- Table of contents
- Deploy to Azure
- Introduction
- Description
- LAB Builder scenario's
- Topology drawing - Hub & Spoke
- Topology drawing - Azure Virtual WAN
- Deployment Steps
- Deployment notes
- Resource Names
- Appendix
| Description | Template |
|---|---|
| Deploy to Azure Subscription |
⚠️ Warning: This deployment is meant for Demo, Test, Learning, Training, Practice or Reproduction purposes ONLY!! Please don't deploy to production environments!!
In my daily work I've created numerous times a (semi-)manual Hub & Spoke topology for Testing, (Self)Training, Demo or Reproduction purposes. I've always done this in multiple ways, like: PowerShell scripts, Azure CLI, ARM or Azure Potal GUI.....whatever was the best fit. But bottom line: Wathever option is fine by me as long as it has the least amount of effort to build it.
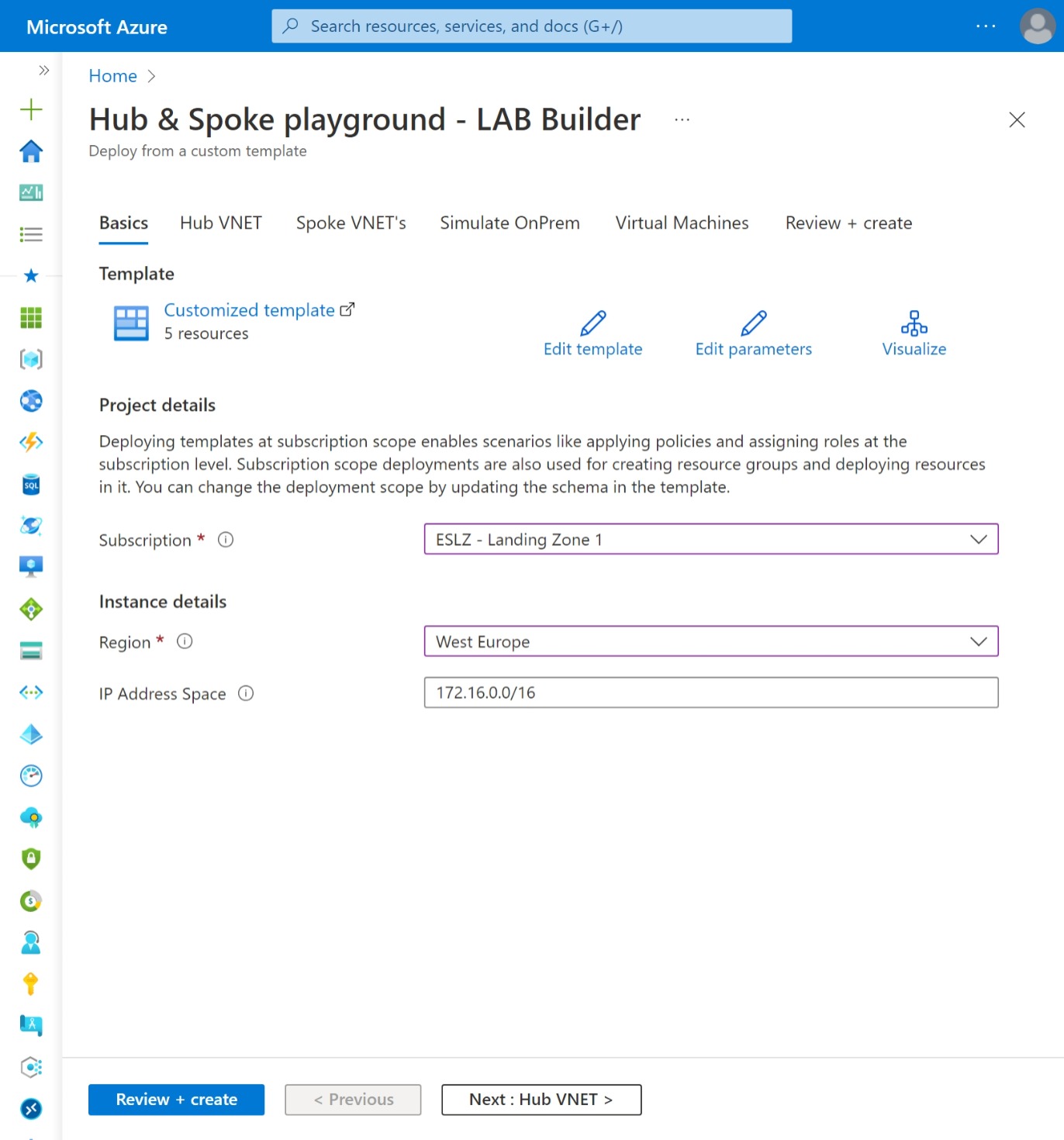
With that in mind I've created a "Hub & Spoke playground Lab builder" so you'll be able to deploy Hub & Spoke scenario's in notime. It takes approx. 30min to deploy a 'full option Hub & Spoke' deployment with 2 Spoke VNET's.
With this 'Hub & Spoke playground - LAB Builder' you'll be able to deploy Hub & Spoke topologies in various ways incl. Azure Virtual WAN.
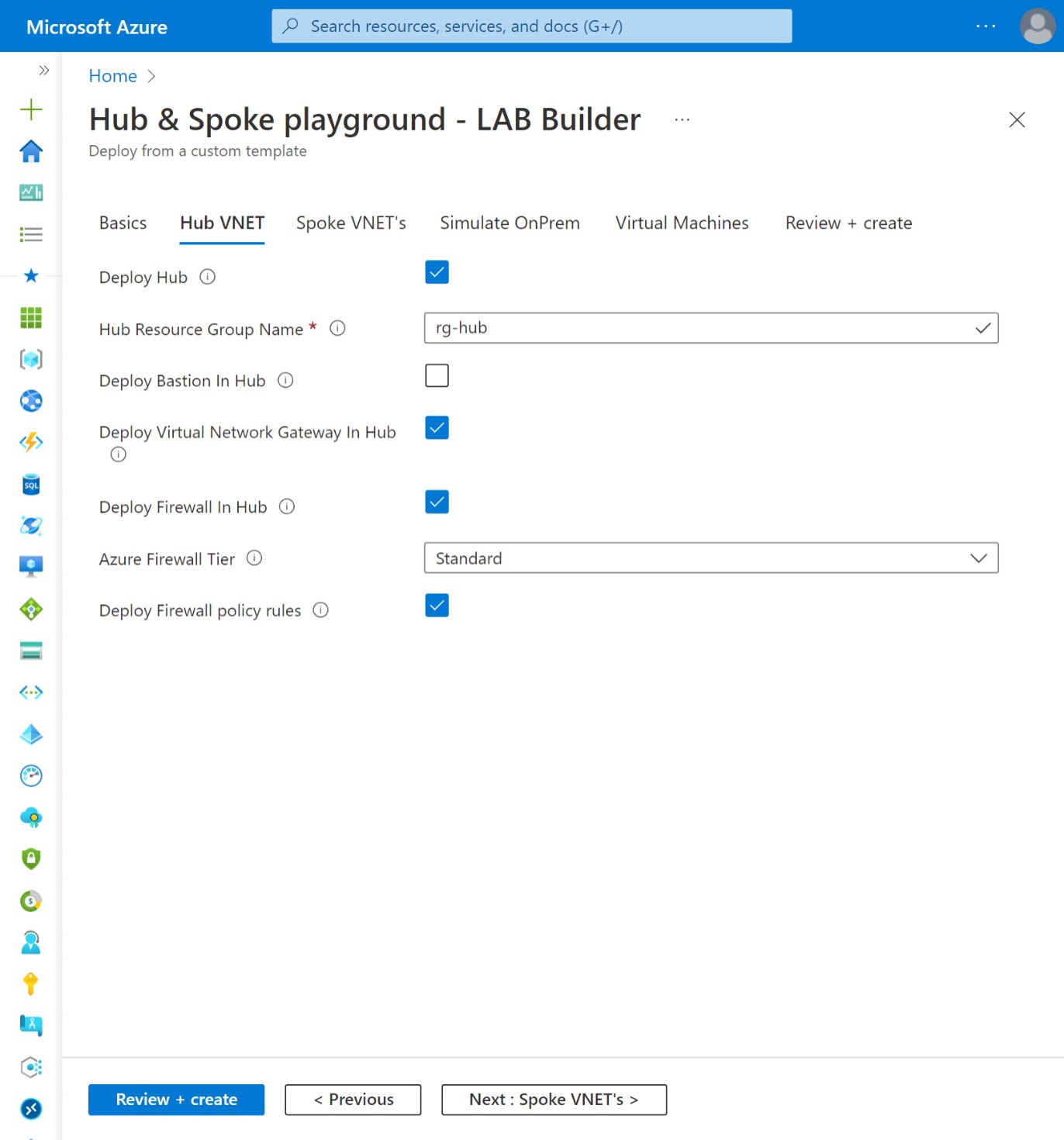
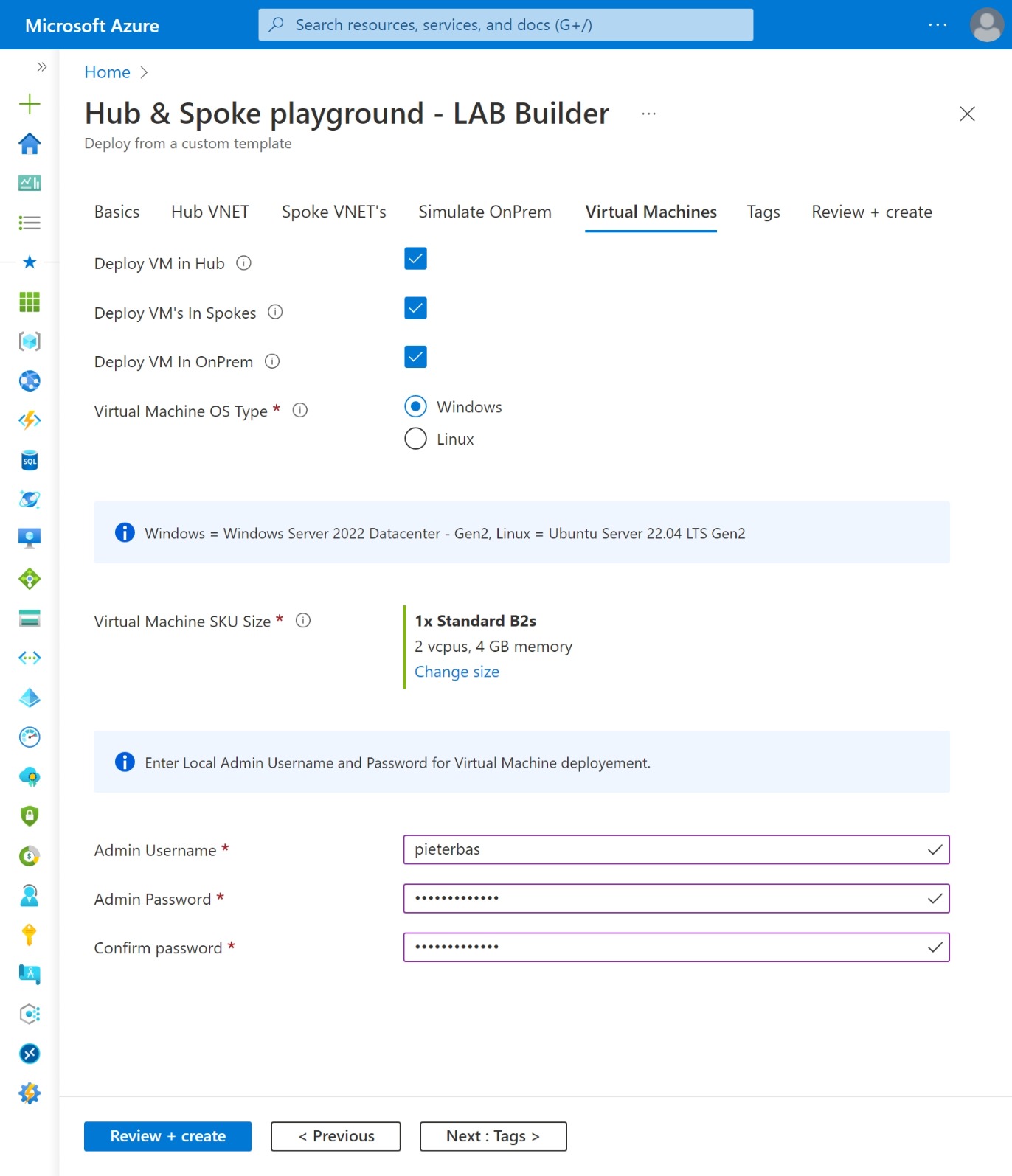
Optionaly you can deploy Azure Firewall (Standard or Premium) in the Hub (VNET or vWAN) incl. Route table, deploy Virtual Machine in Hub VNET and/or Spoke VNET's and deploy Bastion Host in Hub VNET and/or Spoke VNET's. Optional deploy default Azure Firewall rule Collection group which enables spoke-to-spoke and internet traffic.
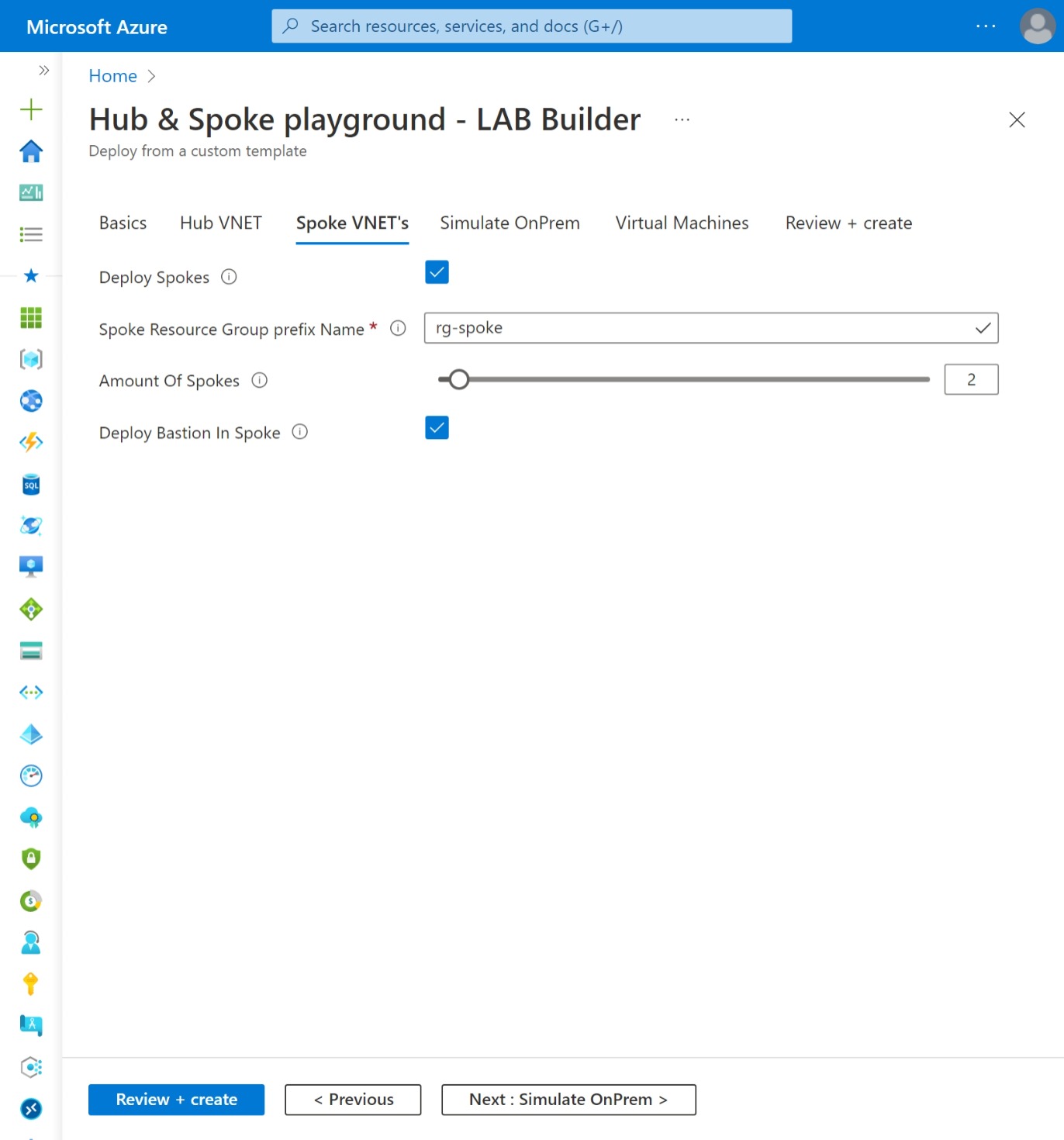
On deployemnt you can specify the amount of Spoke VNET's to be deployed. VNET peerings will be deployed if both Hub and Spoke(s) are selected for deployement.
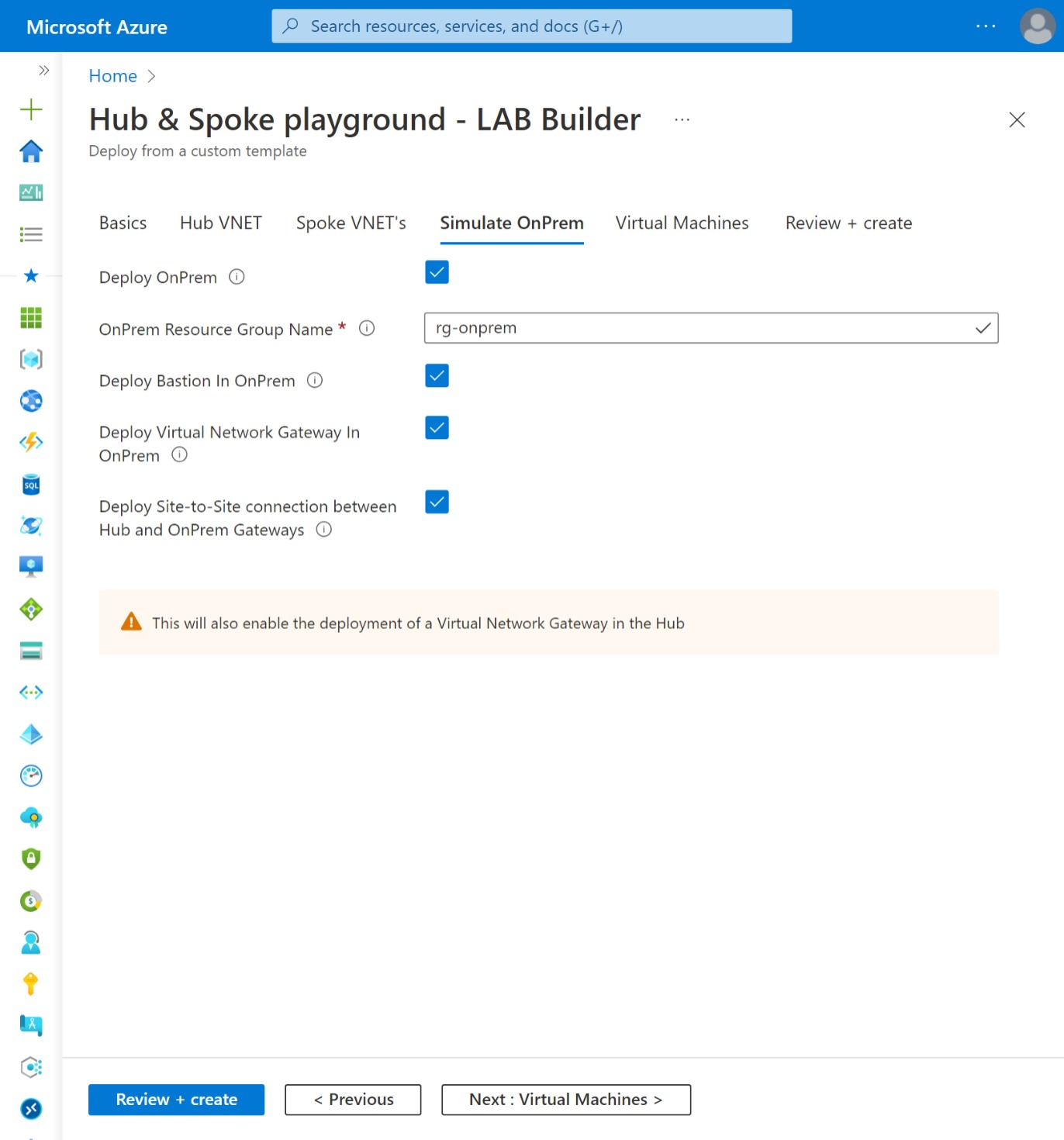
To simulate OnPrem hybrid connectivity you can optionaly deploy a 'OnPrem' VNET. Optionaly deploy a Bastion Host, Virtual Machine and Virtual Network Gateway in the OnPrem VNET. When a Hub is also deployed with a VPN Gateway you can optionaly deploy a site-to-site VPN connection.
With LABbuilder you can deploy 4 main scenario's.
- Only deploy Spoke(s)
- Only deploy VNET Hub or Azure Virtual Hub
- Deploy Hub or vWAN Hub and Spoke(s)
- Deploy Hub or vWAN Hub and Spoke(s) and OnPrem simulating Hybrid connectivity
Within these main scenario's there are multiple options:
| Scenrio | What gets deployed |
|---|---|
| 1. Only deploy Spokes | - Resource Group (rg-Spoke#) - Virtual Network (VNET-Spoke#) - Network Security Group (NSG-Spoke#) linked to 'Default' Subnet - Subnet (Default) - [optional] Subnet (AzureBastionSubnet) - [optional] Subnet (AzureFirewallSubnet) - [optional] Azure Bastion Host (Bastion-Spoke#) incl. Public IP - [optional] Azure Virtual Machine (Windows) Only in combination with Firewall in Hub: - Route table (RT-Hub) linked to 'Default' Subnet, with default route to Azure Firewall |
| 2. Only deploy Hub or vWAN Hub | - Resource Group (rg-Hub) - Virtual Network (VNET-Hub) - Network Security Group (NSG-Hub) linked to 'Default' Subnet - Subnet (Default) - [optional] Subnet (AzureBastionSubnet) - [optional] Subnet (AzureFirewallSubnet) - [optional] Subnet (GatewaySubnet) - [optional] Azure Bastion Host (Bastion-Hub) incl. Public IP - [optional] Azure Firewall (AzFw) incl. Public IP - [optional] Azure Firewall Policy (AzFwPolicy) - [optional] Azure Firewall Policy rule Collection Group - [optional] Azure Virtual Machine (Windows) - [optional] Virtual Network Gateway Only in combination with Firewall in Hub: - Route table (RT-Hub) linked to 'Default' Subnet, with default route to Azure Firewall |
| 3. Deploy Hub or vWAN Hub and Spokes | includes all from scenario 1 and 2, incl: - VNET Peerings |
| 4. Deploy Hub or vWAN Hub and Spokes + OnPrem | includes all from scenario 1, 2 and 3 incl: - Resource Group (rg-OnPrem) - Virtual Network (VNET-OnPrem) - Network Security Group (NSG-OnPrem) linked to 'Default' Subnet - Subnet (Default) - [optional] Subnet (AzureBastionSubnet) - [optional] Subnet (GatewaySubnet) - [optional] Azure Bastion Host (Bastion-Hub) incl. Public IP - [optional] Azure Virtual Machine (Windows) Only in combination with Hub: - [optional] Site-to-Site VPN Connection to Hub Gateway |
- VNET Connections will be deployed when vWAN Hub and Spokes are selected
- VNET Peering will be deployed when Hub and Spoke are selected
- ICMPv4 Firewall rule will be enabled on Virtual Machines
- Windows VM image is Windows Server 2022 Datacenter Gen2
- Linux VM image is Ubuntu Server 22.04 LTS Gen2
- Route table incl. Default routes (Private and Public) will be deployed in vWAN Hub if Azure Firewall is selected.
- Route tables (UDR's) incl. Default route will be deployed if Azure Firewall is selected (0.0.0.0/0 -> Azure Firewall)
- Network Security group will be deplyed to 'default' subnets only
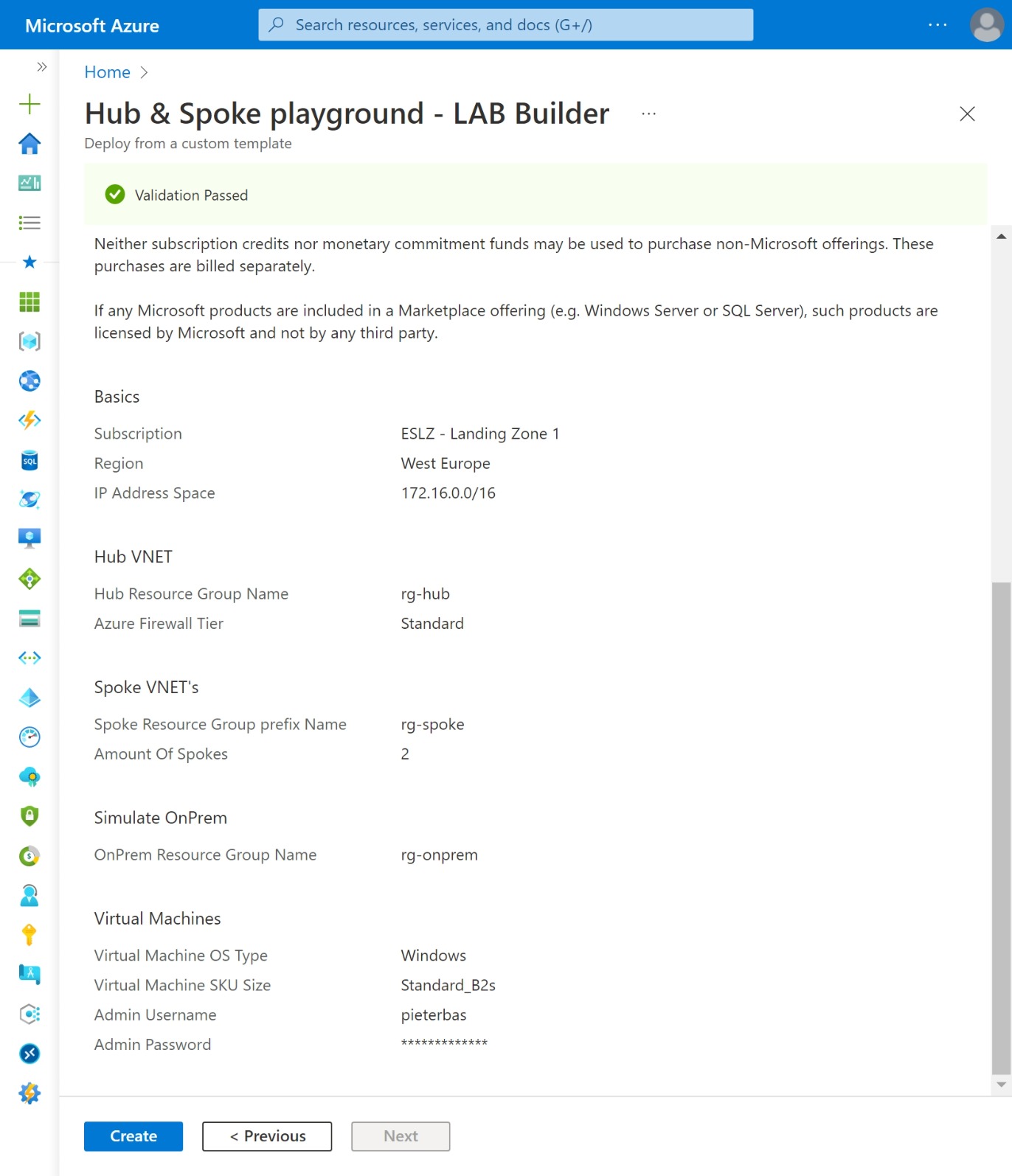
- At deployemt use a /16 subnet. every VNET (Hub and Spoke VNET's) will get a /24 subnet
- Hub VNET will always get the first available /24 subnet. eg. 172.16.0.0/24
- Spoke(s) VNET gets subsequent subnets. eg. 172.16.1.0/24, 172.16.2.0/24 etc.
- OnPrem VNET will always get the latest available /24 subnet. eg. 172.16.255.0/24
- see subnet details:
Spoke VNET's subnets:
| Subnet Name | Subnet address range | notes |
|---|---|---|
| default | x.x.Y.0/26 | |
| AzureBastionSubnet | x.x.Y.128/27 | Only when Bastion is selected |
Hub VNET subnets:
| Subnet Name | Subnet address range | notes |
|---|---|---|
| default | x.x.0.0/26 | |
| AzureFirewallSubnet | x.x.0.64/26 | Only applicable for Hub VNET with Azure Firewall selected |
| AzureBastionSubnet | x.x.0.128/27 | Only when Bastion is selected |
| GatewaySubnet | x.x.0.160/27 | Only when Gateway is selected |
Azure virtual WAN Hub subnet:
| Subnet Name | Subnet address range | notes |
|---|---|---|
| n/a | x.x.0.0/24 |
OnPrem VNET subnets:
| Subnet Name | Subnet address range | notes |
|---|---|---|
| default | x.x.255.0/26 | |
| AzureBastionSubnet | x.x.255.128/27 | Only when Bastion is selected |
| GatewaySubnet | x.x.255.160/27 | Only when Gateway is selected |
| Type | Name |
|---|---|
| Hub VNET | VNET-Hub |
| Spoke VNET's | VNET-Spoke# |
| Hub Virtual Machine | VM-Hub |
| Spoke Virtual Machines | VM-Spoke# |
| Hub Route Table | RT-Hub |
| Spoke Route tables | RT-Spoke# |
| Hub Bastion Host | Bastion-Hub |
| Spoke Bastion Hosts | Bastion-Spoke# |
| Hub Network Security Group | NSG-Hub |
| Spoke Network Security Groups | NSG-Spoke# |
| Hub Azure Firewall | Firewall-Hub |
| Hub Virtual Network Gateway | Gateway-Hub |
| OnPrem VNET | VNET-OnPrem |
| OnPrem Virtual Machine | VM-OnPrem |
| OnPrem Bastion Host | Bastion-OnPrem |
| OnPrem Network Security Group | NSG-OnPrem |
| OnPrem Virtual Network gateway | Gateway-OnPrem |
| Parameter name | type | default value | notes |
|---|---|---|---|
| adminUsername | string | n/a | Admin username for VM |
| adminPassword | secure string | n/a | Admin password for VM |
| AddressSpace | string | 172.16.0.0/16 | IP Address space used for VNETs in deployment. Only enter a /16 subnet. Default = 172.16.0.0/16 |
| location | string | deployment().location | Azure Region. Defualt = Deployment location |
| deploySpokes | bool | true | Deploy Spoke VNETs |
| spokeRgNamePrefix | string | rg-spoke | Spoke Resource Group prefix name. With default value set, spoke resource groups will be: rg-spoke1, rg-spoke2 etc. |
| amountOfSpokes | int | 2 | Amount of Spoke VNETs you want to deploy. Default = 2 |
| deployVMsInSpokes | bool | true | Deploy VM in every Spoke VNET |
| deployBastionInSpoke | bool | false | Deploy Bastion Host in every Spoke VNET |
| deployHUB | bool | true | bool |
| hubRgName | string | rg-hub | Hub Resource Group Name |
| deployBastionInHub | bool | true | Deploy Bastion Host in Hub VNET |
| deployVMinHub | bool | true | Deploy VM in Hub VNET |
| deployFirewallInHub | bool | true | Deploy Azure Firewall in Hub VNET. Includes deployment of custom route tables in Spokes and Hub VNETs |
| AzureFirewallTier | string | Standard | Azure Firewall Tier: Standard or Premium |
| deployFirewallrules | bool | false | Deploy firewall policy rule collection group which enables spoke-to-spoke traffic and internet traffic |
| deployOnPrem | bool | false | Deploy OnPrem VNET |
| onpremRgName | string | rg-onprem | OnPrem Resource Group Name |
| deployBastionInOnPrem | bool | false | Deploy Bastion Host in OnPrem VNET |
| deployVMinOnPrem | bool | false | Deploy VM in OnPrem VNET |
| deployGatewayinOnPrem | bool | false | Deploy Virtual Network Gateway in OnPrem VNET |
| deploySiteToSite | bool | false | Deploy Site-to-Site VPN Connection between OnPrem and Hub VNET |
| osType | string | Windows | Virtual machine OS Type. Windows or Linux |
| vmSize | string | Standard_B2s | Virtual machine SKU size |
BGP support for VPN site-to-siteChoose between Azure vWAN and Hub & SpokeAdd default Firewall Network & Application rulesDeploy separate VNET (simulate OnPrem) and deploy VPN gateways including Site-to-Site tunnelremove static Resource Group namesuse CIDR notation as Address Space (Instead of first two octets)Virtual machine OS Type. Windows and Linux supportVirtual Machine SKU size selectionVirtual machine boot diagnostics (Managed storage account)Virtual machine delete option of Disk and NicTags support for resources deployed- etc...