Intrution Detection Prevention System Suricata
A. Install and Config:
- Add repository stable version:
sudo add-apt-repository ppa:oisf/suricata-stable
- Update:
sudo apt-get update
- Install support engine:
sudo apt-get -y install libpcre3 libpcre3-dbg libpcre3-dev \build-essential autoconf automake libtool libpcap-dev libnet1-dev \libyaml-0-2 libyaml-dev zlib1g zlib1g-dev libcap-ng-dev libcap-ng0 \make libmagic-dev libjansson-dev libjansson4 pkg-config
- Install Suricata:
sudo apt-get install suricata
- Install IPS mode:
sudo apt-get -y install libnetfilter-queue-dev libnetfilter-queue1 libnfnetlink-dev libnfnetlink0
- Config Address Group:
address-groups:HOME_NET: "[192.168.100.0/24]" #HOME_NET: "[192.168.0.0/16,10.0.0.0/8,172.16.0.0/12]" #HOME_NET: "[192.168.0.0/16]" #HOME_NET: "[10.0.0.0/8]"
- Config Suricata Active rules:
default-rule-path: /etc/suricata/rules rule-files: -emerging-clabs_dos.rules -emerging-clabs_metasploit.rules -emerging-clabs_nmap.rules
B. Testing:
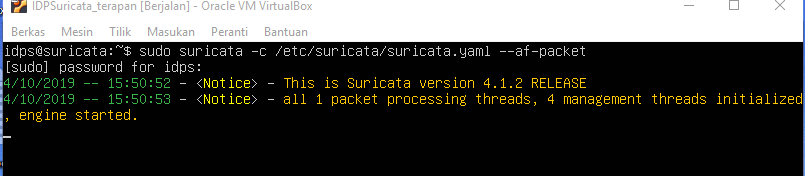
- Start Engine:
Realtime monitoring on 2nd terminal, follow the command: Putty(optional).
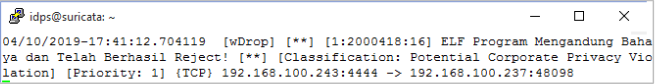
sudo tail -f /var/log/suricata/fast.log
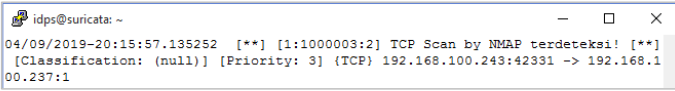
- Scanning TCP report:
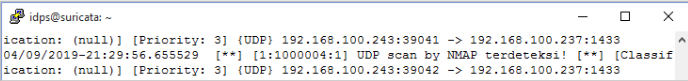
- Scanning UDP report:
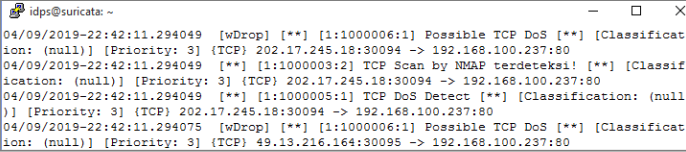
- DOS report:
- Exploit report: