- Website: https://www.leapp.cloud/
- Roadmap: Roadmap
- Wiki: Wiki
- Chat with us: Discord
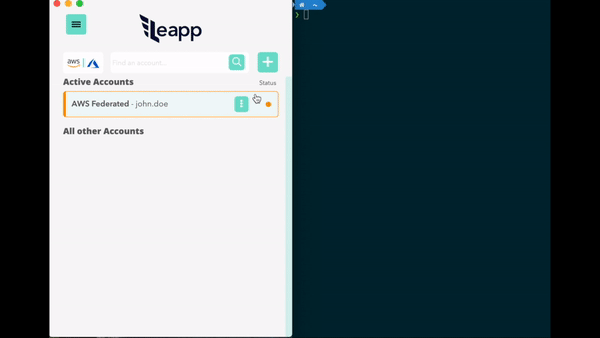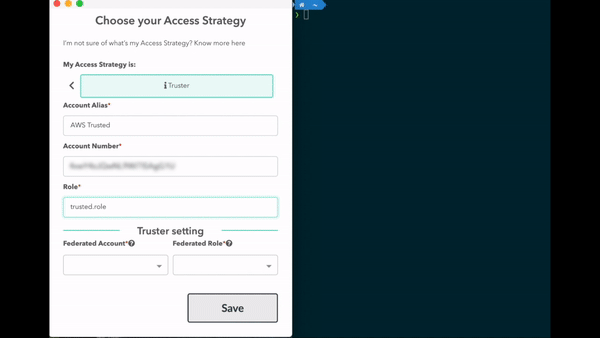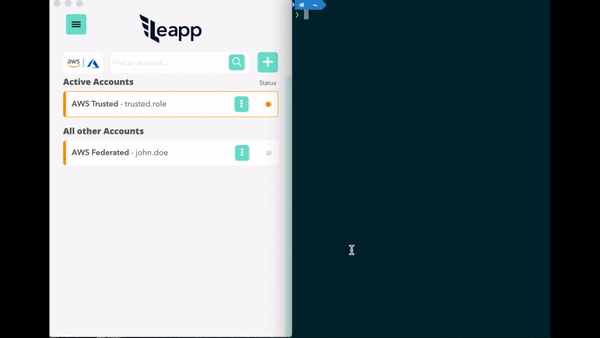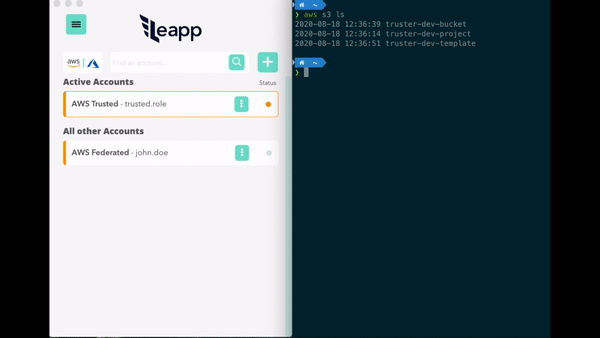
Leapp is a DevTool Desktop App designed to manage and secure Cloud Access in multi-account environments.
The App is designed to work with Cloud Providers APIs, CLIs, and SDKs.
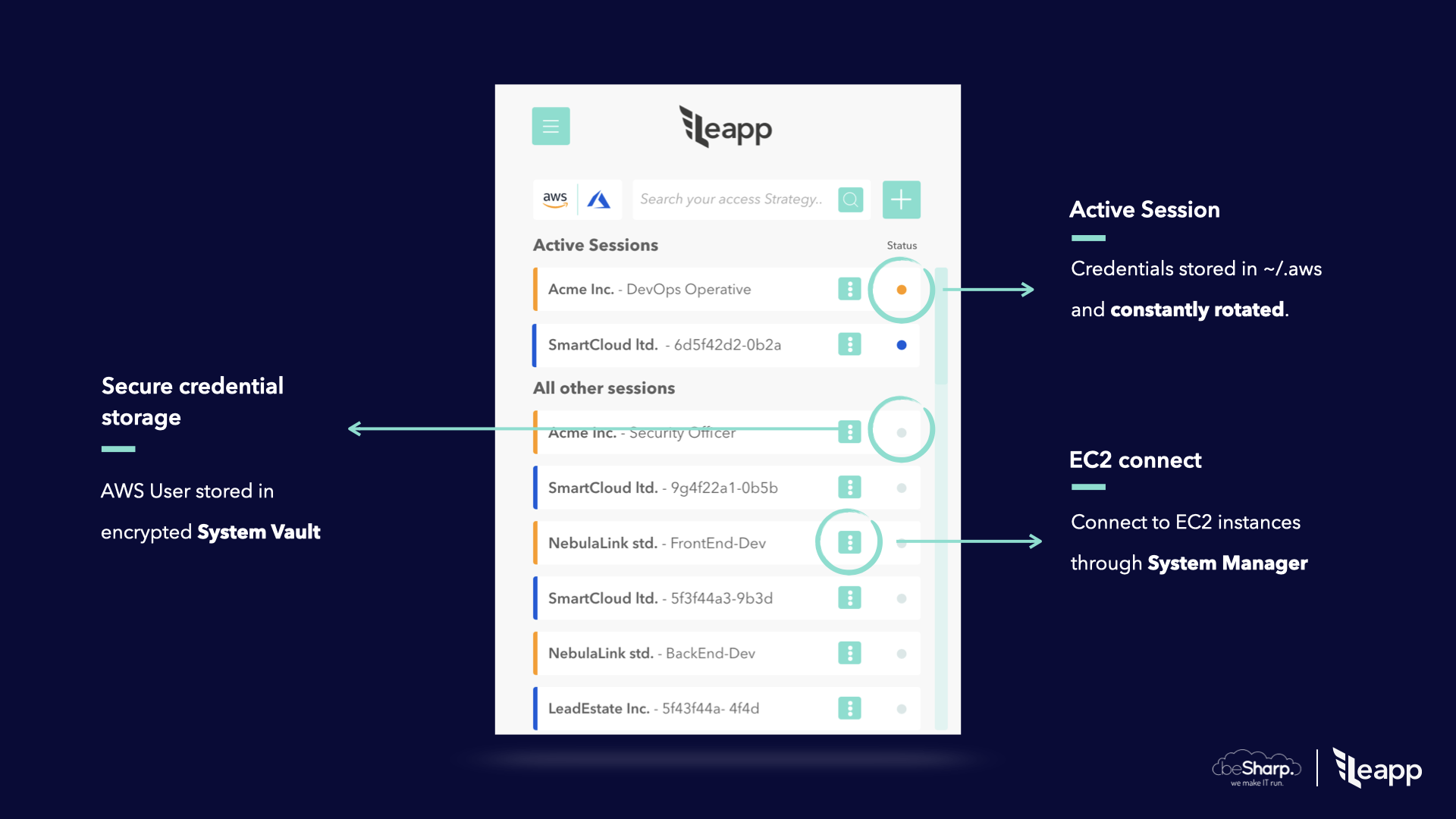
It's a tool that securely stores your access information in a secure place and generates temporary credential sets to access your Cloud from your local machine.
We Strongly believe that access information to Cloud in
~/.awsor~/.azurefiles are not safe, and we prefer to store that information in an encrypted file managed by the system. Credentials will be hourly rotated and accessible in those files only when they are needed, so only when Leapp is active.
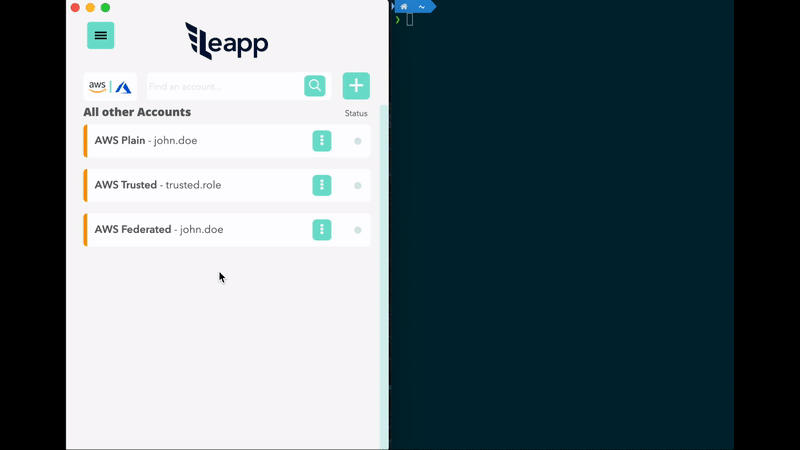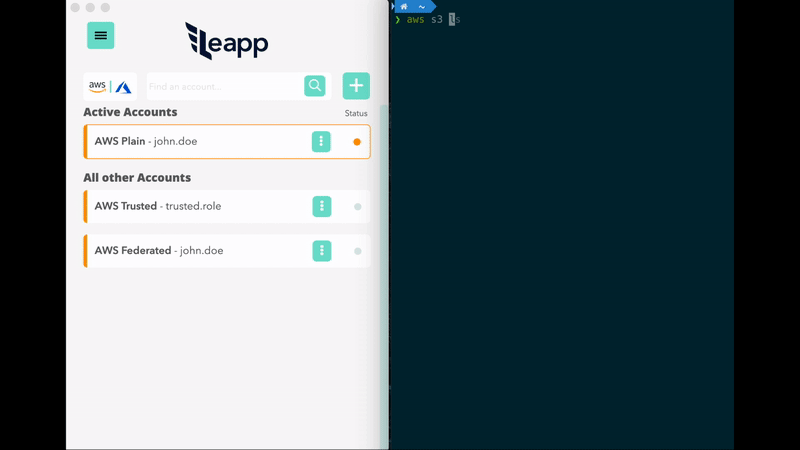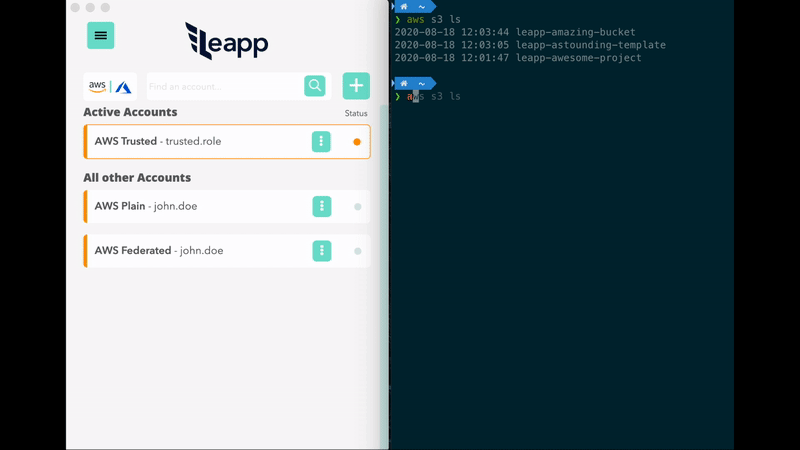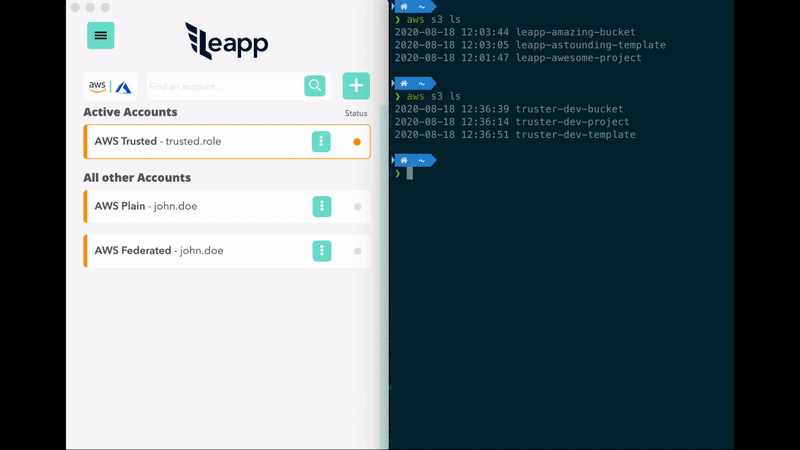
- No need to manage the credentials file. Get connected to your accounts in a click.
- Protect your cloud accounts access data in the system vault and connect straight away.
- Connect with federated single sign-on, roles or static credentials.
- Generate and inject only temporary credentials to comply with security best-practices.
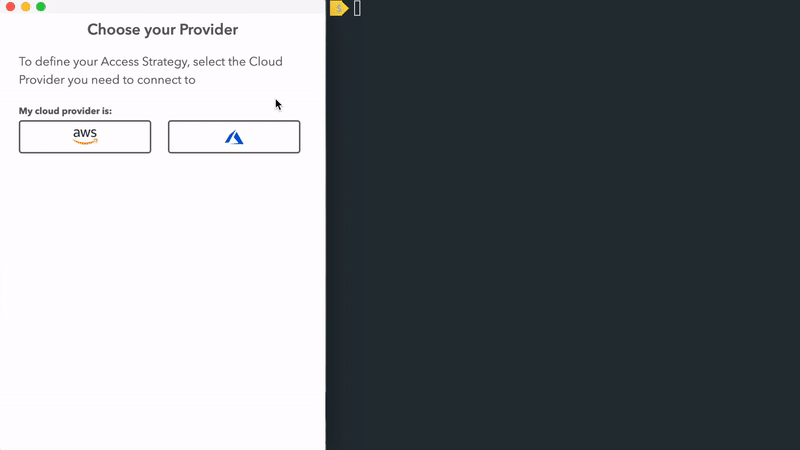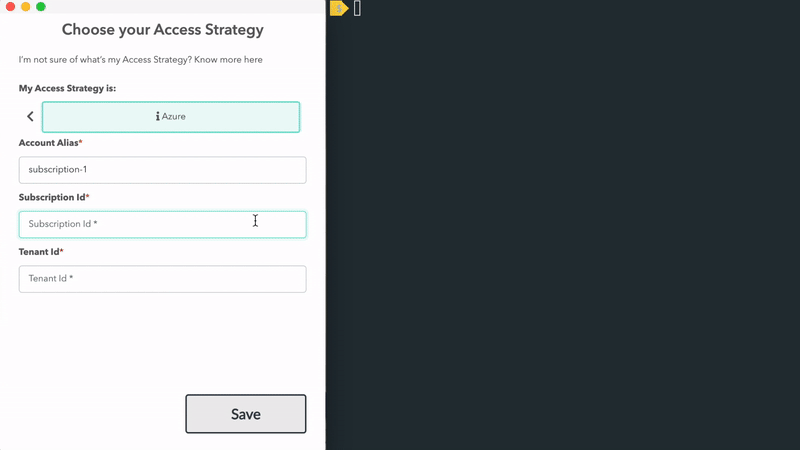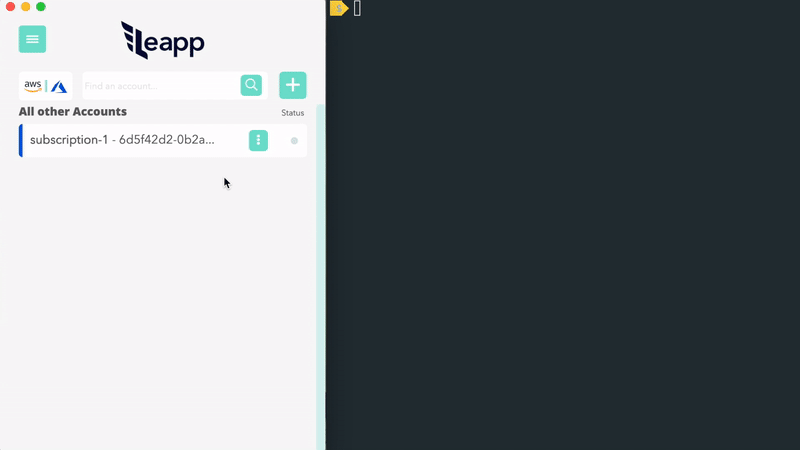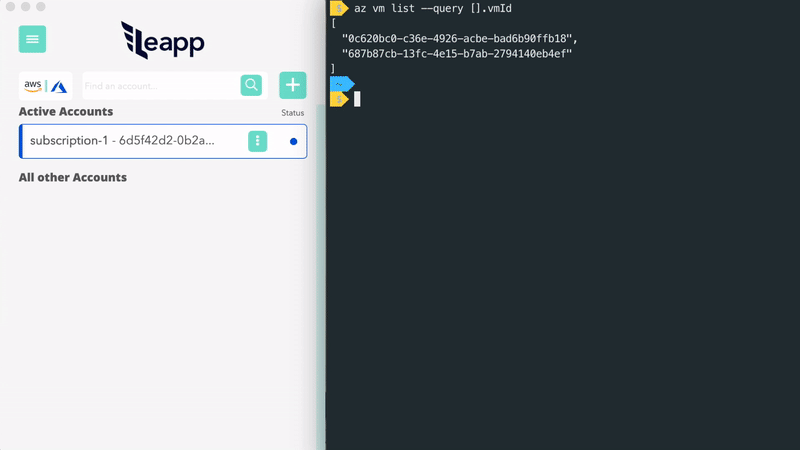
- Access to multiple AWS accounts with AWS single sign-on access.
- Connect to your EC2 Instances with AWS System Manager.
Get here the latest release.
Our use cases are hereby presented to give you a hint on how Leapp can be of help to depend on the type of setup you have in your company and what kind of credentials you need to get.
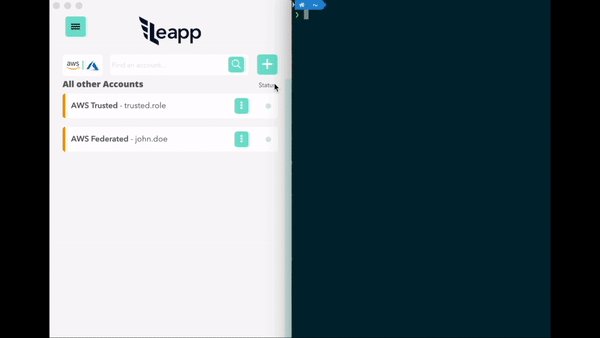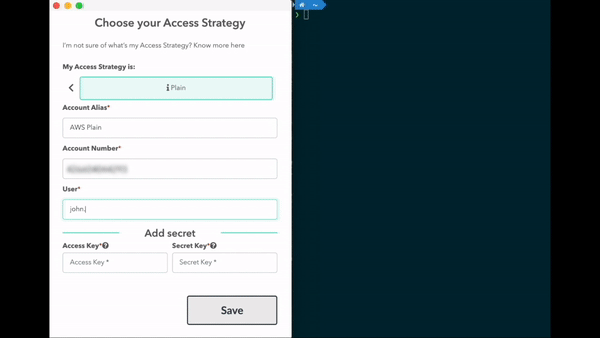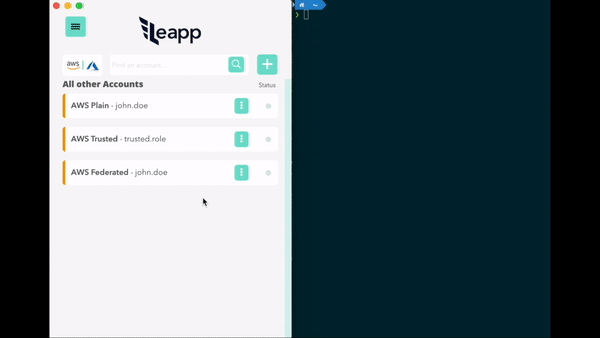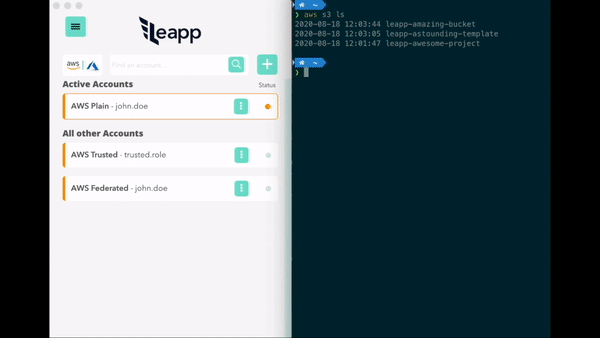
Store AWS IAM User's Access Keys in your System Vault through Leapp. Leapp automatically manages Access Key ID and Secret Access Key in your AWS credentials, generating temporary credentials for them.
No credentials are stored in Leapp.
Please see Vault strategy for more information.
See setup tutorial
Note: it's possible to assign an MFA device to a plain session. Please see MFA section for more details.
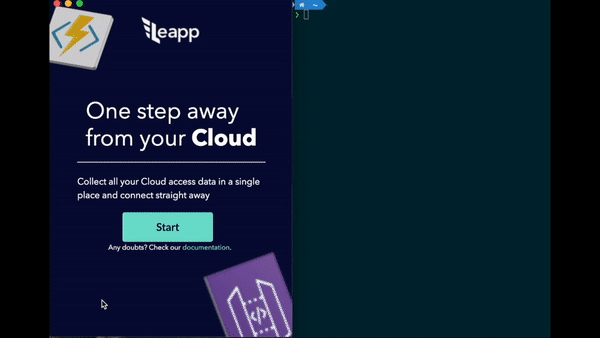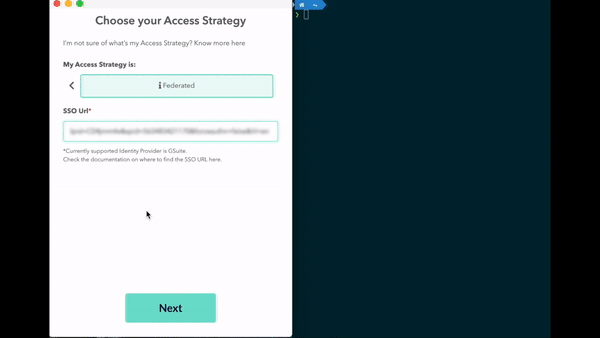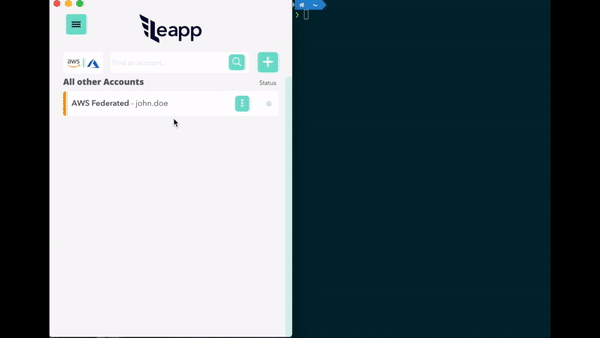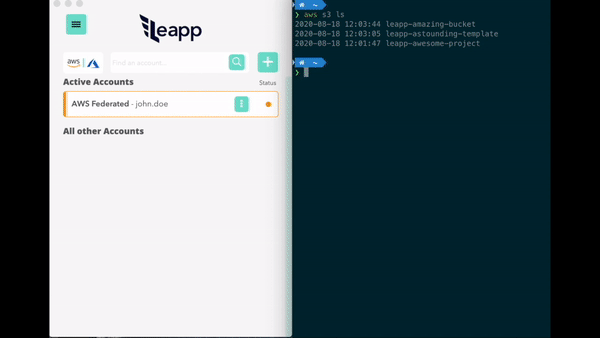
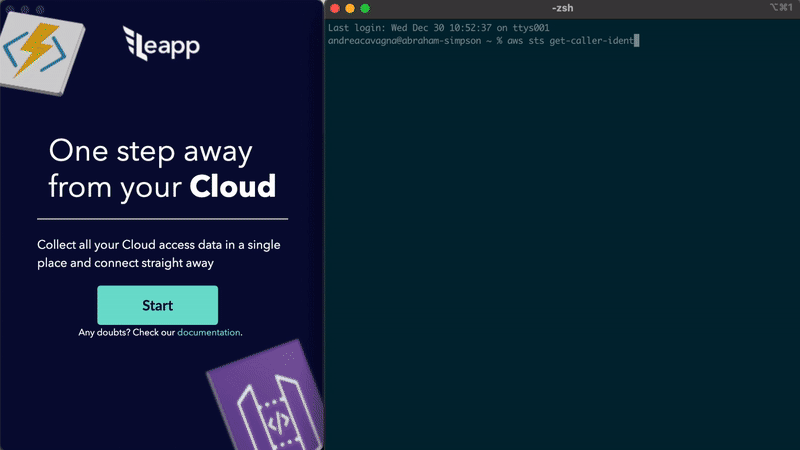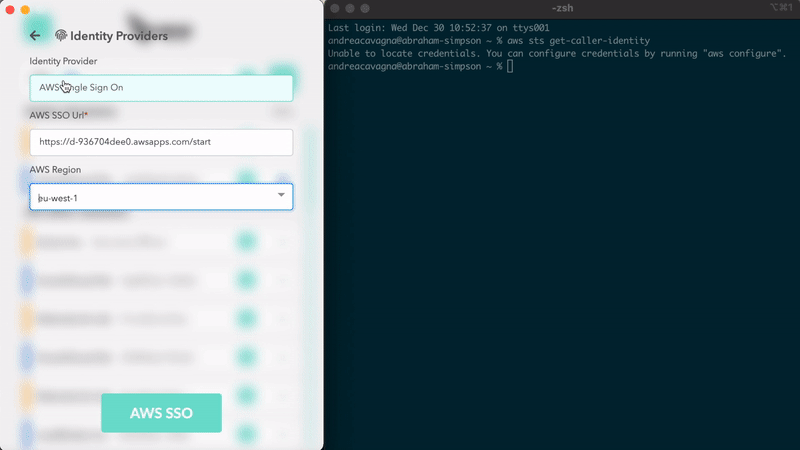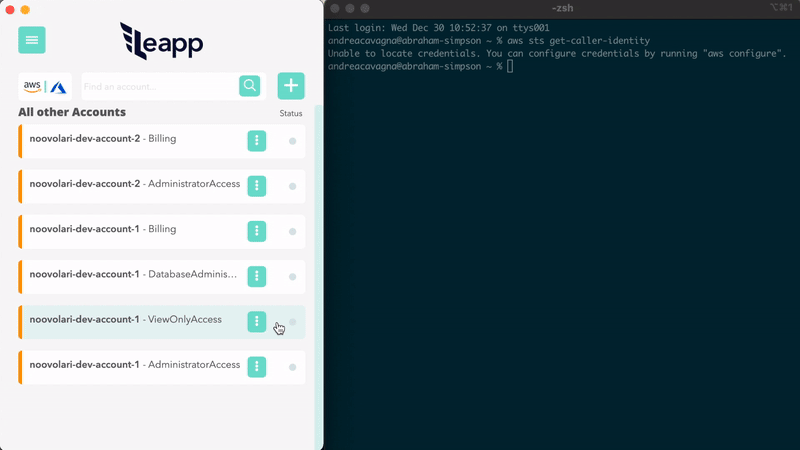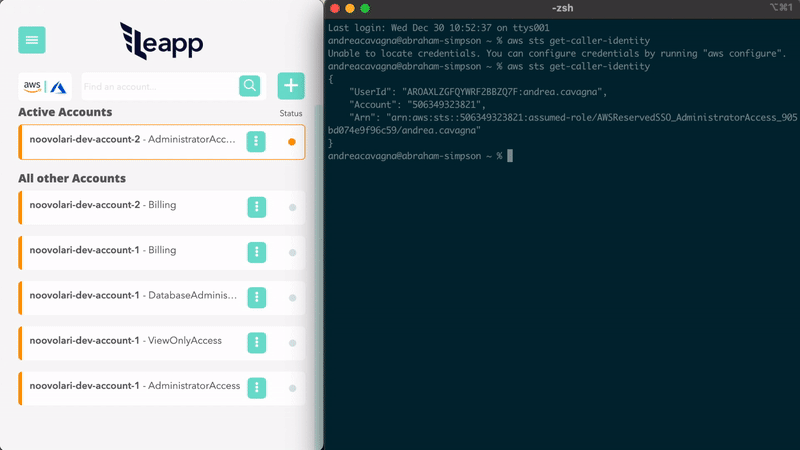
Federation is established between G Suite and AWS. No more AWS credentials management is needed. Leapp allows you to get to cloud resources with company email and password.
See setup tutorial
Access to your AWS Accounts through Leapp and let the App manage all the available session to generate Temporary Access and Secret keys.
See setup tutorial
Access to an Aws Account Role via another AWS Account role or an IAM user, thanks to a cross-account role available via STS. In this access strategy a Truster Role or a Plain User is assumed by a federated role.
See setup tutorial
Note: it's possible to apply MFA to a truster session by setting it on the plain account it relies on. Please see MFA section for more details.
Use Leapp to do Single Sign On with G Suite on Azure to get access to your Subscriptions. In this use case is mandatory to have defined a Federation between Google and Azure. Leapp manage the login process for you to have Azure CLI ready to be used.
See setup tutorial
- AWS - ✅
- AZURE - ✅
- GCP - 🔜
- G Suite to AWS - ✅
- G Suite to Azure - ✅
- AZURE AD to Azure - ✅
- AZURE AD to AWS - 🔜
- AWS Single Sign-On - ✅
By default, Leapp writes logs to the following locations:
- on Linux:
~/.config/Leapp/logs/log.log - on macOS:
~/Library/Logs/Leapp/log.log - on Windows:
%USERPROFILE%\\AppData\\Roaming\\Leapp\\log.logLogs are structured in the following way:
[YYYY-MM-DD HH:mm:ss.mmm] [LEVEL] [rendered/system] [COMPONENT] MESSAGE {Useful Object / Stacktrace Err Object}
Note: please always add logs whenever possible to any issue you want to fill to enable the team identify the problem quickly
Here you can find our documentation.
- Glossary: find other information about the system
- Roadmap: view our next steps and stay up to date
- Contributing: follow the guidelines if you'd like to contribute to the project
- Project Structure: check how we structured the project and where to find the files