The Vault Controller automates the creation of Vault tokens for Kubernetes Pods. This repo includes a set of hands-on tutorials and example programs you can use to try out the Vault Controller.
This is a prototype. Do not use this in production.
- Each Pod requires a dedicated Vault token tied to the Pod's life-cycle
- Each Pod will use a dedicated Vault token to request secrets from a Vault server
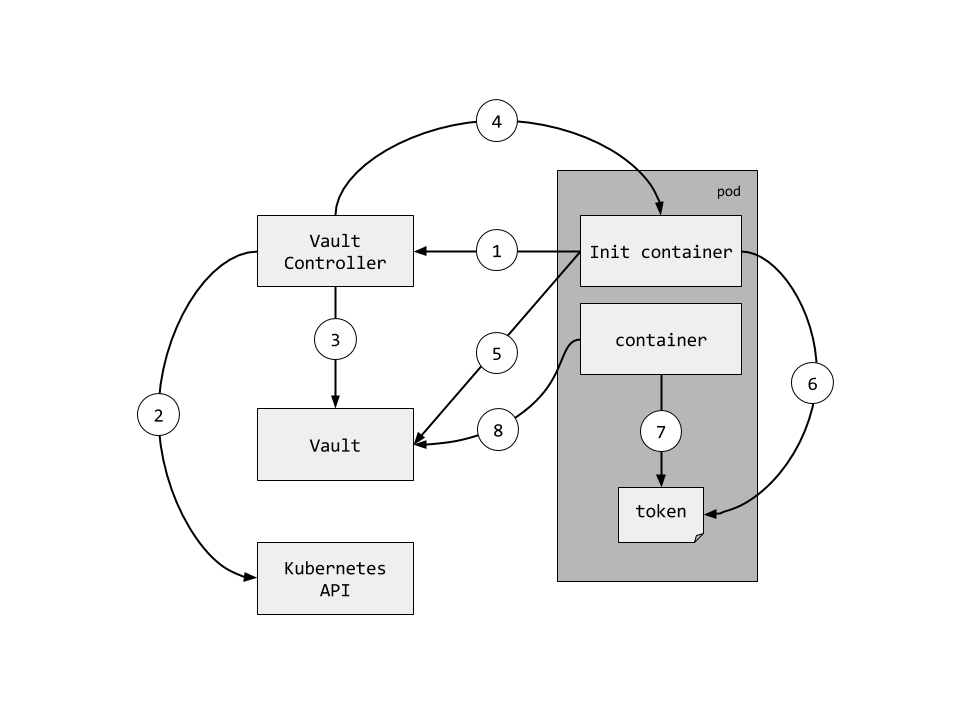
The following diagram demonstrates the flow Pods use to obtain a dedicated token when running in a Kubernetes cluster.
- An Init container requests a wrapped token from the Vault Controller
- The Vault Controller retrieves the Pod details from the Kubernetes API server
- If the Pod exists and contains the
vaultproject.io/policiesannotation a unique wrapped token is generated for the Pod. - The Vault Controller "callsback" the Pod using the Pod IP obtained from the Kubernetes API.
- The Init container unwraps the token to obtain a dedicated Vault token.
- The dedicated token is written to a well-known location and the Init container exits.
- Another container in the Pod reads the token from the token file.
- Another container in the Pod renews the token to keep it from expiring.
More details can be found in the How it Works document.
The following tutorials will guide you through the deployment of the vault-controller and an example application to see how it all works.
Clone this repository:
git clone https://github.com/kelseyhightower/vault-controller.git
cd vault-controller
Before you can complete the tutorials you'll need access to a Kubernetes clusters. Google Container Engine (GKE) or minikube should work.
Once you are done with the tutorials run the following command to clean up:
kubectl delete namespace vault-controller