Time spent: 14 hours spent in total
Objective: Find, analyze, recreate, and document five vulnerabilities affecting an old version of WordPress
- Summary: XSS vulnerability in the meida/library sector (http://localhost:8080/wp-admin/upload.php) prior to 4.6.1 version can allow hackers to inject arbitrary web script or HTML by tricking a superuser (aka admin user) into uploading an image file that has a compromised filename.
- Vulnerability types:XSS
- Tested in version: 4.1
- Fixed in version: 4.6.1
- GIF Walkthrough:
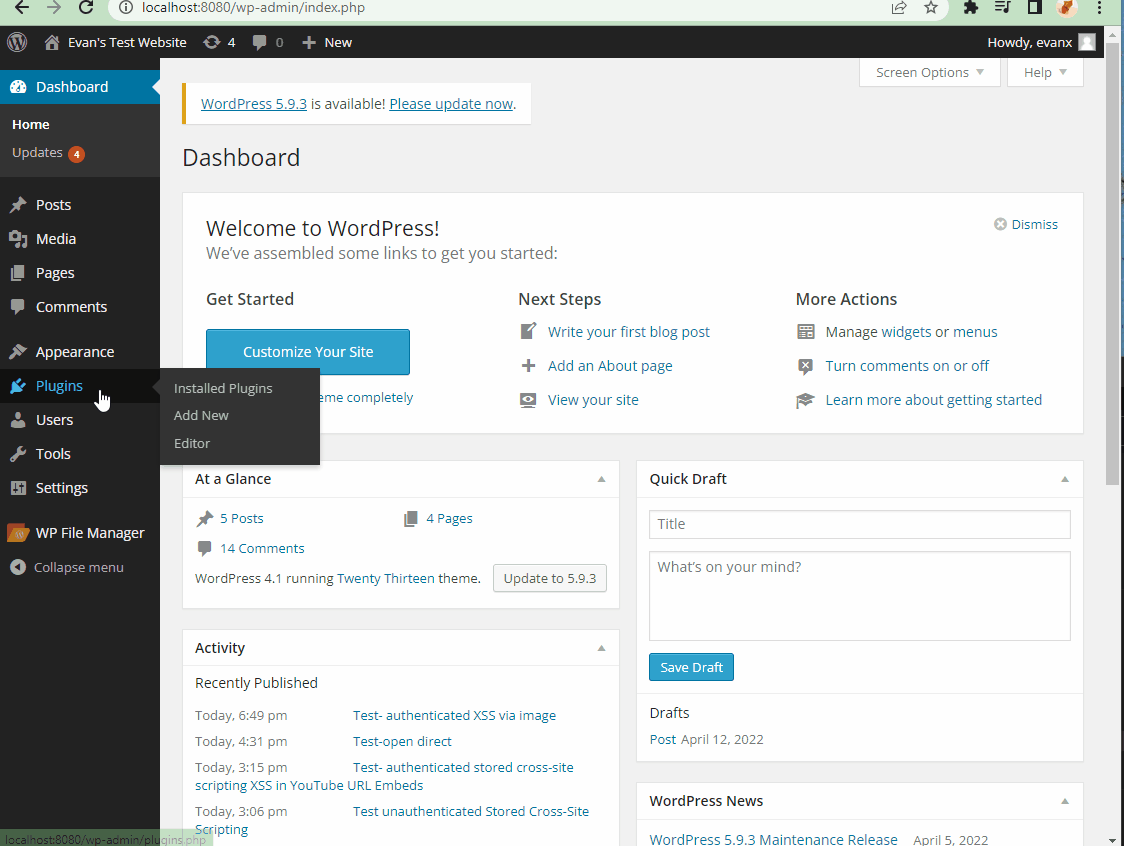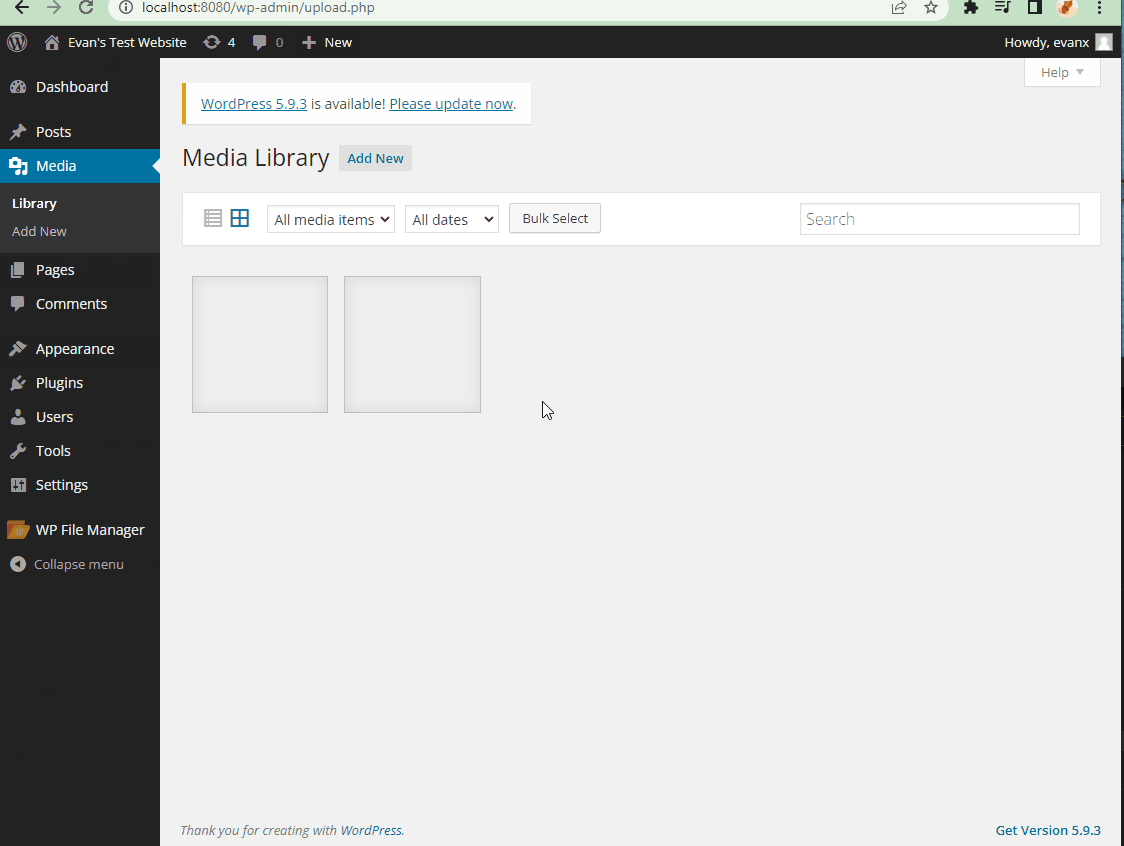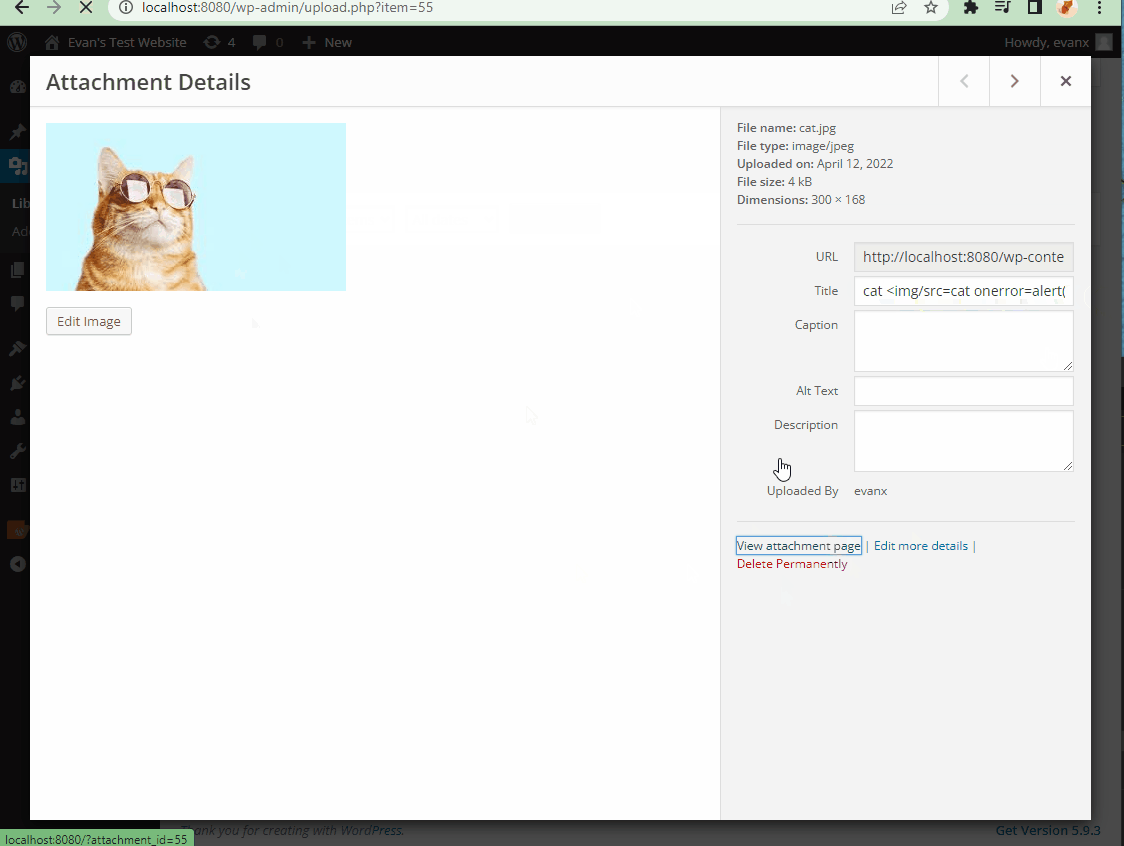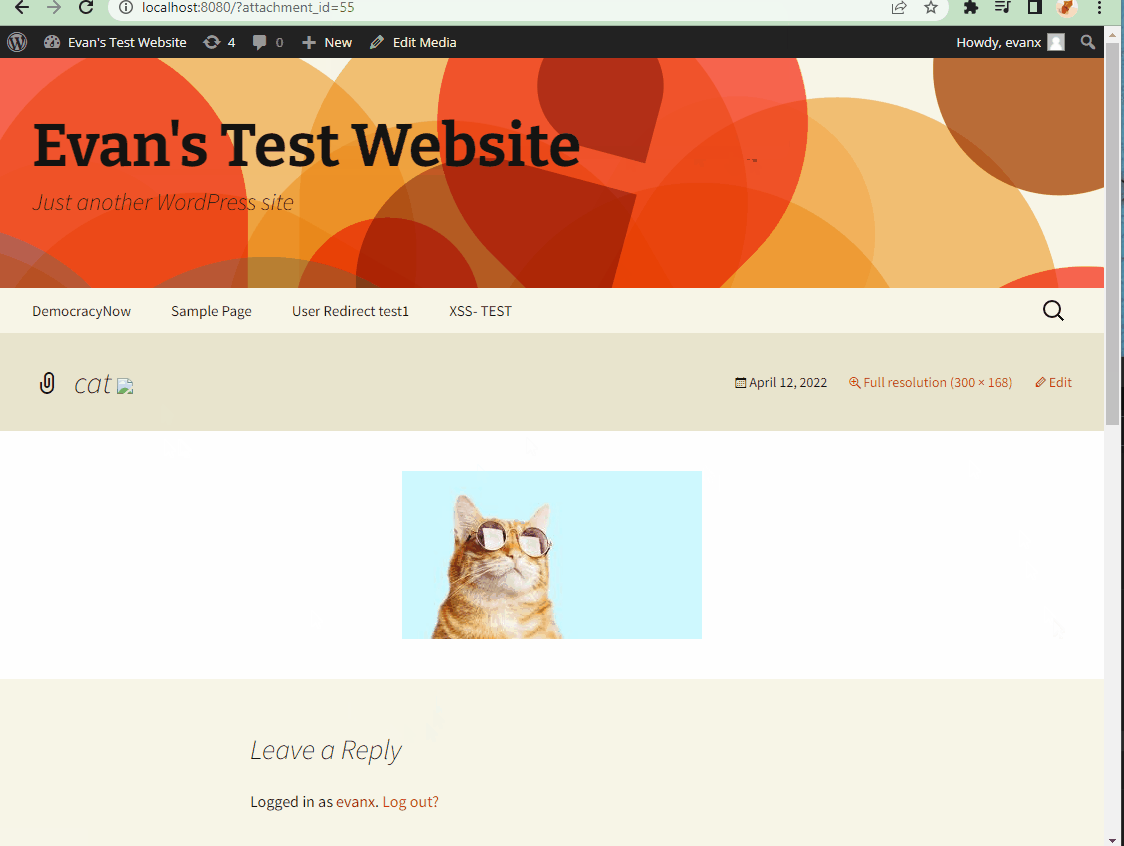
- Steps to recreate: A super user (aka admin) approves of an image with a compromised filename. Please see the snippit below. The XSS will be triggered whenver the page that contains this image is refreshed.
-
cat<img src=cat onerror=alert('hacked!')> - Affected source code:
- Summary: The old version of WordPress is susceptible to a stored XSS. A hacker may inject compromised JavaScript in WordPress and script may triggered whenever activated.
- Vulnerability types: XSS
- Tested in version: 4.1
- Fixed in version: 4.1.2
- GIF Walkthrough:
- Steps to recreate: An admin user accidentially copies/pastes codes that contain a problematic script. The script is activated whenever the page is refreshed that contains the script. Please see the snippet below.
-
<script> alert('Got you!)</script> - Affected source code:
- Summary: A cross-site scripting (XSS) vulnerability allows verified users to insert malicious JavaScript into YouTube RUL Embeds.
- Vulnerability types:XSS
- Tested in version: 4.1
- Fixed in version: 4.1.16
- GIF Walkthrough:
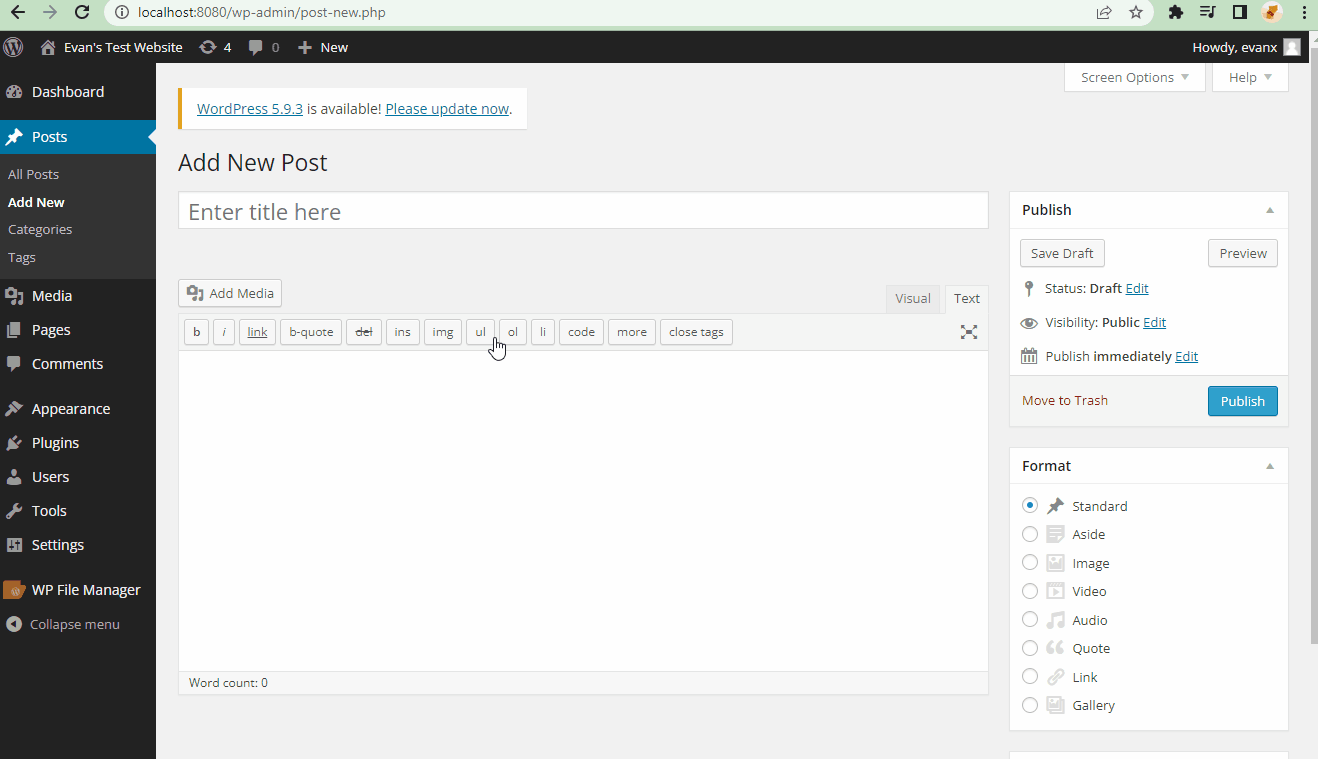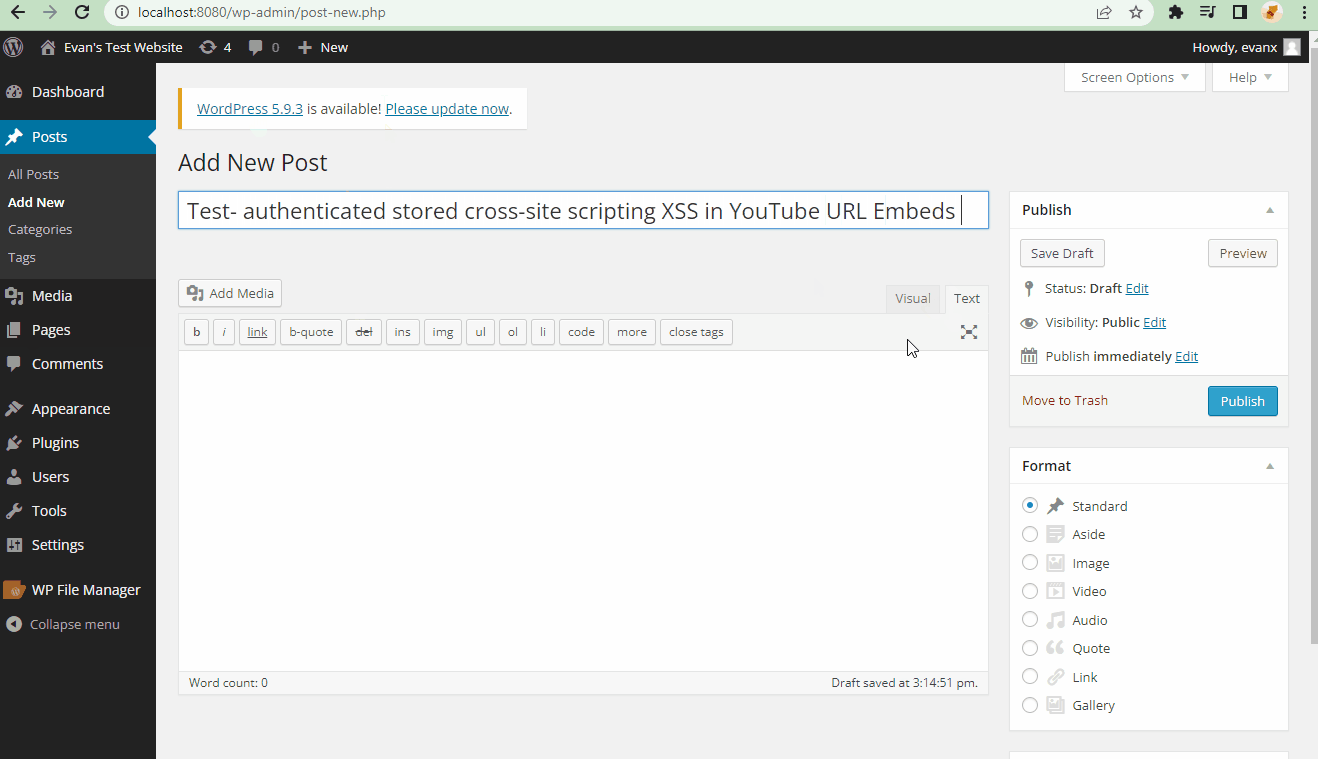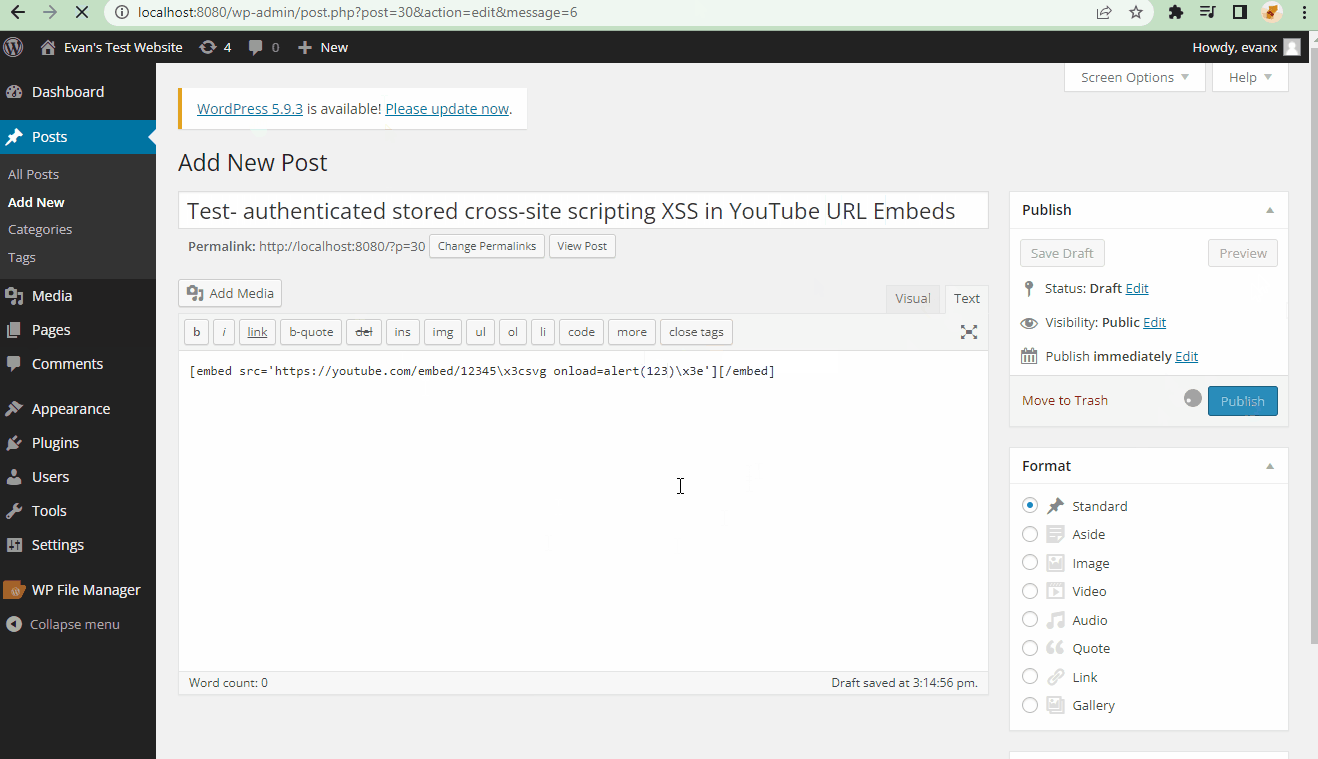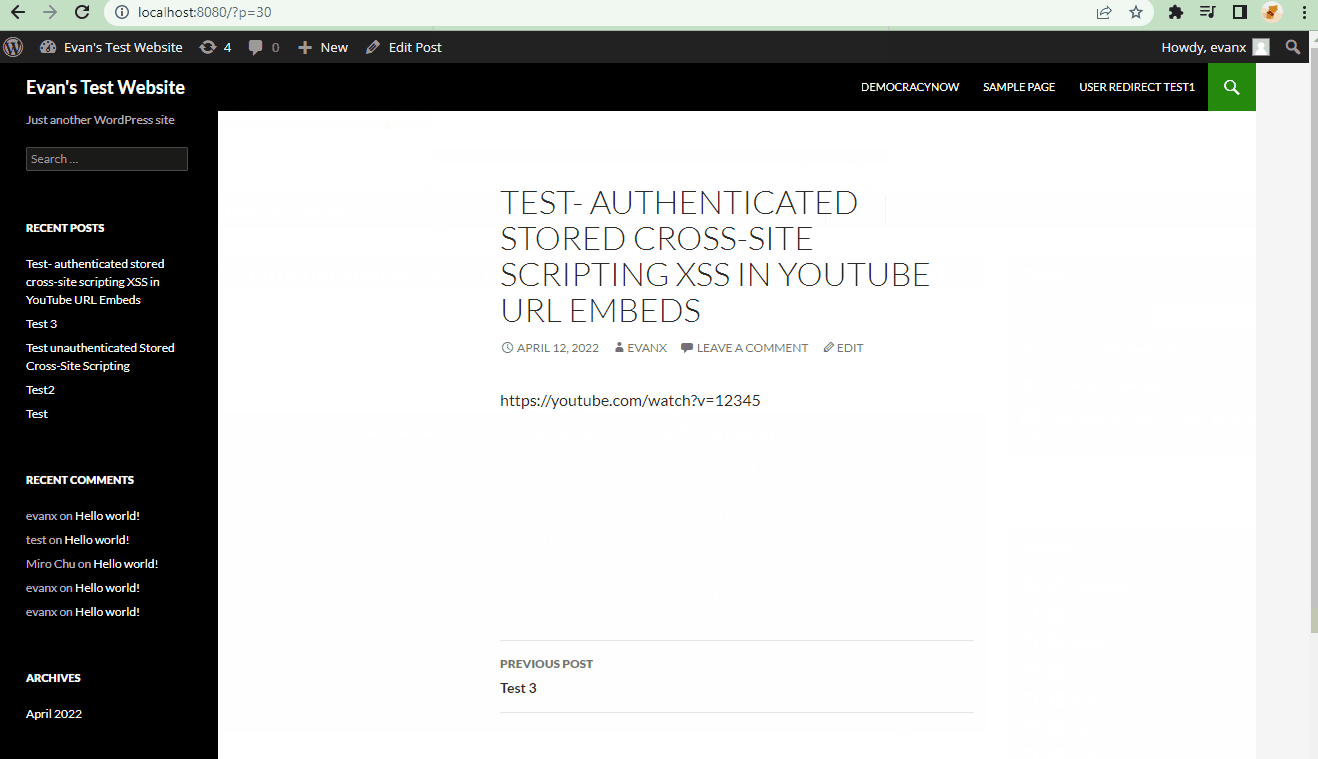
- Steps to recreate: A super user (admin) posts an embedded youtube URL link that contains a compromised script. A window will populate whenever a user refreshes the page.
- Affected source code:
[embed src='https://youtube.com/embed/12345\x3csvg onload=alert(123)\x3e'][/embed]
- Summary: An attacker exploits username and password enumeration vulnerabilities often in the login forms. In our case, an error messge similar to "the username is invalid or the username has the wrong password" is returned. This provides an attacker valuable information for other attacks.
- Vulnerability types: Username/Password Enumeration
- GIF Walkthrough: [Username Password Enumeration]
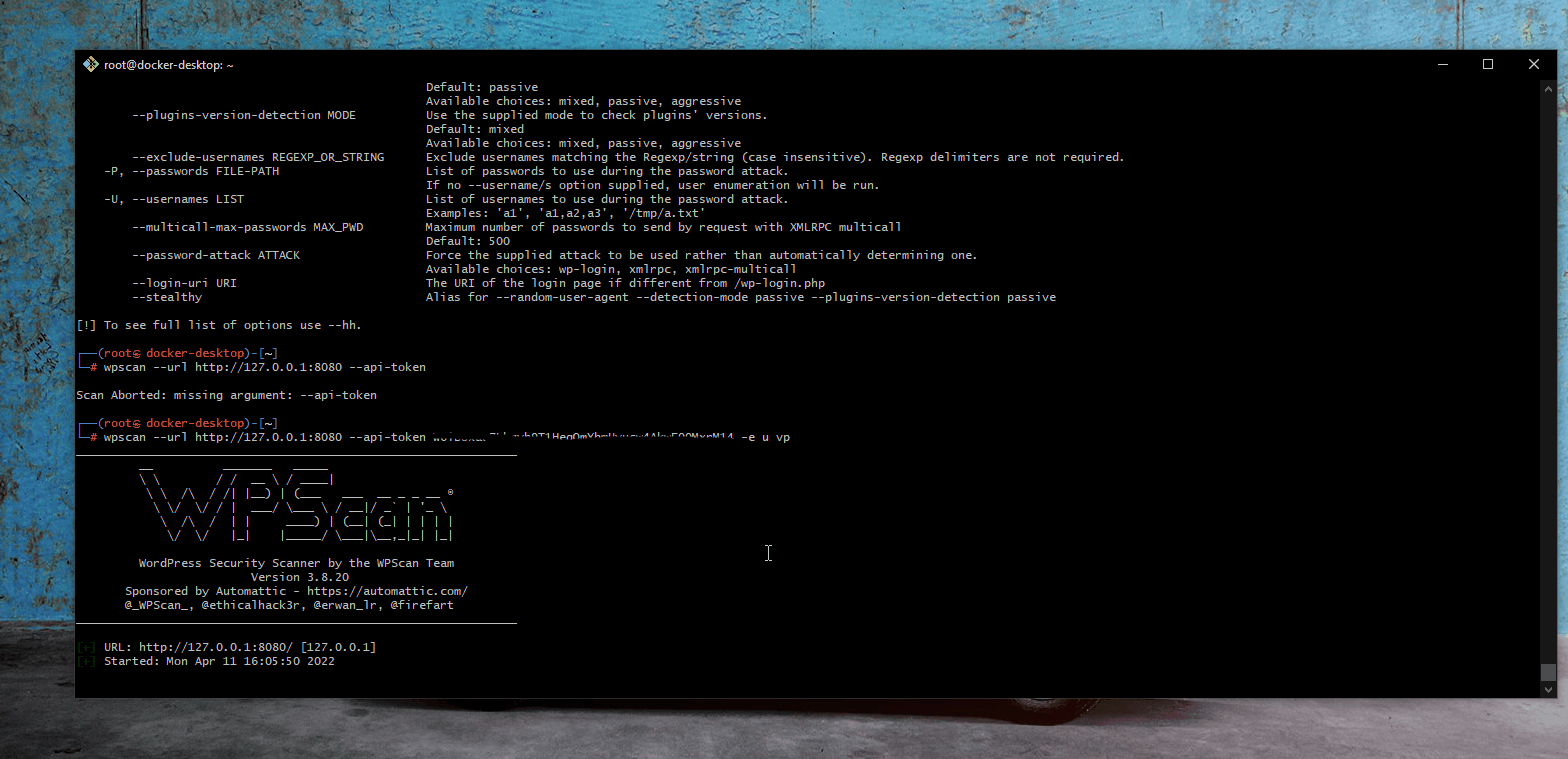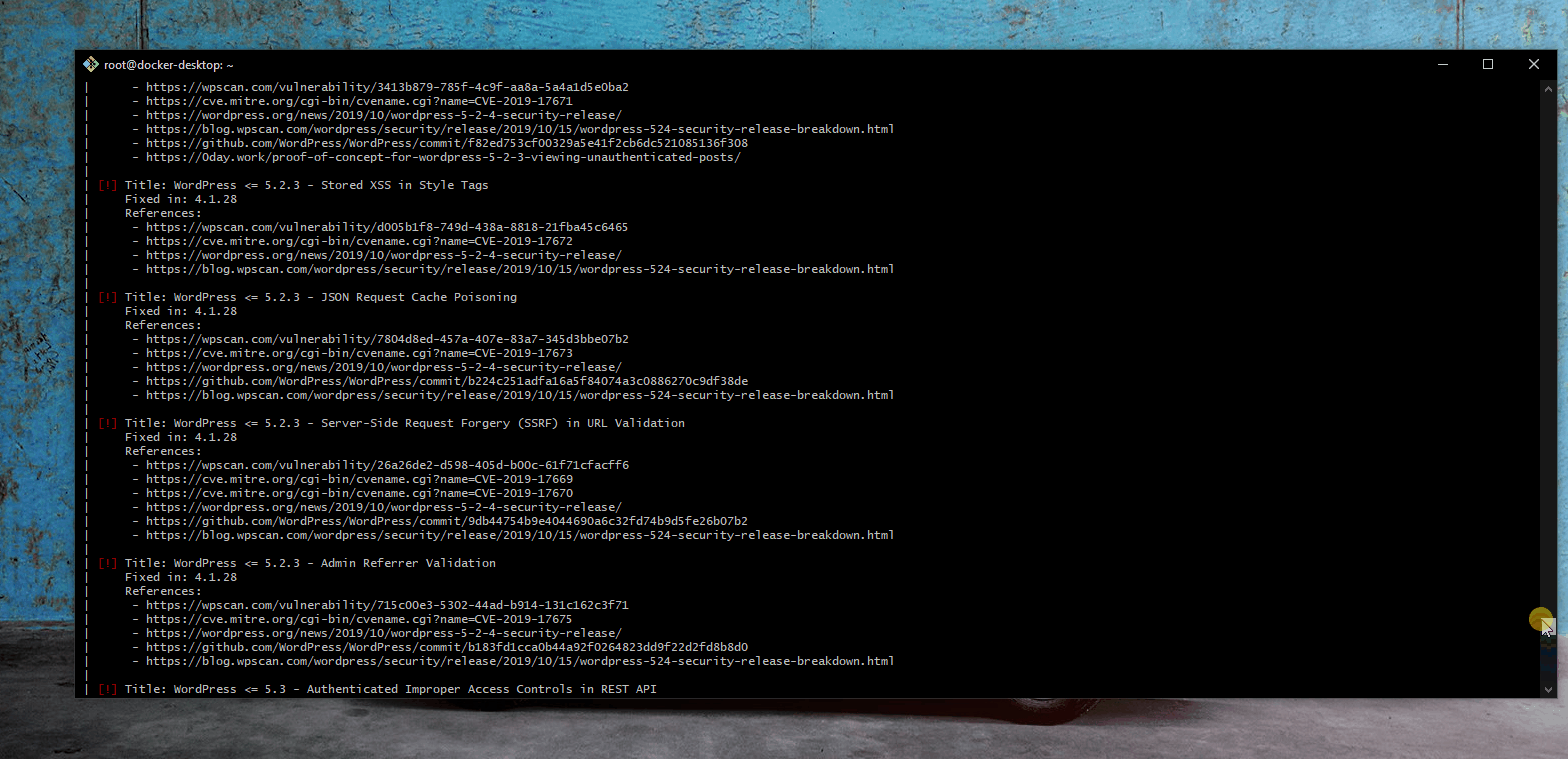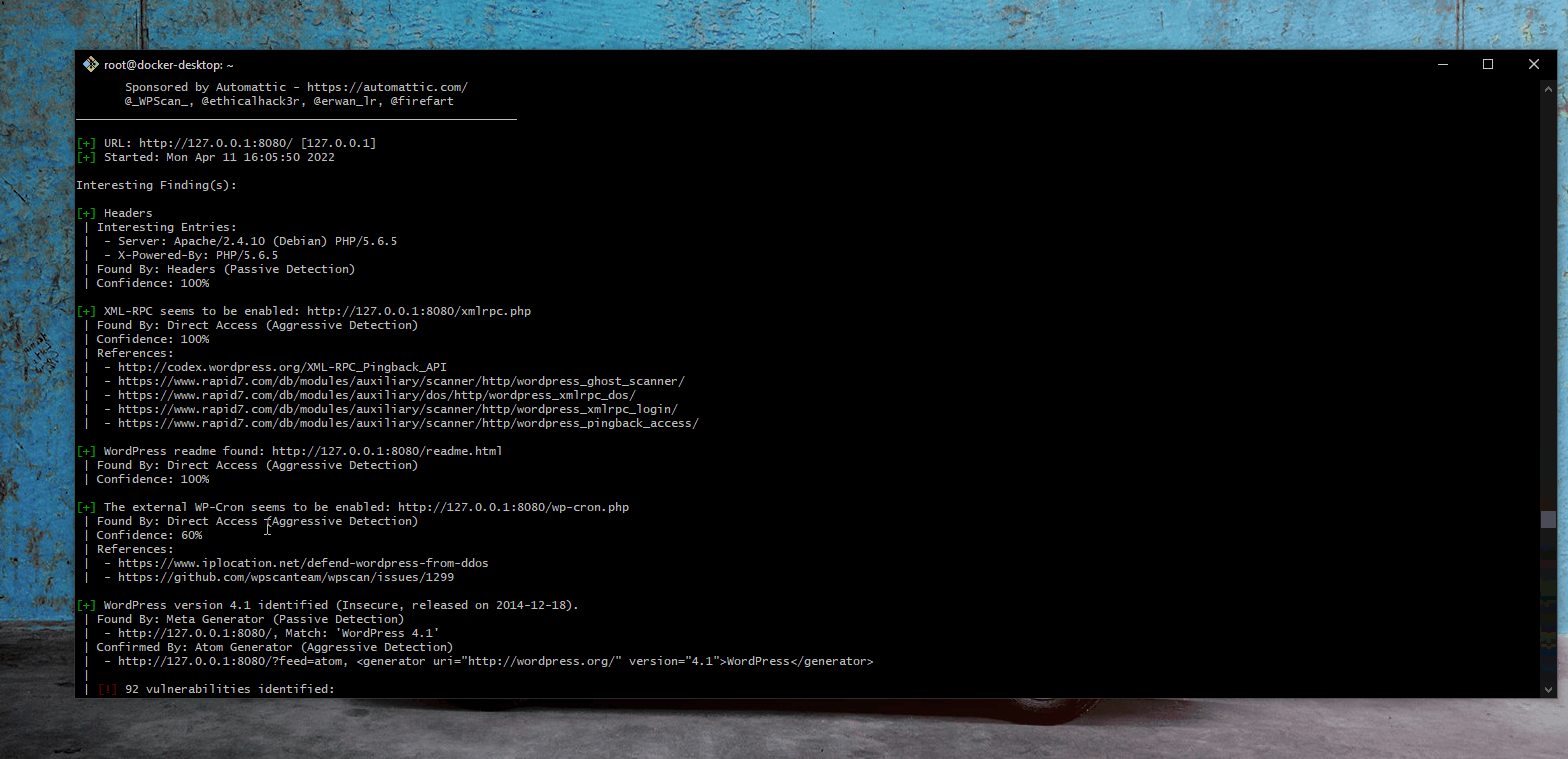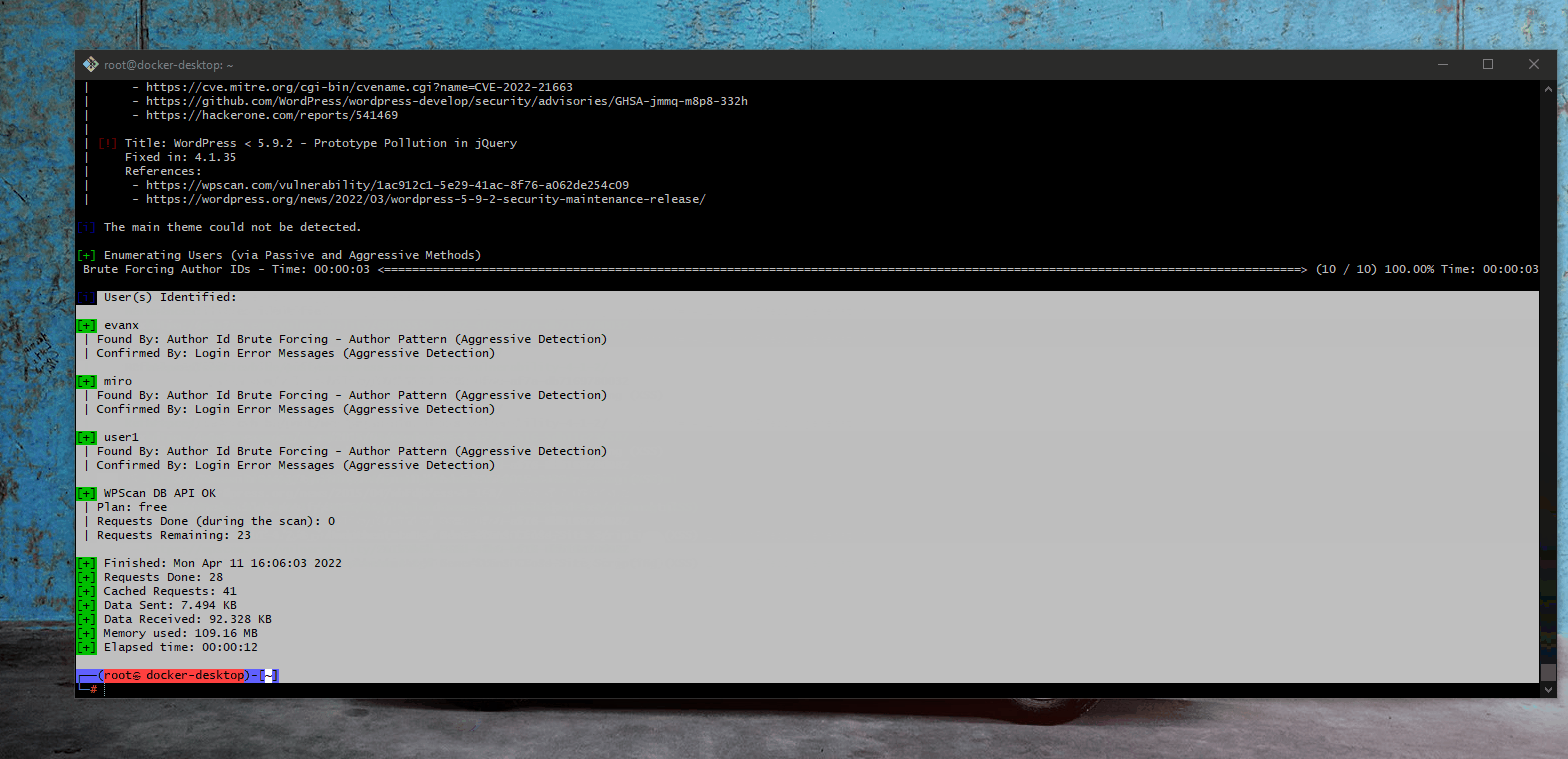
- [Docker Kali Setup]
- [Wpscan]
- Steps to recreate: 1. setup docker and Kali; 2. run wpscan for vulnerabilitites; 3. create password and username text files using Kali Linux command; 4. run wpsan with newly-created password and username files; 5. produce output
- Affected source code:
wpsan --url http:// YOUR OWN LOCALHOST --api-token YOUR OWN TOKEN -e u vp
- Summary: A compromised script may be planted in the comment area. Once an admin approves of the compromised comments. Whenver someone visits this page, the script would be triggered.
- Vulnerability types: XSS
- Tested in version: 4.1
- Fixed in version: 4.1.26
- GIF Walkthrough:
- Steps to recreate: A super user (admin) approves of a contributor's compromised comments or posts a message that is copied/pasted from somewhere. The comment contains malicious script that reveals the website's cookies. The attacker may steal the cookies with ease and thus has access to stored information.
- Affected source code:
<script>alert(document.cookie) </script>
List any additional assets, such as scripts or files
GIFs created with ScreenToGif.
Describe any challenges encountered while doing the work There are many wonderful lessons learned from this project: 1. set up local environment for Docker/Kali/WPSCAN/Tokens; 2. practice and solidify learned hacking skills; 3. hands-on hacking: XSS, CSRF, insecure design, url manipulation, burp etc.
Copyright [2022] [Evan Xu]
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.