Deploying a n-Tier Web App in a Virtual Private Cloud using Terraform & Ansible
Purpose
The purpose of this project is to demonstrate, through the use of a reuseable asset, the concept of Infrastructure as code and how it can enable the ability to automate deployment facilitating a more consistent and faster development, testing, and deployment of workloads into a cloud, using the IBM Cloud VPC Infrastructure, HashiCorp's Terraform, and Red Hat's Ansible.
A n-tier architecture was chosen as a typical cloud workload for this example. A n-tier architecture separates the web / application and data tiers by placing them into separate sub-networks which are logically isolated using virtual network security constructs which can be defined and configured via an API. WordPress, a popular web, blog and e-commerce platform and MySQL, a typical open source database, installed on top of a LAMP stack were chosen as the core software stack because to their simplicity and broad acceptance. Nginx and Nginx Unit were chosen as the Web Server and Application Servers respectively.
The main objectives of this project is to educate enterprise DevOps users and system administrators on how to leverage both the features of IBM Cloud VPC Infrastructure as well as how to use the IBM Cloud Terraform Provider and Ansible to deploy and fully configure a working n-tier application.
This automated approach leveraged previous Solution Tutorials - Highly Available & Scalable Web App documentation.
High Level Architecture
- Infrastructure
- Public Cloud isolation using a VPC
- RFC1918 private bring-your-own-IP addresses
- Application and data layers deployed on isolated subnets accross different availability zones
- Network isolation defined logically using Security Groups and ACLs
- Global DDOS and Global Load Balancing
- VPN-as-a-Service to establish remote secure connectivity between on-pream and the VPC
- SysDig & LogDNA for infrastructure and application monitoring
- Application
- A horizontally scaleable web application deployed into a two different availability zones
- Multiple database servers across two availability zones
- A master/slave data replication strategy across availability zones
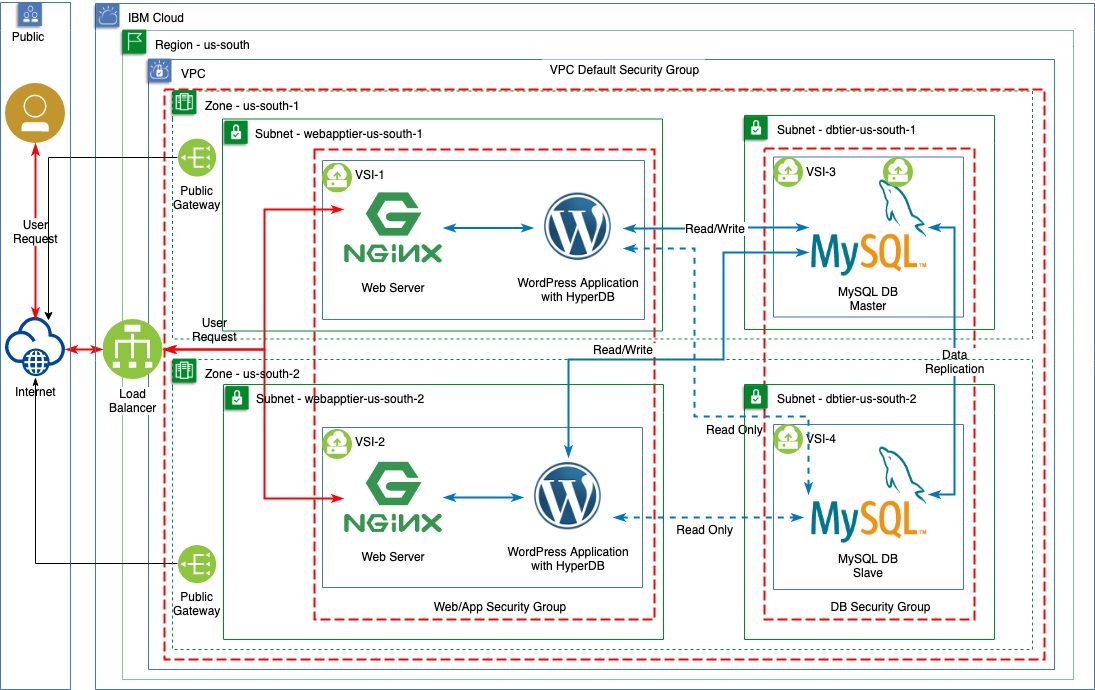
VPC Architecture
Below is the IBM Virtual Private Cloud (VPC) architecture of the solution showing public isolation for both Application (through a Load Balancer) and data.
Infrastructure Architecture
Application Architecture
Not depicted in drawings
- VPNaaS or any VPN Connections
- Cloud Internet Services (GLB function or DNS)
- Management Flows
Assumptions and Limitations
- This documentation is meant to be used for illustrative and learning purposes primarily.
- This document expects the reader to have a basic level of understanding of network infrastructure, Terraform, Ansible and application deployment on a Linux environment.
- The solution will implement HTTP only for simplicity.
- A MySQL database server was implemented on Infrastructure versus as-a-service to illustrate both the ability to define logical tiers between subnets as well as to show the ability to automate deployment and configuration tasks.
- Ansible is used for all post configuration tasks.
VPC Functional Coverage
| Function | Demonstrated | Notes |
|---|---|---|
| VPC | ✅ | |
| Terraform | ✅ | |
| Ansible | ✅ | |
| Resource Groups | ✅ | Assigned, but assumed to be created already. |
| Access Groups | ✅ | Inherited, but assumed to already be created |
| Subnets | ✅ | |
| Private (RFC1918) IP (BYOIP) | ✅ | |
| ACLs | ✅ | |
| Security Groups | ✅ | |
| Virtual Server Instance (VSI) | ✅ | |
| Cloud-init | ✅ | Package installation and configuration beyond base OS image. |
| Secondary Storage | Not used in this scenario | |
| Multiple Network Interfaces in VSI | ✅ | |
| Load Balancer as a Service | ✅ | Public Only |
| Floating IPv4 | Not required for workload. | |
| Public Gateway | ✅ | |
| VPNaaS | ✅ | |
| Cloud Internet Services (CIS) | ✅ | GLB configured for illustrative purposes with DDOS proxy |
| IBM Cloud Monitoring with Sysdig | ✅ | Public endpoint used |
| IBM Cloud Log Analysis with LogDNA | ✅ | Public endpoint Used |
System Requirements
Operating system
| Tier | Operating system |
|---|---|
| Web Server & Application | Ubuntu 16.04 |
| Data | Ubuntu 16.04 |
Hardware
| Tier | Type | Profile |
|---|---|---|
| Web Server and Application | VSI | cc1-2x4 |
| Data | VSI | bc1-4x16 |
Runtime Services
| Service Name | Demonstrated | Notes |
|---|---|---|
| Cloud Internet Services (CIS) GLB | ✅ | GLB configured for illustrative purposes with DDOS proxy. Alternatively a CNAME could have been used to publish the application URL. |
| IBM Cloud Monitoring with Sysdig | ✅ | Public endpoint used |
| IBM Cloud Log Analysis with LogDNA | ✅ | Public endpoint Used |
| IBM Cloud Databases | A VSI based instance of MySQL was chosen instead of a Database-as-a-Service capability to illustrate both the ability to create logial network constructs and security and the ability to use Terraform and Ansible to configure the environment. |
Documented Steps
Prerequisites
The following software needs to be installed:
- Terraform 0.11 or greater
- IBM Cloud Terraform Provider version 0.17.1
- Ansible 2.8
The following must be configured prior to running Terraform / Ansible
- A Public SSH key as described in SSH Keys.
- A resource group exists and is referenced in configuration as described in Managing resource groups
- User permissions and the required access as described in Managing user permissions for VPC resources
Deploy VPC Infrastructure using Terraform & Ansible
- Deploy Infrastructure using Terraform
- Establish site-to-site VPN
- Configure Application Layer using Ansible
Additional Documentation Provided
Useful links for Terraform and Ansible
The IBM Cloud Provider for Terraform Documentation
Useful links for IBM Cloud VPC documentation.
Getting started with IBM Cloud Virtual Private Cloud
Assigning role-based access to VPC resources