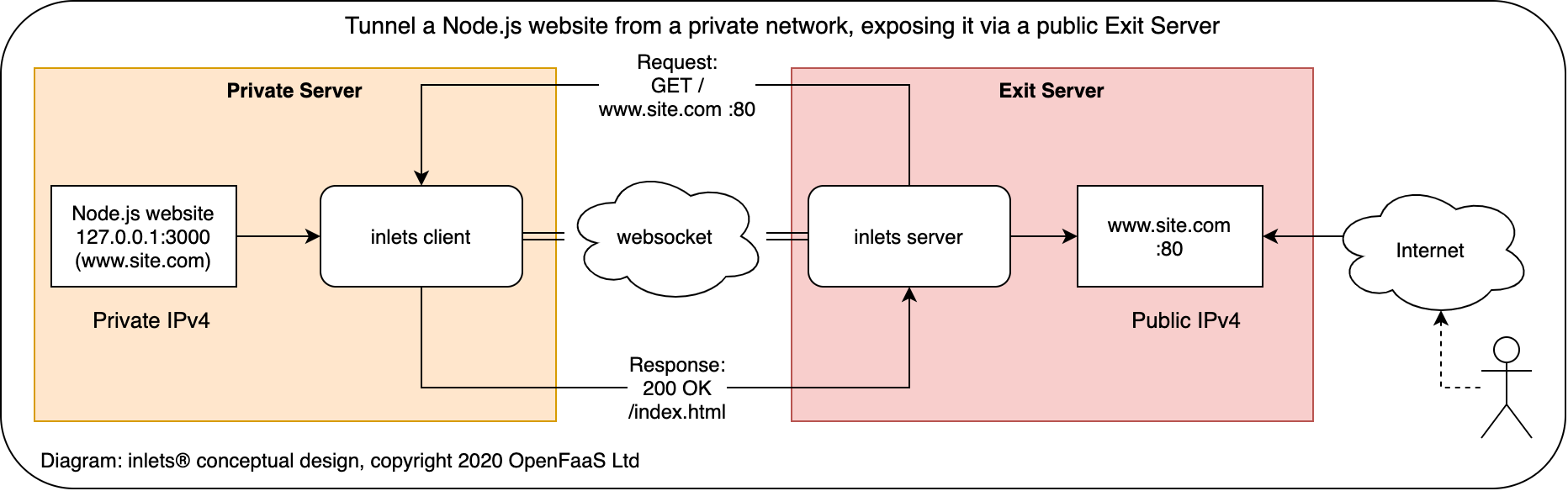
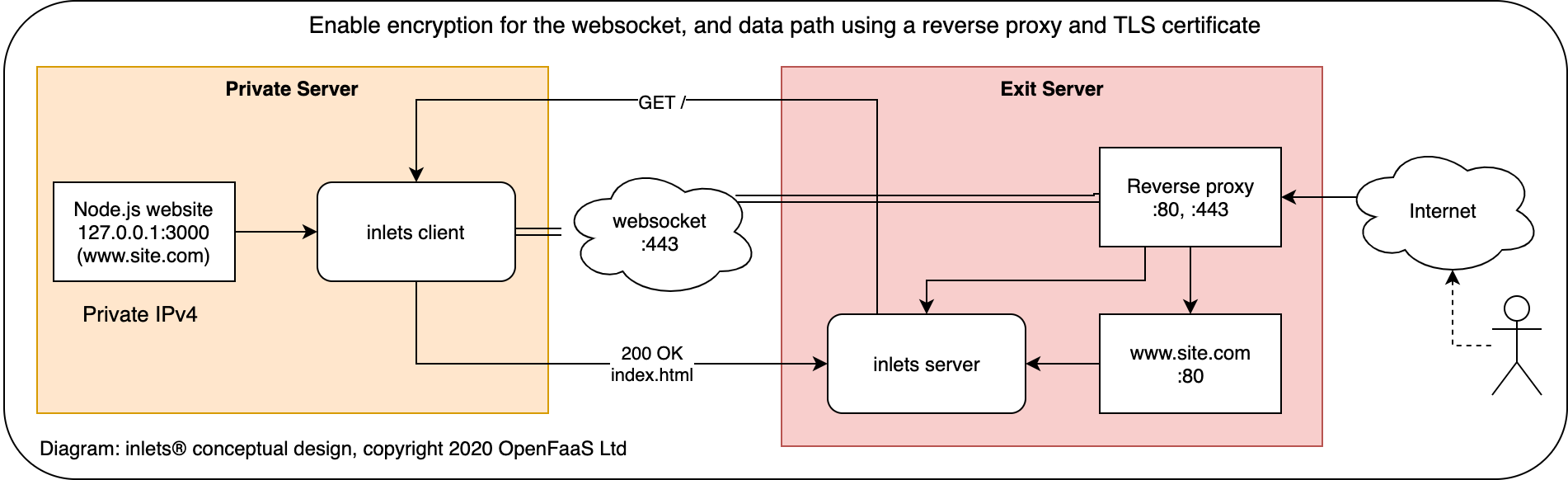
Expose your local endpoints to the Internet or to another network, traversing firewalls, proxies, and NAT.
inlets® combines a reverse proxy and websocket tunnels to expose your internal and development endpoints to the public Internet via an exit-server. An exit-server may be a 5-10 USD VPS or any other computer with an IPv4 IP address. You can also tunnel services without exposing them on the Internet, making inlets a suitable replacement for a VPN.
Why do we need this project? Similar tools such as ngrok or Argo Tunnel from Cloudflare are closed-source, have limits built-in, can work out expensive, and have limited support for arm/arm64. Ngrok is also often banned by corporate firewall policies meaning it can be unusable. Other open-source tunnel tools are designed to only set up a single static tunnel. inlets aims to dynamically bind and discover your local services to DNS entries with automated TLS certificates to a public IP address over a websocket tunnel.
When combined with SSL - inlets can be used with any corporate HTTP proxy which supports CONNECT.
Conceptual diagram for inlets
inlets is brought to you by Alex Ellis. Alex is a CNCF Ambassador and the founder of OpenFaaS.
OpenFaaS® makes it easy for developers to deploy event-driven functions and microservices to Kubernetes without repetitive, boiler-plate coding. Package your code or an existing binary in a Docker image to get a highly scalable endpoint with auto-scaling and metrics. The project has around 21k GitHub stars, over 270 contributors and a growing number of end-users in production.
Head over to the new OpenFaaS Ltd SWAG store to get your very own branded inlets hoodie, t-shirt and mug.
Buy an Insiders Subscription to get regular updates on the inlets, openfaas, k3sup, arkade along with hints and tips on Go, Docker and Kubernetes.
Important
Developers wishing to use inlets within a corporate network are advised to seek approval from their administrators or management before using the tool. By downloading, using, or distributing inlets, you agree to the LICENSE terms & conditions. No warranty or liability is provided.
- automatically create endpoints on exit-server based upon client definitions
- multiplex sites on same port and websocket through the use of DNS / host entries
- link encryption using SSL over websockets (
wss://) - authentication for server and client
- automatic reconnect
- native multi-arch with ARMHF/ARM64 support
- Dockerfile and Kubernetes YAML files
- discover and implement
Servicetype ofLoadBalancerfor Kubernetes - inlets-operator - tunnelling websocket traffic in addition to HTTP(s)
- get a logo for the project
- TLS certificates when used with a reverse proxy like Nginx, Caddy or Traefik
The following features / use-cases are covered by inlets.pro.
- Tunnel L4 TCP traffic in addition to HTTP/s at L7
- Automated TLS - including via inletsctl/inlets-operator
- Commercial services & support
Unlike HTTP 1.1 which follows a synchronous request/response model websockets use an asynchronous pub/sub model for sending and receiving messages. This presents a challenge for tunneling a synchronous protocol over an asynchronous bus.
inlets 2.0 introduces performance enhancements and leverages parts of the Kubernetes and Rancher API. It uses the same tunnelling packages that enable node-to-node communication in Rancher's k3s project. It is suitable for development and may be useful in production. Before deploying inlets into production, it is advised that you do adequate testing.
Feel free to open issues if you have comments, suggestions or contributions.
- The tunnel link is secured via
--tokenflag using a shared secret - The default configuration uses websockets without SSL
ws://, but to enable encryption you could enable SSLwss:// - A timeout for requests can be configured via args on the server
The upstream URL has to be configured on both server and client until a discovery or service advertisement mechanism is addedThe client can advertise upstream URLs, which it can serve- The tunnel transport is wrapped by default which strips CORS headers from responses, but you can disable it with the
--disable-transport-wrappingflag on the server
Inlets is a Cloud Native Tunnel and is listed on the Cloud Native Landscape under Service Proxies.
- inlets - Cloud Native Tunnel for L7 / HTTP traffic written in Go
- inlets-pro - Cloud Native Tunnel for L4 TCP
- inlets-operator - Public IPs for your private Kubernetes Services and CRD
- inletsctl - Automate the cloud for fast HTTP (L7) and TCP (L4) tunnels
You can install the CLI with a curl utility script, brew or by downloading the binary from the releases page. Once installed you'll get the inlets command.
Note:
inletsis made available free-of-charge, but you can support its ongoing development and sign up for updates through GitHub Sponsors 💪
Utility script with curl:
# Install to local directory
curl -sLS https://get.inlets.dev | sh
# Install to /usr/local/bin/
curl -sLS https://get.inlets.dev | sudo shVia brew:
brew install inletsNote: the
brewdistribution is maintained by the brew team, so it may lag a little behind the GitHub release.
Binaries are made available on the releases page for Linux (x86_64, armhf & arm64), Windows (experimental), and for Darwin (MacOS). You will also find SHA checksums available if you want to verify your download.
Windows users are encouraged to use git bash to install the inlets binary.
Using inlets I was able to set up a public endpoint (with a custom domain name) for my JavaScript & Webpack Create React App.
You can run inlets between any two computers with connectivity, these could be containers, VMs, bare metal or even "loop-back" on your own laptop.
Try the quickstart tutorial now on your local computer.
inlets and inlets PRO now has a dedicated documentation site:
Official docs: docs.inlets.dev
Other inlets OSS documentation & tutorials:
HTTPS for your local endpoints with inlets and Caddy
You can add TLS to inlets using a simple reverse proxy like Caddy or Nginx, alternatively you can use inlets PRO which adds TLS encryption automatically.
- Docs: Quickstart tutorial on your laptop
- Docs: Inlets & Kubernetes recipes
- Docs: Run Inlets on a VPS
- Tutorial: Get a LoadBalancer for your private Kubernetes cluster with inlets-operator
See also: advanced usage of inlets including Docker, Kubernetes, multiple-services, and binding to private IPs
Read community tutorials, the launch posts on Hacker News, and send a PR if you have written about inlets or inlets PRO:
You can share about inlets using
@inletsdev,#inletsdev, andhttps://inlets.dev.
See ADOPTERS.md for what companies are doing with inlets today.
See CONTRIBUTING.md
kubectl port-forward- built into the Kubernetes CLI, forwards a single port to the local computer.- kubefwd - Kubernetes utility to port-forward multiple services to your local computer.
- kurun - Run main.go in Kubernetes with one command, also port-forward your app into Kubernetes.
inlets® is a registered trademark of OpenFaaS Ltd. All rights reserved, registered company in the UK: 11076587