This repository contains examples for VPC Lattice implementation on Amazon EKS.
Amazon VPC Lattice is an application layer networking service that gives you a consistent way to connect, secure, and monitor service-to-service communication without any prior networking expertise.
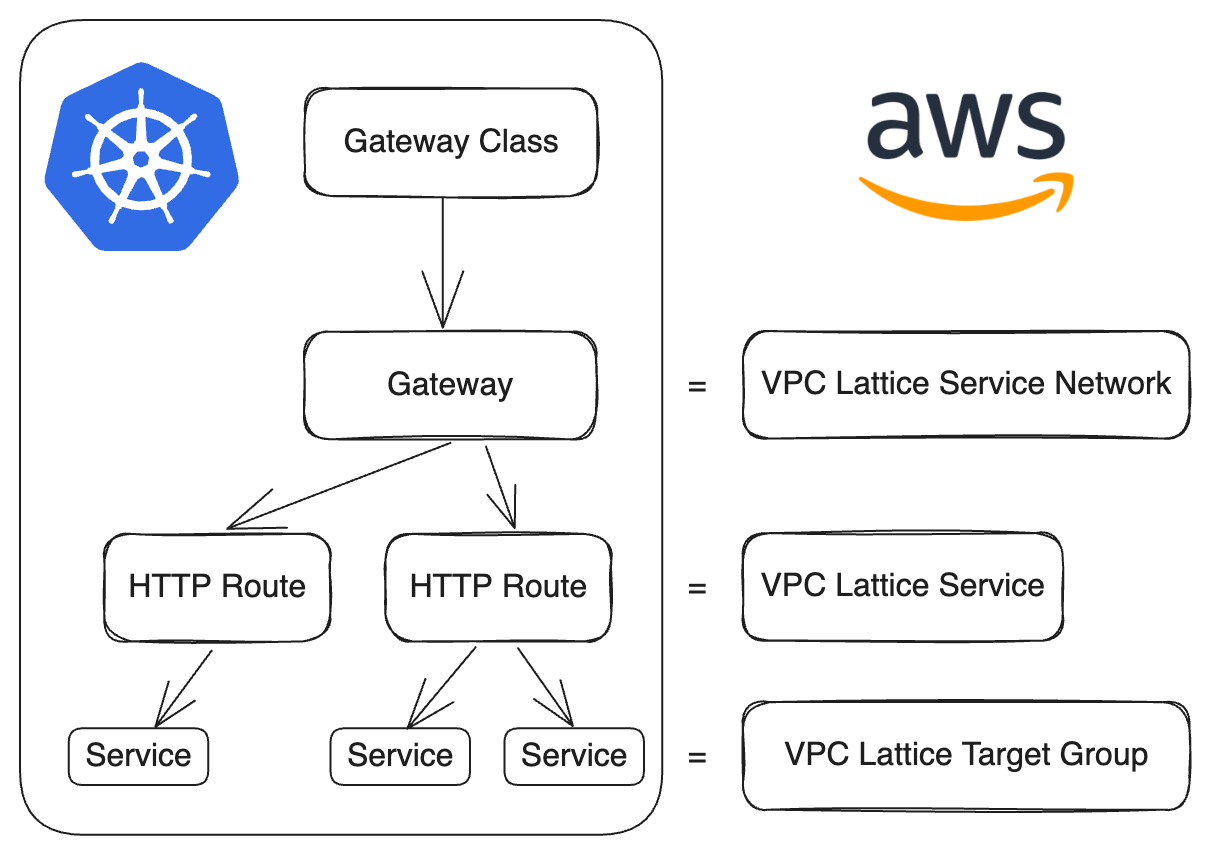
The resources in this repository deploys The AWS Gateway API Controller and this controller is an implementation of the Kubernetes Gateway API. The controller then integrates VPC Lattice with the Kubernetes Gateway API. The controller watches for the creation of Gateway API resources such as gateways and routes and provisions corresponding Amazon VPC Lattice objects. This enables users to configure VPC Lattice Service Networks using Kubernetes APIs, without needing to write custom code or manage sidecar proxies.
- A Kubernetes Cluster
- AWS IAM Permissions for creating and attaching IAM Roles
- Installation of required tools:
If you don't have an Amazon EKS cluster, you can use the Terraform code in cluster folder to deploy one. This Terraform code creates the following resources:
- A VPC with three private and three public subnets,
- An Amazon EKS Cluster with Kubernetes version set to 1.29 and a Managed Node Group with one instance,
- Some EKS and Custom Addons such as Karpenter and External Secrets Operator,
- Required IAM Roles for Addons and the AWS Gateway API Controller.
You can update the Terraform codes according to your requirements and environment.
terraform init
terraform plan
terraform apply --auto-approvePS:
- These resources are not Free Tier eligible.
- You need to configure AWS Authentication for Terraform with either Environment Variables or AWS CLI named profiles.
You can connect to your cluster using this command:
aws eks --region <region> update-kubeconfig --name <cluster_name>You need to change
regionandcluster_nameparameters.
You can find the Kubernetes manifests for an e-commerce application that consists of seven microservices in the example-application folder. Kustomize can be used to deploy the entire application stack.
kubectl apply -k example-application/The service object of the UI service creates a Network Load Balancer.
When you want to install the AWS Gateway API Controller and configure the Security Group access you can run ./vpc-lattice/.installation.sh.
The script has one function called install.
- Install function configures the Security Group authorisation and installs the required AWS Gateway API Controller Helm Chart to the Kubernetes cluster.
kubectl get deployment -n gateway-api-controller
NAME READY UP-TO-DATE AVAILABLE AGE
gateway-api-controller-aws-gateway-controller-chart 2/2 2 2 24sIn the vpc-lattice folder you can find the resources for the controller. First you need to install the Gateway Class and the Gateway.
kubectl apply -f vpc-lattice/controller/gatewayclass.yaml
kubectl apply -f vpc-lattice/controller/gateway.yamlkubectl get gateway -n checkout
NAME CLASS ADDRESS PROGRAMMED AGE
eks-cluster amazon-vpc-lattice True 29sWait until the status is Reconciled (this could take about five minutes).
kubectl wait --for=condition=Programmed gateway/eks-cluster -n checkoutThere is also a v2 of the Checkout microservice with a minor change. The definitions for the v2 Checkout service are in applicationv2. In this example, we will route the traffic with VPC Lattice between v1 and v2 of the Checkout service.
kubectl apply -k vpc-lattice/applicationv2/
kubectl rollout status deployment/checkout -n checkoutv2Now it's time to actually deploy the HTTPRoute resource.
apiVersion: gateway.networking.k8s.io/v1beta1
kind: HTTPRoute
metadata:
name: checkoutroute
namespace: checkout
spec:
parentRefs:
- name: eks-cluster
sectionName: http
rules:
- backendRefs:
- name: checkout
namespace: checkout
kind: Service
port: 80
weight: 25
- name: checkout
namespace: checkoutv2
kind: Service
port: 80
weight: 75As you can see, the Checkout Route Manifest distributes 75% traffic to checkoutv2 and remaining 25% traffic to checkout. There is also a Target Group Policy manifest that defines the Target Group behaviour.
kubectl apply -f vpc-lattice/controller/checkout-route.yaml
kubectl apply -f vpc-lattice/controller/target-group-policy.yamlThis creation of the associated resources may take 2-3 minutes, you can run the following command to wait for it to complete:
kubectl wait --for=jsonpath='{.status.parents[-1:].conditions[-1:].reason}'=ResolvedRefs httproute/checkoutroute -n checkoutOnce completed, you will find the HTTPRoute's DNS name from HTTPRoute status.
kubectl describe httproute checkoutroute -n checkoutYou can see the DNS name with this command:
kubectl get httproute checkoutroute -n checkout -o json | jq -r '.metadata.annotations["application-networking.k8s.aws/lattice-assigned-domain-name"]'Finally you need to update the ConfigMap of the UI service to update the DNS name for the Checkout service.
apiVersion: v1
kind: ConfigMap
metadata:
name: ui
namespace: ui
data:
ENDPOINTS_CHECKOUT: http://<NEW DNS ADDRESS FOR THE CHECKOUT SERVICE>
...After restarting the UI service deployment, you should be able to see the updated version of the Checkout service.
kubectl rollout restart deployment/ui -n ui