Several handy commands to facilitate common Android pentesting tasks.
It uses pure-python-adb to interface with the ADB server.
- Python 3
- ADB
- Rooted Android phone
- Clone the repository:
git clone https://github.com/Hamz-a/frida-android-helper - Install
python3 setup.py install
Commands are self explanatory. Ask for help fah --help.
- Start the frida-server
fah server start - Stop the frida-server
fah server stop - Reboot the frida-server
fah server reboot - Update the frida-server
fah server update: The latest Android frida-server is fetched from GitHub release page using the GitHub API. This is then installed on the Android device usingfah server updatecommand.
- Enable proxy:
fah proxy: will automatically select an IP address from your PC, default port 8080fah proxy enable: same as abovefah proxy enable 192.168.137.137: specify IP address, default port 8080fah proxy enable 192.168.137.137 8888: specify IP address and port
- Disable proxy
fah proxy disable - Get current proxy settings
fah proxy get
Route traffic by performing adb reverse and a few iptables rules:
- Connect your Android mobile device via USB
- Setup an intercepting proxy (ex: Burp)
- Configure intercepting proxy to use transparent proxy
- Connect to random wifi hotspot on Android device
- Enable rproxy:
fah rproxy: will use default port 8844fah rproxy enable: same as abovefah rproxy enable 8888: specify port
- Disable rproxy:
fah rproxy disable: will use default port 8844fah rproxy disable 8888: specify port
fah screen: take a screenshot with the following formatdeviceID_%Y.%m.%d_%H.%M.%S.pngfah screen filename: take a screenshot with the following format:deviceID_filename.png
fah snap: take a disk snapshot of the current open appfah snap com.example.app: take a disk snapshot ofcom.example.appapp
fah cert: generate a custom CA certificate to be imported in burp & devicefah cert generate: same as abovefah cert install: install specified certificate on devicefah cert setup: generate and install certificate (above commands combined)
fah app: try to download the currently opened appfah app dl: same as abovefah app dl <filter>: list apps by filter and download them
fah app list: list installed app on Android device.
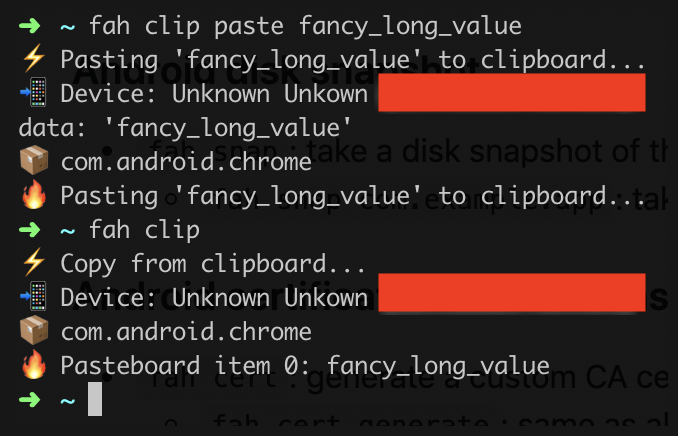
fah clip: display content of clipboardfah clip copy: same as abovefah clip paste foo bar: set the content of the clipboard tofoo bar
fah ps: list apps/processesfah ps foobar: same as above but filter onfoobar
Ideas and bug reports are welcome!