Miasm's Ollvm Deflattener
MODeflattener deobfuscates control flow flattened functions obfuscated by OLLVM using Miasm.
https://mrt4ntr4.github.io/MODeflattener/
| Flattened Flow | Deflattened Flow |
|---|---|
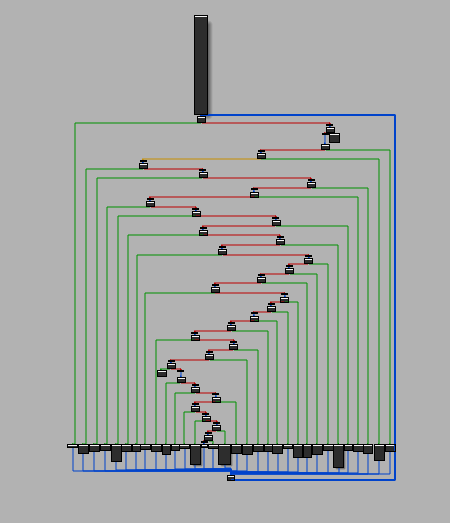 |
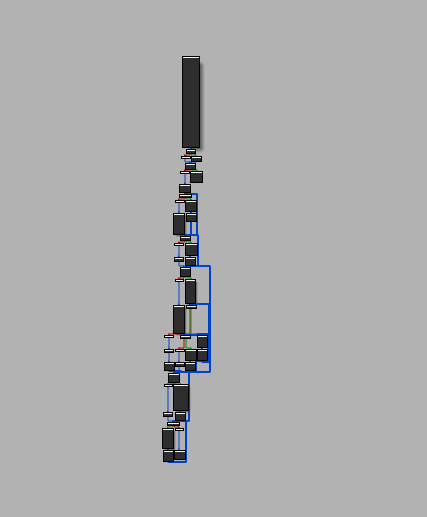 |
git clone https://github.com/mrT4ntr4/MODeflattener.git
cd MODeflattener
pip3 install -r requirements.txt
└──╼ $python3 modeflattener.py -h
usage: modeflattener [-h] [-b BASEADDR] [-a] [-l LOG] filename patch_filename address
positional arguments:
filename file to deobfuscate
patch_filename deobfuscated file name
address obfuscated function address
optional arguments:
-h, --help show this help message and exit
-b BASEADDR, --baseaddr BASEADDR
file base address
-a, --all find and deobfuscate all flattened functions recursively
-l LOG, --log LOG logging level (default=INFO)
- x86
-
Tim Blazytko's flattening heuristic script
While disassembling the specified function we can look out for other functions used by it and can make use of this script to automatically detect whether it is a flattened one and try to deobfuscate it. This has already been integrated into the tool!
-
This script hides the nop instructions from IDA graph view as the backbone is converted into a long nop chain after deobfuscation.
-
Obfuscation is a most common software protection technique to deliberately make the source or machine code hard to understand. Thanks to the IDA powerful CFG API, Qiling IDA plugin can implement multiple de-obfuscation techniques with a mixture of static and dynamic analysis.
Dissecting LLVM Obfuscator - RPISEC
Automated Detection of Control-flow Flattening - Tim Blazytko