AzADServicePrincipalInsights
Insights and change tracking on Azure Active Directory Service Principals (Enterprise Applications and Applications)
- 20220505_1
- fix:
using:scriptPathvariable in foreach parallel (this is only relevant for Azure DevOps and GitHub if you have a non default folder structure in your repository) - thanks Matt :)
- fix:
- 20220501_1
- parameter
-ManagementGroupIdaccepts multiple Management Groups in form of an array e.g..\pwsh\AzADServicePrincipalInsights.ps1 -ManagementGroupId @('mgId0', 'mgId1') - new parameter
-OnlyProcessSPsThatHaveARoleAssignmentInTheRelevantMGScopes. You may want to only report on Service Principals that have RBAC permissions on Azure resources at and below that Management Group scope(s) (Management Groups, Subscriptions, Resource Groups and Resources) - Role assignments on Azure resources - mark those RBAC Role assignments which leverage a RBAC Role definition that can create role assignments as critical
- updated YAML workflow/pipeline files
- minor bug fixes
- performance optimization
- parameter
- 20220425_2
- add parameter
-ManagementGroupId(if undefined, then Tenant Root Management Group will be used) - use AzAPICall module version 1.1.11
- add parameter
- 20220404_1
- add FederatedIdentityCredentials
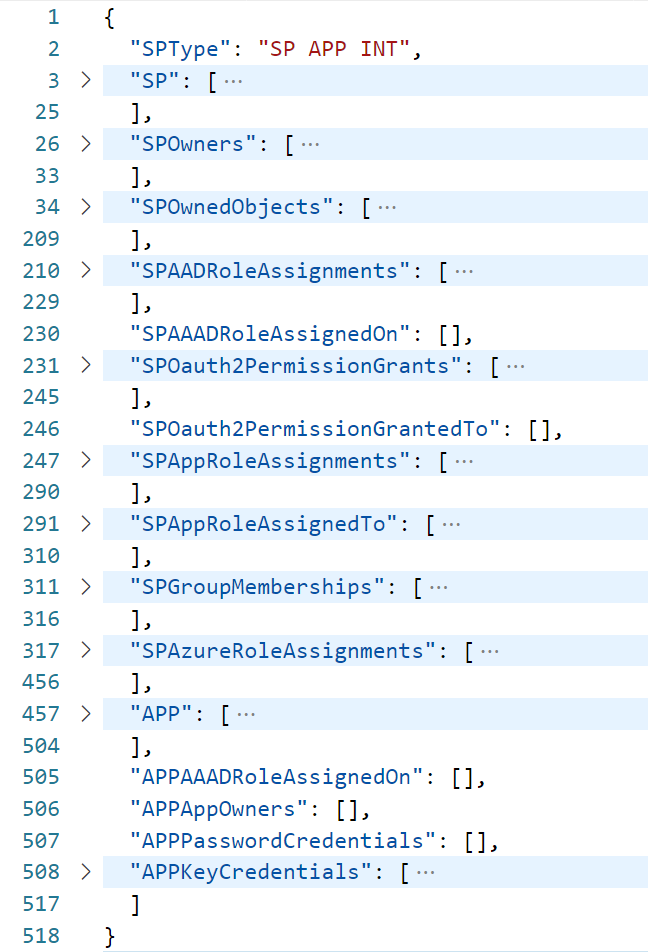
- HTML export
- JSON export
- CSV export (wip)
- AADRoleAssignments
- AppRoleAssignments
- Oauth2PermissionGrants
- AppSecrets
- AppCertificates
- AppFederatedIdentityCredentials
- Customizable permission classification (permissionClassification.json)
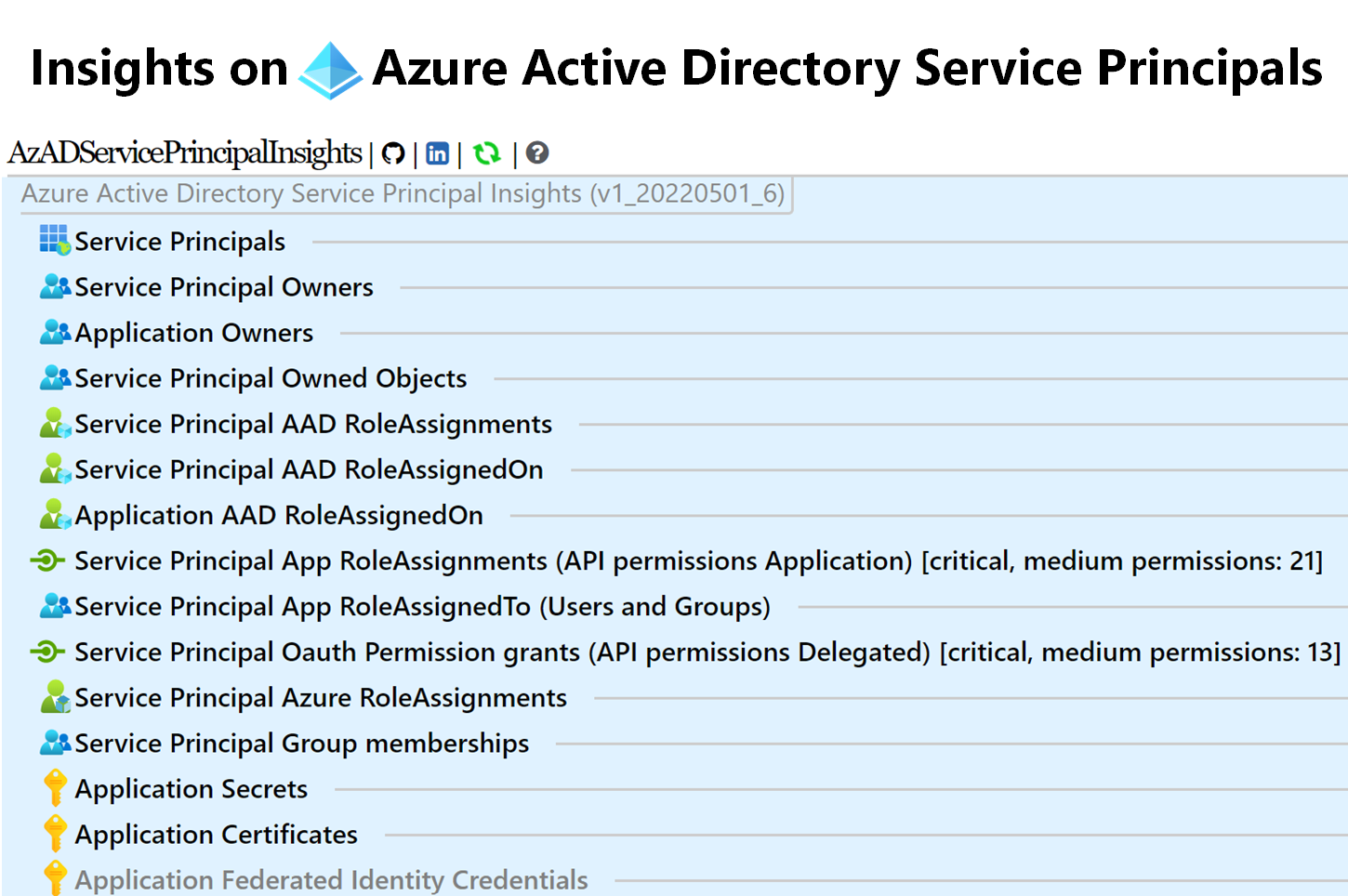
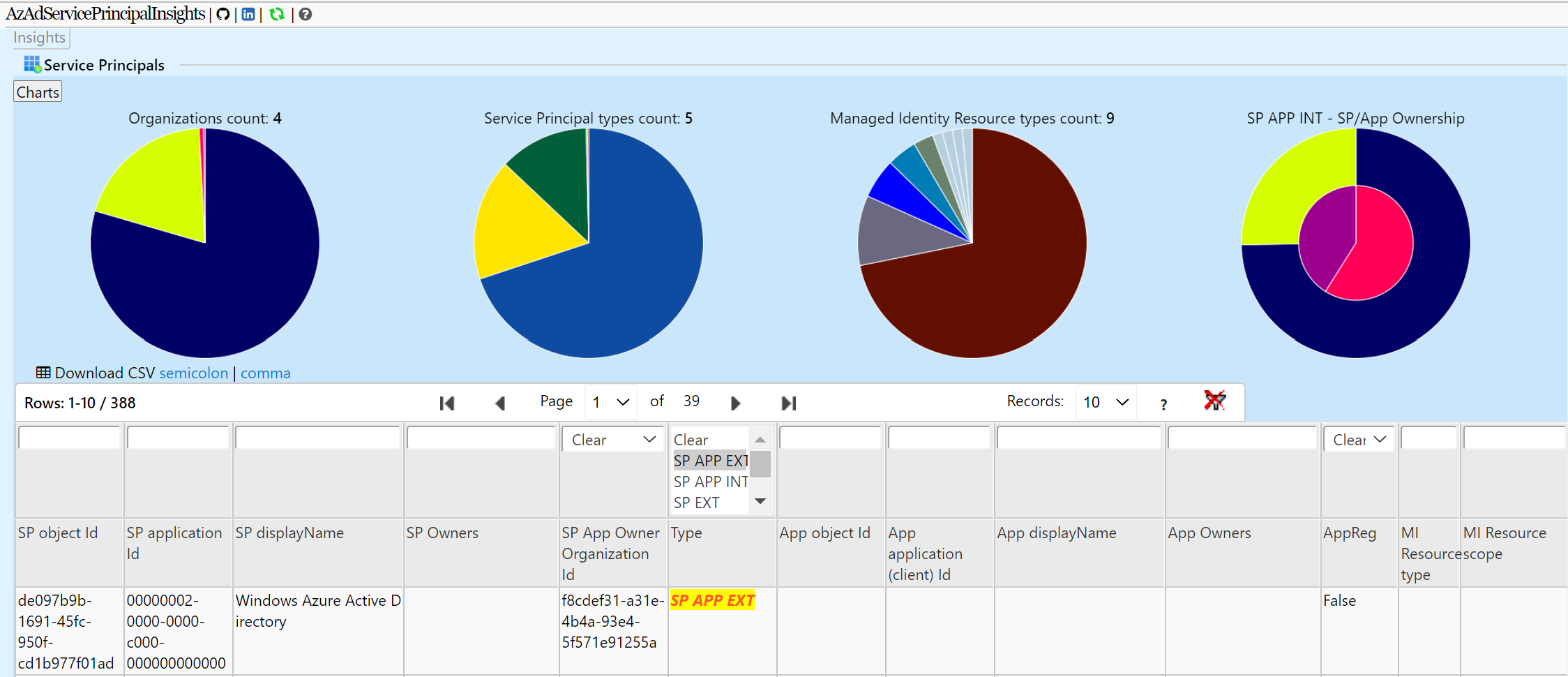
- ServicePrincipals by type
- ServicePrincipal owners
- Application owners
- ServicePrincipal owned objects
- ServicePrincipal AAD Role assignments
- ServicePrincipal AAD Role assignedOn
- Application AAD Role assignedOn
- App Role assignments (API permissions Application)
- App Roles assignedTo (Users and Groups)
- Oauth permission grants (API permissions delegated)
- Azure Role assignments (Azure Resources; Management Groups, Subscriptions, Resource Groups, Resources)
- ServicePrincipal Group memberships
- Application Secrets
- Application Certificates
- Application Federated Identity Credentials
Management Group (Tenant Root Management Group) RBAC: Reader
Microsoft Graph API | Application | Application.Read.All
Microsoft Graph API | Application | Group.Read.All
Microsoft Graph API | Application | RoleManagement.Read.All
Microsoft Graph API | Application | User.Read.All
The Build Service Account or Project Collection Build Service Account (which ever you use) requires Contribute permissions on the repository (Project settings - Repos - Security)
Requires PowerShell Version >= 7.0.3
Requires PowerShell Module 'AzAPICall'.
Running in Azure DevOps or GitHub Actions the AzAPICall PowerShell module will be installed automatically.
AzAPICall resources:
#USER: 'Application (client) ID' of the App registration OR 'Application ID' of the Service Principal (Enterprise Application)
#PASSWORD: Secret of the App registration
$pscredential = Get-Credential
Connect-AzAccount -ServicePrincipal -TenantId <tenantId> -Credential $pscredential
Also check https://www.azadvertizer.net - AzAdvertizer helps you to keep up with the pace by providing overview and insights on new releases and changes/updates for Azure Governance capabilities such as Azure Policy's Policy definitions, initiatives (Set definitions), aliases and Azure RBAC's Role definitions and resource provider operations.
Also check https://aka.ms/AzGovViz - Azure Governance Visualizer is intended to help you to get a holistic overview on your technical Azure Governance implementation by connecting the dots.
It is a PowerShell script that iterates your Azure Tenant's Management Group hierarchy down to Subscription level, it captures most relevant Azure governance capabilities such as Azure Policy, RBAC and Blueprints and a lot more..
- Listed as tool for the Govern discipline in the Microsoft Cloud Adoption Framework (CAF)
- Listed as security monitoring tool in the Microsoft Well Architected Framework (WAF)
Please note that while being developed by a Microsoft employee, AzADServicePrincipalInsights is not a Microsoft service or product. AzADServicePrincipalInsights is a personal/community driven project, there are none implicit or explicit obligations related to this project, it is provided 'as is' with no warranties and confer no rights.