This is a Amazon EC2 Container Service reference architecture with cloudformation templates that will provision a complete ECS environment with many advanced optional features:
- standalone service-only ECS environment (simple provisioning)
- ECS Windows Container(simpole provisioning)
- ECS CI/CD with Code* and Cloudformation
- ECS Service Autoscaling and ECS instances host Autoscaling triggered by Cloudwatch alarms
- Log Consolidation with awslogs driver
- ECS Events to CloudWatch Events and eventually go to SNS
- Spot Fleet support
- ASG scaling in triggering ECS container instance draining(link)
- [NEW] credentials management with EC2 Parameter Store(link)
This cloudformation template will provision common Amazon ECS infrastructure including:
- VPC, IGW, subnets, routing tables, security groups
- IAM role
- Autoscaling Group and Launch Configuration
- Lambda function as custom resource to query latest ECS AMI ID
- ECS Service, Cluster, Task Definition
- Caddy as the default web server
click the button to launch the demo stack in us-west-2
check the cloudformation output and click the LoadBalancerURL link to see the result.
For Amazon ECS Windows Container, please click the button below:
- By default this template will create spot instance(m3.medium). If you need on-demand instance instead, specify SpotPrice parameter to "0"
Fork this GitHub repository(https://github.com/pahud/ecs-cfn-refarch) into your GitHub account.
From your terminal application, execute the following command (make sure to replace <your_github_username> with your actual GitHub username):
git clone https://github.com/<your_github_username>/ecs-cfn-refarch
This creates a directory named ecs-cfn-refarch in your current directory, which contains the code for the Amazon ECS sample app unser src directory.
click the button to launch the demo stack in us-west-2
The CloudFormation template requires the following parameters:
- GitHub configuration
- CodeBuildEnvironment: CodeBuild environment.
- GitHubBranch: The branch of the repo to deploy continuously. Leave it as default "master"
- GitHubRepo: The name of the github repo to deploy continuously. Leave it as default "ecs-cfn-refarch"
- GitHubToken: Token for the user specified above. (https://github.com/settings/tokens)
- GitHubUser: Your username on GitHub.
- ServiceName: Your ECS Service name.
- UseCodeCommit: If you use CodeCommit instead, select "yes" and ignore all GithHub parameters above.
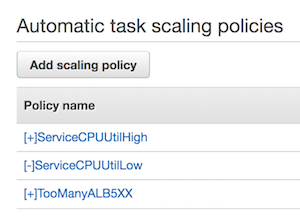
The Cloudformation template will generate a few Service Autoscaling policies for you:
The Autoscaling Group will scale out when:
- The CPUUtilization of EC2 instances within the Autoscaling Group is high
- The CPUReservation of ECS Cluster is high
- The MemoryReservation of ECS Cluster is high
UPDATE - This refarch will configure the hosts scaling policies just as Expedia's sharing in AWS Summit Santa Clara 2016(video).
Amazon ECS supports many docker log drivers, by default, this refarch will use awslogs and output consolidated logs to Amazon CloudWatch Logs.
All ECS Events from the ECS Cluster created by this cloudformation template will go to CloudWatch Events rule and then publish to SNS Topic. You can find the SNS Topic in the cloudformation outputs.
Monitor Cluster State with Amazon ECS Event Stream | AWS Compute Blog - https://aws.amazon.com/tw/blogs/compute/monitor-cluster-state-with-amazon-ecs-event-stream/
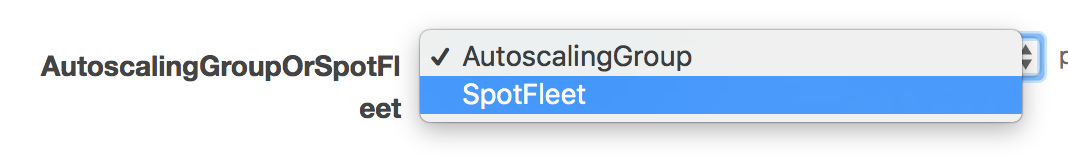
By default the ECS cluster in this refarch is provisioned by Autoscaling Group, alternatively, you can select SpotFleet in AutoscalingGroupOrSpotFleet cloudformation parameter.
When cloudformation provisions the ECS cluster with spot fleet, it will launch the spot instances with Diversified Allocation Strategy with instances type m3.medium, m4.large and c4.large. With the diversity of instance types and multi-AZ allocation, you would not risk losing all ECS cluster with the spot price is lower than the market price - the spot fleet will maintain the desired capacity for you.
Powering your Amazon ECS Clusters with Spot Fleet | AWS Compute Blog - https://aws.amazon.com/tw/blogs/compute/powering-your-amazon-ecs-clusters-with-spot-fleet/
By lauching the cloudformation template, it will provision an EC2 Parameter "ECSYourName" in Parameter Store for you alone with KMS Key and Alias(alias/myEcsKeyAlias). To create a new parameter with KMS encrypted, try the following commands:
$ ssm put-parameter --name ECSYourPassword --value password1234 --type SecureString --key-id alias/myEcsKeyAlias
And you can specify the optional "ECSYourName" in the cloudformation input parameter.
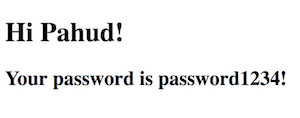
When the stack is created, try open the teting URL:
http://Your_LoadBalancerURL_IN_CloudFormation_Output/greeting.html
and you should be able to see this:
you can check this bootstrap startup.sh to see how it generates the credentials within the ECS Task. https://github.com/pahud/docker-caddy/blob/master/startup.sh
Managing Secrets for Amazon ECS Applications Using Parameter Store and IAM Roles for Tasks | AWS Compute Blog - https://aws.amazon.com/tw/blogs/compute/managing-secrets-for-amazon-ecs-applications-using-parameter-store-and-iam-roles-for-tasks/