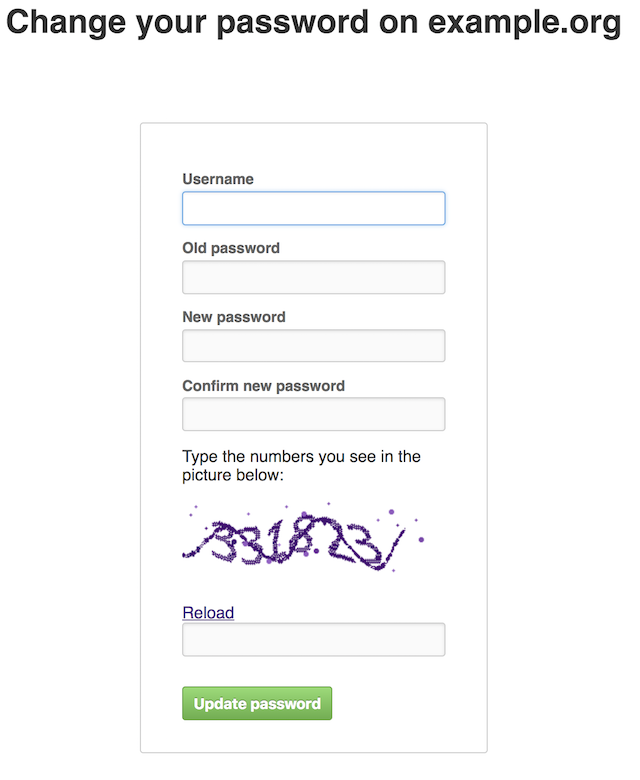
WebUI Client capable of connecting to backend LDAP server and changing the users password.
The configuration is made with environment variables:
| Env variable | Default value | Description |
|---|---|---|
| LPW_TITLE | Change your global password for example.org | Title that will appear on the page |
| LPW_HOST | LDAP Host to connect to | |
| LPW_PORT | 636 | LDAP Port (389 |
| LPW_ENCRYPTED | true | Use encrypted communication |
| LPW_START_TLS | false | Start TLS communication |
| LPW_SSL_SKIP_VERIFY | true | Skip TLS CA verification |
| LPW_USER_DN | uid=%s,ou=people,dc=example,dc=org | Filter expression to search the user for Binding |
| LPW_USER_BASE | ou=people,dc=example,dc=org | Base to use when doing the binding |
| CA_FILE | ca.crt | ca certification path for encrypting communication |
dep ensure
LPW_HOST=ldap_host_ip go run main.goBrowse http://localhost:8080/
docker run -d -p 8080:8080 --name ldap-passwd-webui \
-e LPW_TITLE="Change your global password for example.org" \
-e LPW_HOST="your_ldap_host" \
-e LPW_PORT="636" \
-e LPW_ENCRYPTED="true" \
-e LPW_START_TLS="false" \
-e LPW_SSL_SKIP_VERIFY="true" \
-e LPW_USER_DN="uid=%s,ou=people,dc=example,dc=org" \
-e LPW_USER_BASE="ou=people,dc=example,dc=org" \
-e CA_FILE='/app/ca.cert' \
-e LPW_PATTERN_INFO="Password must be at least 8 characters long." \
npenkov/docker-ldap-passwd-webui:latestgo mod downloadmake build modify below attribute for ldap user: "sambaNTPassword" and "sambaLMPassword"
code:
rootCA, err := x509.SystemCertPool()
if err != nil {
log.Printf("Failed to load system cert:%v", err)
// return nil, err
}
if rootCA == nil {
rootCA = x509.NewCertPool()
fileName := "./certs/ca.crt"
ldapCert, err := ioutil.ReadFile(fileName)
if err != nil {
log.Fatal(fmt.Sprintf("failed to read file: %s ", fileName))
}
ok := rootCA.AppendCertsFromPEM(ldapCert)
if !ok {
log.Fatal(fmt.Sprintf("ca file not added: %s", fileName))
}
}
config := &tls.Config{
InsecureSkipVerify: true,
ServerName: "YourServerName",
RootCAs: rootCA,
}
l, err := ldap.DialTLS("tcp", fmt.Sprintf("%s:%d", "YourServerName", 636), config)code:
import "regexp"
func ChenkPasswordStrength(p string) (level int) {
reg := regexp.MustCompile(`^(?:([a-z])|([A-Z])|([0-9])|(\W)){8,25}$`)
for _, str := range reg.FindStringSubmatch(p) {
if len(str) == 0 {
continue
}
level += 1
}
return level
}modify olc config, or try to change code: bind admin dn and obtain admin privileges