This project is active but it has been moved to its own organization for better control during its development.
This project provides instructions required to setup the demo described by Yoshiyuki Kurauchi in this post. The main goal of this project is to provide an end-to-end implementation of a Cloud-Native Network Function for didactic purposes.
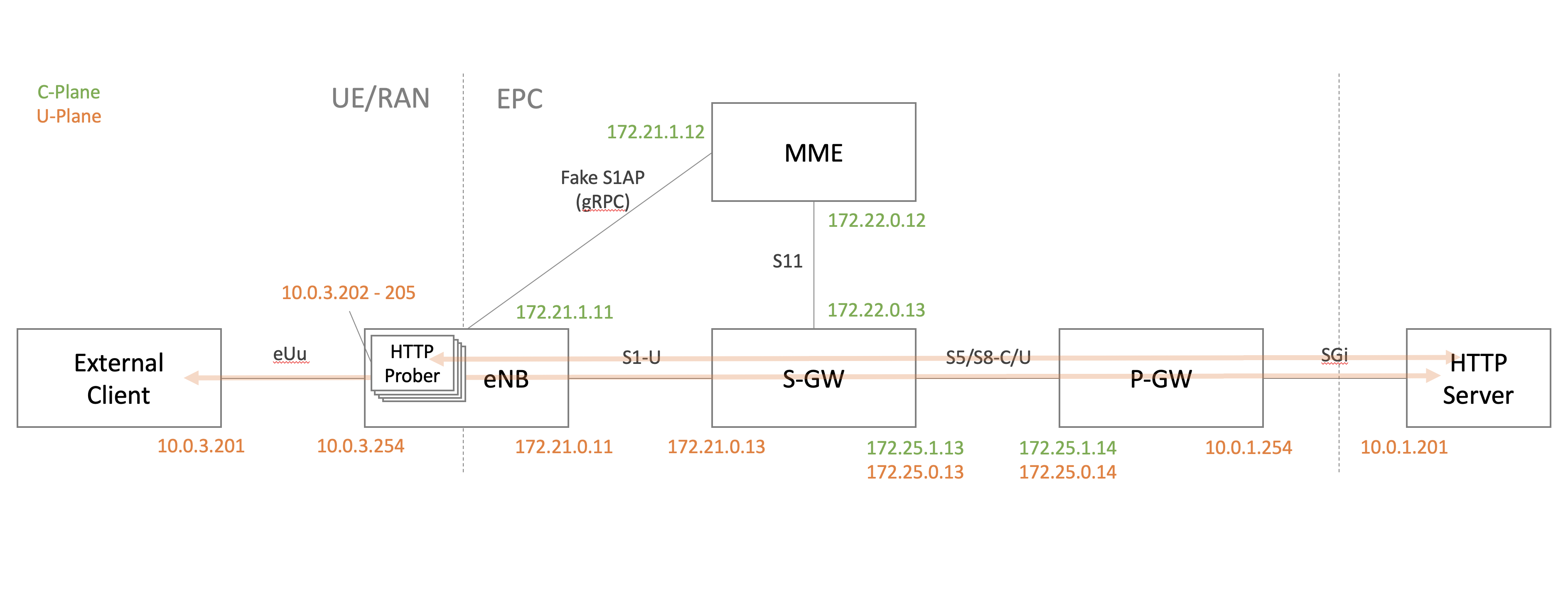
- User Equipment (UE): This is the device that requests connectivity to the network and downloads/uploads any data.
- Evolved UMTS Terrestrial Radio Access Network (E-UTRAN): The network of antennas or Evolved Node B (EnodeB), gives radio access to the UE anywhere there is coverage.
- Public Data Network (PDN): It is a shared network that is accessed by users that belong to different organizations.
- Evolved Packet Core (EPC): It validates the session request from
the UE, generates a PDP context and gives access to the PDN.
- Mobility Management Entity (MME): It does all the signaling for the mobile devices but does not process any user data traffic. An MME will provide session and mobility management for users. In addition, it tracks the location of the UE and selects the S-GW and P-GW that should serve this UE.
- Serving Gateway (S-GW): In order to eliminate any effect on user data while the UE moves between different eNodeBs, the S-GW works as an anchor point for the user data of the UE, while the UE is moving between different eNodeBs.
- PDN Gateway (P-GW): This is the node that connects between the LTE network and the PDN.
- S1-U: Interface for S1 user plane data for each bearer between the EnodeB and S-GW. Provides non guaranteed data delivery of user plane Protocol Data Units (PDUs).
- S1-MME: Responsible for delivering signaling protocols between the EnodeB and the MME. Consists of a Stream Control Transmission Protocol (SCTP) over IP. The application signaling protocol is an S1-AP (Application Protocol).
- S11: Interface defined between the MME and S-GW for EPS management.
- S5/S8:: Provides user plane tunneling and tunnel management function between the S-GW and P-GW. It enables S-GW to connect to multiple P-GWs for providing different IP services to the UE. Also used for S-GW relocation associated with the UE mobility. In principle S5 and S8 is the same interface, the difference being that S8 is used when roaming between different operators while S5 is network internal.
- SGi: Interface is used between P-GW and intranet or internet.
This project uses Vagrant tool for provisioning Virtual Machines
automatically. It's highly recommended to use the setup.sh script
of the bootstrap-vagrant project for installing Vagrant
dependencies and plugins required for its project. The script
supports two Virtualization providers (Libvirt and VirtualBox).
curl -fsSL http://bit.ly/initVagrant | PROVIDER=libvirt bash
Once Vagrant is installed, it's possible to deploy the demo with the following instruction:
DEPLOYMENT_TYPE=k8s MULTI_CNI=danm PKG_MGR=helm vagrant up
| Name | Default | Options | Description |
|---|---|---|---|
| DEBUG | true | false, true | Enables verbose execution |
| DEPLOYMENT_TYPE | docker | docker, k8s | Defines the container orchestrator tool to be used for the deployment |
| MULTI_CNI | multus | multus, danm, nsm | Determines the CNI multiplexer to be used for the deployment |
| PKG_MGR | k8s | k8s, helm | Determines the Kubernetes package manager to be used |
| HOST_IP | Local IP address of the host server | ||
| PLUGIN_CNI | flannel | flannel, ipvlan | Determines the CNI plugin to be used by DANM |
| ENABLE_SKYDIVE | false | false, true | Enables Skydive web dashboard |
| ENABLE_PORTAINER | false | false, true | Enables Portainer web dashboard |
| DEPLOY_KIND_CLUSTER | true | false, true | Determines whether a K8s cluster is deployed with Kind |
Once the Virtual Machine is provisioned by Vagrant, it's possible to check the logs of the different containers.
vagrant ssh
cd /vagrant
make k8s-logs
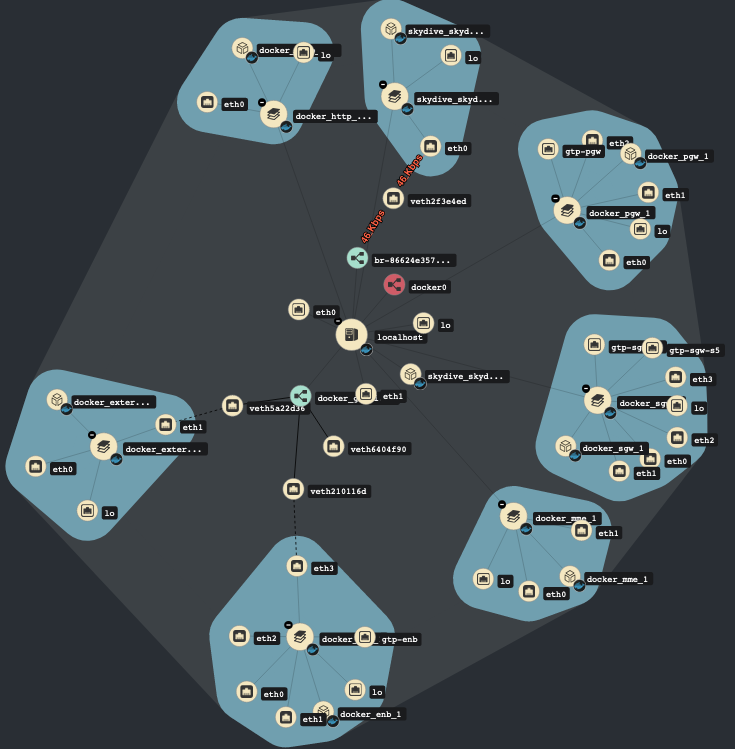
The Skydive real-time network analyzer can be deployed during the
provisioning process using the ENABLE_SKYDIVE environment variable.
Once the services are up and running it's possible to access it thru
the 8082 local port.