This project demonstrates how to set up a user for each ELK service and store user credentials in keystores.
Brief video explanation: https://github.com/evermight/elk-docker-compose-keystore
Full video explanation: TBD
- Type
docker-compose up --build -d. - Go to kibana at
https://<ip address of server>:5601 - Login with
elasticand the password found in the.envfile. - Go to Fleet > Settings.
- Run the
./get-cert-details.shto determine your CA finger print and your CA. - Populate the information as shown in this screenshot:
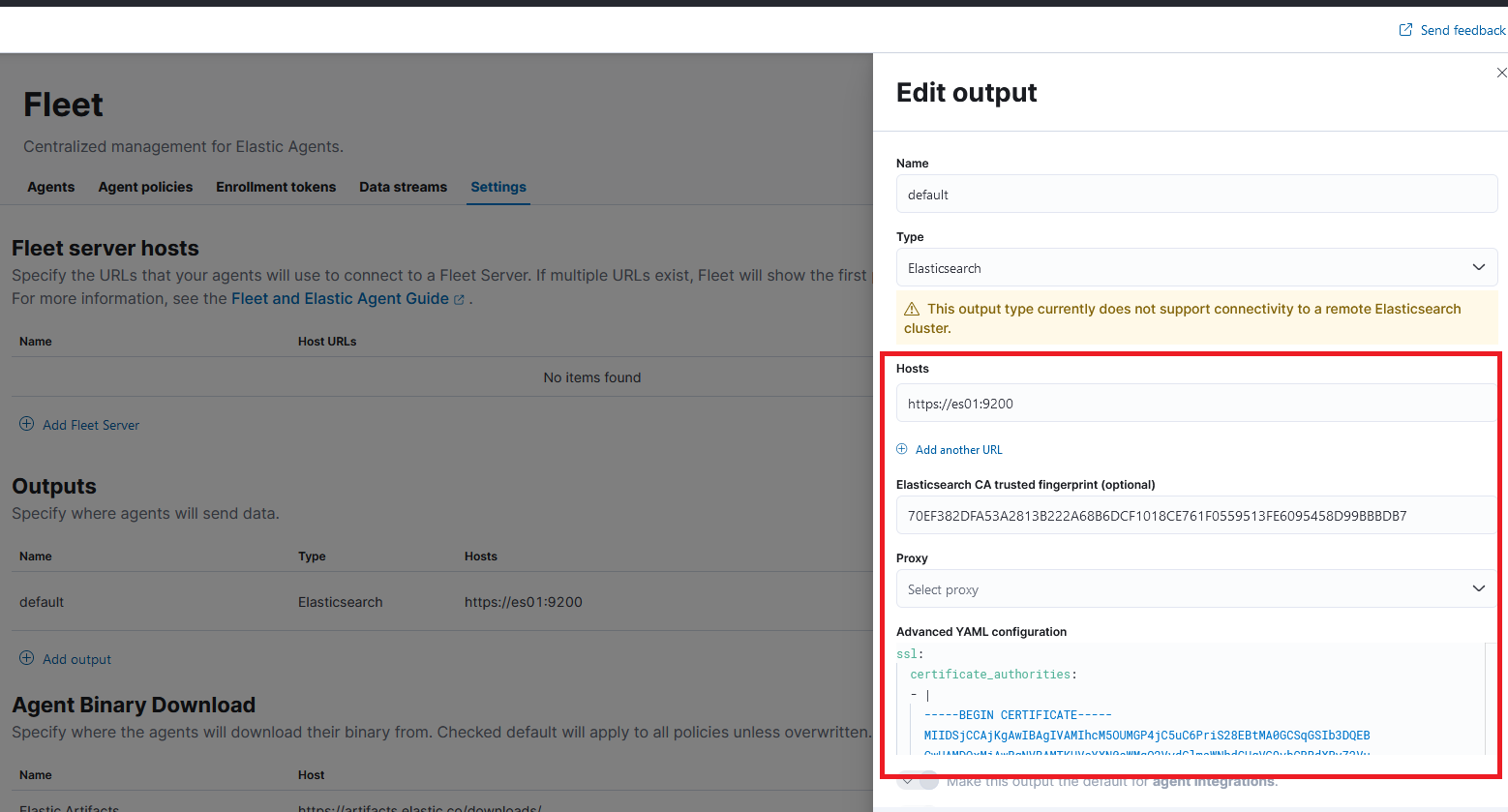
- Press save.
- Ensure everything is operational: metricbeat, filebeat, logstash, APM.
You can now remove any secrets from your .env file and also change the password for the elastic user.
- Go to your
.envfile and replaceELASTIC_PASSWORD, APM_PASS, ENCRYPTION_KEYwith fake data. Do NOT delete these variables because I haven't done enough "null" and "empty" checks in my bash scripts. The more important point is that these variables are no longer used. - Go to your
docker-compose.ymlfile and delete the lineELASTICSEARCH_PASSWORDfrom the environment of thees01container. It's not used any more. - Go to your
docker-compose.ymlfile and delete the linesKIBANA_*from the environment of thefleet-servercontainer. It's not used any more. - Go to Kibana Stack Management > Users and change the password for the
elasticuser so that no one can use it again. You can change the password forelasticunder Stack Management.