act-splunk is a Splunk Add-on that adds workflow actions and external lookups towards the ACT platform.
The add-on is preconfigured to use an open, read only ACT instance with public data.
- Download the add-on from splunkbase.
or
- clone repository and build
./build.sh
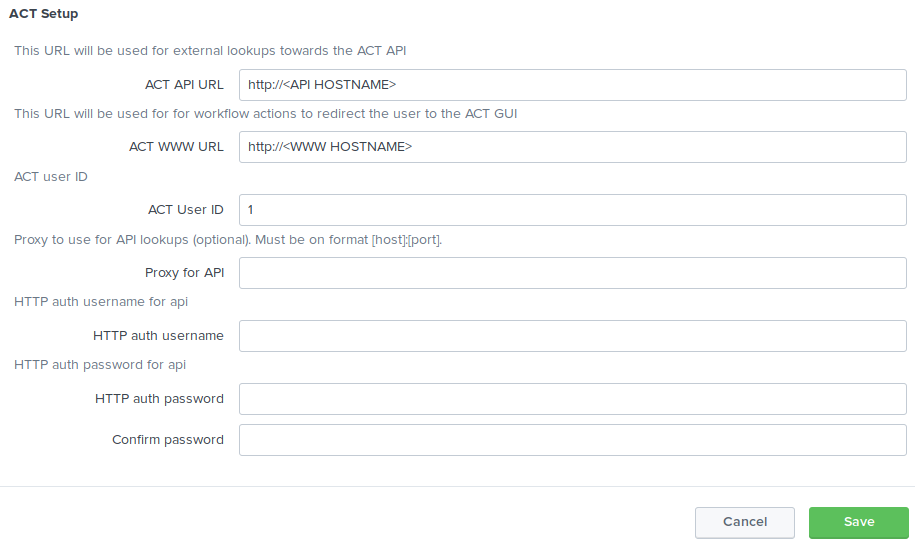
After installation, enter app > act > Set up to enter information on API and WWW hostname to connect to a running ACT instance.
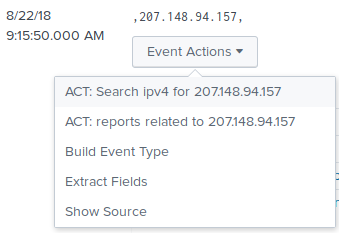
Within search result, you will find workflow actions on supported field. When clicking on a workflow action, you will be redirected to the ACT GUI.
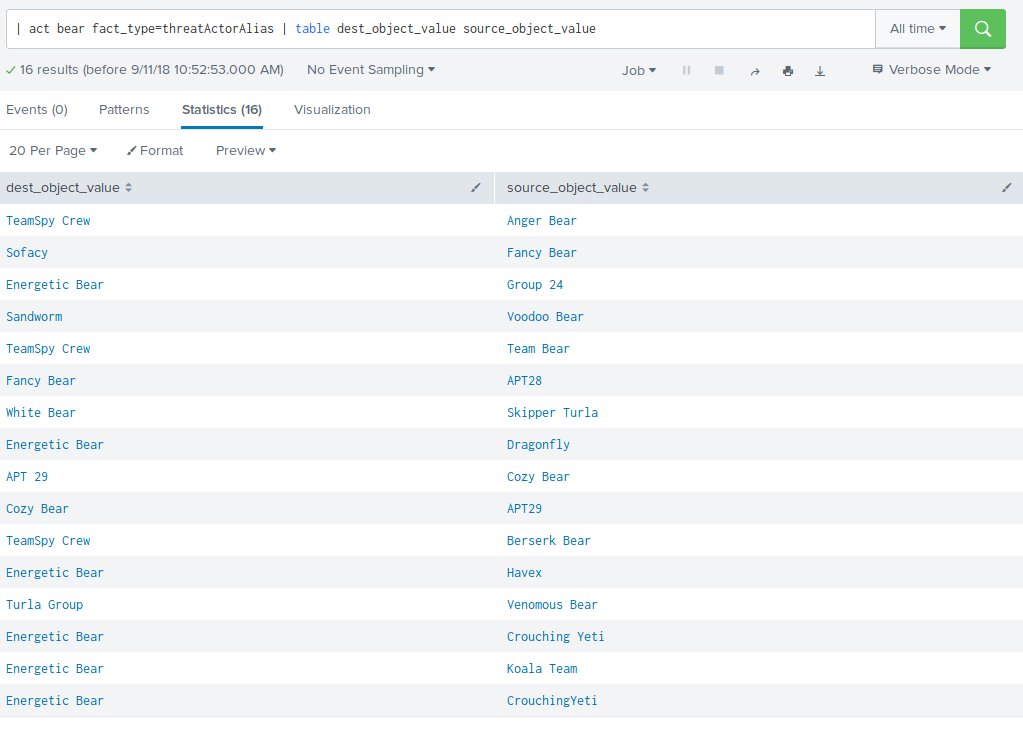
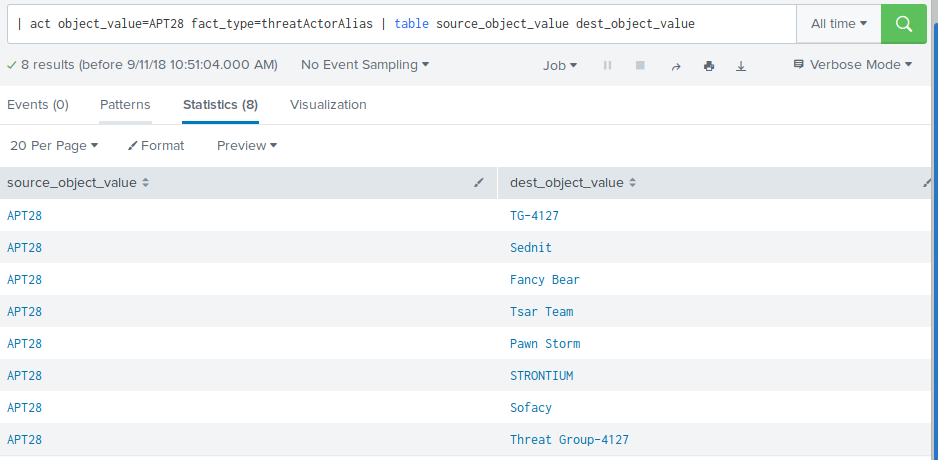
You can specify a generic search using the act command, to generate events based on an ACT query:
| act [<keyword>] [option=value] [option=value]
The follwoing options can be specified, using option=value to limit the search result.
- limit (default=25)
- fact_type
- fact_value
- object_type
- object_value
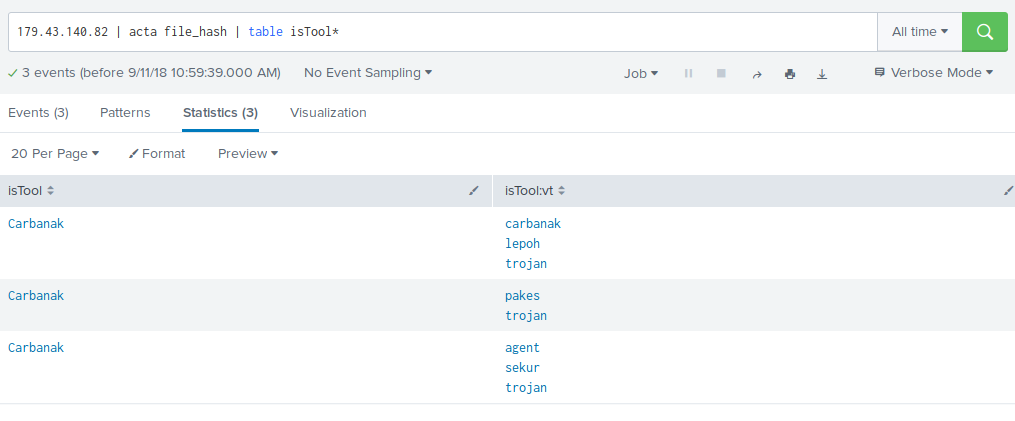
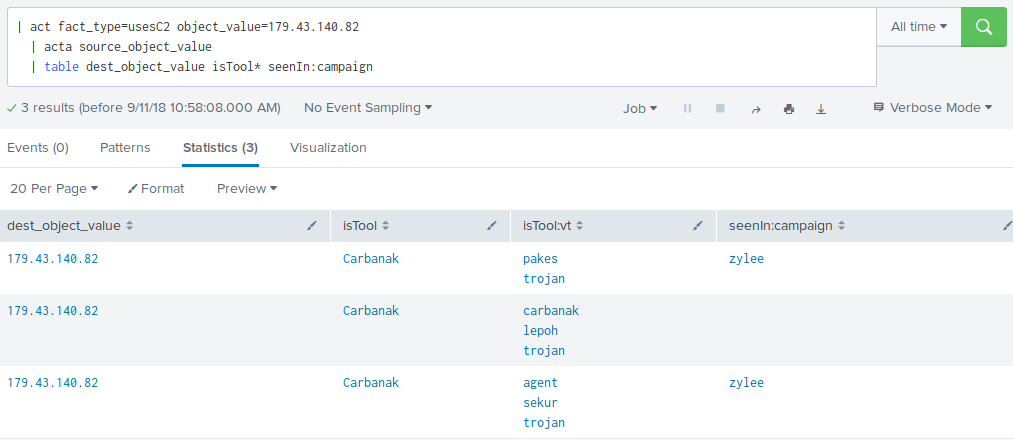
You can use the acta command to annotate existing events with data from an ACT query:
.... | acta field1 [... fieldN] [option=value] [option=value]
Fields specified will be used as object_value in the search and the search result can be limited by the same options specified in the ACT Search.
actsearch and acta can also be combined to annotate results from the search: