Access Control software written for FamiLAB.
- Badge scanner and door unlock trigger.
- Microcontroller written in CircuitPython.
- Reads badge, calls auth server, if ✅ then open door.
See nfc/README.md
- HTTP server written in Typescript.
- Exposes
/accessendpoint. /accessendpoint fetches badge list from Google Sheets for validation.
See api/README.md
- Install Node 18+
- Globally install
pnpmnpm install --global pnpm
- Install Node packages
pnpm install
- Follow Development Setup instructions for the sub-project you wish to work on.
The Docker image is built via GitHub Actions whenever a new commit is merged into the release/v4 branch. The image is
therefore tagged ghcr.io/familab/accesscontroller:release-v4.
The server application is composed of multiple docker containers defined by the ./access-controller.stack.yml Docker
Stack. To deploy this file to the server, you must have a Docker Context set up locally, and then update the Stack using
the stack file.
On your local machine, create a new Docker Context for the access controller server.
docker context create familab.accesscontroller --docker "host=ssh://familab@accesscontroller.familab.lan.local"
docker context use familab.accesscontrollerOnce you run these commands all docker * commands you use will target the remote server.
You can always switch back to targeting your local machine by running:
docker context use defaultOnce you have a Docker Context set up for the remote server, run the following command to push the Stack.
docker stack deploy -c "./access-controller.stack.yml" access-controllerMake sure to check the logs of the containers to ensure the deployment worked.
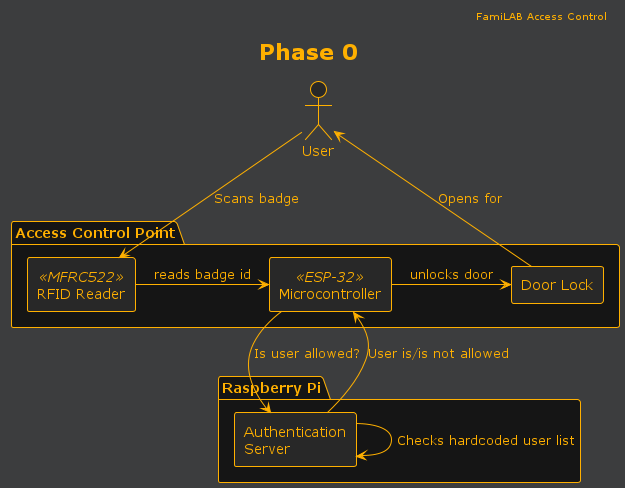
Currently implementing Phase 0.
Phase 0 is the absolute minimum functionality that allows badge access to the new facility. It is not meant to be long-term, it is not meant to be well-designed. Has the minimum number of infrastructure dependencies.
- Working door lock
- ACP that can read badges and unlock door
- WiFi network without Internet
- User scans badge
- ACP calls Auth Server with badge and location
- Auth Server checks against hardcoded list and responds ✅/❌
- If user has access, ACP triggers relay to unlock door
- ACP: ESP-32 and MFRC522 connected on a breadboard, possibly powered by USB
- Auth Server: Living on a raspberry pi or something
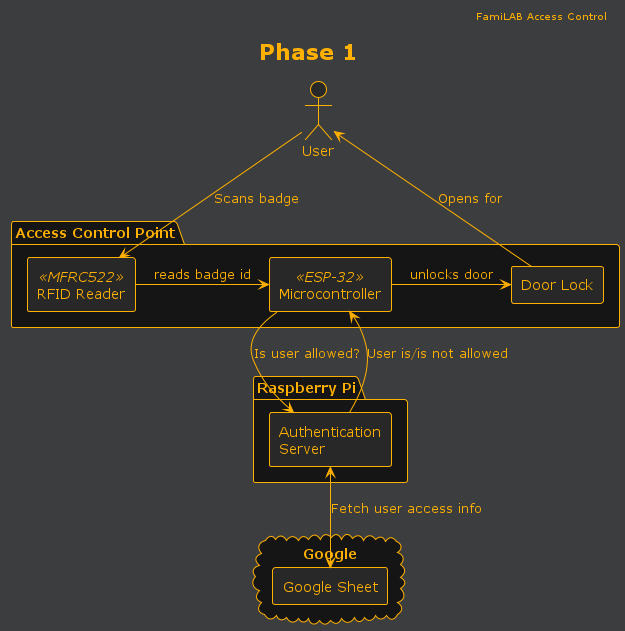
This is the first real version of the access control system.
- 12/24v DC power line run to the door location
- Internet access
- User scans badge
- ACP calls Auth Server with badge and location
- Auth Server fetches Google Sheet contents (or checks cache) and responds ✅/❌
- If user has access, ACP triggers relay to unlock door
- ACP: MFRC522 mounted outside door, ESP32 mounted inside. Powered by hardwired DC.
- Auth Server: Can still be on temp hardware, but now has internet access.
Some enhancements that can be made in the future, fairly independently.
- Manufactured PCB
- External antenna for MFRC522
- Status LED/display
- Centralized relay board that powers all door locks
- ACP would then not be responsible for door lock, just communicating with auth server
- All power control in one place
- Allows for remote opening of doors, doors unlocked for open house, etc.
- Permanent hosting infrastructure, more reliable server than Raspberry Pi
- Internal DNS hostname would allow for TLS, reduces sniffing/man-in-the-middle attacks
- Put all access control devices on separate subnet/vlan, improves network security