We want to create a repository which can provide different "Malwares" (or program which can simulate the malware's action ) which are written by Python, the malwares will content phishing email generator, backdoor trojan, screen freezer, key logger, malware process watchdog protector, DDoS attacker, traffic data blocker / replacer , password cracker and so on for below purposes :
- Education for any level of cyber security course about malware / program harmful action or the related course lab assignment / demo.
- Training for company employees, semi-professionals such as the workshop about the cyber attack and defense.
- Development or cluster management for cluster admin to remote manage cloud computing infra (with out using credentials ) such as do program hot update or software deployment.
- Testing for the security solution program / malware detection program to detect the malware.
- Research in cluster network unusual/exception traffic detection, trojan detection, risk respond, penetration action detection.
[TOC]
Most the malwares in this repository are implemented by python and C, some program need to work together with attack tool / software. The cyber attack vectors [8] and the malicious action [18] we provide are :
| Idx | Attack Vector | Malicious action |
|---|---|---|
| 1 | Compromised Credentials | File stolen, critical data leakage/capture, history scanning, keyboard input logging, screen shot capture, browser cookie archiving. |
| 2 | Weak Credentials | Password dictionary crack attack ( zip file ) |
| 3 | Phishing | Phishing email generation, scam email generation. |
| 4 | Brute Force | Web account login brute force crack and takeover. |
| 5 | Distributed Denial of Service | DDoS attack on web, OT-system(PLC), different service ( such as email server ). |
| 6 | Trojans | Backdoor trojan, spy trojan |
| 7 | Man-in-the-Middle Attacks | Arp spoofing , traffic block , packets drop, packets data replacement. |
| 8 | Insider threats | Malware camouflage, Malicious(code/program) inject, device I/O Compromise (mouse, keyboard, screen frozen), malware process protection watchdog. |
The malware programs currently we provide ( configurable via ansible and deploy to env ) are :
- Backdoor Trojan system : A backdoor trojan system which contents a watch dog protected backdoor trojan, a peer to peer single trojan controller and a multiple trojans control hub system.
- DDoS Attacker : A DDoS attack management system can plug different client to launch DDoS attack.
- Program/Malware Watchdog : robust watchdog program designed to bind to target programs, diligently monitor their execution states, and ensure uninterrupted functionality.
- Phishing email sending : Use GPT3.5 generate email (normal email contents) then bind different phishing malware as attachment and link.
- Password cracker : Auto brute force break a password protected zip file or a web login with only user name and password. Use AI to split the dictionary to human generated password and the machine generated password to increate the cracking speed.
Next develop:
- Ransomware system (ransomware + payment web)
- Use AI to build the normal user time line.
- Password cracker : Search the real user (prompt) from internet based on the user name, then use AI to filter and get the password with high possibility ( such us birthday match, children name ) .
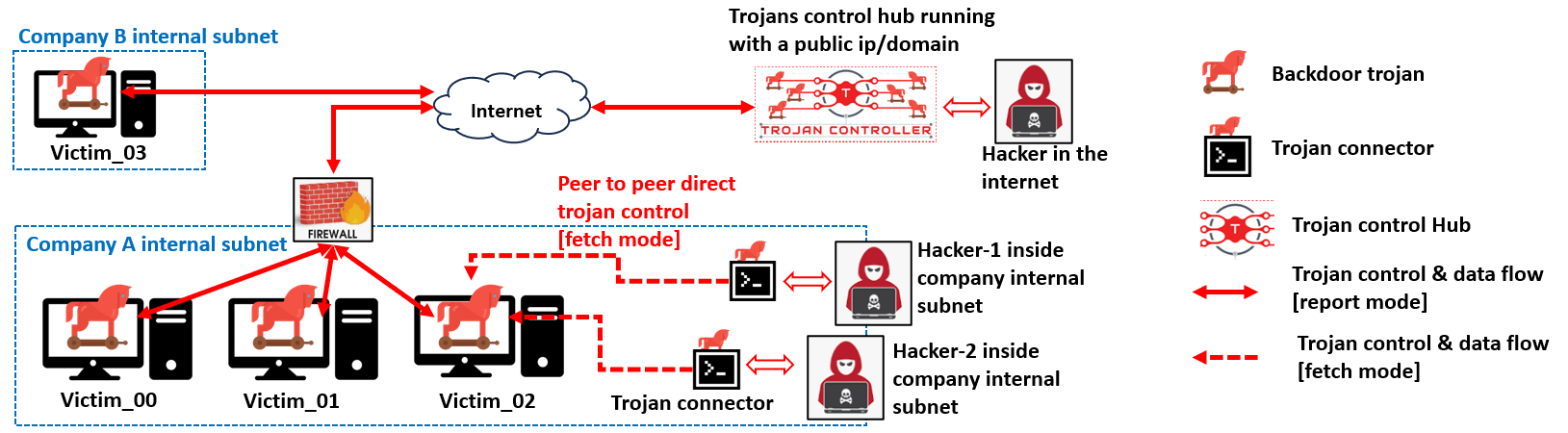
The Trojan system contents 3 main programs:
- One Backdoor Trojan program running on victim open a backdoor to allow hacker to remote run commands, steal credential files, do harmful action to the host computer or insert other malware into a host without authorization.
- One P2P Trojan Connector which is a console based peer to peer direct trojan remote connector for hacker used to remote control one of the backdoor trojan to do the harmful action such as rename all user's file, full fill user's home folder with garbage files. It allows multiple hackers to control one trojan at the same time.
- One Trojans Controller Hub which is a UI based trojan management hub used for hacker to manage multiple trojan in different victim host or batch launch attack such as clear all files in every victim computer's home folder. It allows one hacker control multiple trojans at the same time.
The workflow between the backdoor trojan and trojan controller is shown below:
To use the backdoor trojan, please refer to this document: link to the backdoor trojan usage document
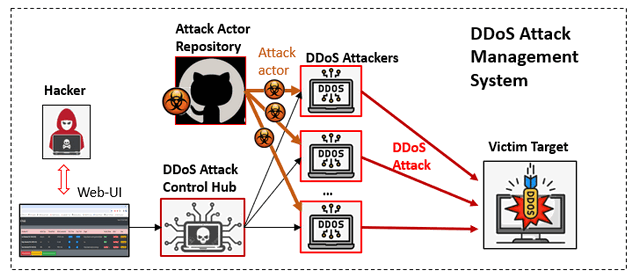
The DDoS attacker system contents 3 main parts :
- The DDoS Attacker program is running on single nodes with a attack thread pool to start several hundreds of parallel threads to implement the attack at the same time based on the user's config. Currently we provide 10 different categories service attack actors and user can also easily plug their customized attack program in the attacker.
- The DDoS Attack Actors Repository contents several attack actors to send different kinds of network request (such SSH, https-GET, https-POST, SMB login...) to the target. Each attack actor object will be assembled in a attack thread and put in to the attack pool of the related DDoS attacker.
- The DDos Control Hub is used to link all the DDoS attackers together so the user can monitor the current attack state and control each DDoS attacker via the hub's web interface.
To use the DDoS Attacker, please refer to this document: link to the DDoS Attacker usage document
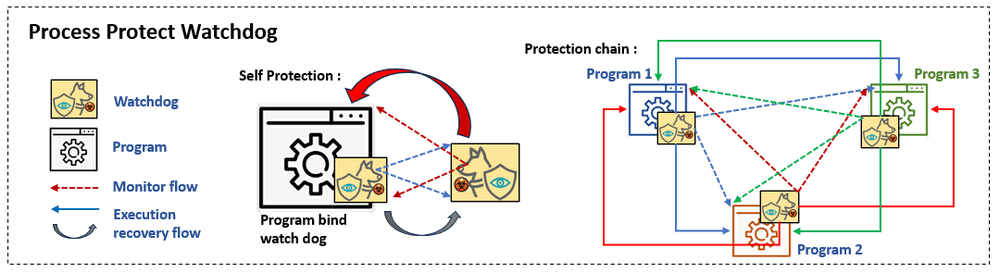
Project Design Purpose : During participating the cyber exercise as red team member, we found that the injected malware or attack launching program can easy be stopped by the blue team or defense program / mechanisms via killing the process / deleting the file. To address this, our project aims to develop a robust watchdog program designed to bind to target programs, diligently monitor their execution states, and ensure uninterrupted functionality.
- Continuous Monitoring : Establish a vigilant watchdog program that binds seamlessly to the target program, enabling real-time monitoring of its execution state.
- **Dynamic Response Mechanism : **Implement a responsive system that, in the event of the target program being closed or its process terminated, automatically initiates a new, independent process to resume program execution.
- **File Integrity and Recovery : **Create a safeguard mechanism capable of detecting instances where the target program file is deleted. Upon identification, the watchdog will promptly restore the program from a designated backup, ensuring minimal downtime.
The watchdog not only shields the program during execution, but also can be used in the Cyber Exercise Red Teaming, Service Program Protection and Malware Action Detection Research. The user can bind the watchdog to a single program to make it protect itself or hook several programs with watchdog to build a protection chain to make them auto protect each other.
To use the program watchdog, please refer to this document: link to the watchdog usage document
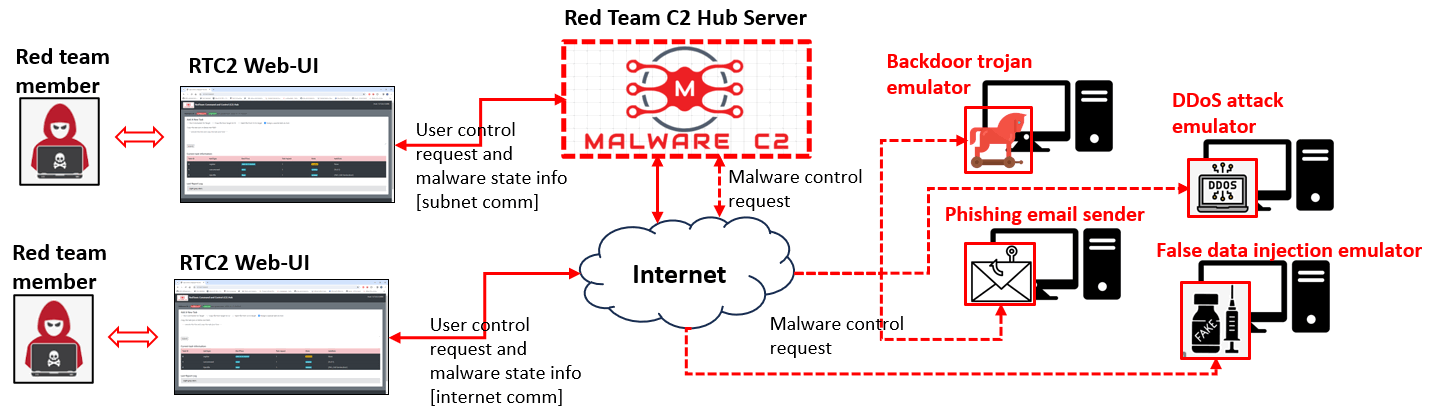
Project Design Purpose : The Red Team Command and Control (RTC2) server, commonly known as a C&C server, plays a pivotal role in cyber exercises and ranges. It serves as a centralized hub that red team members use to control and communicate with simulated compromised victims. This command center enables red team members or attackers to seamlessly issue instructions to the compromised machines, collect data from them, and coordinate various malicious activities within the exercise program. Our goal is to offer a comprehensive C2 server emulation solution designed for cyber exercise red team members. This solution allows them to seamlessly integrate different probing programs and malicious action programs, providing dynamic monitoring, scheduling, and control capabilities. The versatility of our solution makes it applicable across a range of fields, offering a robust platform for enhancing cyber defense readiness and testing the resilience of security measures.
The system can be applied on below fields :
**Cyber Exercise Red Team Malicious C2 Servers Simulation **
- Botnet Control: Cybercriminals use C2 servers to control networks of compromised computers (botnets) for various malicious activities, such as launching DDoS attacks, stealing sensitive information, spreading malware, and more.
- Remote Control: C2 servers provide attackers with a means to remotely issue commands to compromised systems, allowing them to manipulate and control the infected machines.
**Defensive C2 Frameworks **
- Red Team Operations: In the context of cybersecurity exercises, red teams (ethical hackers) may use C2 frameworks to simulate the tactics, techniques, and procedures (TTPs) of real-world adversaries. This helps organizations test their defenses and improve their incident response capabilities.
- Training and Simulation: Security professionals use C2 frameworks for training purposes, allowing them to understand and practice responding to simulated cyber threats in a controlled environment.
The RTC2 ( red team command and control ) system will provide a multi-threading based client which users can easily hook the client into their malicious action program to integrate in the RTC2 system. The RTC2 server not only offers a robust back-end but also comes equipped with a user-friendly web interface and an HTTP request handler API. So the users to can remote control the integrated malware effortlessly—either through a web browser or their custom programs. This combination of adaptability and accessibility enhances the user experience, providing a versatile platform for managing and orchestrating their cyber exercise scenarios.
To use the c2Emulator program , please refer to this document: link to the c2Emulaor usage document
Program design purpose : The objective of this project is to develop a demonstration and workshop utilizing the Railway (Metro) IT/OT System Cyber Security Test Platform, the Red Team Command and Control (C2) System, and the Modbus false data injector program for FDI & FCI attack on OT system. Our aim is to showcase how a hacker (red team member) could potentially launch an Operational Technology (OT) Cyber Attack on the programmable logic controllers (PLCs) governing railway train control, with the potential consequence of causing a collision accident between two trains. This particular attack scenario is proposed as one of the demonstration cases for the Cross Sword 2023 Test-Run, providing a realistic and controlled environment to assess the cybersecurity resilience of the railway infrastructure.
To use the False Modbus command and injection attack program, please refer to this document: link to the false cmd injector document
Program design purpose : We want to create a ARP Spoofing Attacker which can be integrated in our C2 Emulation system to use the comprehensive suite software Ettercap to implement the ARP Spoofing attack to block/drop the specific packet send from / to the OT system HMI. This program will be used for the Cross Sword 2023 Cyber Exercise test run Railway OT system attack demo.
This Ettercap wrapper ARP Spoofing malware is used to let the red team attacker can apply different kinds of packet filter on the network traffic via using Ettercap's ARP spoofing function on the router/switch to launch the packet drop, traffic block or even man in the middle attack. The ARP spoofing attacker is extended from the standard c2BackdoorTrojan module <c2TestMalware>by adding the our customized Ettercap Wrapper module, so the C2 Emulation system control it broad cast the ARP poisoning message to the railway HMI mode, the operational room subnet's switch/router and the related connected PLC sets.
To use the C2Ettercap wrapper, please refer to this document: link to the ARP spoofing attacker usage document
Last edit by LiuYuancheng (liu_yuan_cheng@hotmail.com) at 29/10/2023, if you have any problem please free to message me.