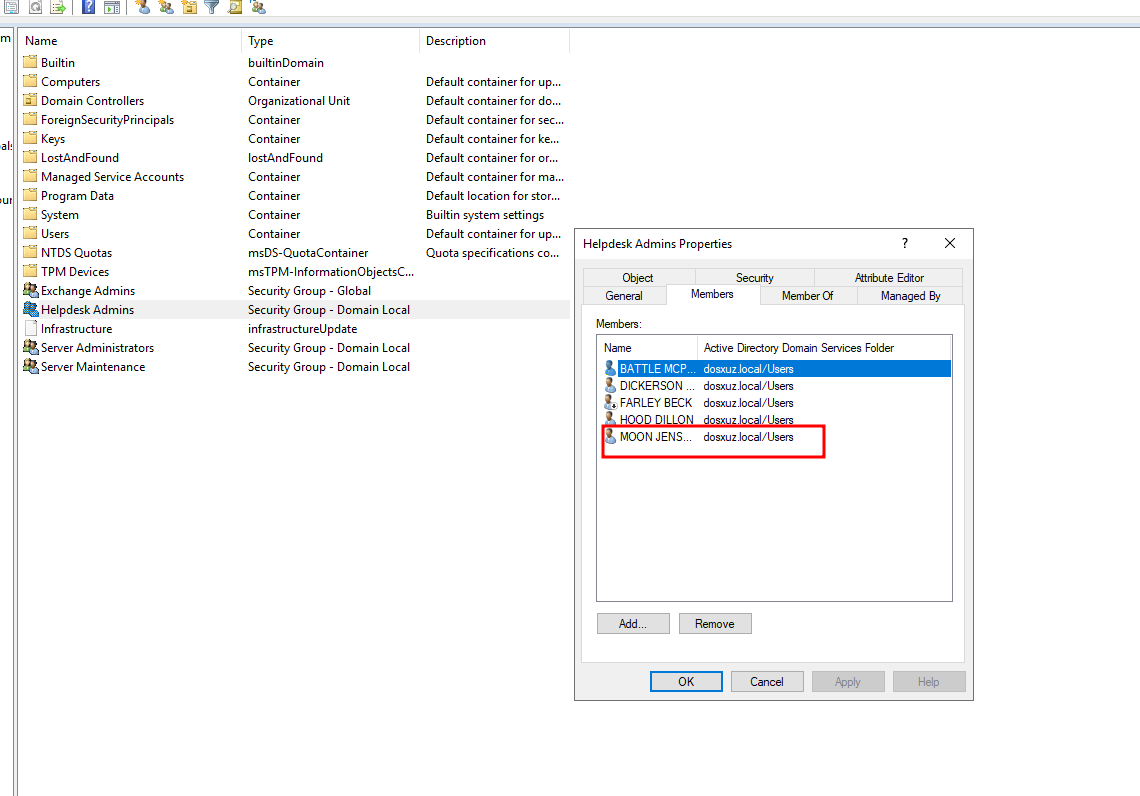
- “Helpdesk Admins” is local administrator on your own machine - has 5 members
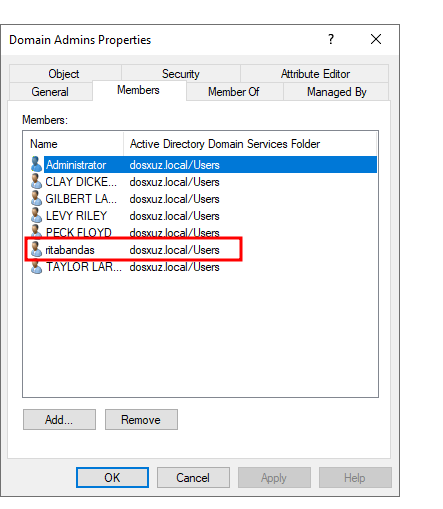
- “Domain Admins” has 5 members
- “Exchange Admins” is a local administrator on the domain controller - has 5 members
Attack surface detection use cases:
-
Gather the count of administrators on the crown jewel machine and domain controller (including local accounts). Detect when this number changes.
-
Detect when a computer account is added to any of the created domain security groups.
-
Detect a change to the domain admins group membership and alert in slack
-
Detect when a helpdesk administrator is also a server administrator
-
Detect an attempt to spray passwords using user attributes
Test Cases:
-
Add a local administrator account to the crown jewel machines
-
Create a group with 5 members and add it to the server administrators group
-
Add a computer account to the domain admins group
-
Add server administrator group membership to one of the members of the “helpdesk admins”
-
Password spray against all users using an automated tool
The LANALyser code is the one that we run on the "Own Machine" (Here it is Client01). You can use the Visual Studio project solution to open and build the project
Before compiling change the hardcoded IP address on the Client.cs code. (Will be changed later on)
- It monitors total numner of admins (including local admin)
- It monitors admin groups and checks if there is any changes to them
- It monitors if any computer account is added to any Security Group or not
- It monitors for password sprays by using the user attributes
badPwdCountandbadPasswordTime - It does these things using LDAP queries (reason for being called LANALyser) and sends the results to the
server.pycode running on another linux server (or windows if required) - It runs at an interval of 300 miliseconds gap between each function
- Can be run by user
NOTE: Detailed working description will be provided in my blog once I am satisfied with the working
- The
server.pyprogram starts a TCP server and waits for connections from theLANALyser.exe - It accepts all the inputs sent to it and has function which analyses the output
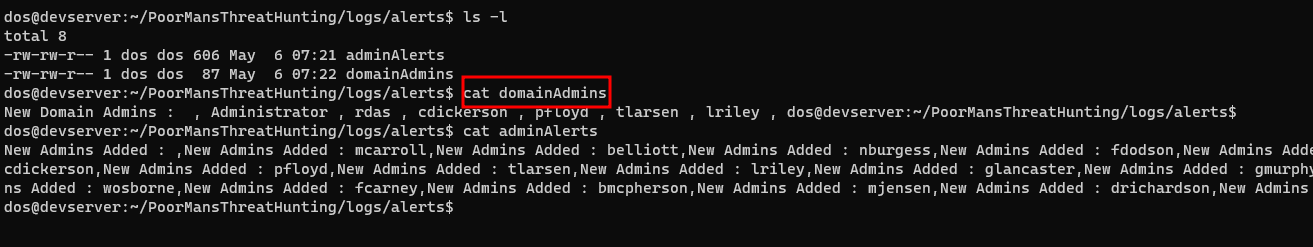
- Then it will create alert files in the folder
logs/alertsdepending upon the type of alert that is generate (Slack integration will be done later)
- First place the compiled binary of
LANALyser.exeon the machine that you Own (not the Cown Jewel) - Then start the
server.pycode on linux server
python3 server.py
- Once the server has started, run the
LANALyser.exeon the target machine - As soon you start
LANALyser.exeit will start sending all the information to the linux server
- The linux server will also receive those information
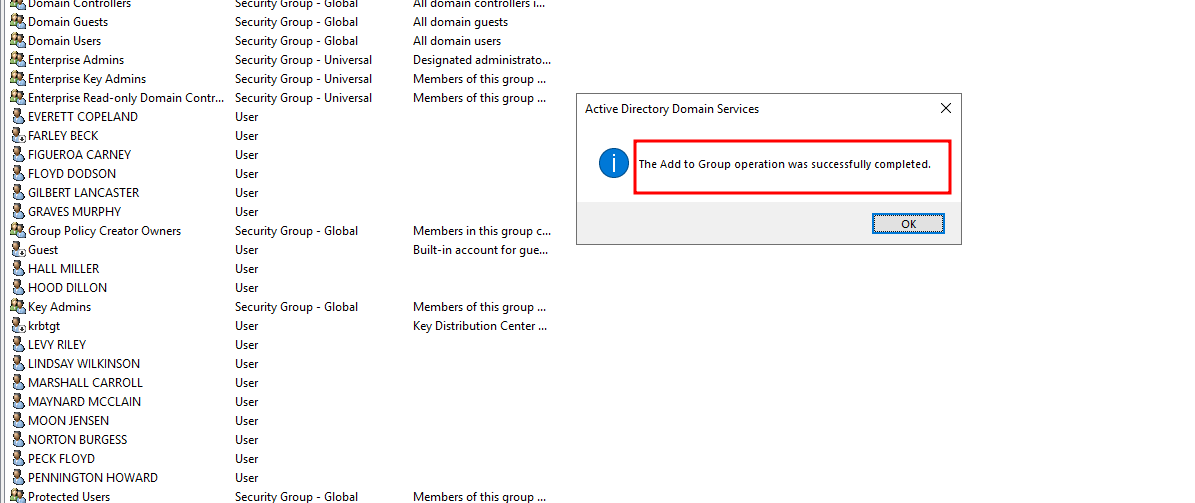
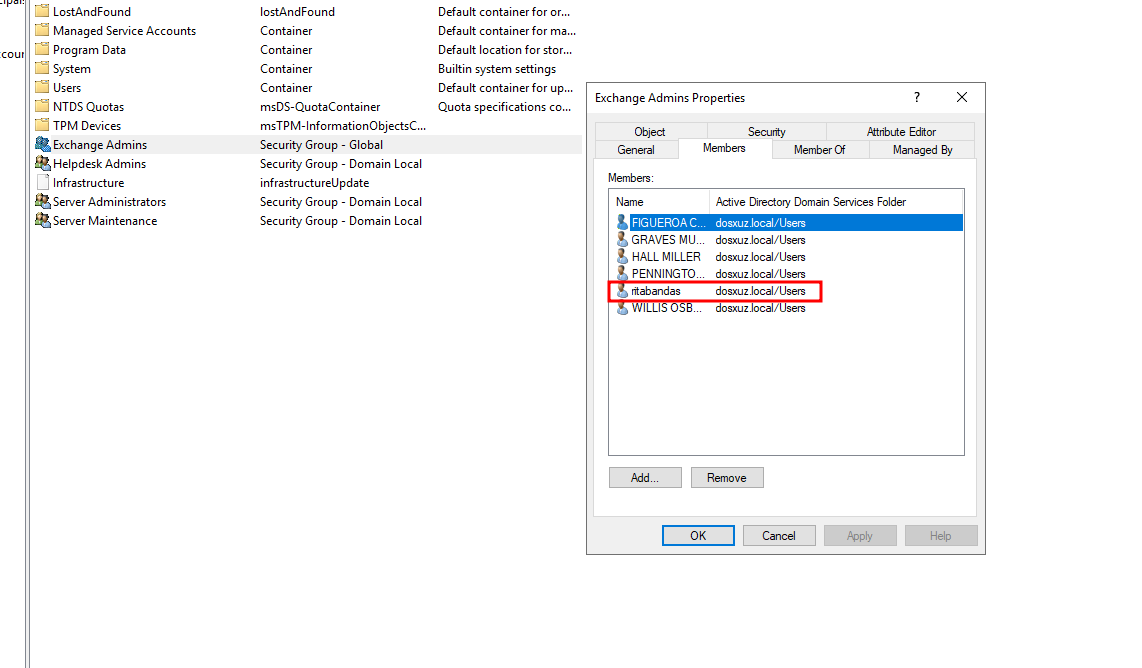
- First we add a different user to the
Exchange Adminsgroup
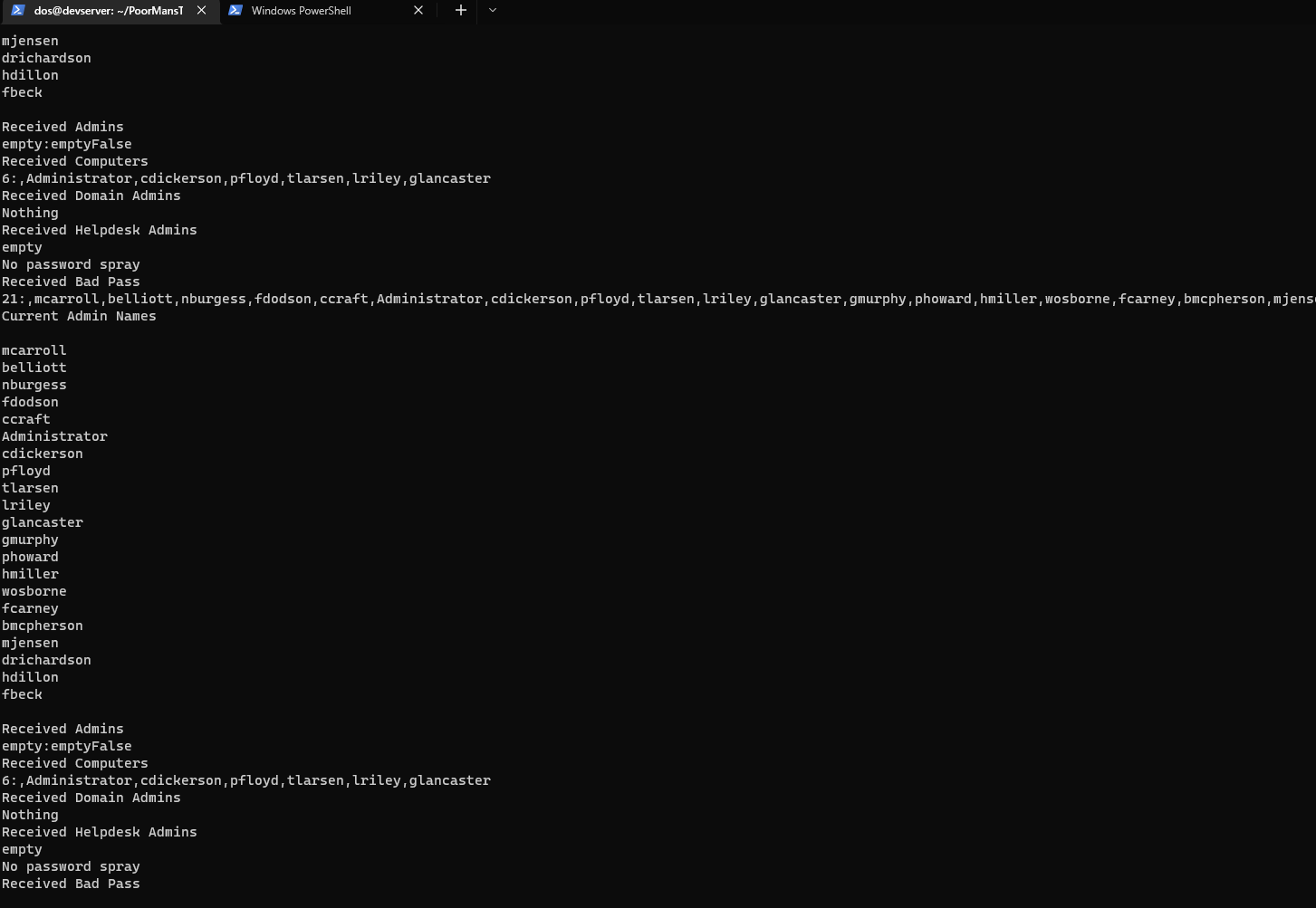
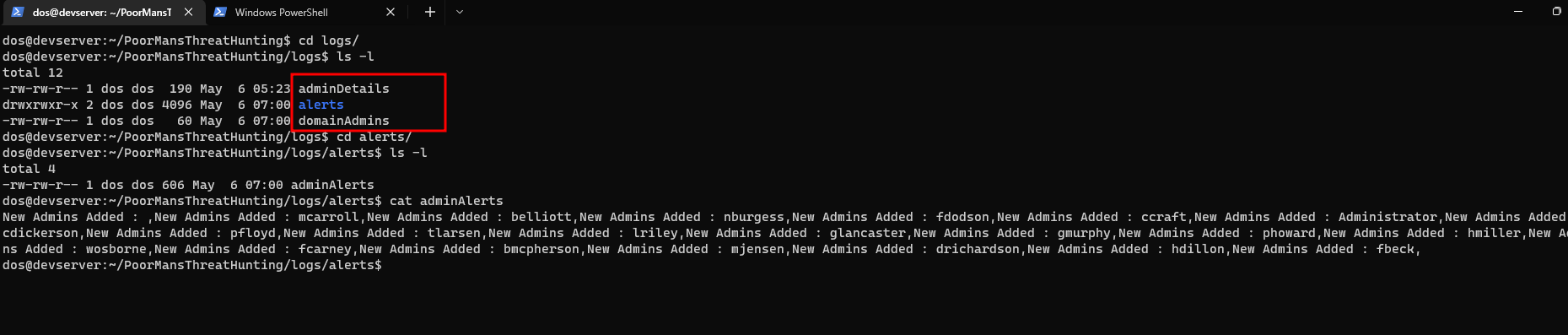
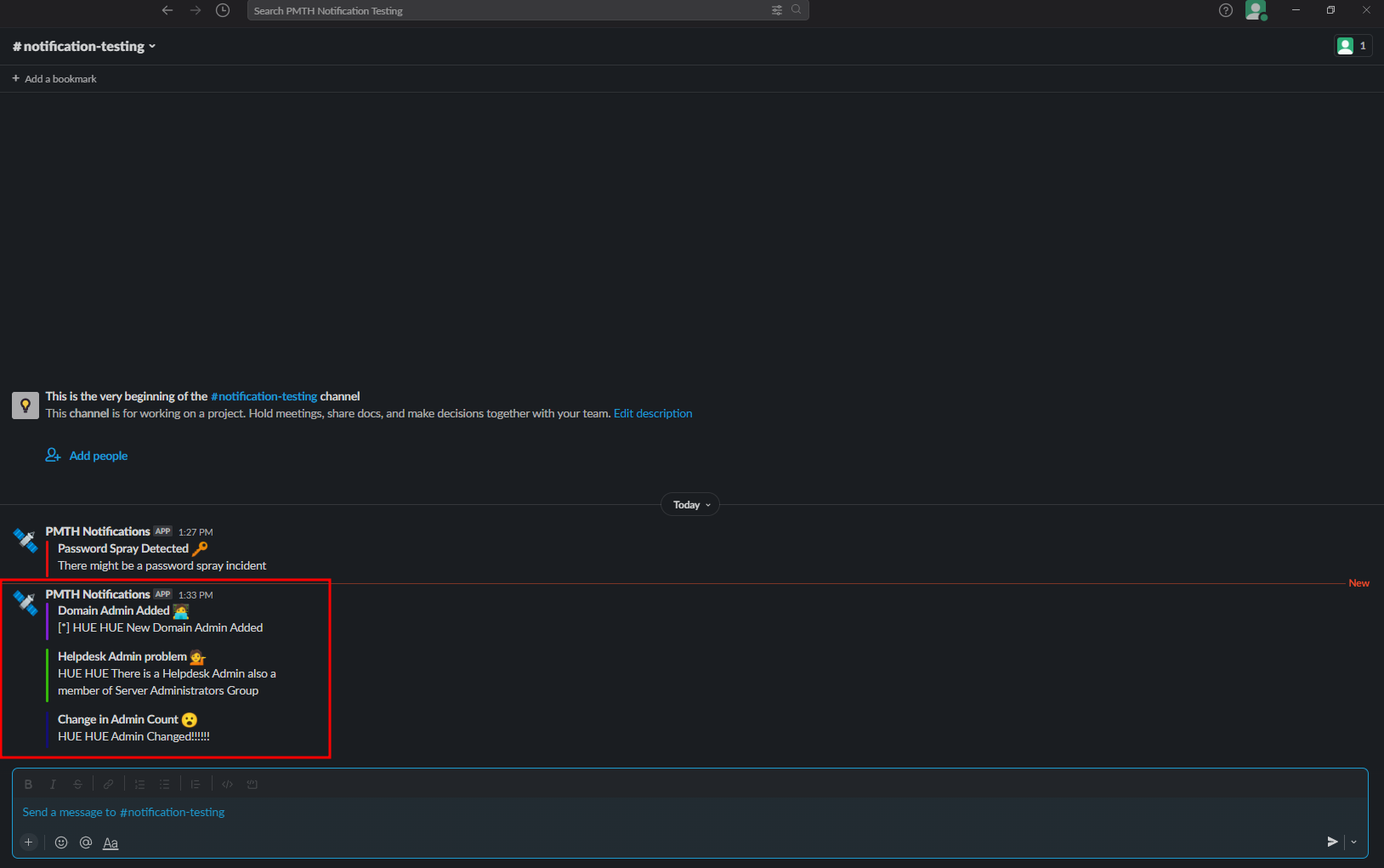
- After that if we check the
logs/alertsfolder there will be a new file calledadminDetails - This will have the name of all the admins that are currently there, including the new admin added
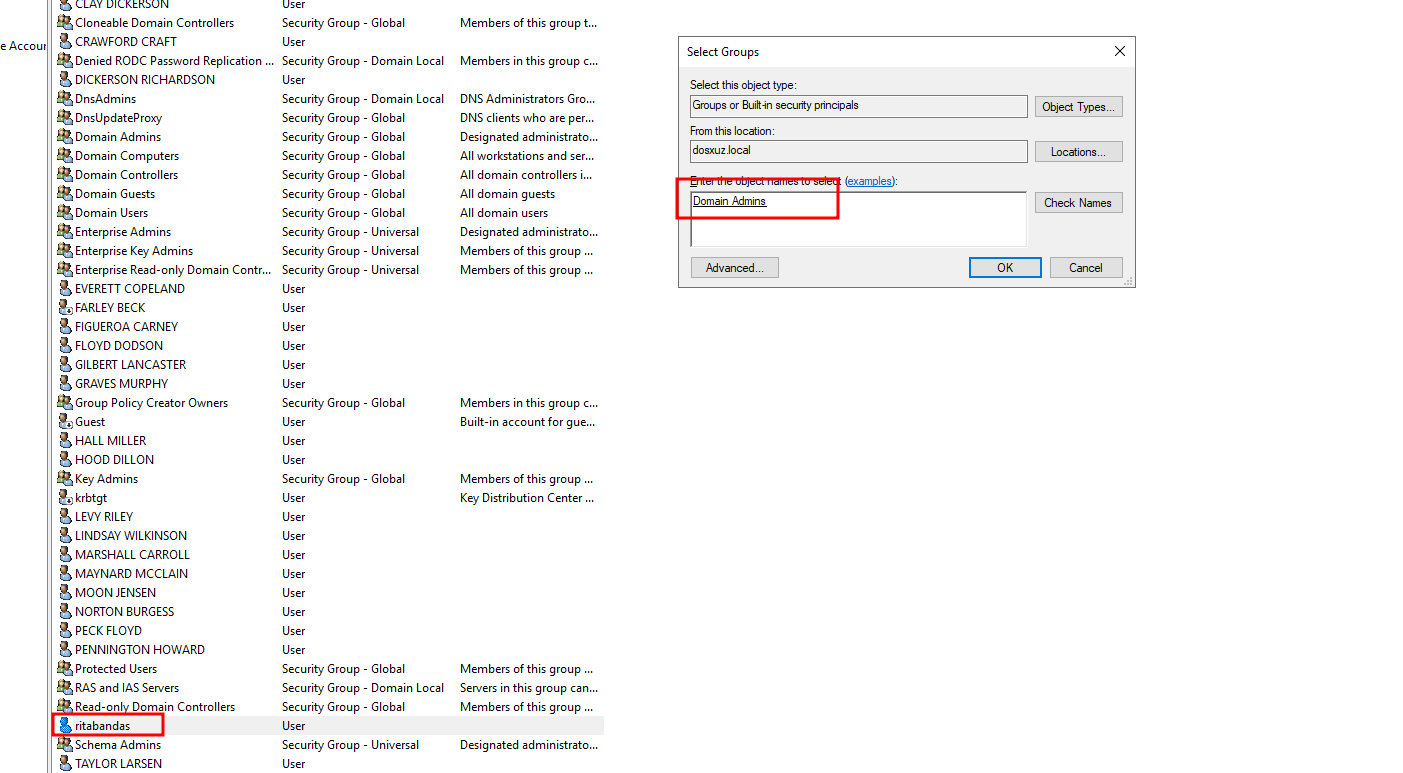
- Add a user to the
Domain Adminsgroup
- We will see that there will be a file
domainAdminsin thelogs/alertsfolder - Along with the file
adminDetailsas there is a change in the number of admins
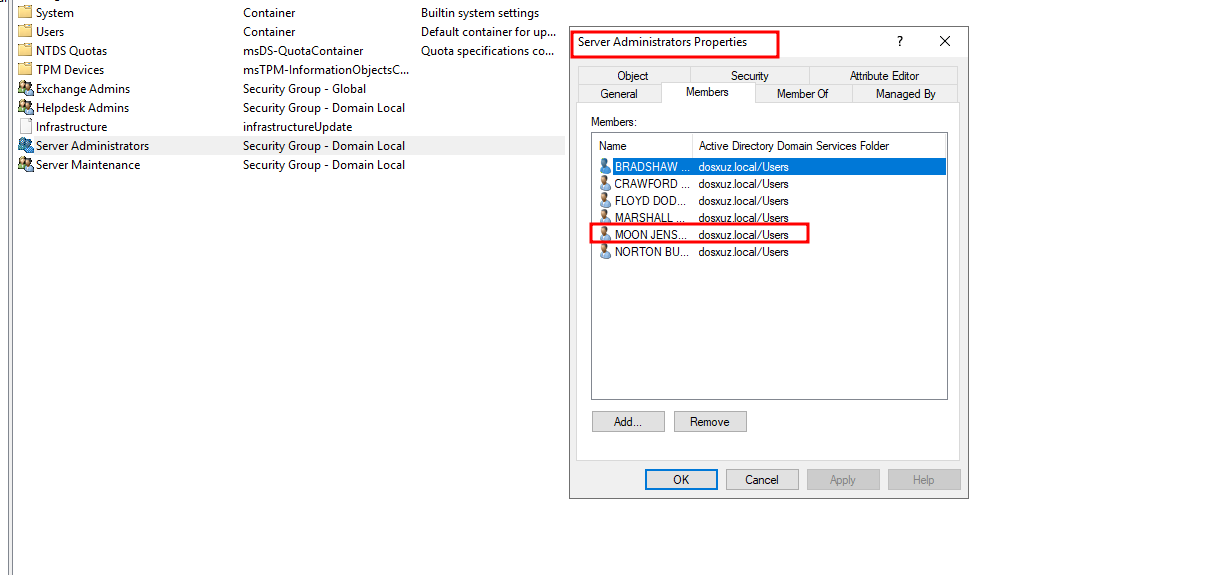
- Add the user a user from the
Helpdesk Adminsgroup to theServer Administratorsgroup
- Here we will add the member
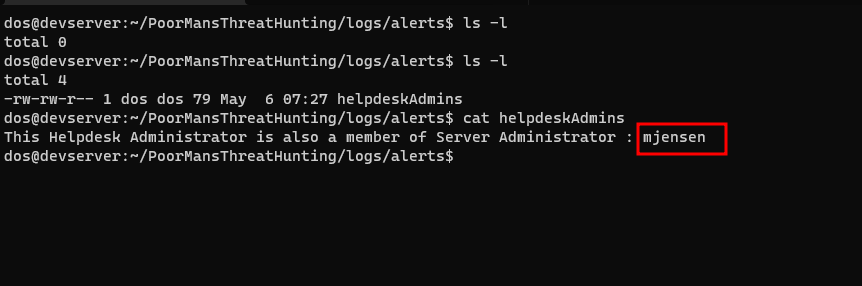
MOON JENSENfrom theHelpdesk Adminsgroup toServer Administratorsgroup
- We will find that there is a file
helpdeskAdminsin the folderlogs/alerts
-
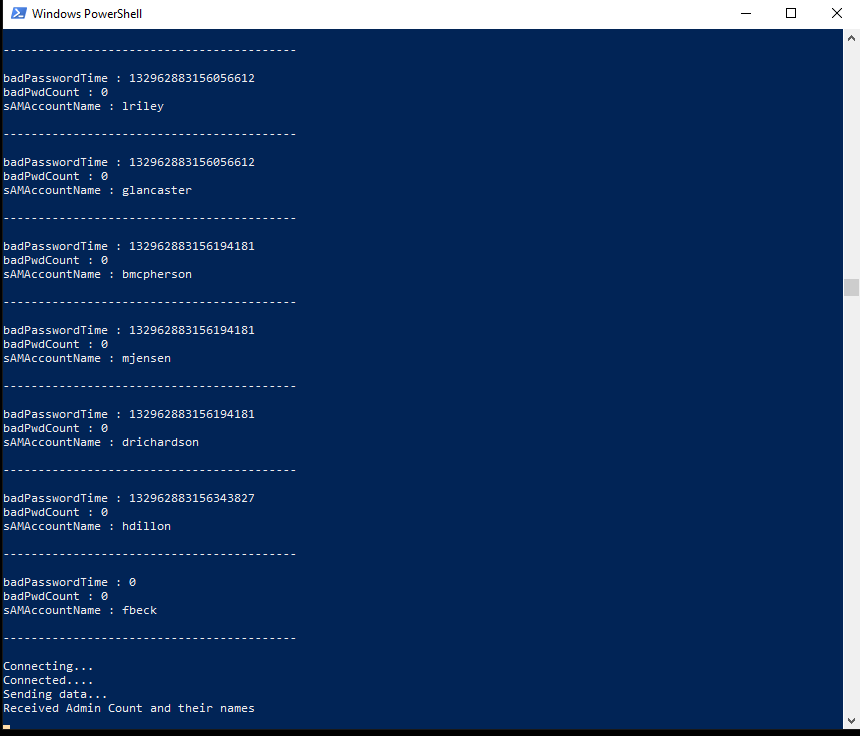
Here the user attributes
badPwdCountandbadPasswordTimeare used to determine whether there has been any attempt at password spraying or not -
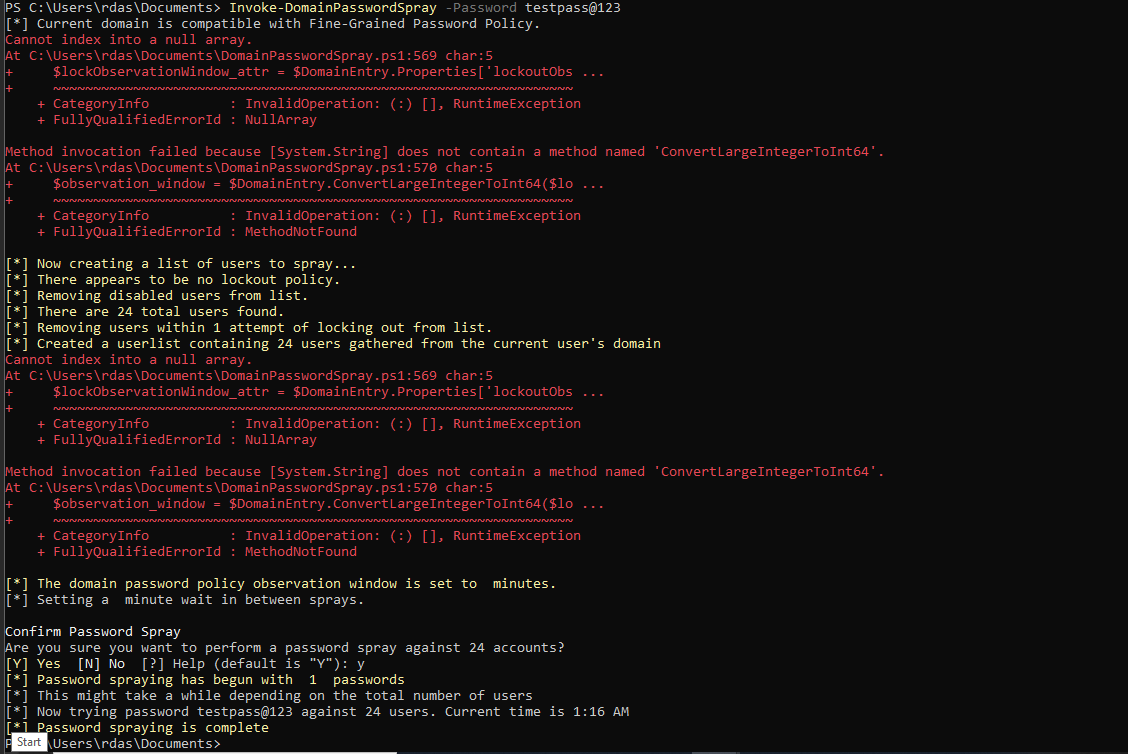
Use the script DomainPasswordSpray.ps1 to password spray against all the user accounts on the domain
-
Login as the domain Administrator
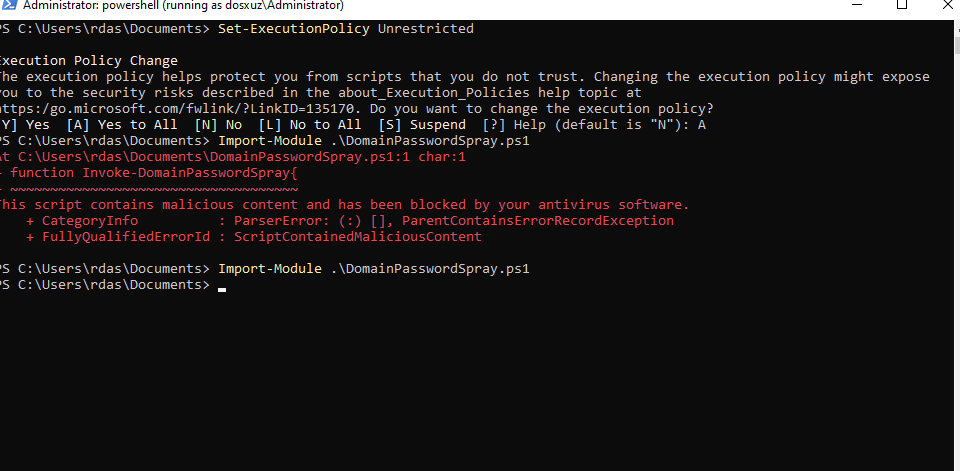
- Set the
Execution PolicytoUnrestricted
- Do turn off Windows Defender, if you're using any public script
- Now import the powershell module
- Execute the function
Invoke-DomainPassowrdSpraywith any password
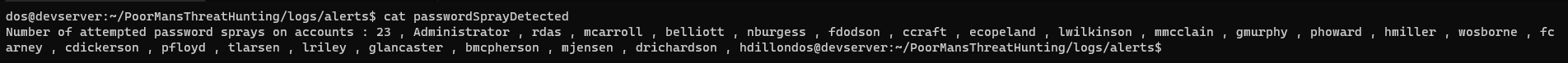
- In the
logs/alertsdirectory, you'll find a file with the details of the password spray - It tells the number of accounts the password spray was performed against
- The
sAMAccountNameof the accounts as well
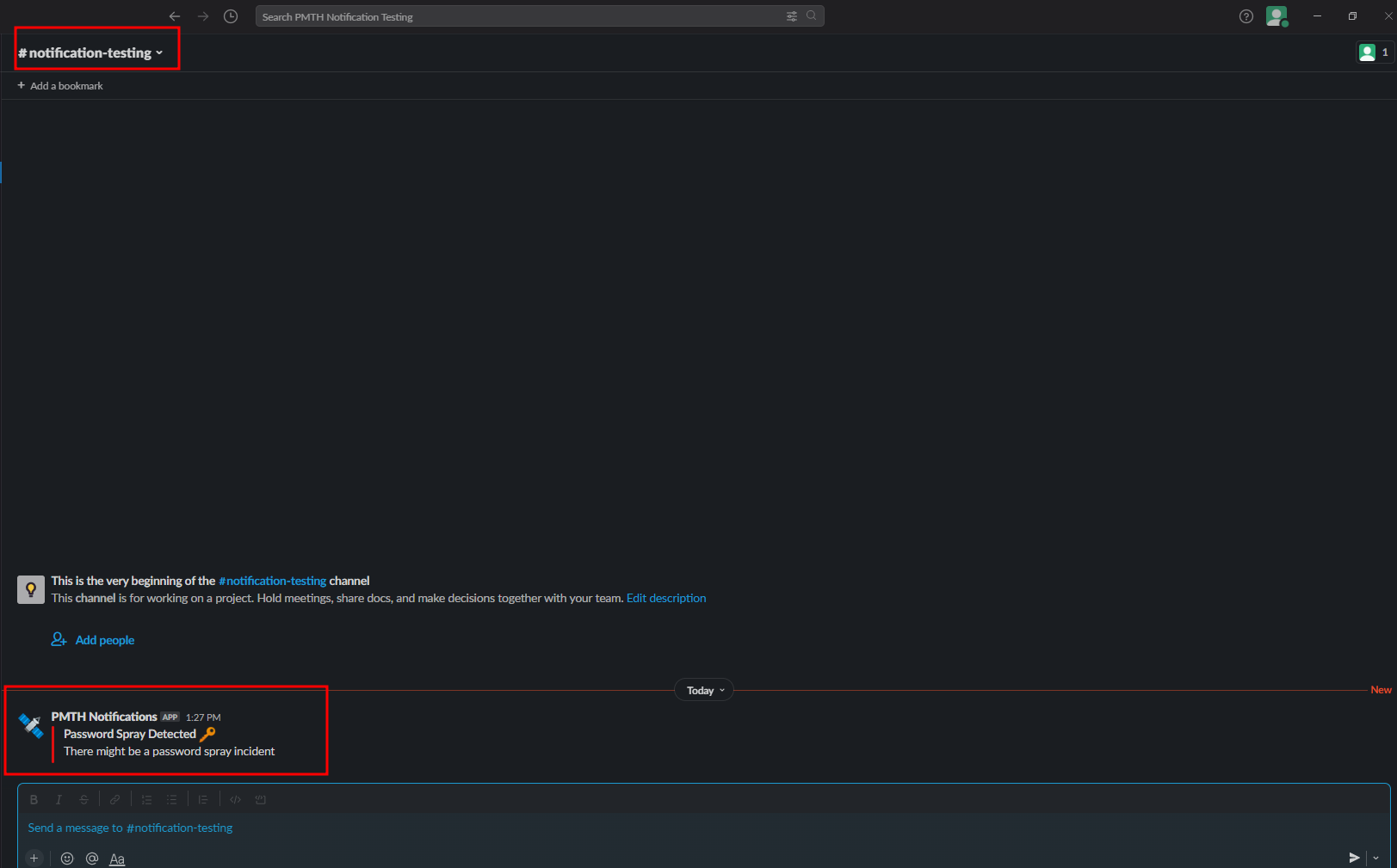
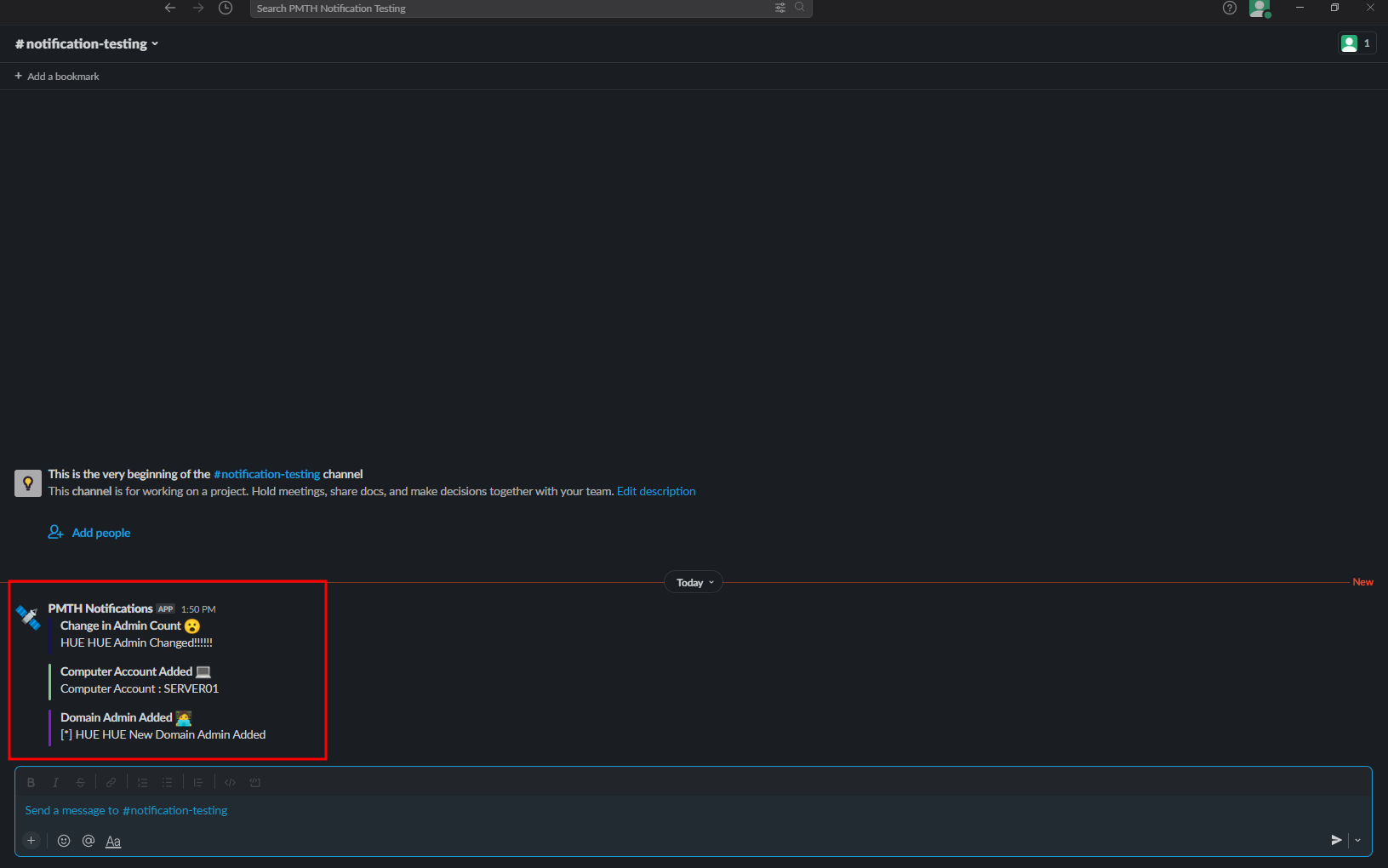
- Now a slack alert will be generated for each of the use cases
- You need to add your own webhook to receive the notification on a particular channel
- Refer to Sending Automated slack messages
Implement Slack/Desktop notification for alerts- Improve the algorithm to detect password sprays, in order reduce the number of false positives
- Improve sync between the server and client
- Fix occasional crashes
- Detect local administrators by parsing the Group Policy
- Prevent counting same admins again