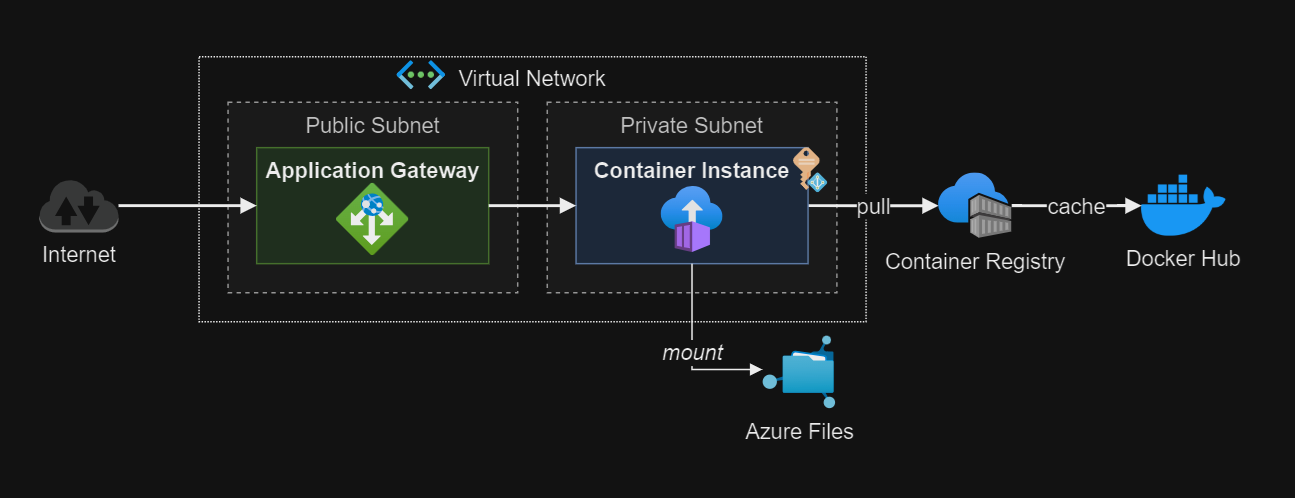
Deploy Azure Container Instances groups in a VNET.
Start by creating the .auto.tfvars from the template:
cp config/template.tfvars .auto.tfvarsCreate the first batch of resources:
terraform init
terraform apply -auto-approveThe container image must exist in order to deploy the CI.
Once the resources are created, build and push the application image to the ACR:
cd app
az acr build --registry crchokolatte --image app:latest --file Dockerfile.amd64 .Once the image is pushed, set the config to create the CI and the AGW:
create_containers = trueCreate the remaining resources:
terraform apply -auto-approveConnect to the application using the Application Gateway public address.
An option to deploy containers with YAML files is also available.
Example copied from the documentation in the deploy-aci.yaml file:
az group create --name myResourceGroup --location eastus
az container create --resource-group myResourceGroup --file deploy-aci.yamlAzure Container Registry supports Artifact Cache. Follow the steps in the documentation to create a caching rule.
Here's a NGINX rule via CLI:
Important
Use authentication for real world deployment.
az acr cache create -r crchokolatte -n nginx -s docker.io/library/nginx -t nginxLogin to ACR and run a test pull command:
az acr login -n crchokolatte
docker pull crchokolatte.azurecr.io/nginx:latestDeploy a new instance using the cached NGINX:
Important
This procedure might require a service identity.
az group create --name rg-artifact-cache --location eastus
az container create --resource-group rg-artifact-cache --file deploy-nginx-cached.yaml