Deployment of Zero Trust, persona-based Azure AD Conditional Access Policies via Microsoft Graph, utilizing PowerShell.
Based upon the excellent Microsoft Learn: Conditional Access architecture and personas and Framework and policies pages authored by Claus Jespersen.
PowerShell SDK for Microsoft Graph
Install-Module Microsoft.Graph -AllowClobber -ForceOptionally, also install:
Install-Module Microsoft.Graph.Beta -AllowClobber -ForceConditional Access Policies as code deployed via the PowerShell SDK for Microsoft Graph.
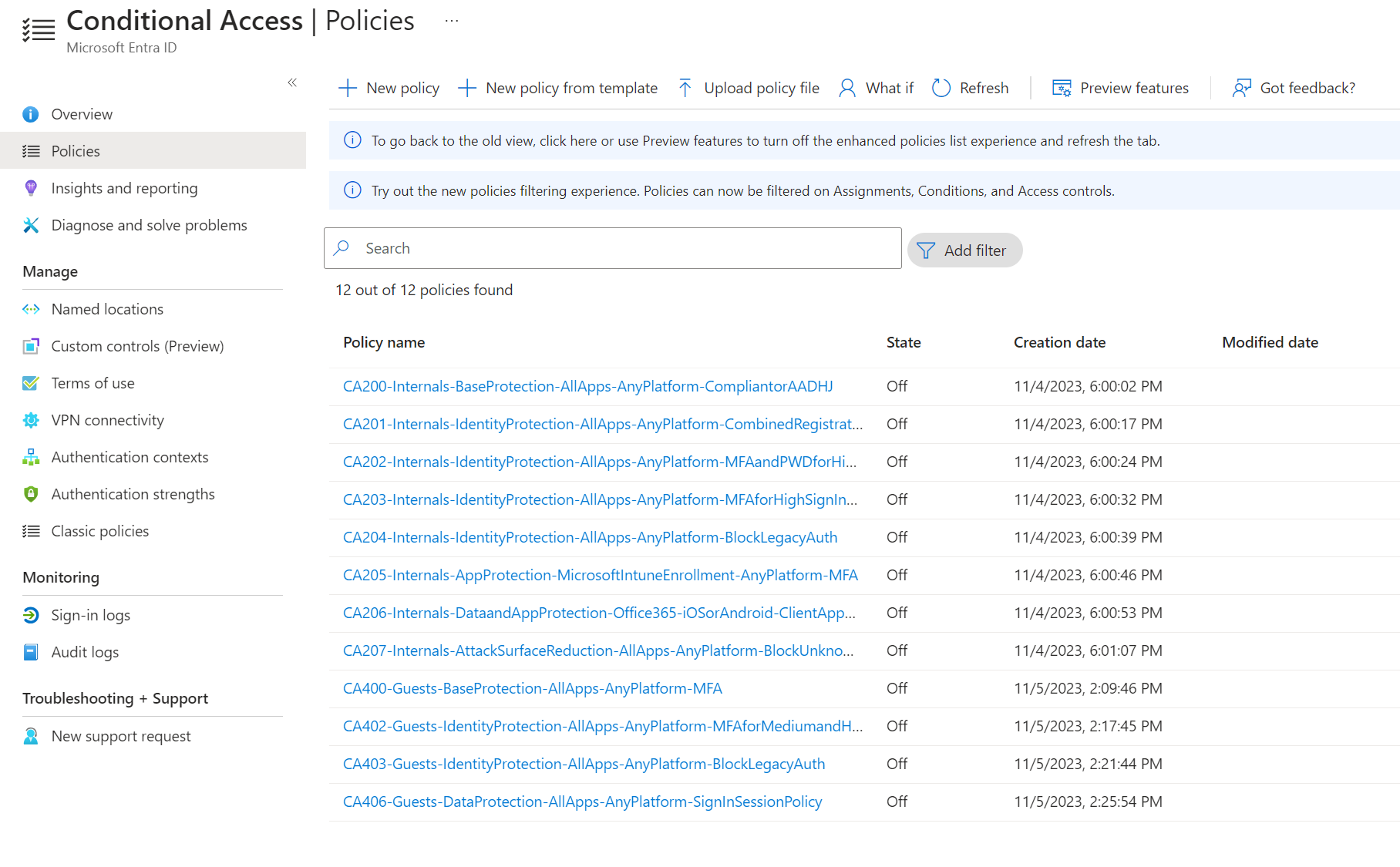
Policies can be deployed in any order and will be 'Off' by default.
Persona groups will be created if they do not already exist.
This collection is a work in progress.
Internals require a Compliant or Domain-Joined Device.
Internals performing Security registration (ie. MFA enrollment) require a Compliant or Domain-Joined Device.
Internals with High User Risk must perform MFA and change their password.
Internals with High Sign-In Risk must perform MFA.
Internals are blocked from Legacy Authentication methods.
Internals must perform MFA to enroll a device.
Internals accessing Office 365 from iOS or Android must use an Approved App or an App Protection Policy.
Internals on unknown platforms are blocked.
Guests must perform MFA.
Guests with Medium or High Risk must always perform MFA.
Guests are blocked from Legacy Authentication methods.
Guests have a limited Sign-In Session.
Workload Identities in untrusted locations are blocked.
Workload Identities with High Risk are blocked.