This tool is to solve CTF decoding baby first Problem. Give me your cipher, and i will decrypt/decode it!
Inspiration from kaibro's EasyWebSolver
- Brute force all possible encode
- Specifie FLAG header
- If find the FLAG, automatic copy to your clipboard
- Brute force Classical cipher supported
- Specifie FLAG header as your custom list
python2.7 & pip2
- Clone this repo
git clone https://github.com/finn79426/EzCryptSolver.git- Using pip to get essential libraries
cd EzCryptSolver
pip2 install -r requirements.txt --userFor example (Base64):
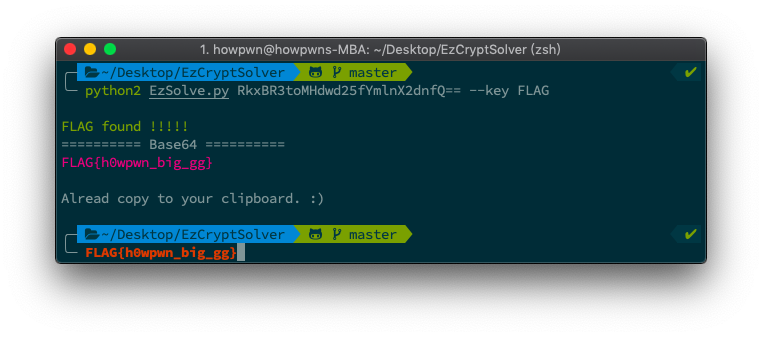
python2 EzSolve.py RkxBR3toMHdwd25fYmlnX2dnfQ==Now, you will get output like this:
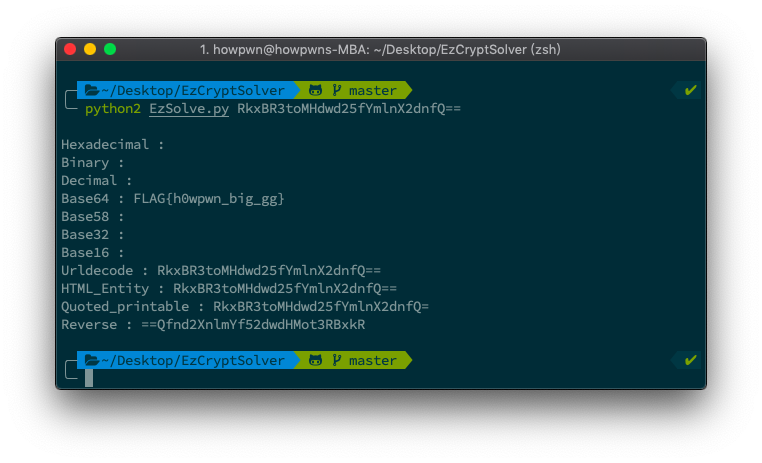
And also, you can specifie CTF FLAG header, just add --key argument.
python2 EzSolve.py RkxBR3toMHdwd25fYmlnX2dnfQ== --key FLAGNow, you will get output like this:
If not find any compare FLAG, just no output.
If your ciphertext has white-space or any special character, Enclose them in quotation marks, otherwise you will get an Error.
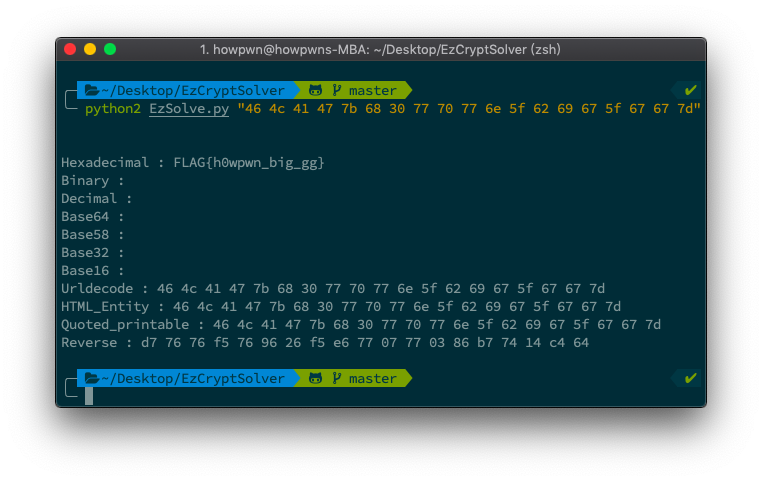
python2 EzSolve.py "46 4c 41 47 7b 68 30 77 70 77 6e 5f 62 69 67 5f 67 67 7d"You can preparatory CTFs FLAG header, so you don't have to use --key anymore!
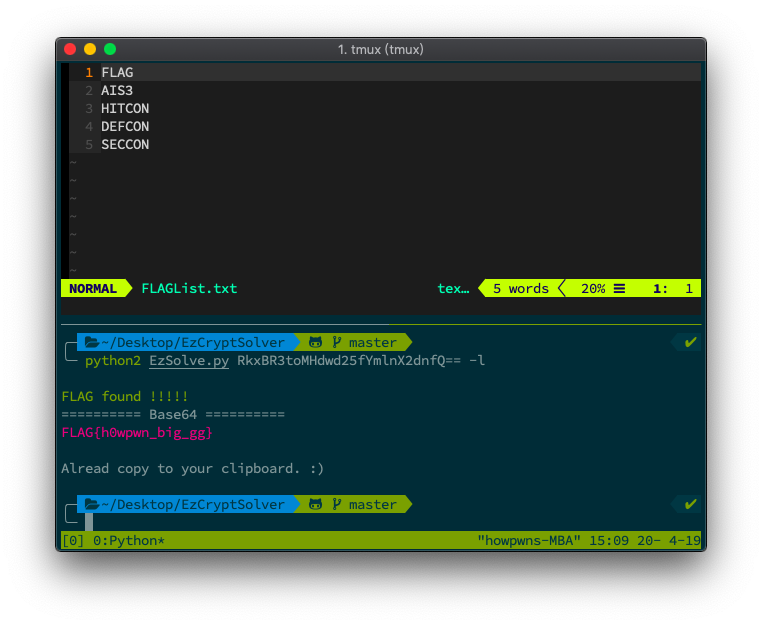
Add -l to enable longlist support:
python2 EzSolve.py RkxBR3toMHdwd25fYmlnX2dnfQ== -l
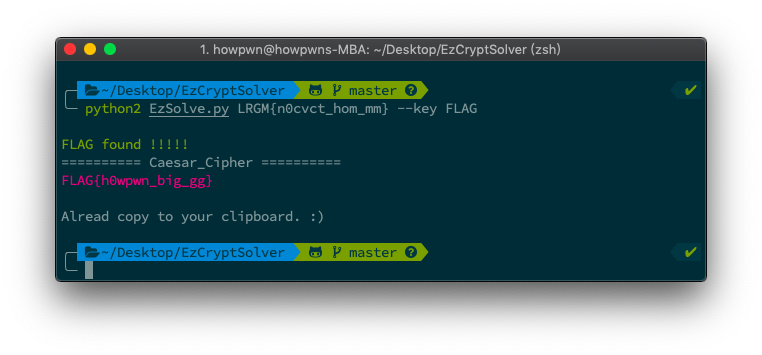
By the way, Only using --key or -l can get Brute Force output, like this:
python2 EzSolve.py LRGM{n0cvct_hom_mm} --key FLAG
- Encode transform
- Hex
- Binary
- Decimal
- Base64
- Base58
- Base32
- Base16
- URLencoded
- HTML Entity
- Quoted-printable
- Brute force (Enable when using
-lor--key)- Transposition Cipher
- Caesar cipher
- Others
- Reverse String
My Email:finn79426@gmail.com
如果你找到 Bug 或 Error msg,發給我一個 issues
或者如果你有更好的想法,歡迎 Fork、PR
pip2 uninstall -r requirements.txt --yes
cd ../
rm EzCryptSolve -r