The Serverless OAuth secured Node.js API code sample:
- The API takes finer control over OAuth claims-based authorization to enable security with good manageability.
- The API uses JSON request logging and log aggregation, for the best supportability.
The AWS deployed API runs as part of an OAuth end-to-end setup, to serve my blog's frontend code samples.
This enables productive frontend developemnt against remote cloud endpoints:
The API's clients are UIs, which get user-level access tokens by running an OpenID Connect code flow.
To enable test-driven development, the API instead mocks the authorization server:
- Ensure that Node.js 20 or later is installed
- Integration tests run Wiremock in Docker, so ensure that Docker is installed
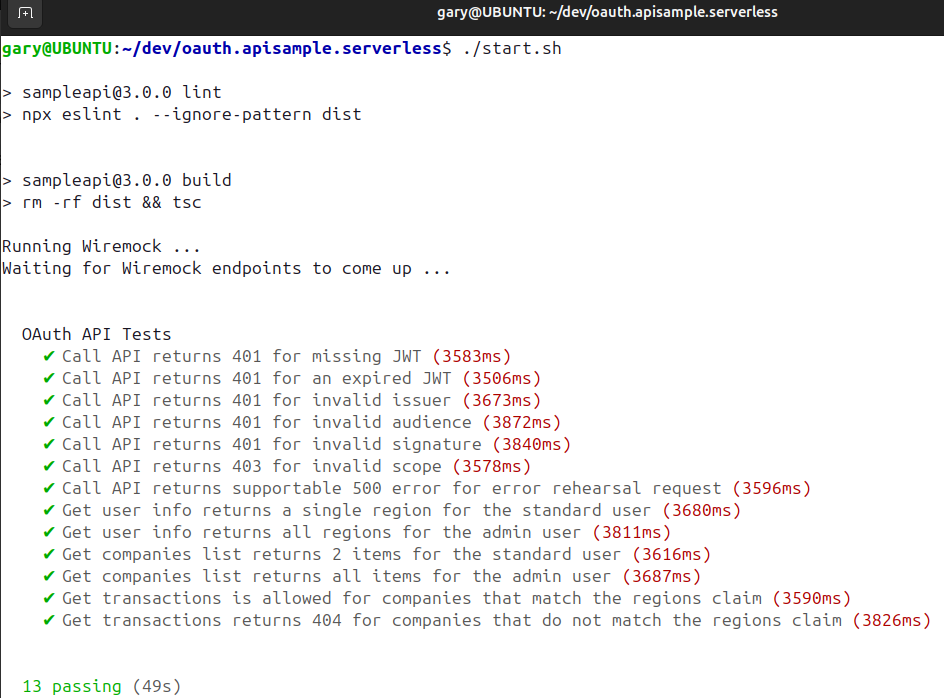
Run this command to build code and then run mocha tests that invoke all lambdas:
./start.shThis works well enough to meet my low cost deployment goals, though these technical limitations exist:
- The lambdas cannot be run as real HTTP endpoints locally, and be called concurrently by clients.
- The lambdas cannot be load tested locally, due to the slow lambda startup times.
- The lambdas cannot use in-memory caching of token signing public keys or extra claims.
- See the API Journey - Server Side for further information on the API's desired behaviour.
- See the Serverless API Overview for further details on the API development and deployment details.
- The API uses Node.js and TypeScript.
- The jose library manages in-memory JWT validation.
- AWS Route 53 provides custom hosting domains.
- AWS Certificate Manager issues and auto-renews the API's SSL certificate.
- AWS Cognito is the API's default Authorization Server.
- DynamoDB caches JWKS keys and extra claims.
- The AWS API Gateway is the internet API entry point.
- The API logs output to CloudWatch and could be shipped to a log aggregation system.