Please go to original repository, https://github.com/sergiomarotco/Network-segmentation-cheat-sheet
Network-segmentation-cheat-sheet contributed by @sergiomarotco and @eltociear
Do not use this repository, you must go to Network-segmentation-cheat-sheet and support them.
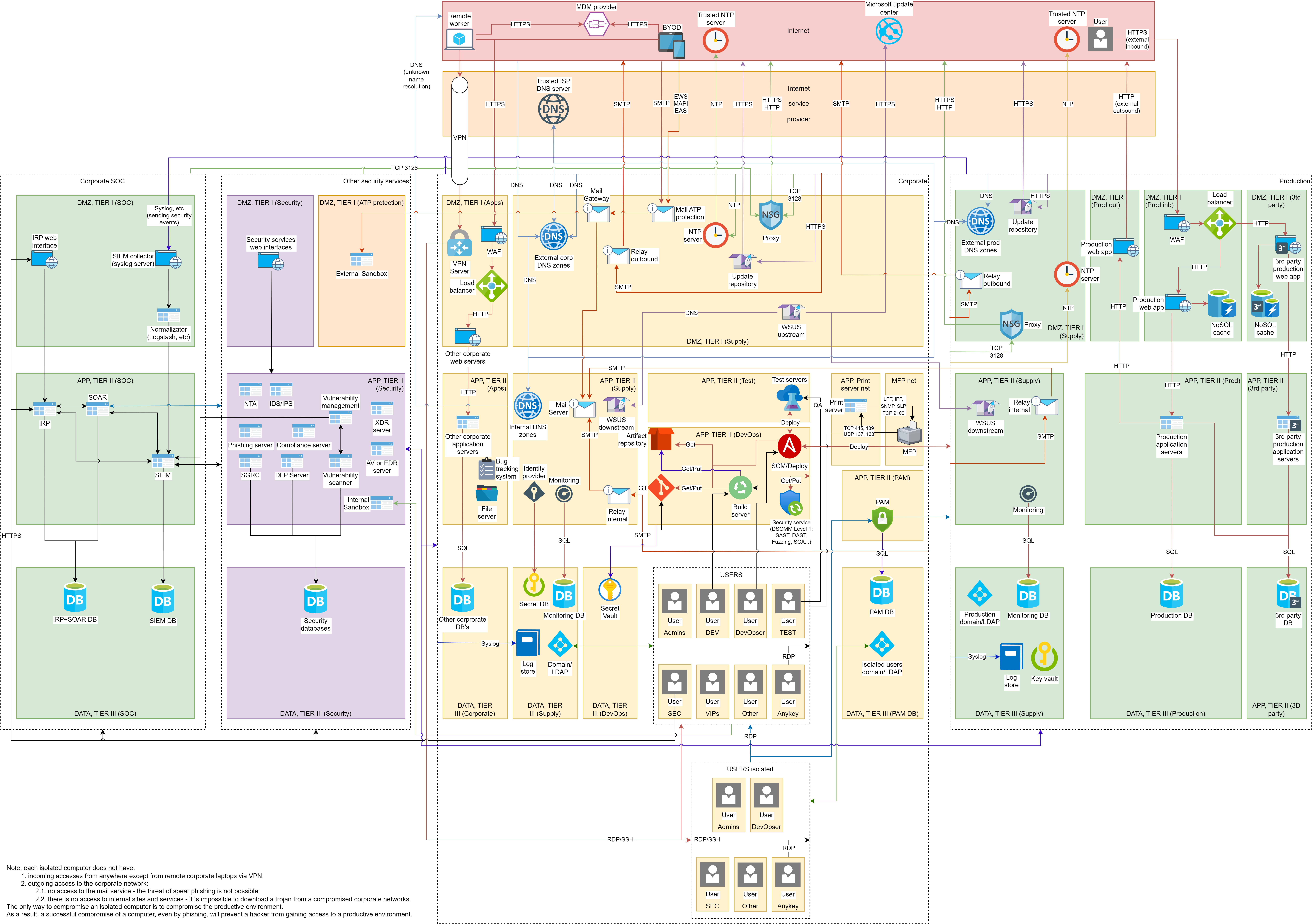
Network segmentation acts as a cornerstone in the architecture of cybersecurity, serving as a proactive measure against unauthorized access and attacks. By dividing a network into distinct segments, organizations can control the flow of traffic, enforce security policies more effectively, and limit the spread of potential threats. Below is a more detailed exploration of the four segmentation levels.
- Graphic diagrams are available in the Release page
- The schema sources are located in the repository
Elements used in network diagrams:

Crossing the border of the rectangle means crossing the firewall.
To further enrich and elaborate on the provided information, let's delve deeper into each level of network segmentation, adding more detailed explanations and clarifications to better understand the significance and implementation nuances of each stage.
| Level | Segmentation | Advantages | Disadvantages | Key Notes |
|---|---|---|---|---|
| Level 1 | Basic Segmentation | - First line of defense against intrusions. - Isolates production from corporate environments. |
- Corporate network's inherent vulnerabilities pose risks. - Potential compromise could lead to broader network access. |
- Emphasizes basic protection and isolation. - Recommends upgrading to higher levels for improved security. |
| Level 2 | Adoption of Basic Security Practices | - More control over network traffic. - Duplication of essential services enhances resilience. - Integrates security in software development. |
- Increased operational complexity and costs. | - Suggests a granular control and resilience approach. - Advocates for security integration in development processes. |
| Level 3 | High Adoption of Security Practices | - Comprehensive security ecosystem. - Cybersecurity becomes a part of company governance. |
- High costs and need for specialized personnel. | - Focuses on establishing a robust security framework. - Stresses on strategic security governance. |
| Level 4 | Advanced Deployment of Security Practices at Scale | - Ultimate security with independent operation of segments. - Effectiveness of air-gapping sensitive environments. |
- Requirement for dual workstations increases physical space and management complexity. | - Represents the pinnacle of security practices. - Dual workstations as a pivotal security measure. |
- Foundation for Security: Establishes the groundwork for more advanced security measures by initially separating critical and non-critical network segments.
- Environmental Isolation: Clearly demarcates the boundary between production and corporate environments, thus minimizing the attack surface accessible to potential intruders.
- Potential Weaknesses: The presence of default network access rights, including administrative privileges from within the corporate segment to the production environment, can be exploited, highlighting the need for more stringent controls.
- Layered Security Measures: Emphasizes the importance of deploying a layered security approach, combining information protection tools with continuous monitoring and rapid incident response capabilities.
- Progression to Higher Segmentation: Acts as a stepping stone towards adopting more comprehensive segmentation strategies, underscoring the necessity for evolving network defenses in response to advanced threats.
- Enhanced Segmentation Benefits: Introduces additional layers of separation within the corporate network, further securing sensitive data and operations.
- Infrastructure Duplication: Ensures business continuity and resilience by duplicating key infrastructure components, thereby safeguarding against disruptions in the supporting systems.
- Resource Intensive: The added complexity and the requirement for duplicate infrastructure significantly increase operational costs and maintenance demands, challenging smaller organizations.
- Comprehensive Security Posture: Marks a strategic pivot towards a holistic security stance, integrating advanced tools and practices such as SIEM systems, DLP strategies, and proactive phishing defenses.
- Organizational Commitment: Reflects a mature understanding of cybersecurity's critical role, supported by a dedicated and sufficiently staffed information security unit.
- Investment Implications: The significant financial and human resource investments required for this level of security can be prohibitive, especially for entities with limited budgets.
- Air-Gap Strategy: Embraces the pinnacle of isolation techniques, effectively neutralizing the threat of external attacks through strict access controls and physical separation.
- Targeted Security Enhancements: Focuses on fortifying the production environment with specialized security services and training, including sophisticated access management and compliance monitoring.
- Dual Workstation Deployment: While significantly enhancing security, the requirement for multiple workstations introduces logistical and space considerations.