This repository contains demo IaC (Infrastructure as Code) for Azure AD Privileged Identity Management. The terraform support for Azure resources PIM settings such as Approvers and Activation maximum duration (hours) is currently non-existing. There are ongoing issues tracking the implementation, e.g., Privileged Identity Management (PIM).
This repository contains a powershell script that uses the Az.Resources module to update the PIM settings for a role assignment.
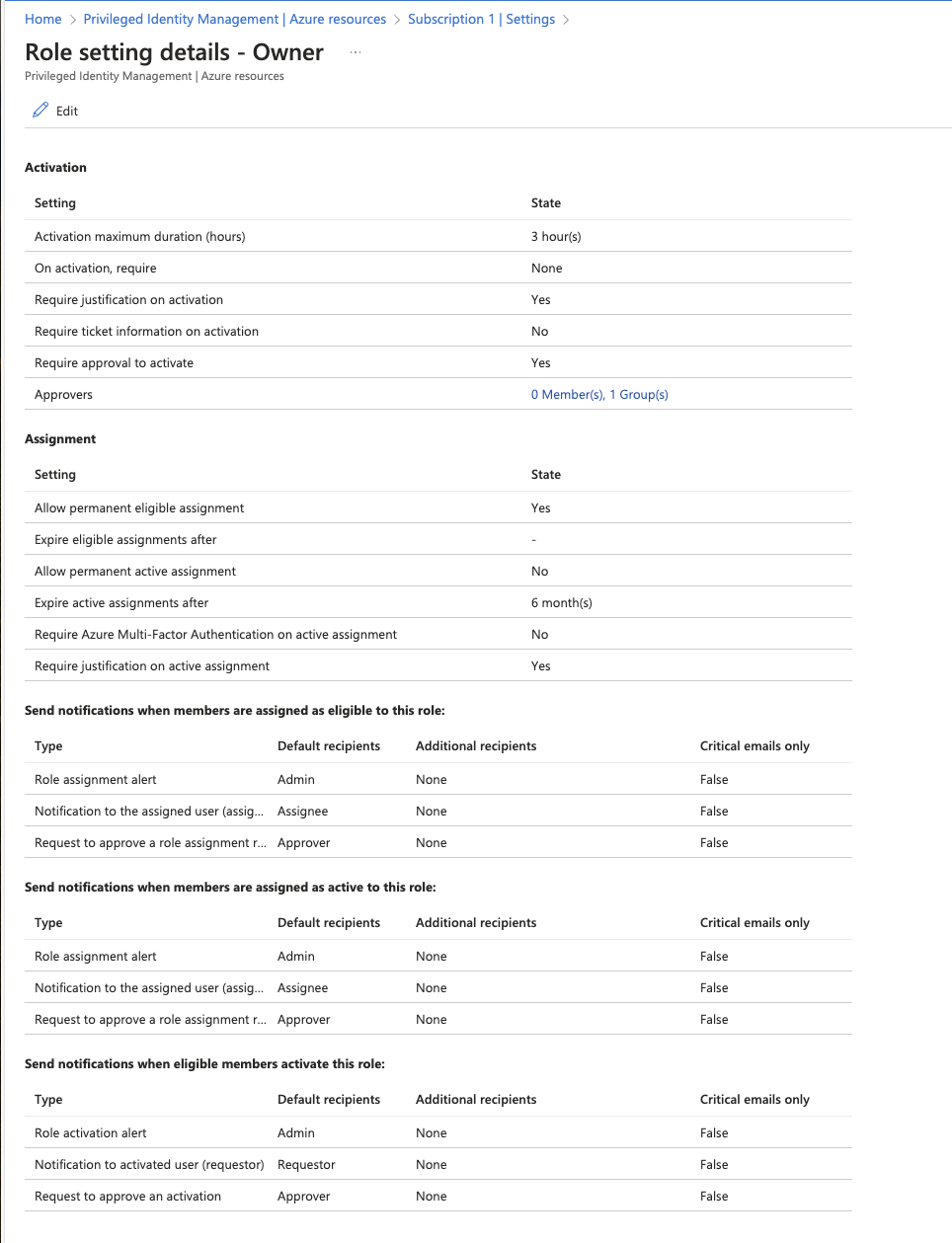
- Updates ExpirationRule to
Never - Updates Approvers to a spesific Azure AD group
- Updates Activation maximum duration (hours) to
3
- Microsoft Entra Identity Protection Plan 2 (P2)
PIM for Azure Resources is a service in Azure that enables you to manage, control, and monitor just-in-time Azure resources access within your organization.
- Install powershell.
- Go into powershell mode.
pwsh
- Install Az.Resources module
Install-Module -Name Az -AllowClobber -Scope CurrentUser
- Login using
Connect-AzAccount
- Run the script
update-pim-rules.ps1
- The terraform documentation states the
ExpirationRuleis optional. However, not setting it results in the error:
Unexpected status 400 with error: RoleAssignmentRequestPolicyValidationFailed: The following policy rules failed: ["ExpirationRule"]
- It is not possible to set the PIM role assignment expiration duration to
not expirewithout chainging theRoleManagementPolicyExpirationRulefirst. - Updating or creating new
IRoleManagementPolicyRulesrequires full namespace on, e.g.,Microsoft.Azure.PowerShell.Cmdlets.Resources.Authorization.Models.Api20201001Preview.RoleManagementPolicyApprovalRule. The same applies toruleType. - Adding
-Debugto theNew-AzRoleManagementPolicyRulecmdlet provides more information on the error, including the JSON payload. - All the types need full namespace