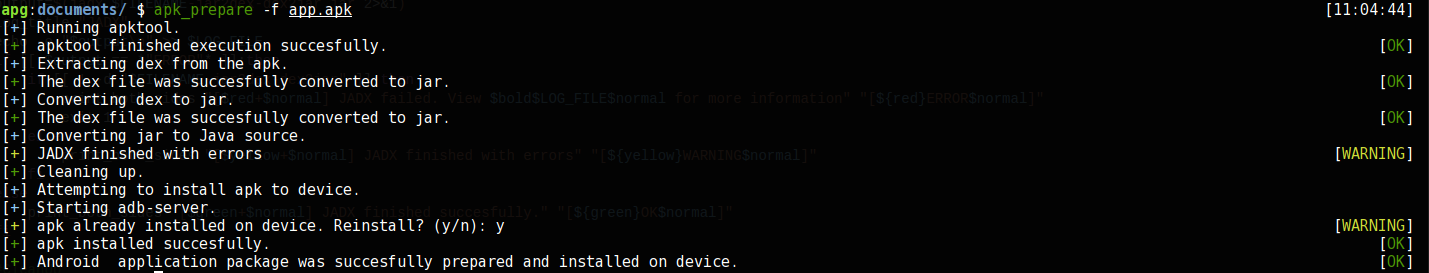
This is a collection of script I created in order to automate certain tideious and time consuming tasks performed during a Android Penetration Assessment. A description of each script follows.
A bash script that decompiles the apk, producing both the source in Java and the smali. The files are aranged neatly in a simple folder structure. The script also attempts to install the application on the device. The boring stuff are over! Happy hacking.
- apktool
- d2j-jar2dex.sh as d2j-jar2dex, simply create symbolic link
ln d2j-jar2dex.sh d2j-jar2dexinside PATH - d2j-dex2jar.sh same as above
- jadx
OPTIONAL
- adb Required to install application on connected device.
apk_prepera.sh apk_prepare -f <target.apk> [-o <output folder>]

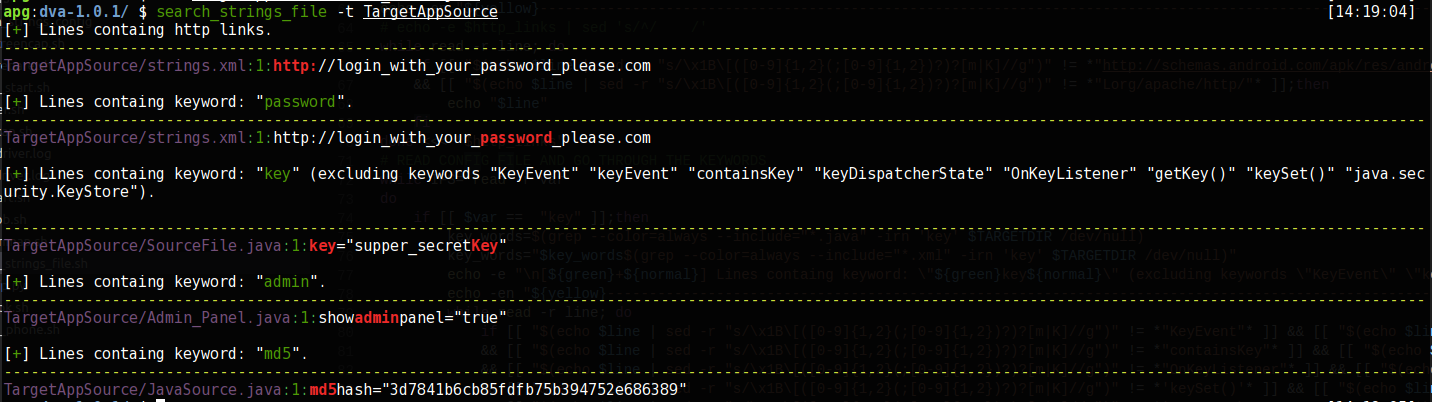
A bash script used for static analysis on the applications source. It searches for strings, as provided by the configuration file. The default configuration file is at the script's base directory, named ..search_strings_config.
The script will search by default for http:// links since it is something you should be looking for anyway see MiM. The script also attempts to get rid some of the riffraff when searching for the string key.
This is a simple script that takes a screenshot of the screen currently displayed on the phone. It stores the screen on the screenshot directory of the Project. To use, please modify it and add your root directories.
Small wrapper script used to sign an apk so it is possible to install it on an Android device, after patching it. It requires sign.jar to be in the /usr/local/bin directory.
Small wrapper for MWR's drozer. It initiates drozer on the terminal and it starts the drozer server on the phone,