Enables a token owner to keep it separately for use in services that require it.
If you want to share your Google Photos or Youtube Library outside of those apps you have to share your Google Account credentials. This is not safe and not recommended. This app allows you to keep your Google Auth Token separately and use it in other apps that require it.
- Authentication: Setup with Amazon Cognito for secure user authentication.
- API: Integration with API Gateway.
- Database: Real-time database powered by Amazon DynamoDB.
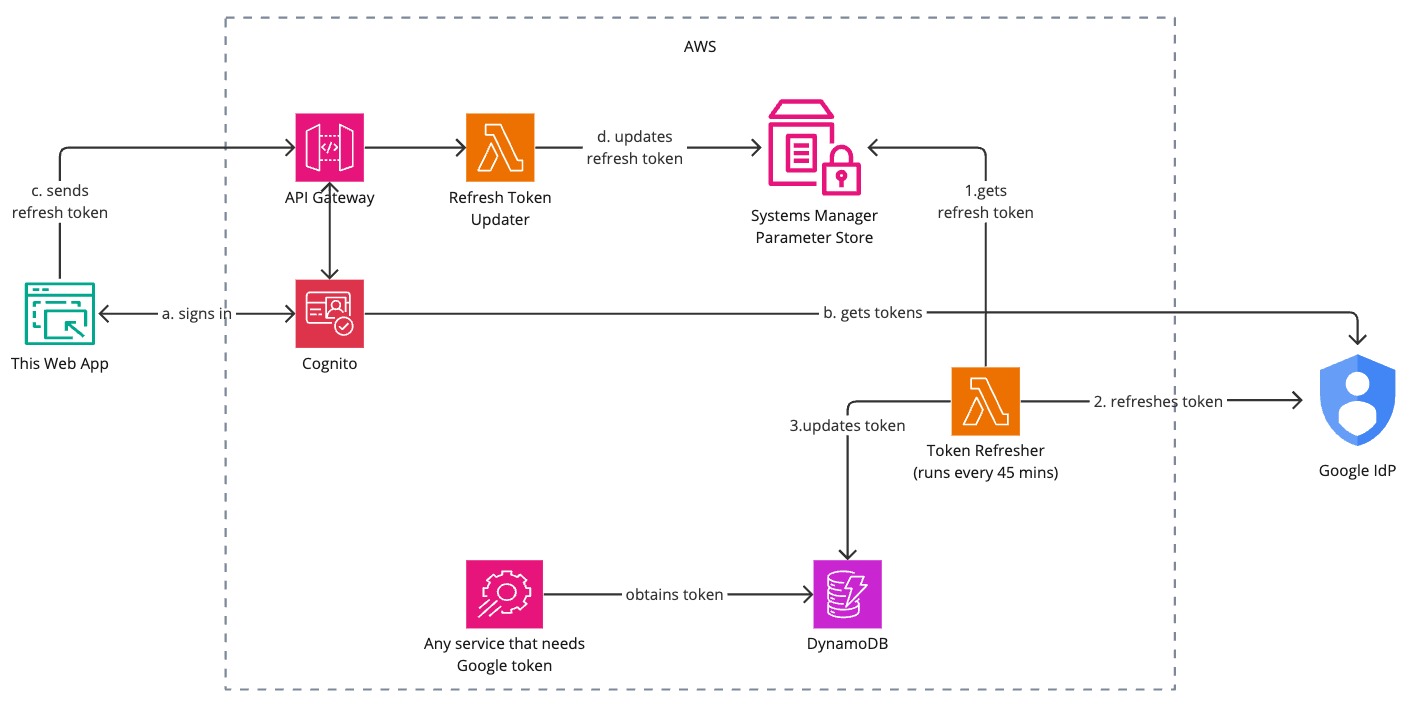
User installs the webb app onto their phone and enables Push Notifications. Then the flow goes as follows:
- (a, b) User logs in with their Google Account and authorizes the app to access their Google Photos and Youtube Libraries. As a result user obtains the Google Auth Tokens (including refresh_token).
- (c, d) User submits the Google Auth refresh_token to the AWS SSM Parameter Store where it is kept securely.
On a periodic basis (every 45 minutes) a dedicated lambda function refreshes Google Auth Token using refresh_token and stores it in the DynamoDB database. If the refresh_token is invalid the user is notified via Push Notification so that they can re-authorize the app repeating the Phase One.
Any other app that requires Google Auth Token can obtain it from the DynamoDB database.
In order to deploy the solution you need to have the following:
- Initiate an empty Amplify project.
- Configure Google App
and add Authorization Scopes.
This solution is configured to get access to Google Photos and Youtube Libraries. So the scopes would be:
https://www.googleapis.com/auth/photoslibrary.readonlyhttps://www.googleapis.com/auth/youtube.readonly
- Caveat: You will need to add your Google account to the list of test users in the Google Developer Console in order to allow those scopes.
- Generate web push keys with
npx web-push@latest generate-vapid-keys - Setup secrets:
APP_ID: Amplify App IDGOOGLE_CLIENT_ID: Google App IDGOOGLE_CLIENT_SECRET: Google App SecretWEB_PUSH_PUBLIC_KEY: Public Key for web pushWEB_PUSH_PRIVATE_KEY: Private Key for web push
- Connect the repository to the Amplify app.
In order to successfully deploy the solution to a sandbox you must provide APP_ID secret with npx ampx sandbox secret set APP_ID.
See CONTRIBUTING for more information.
This project is licensed under the MIT-0 License. See the LICENSE file.