Powerful and user-friendly password hunting tool.
Use h8mail to find passwords through different breach and reconnaissance services, or local breaches such as Troy Hunt's "Collection1" and the infamous "Breach Compilation" torrent.
First Anniversary update, feedback and pull requests are welcomed ❤️ 🎂
📖 Table of Content
- Features
- Demo
- APIs
- Install
- Update
- Docker
- Usage
- Configuration file & keys
- Supported custom queries
- Troubleshooting
- Thanks & Credits
- Related open source projects
- Notes
🍊 Features
- 🔎 Email pattern matching (reg exp), useful for reading from other tool outputs
- 💫 Loosey patterns for local searchs ("john.smith", "evilcorp")
- 📦 Painless install. Available through
pip, only requiresrequests - ✅ CLI or Bulk file-reading for targeting
- 📝 Output to CSV file
- 💪 Compatible with the "Breach Compilation" torrent scripts
- 🏠 Search cleartext and compressed .gz files locally using multiprocessing
- 🌀 Compatible with "Collection#1"
- 🔥 Get related emails
- 🐲 Chase related emails by adding them to the ongoing search
- 👑 Supports premium lookup services for advanced users
- 🏭 Custom query premium APIs. Supports username, hash, ip, domain and password
- 📚 Regroup breach results for all targets and methods
- 👀 Includes option to hide passwords for demonstrations
- 🌈 Delicious colors
📦 pip3 install h8mail
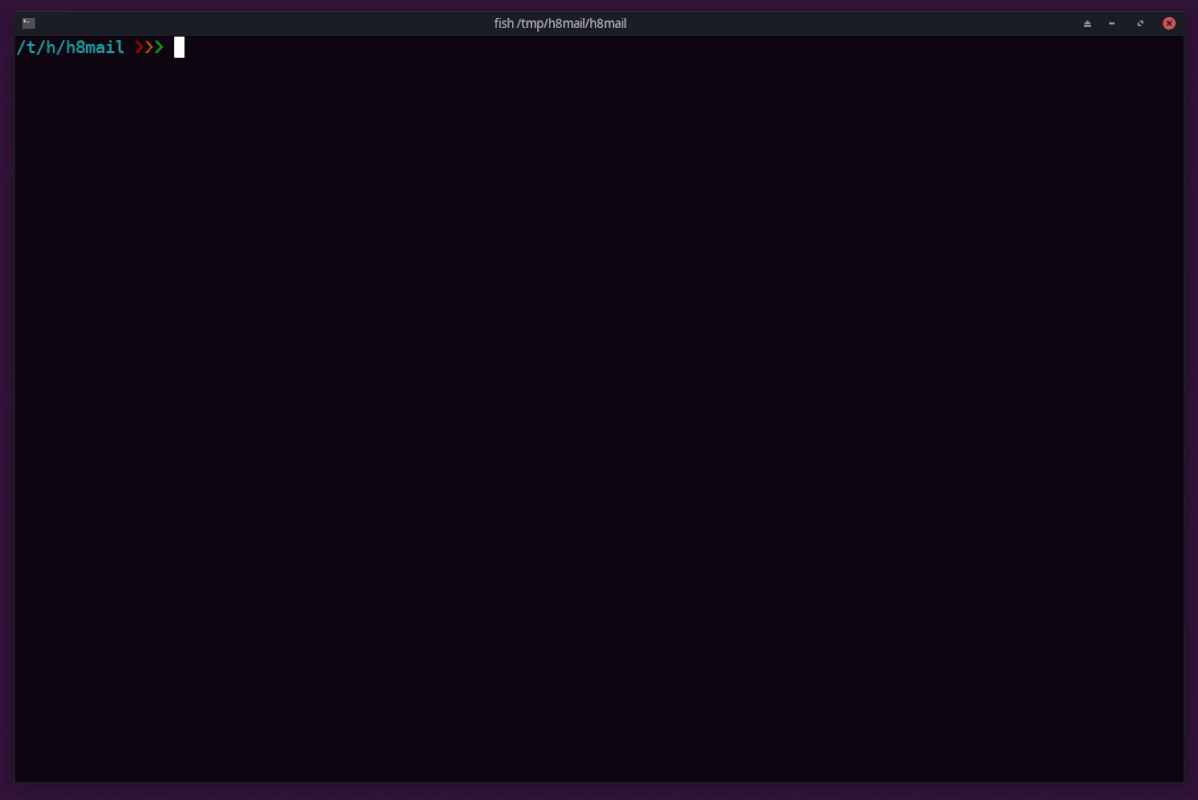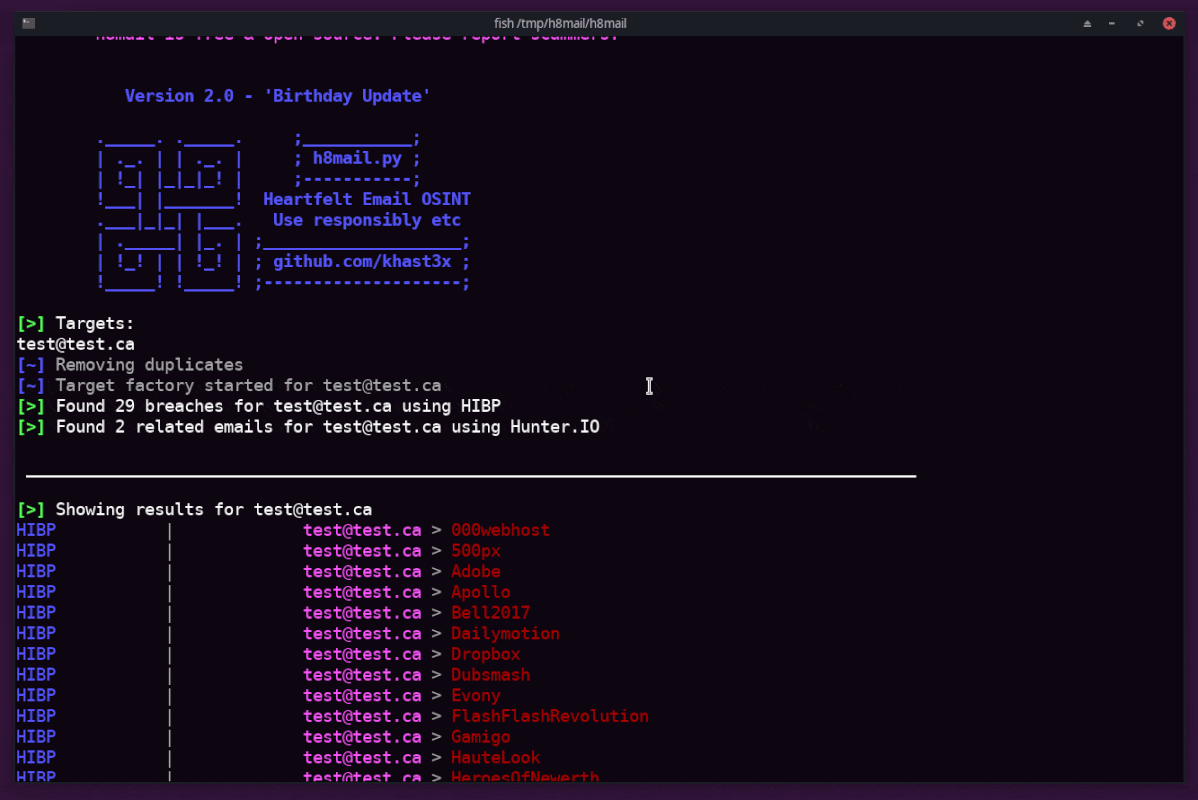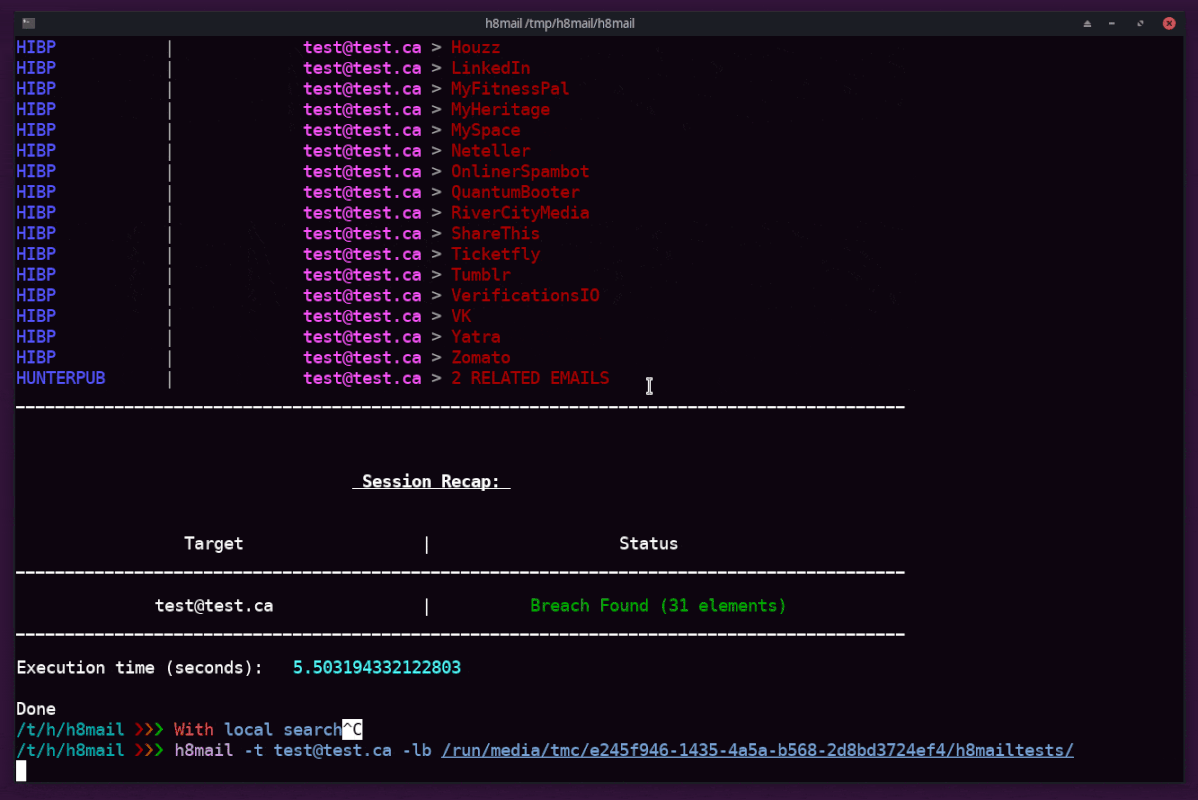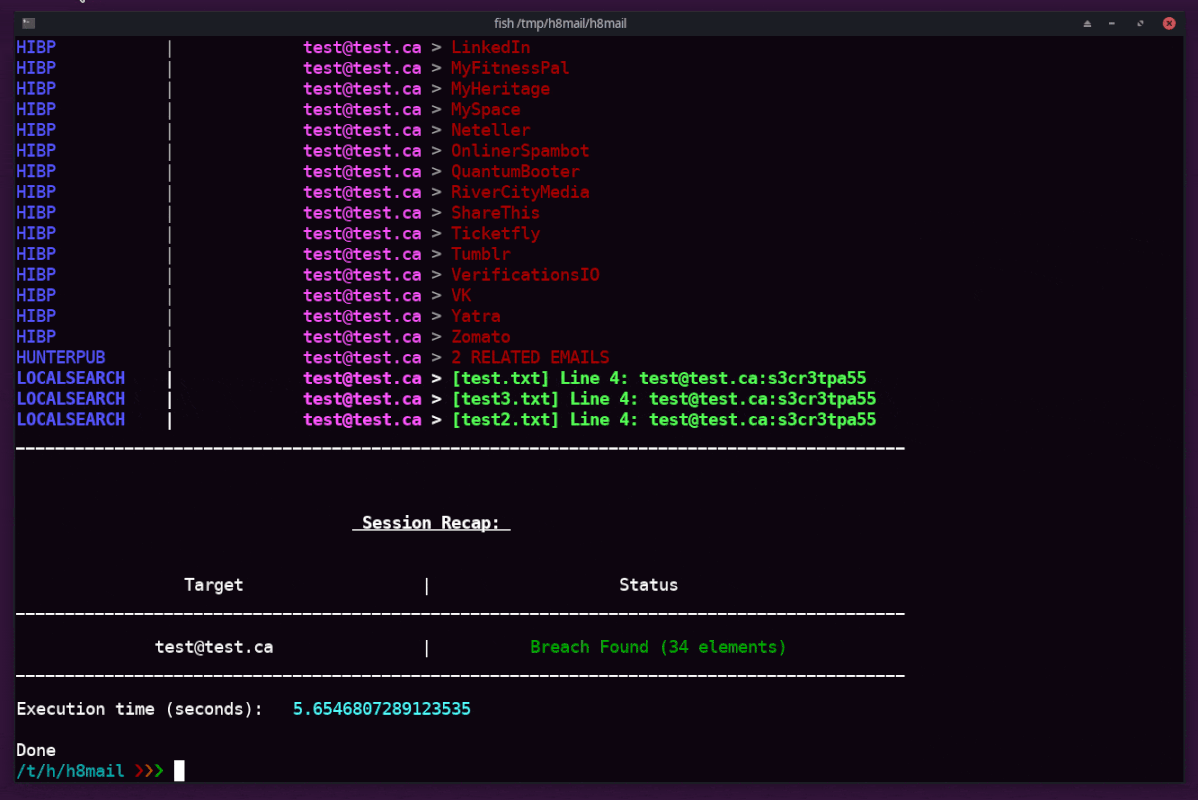
Demo
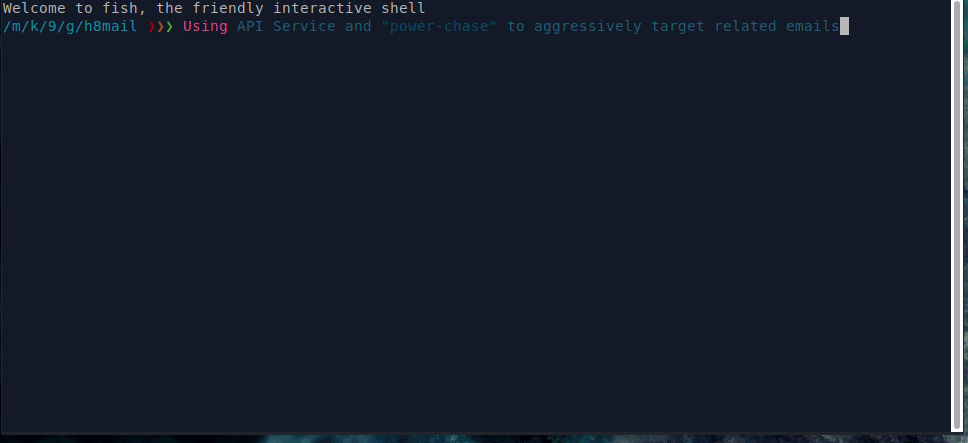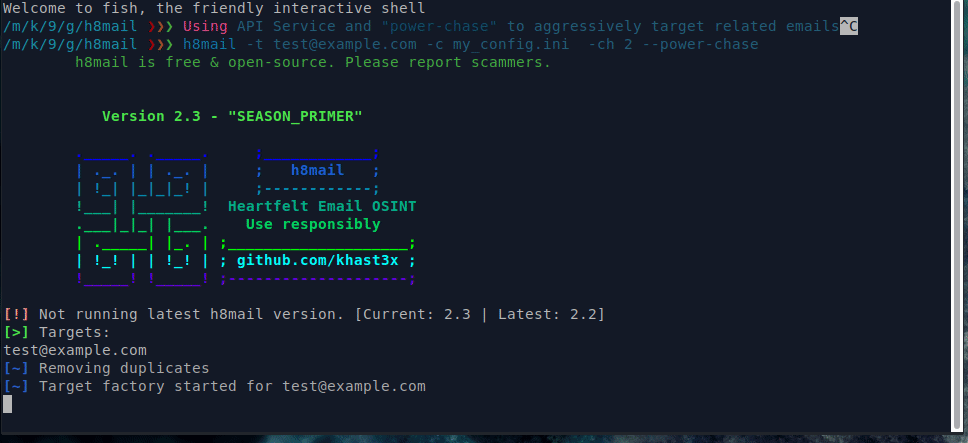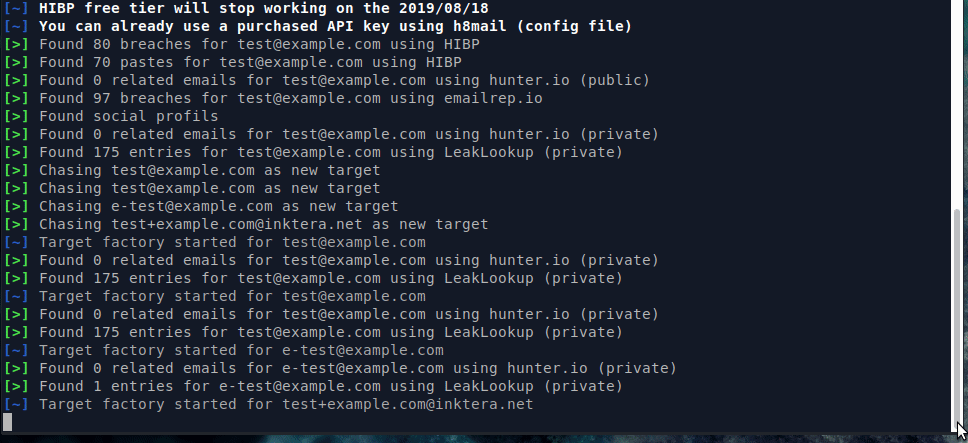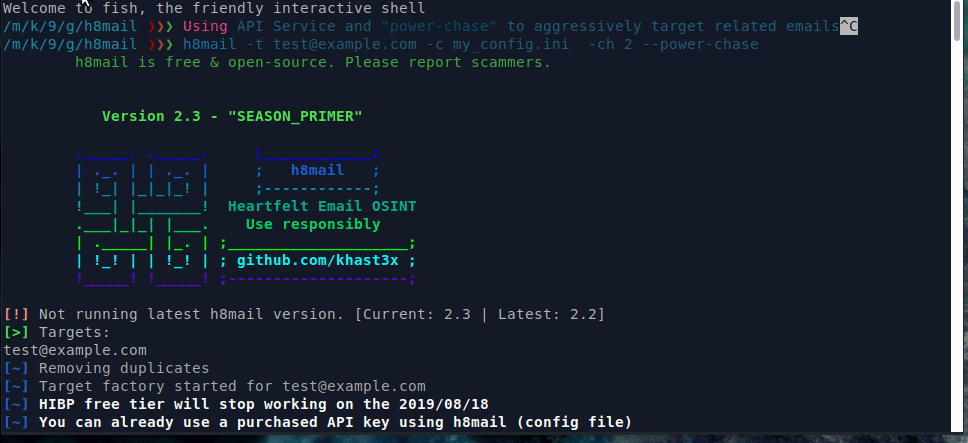
Out of the box
With API services & chasing enabled
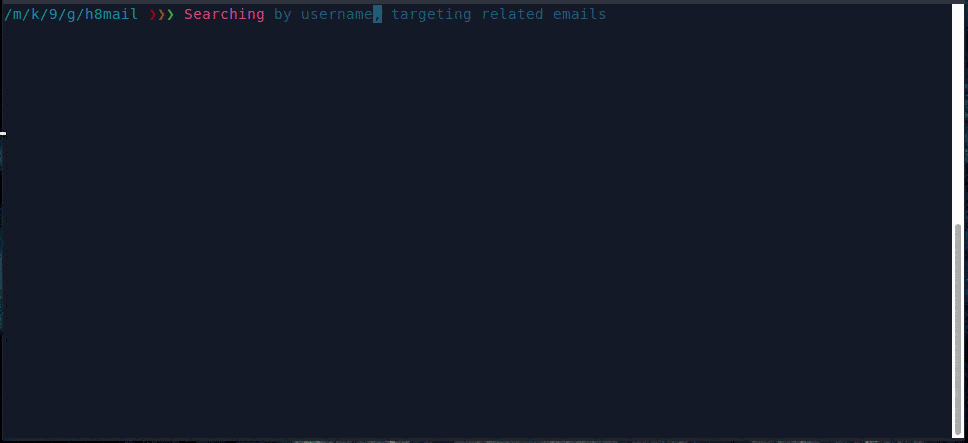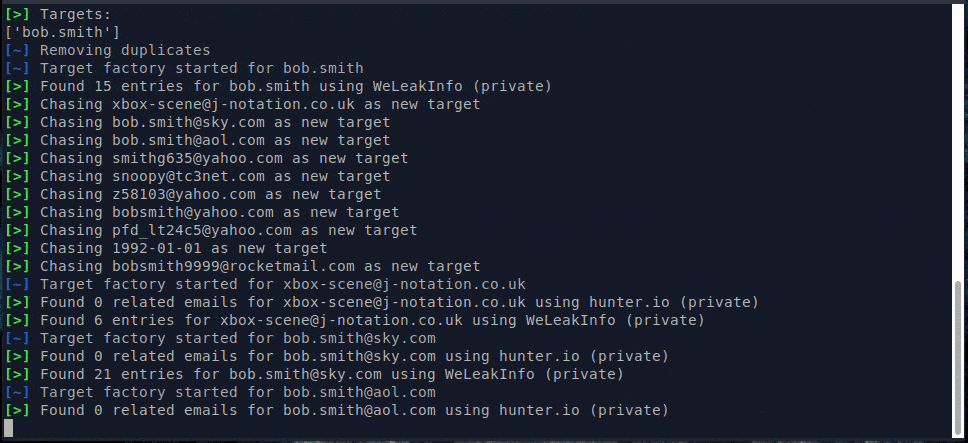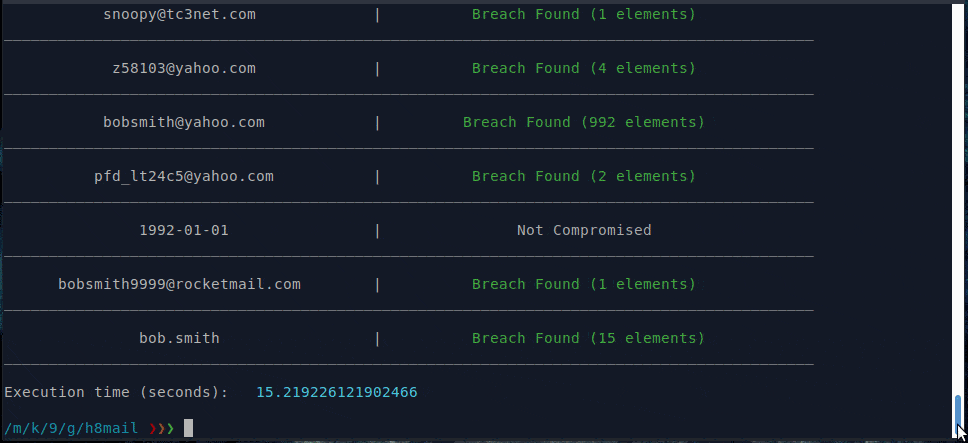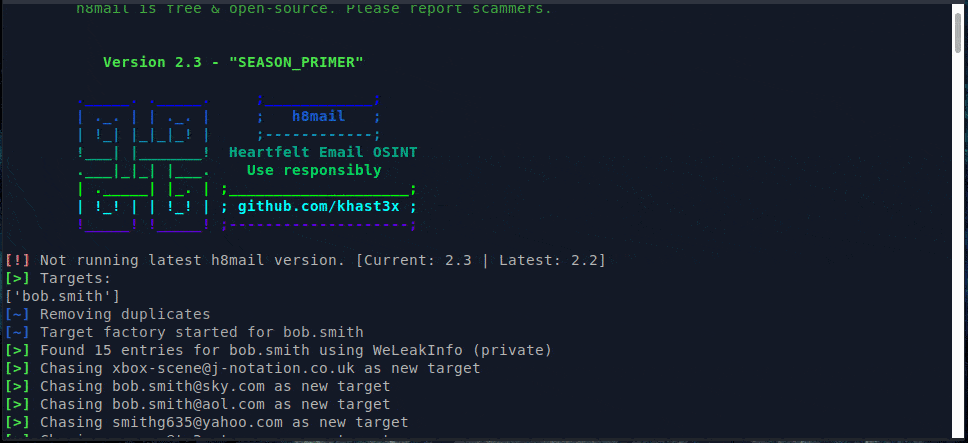
Searching using username with API service, power chasing enabled
APIs
| Service | Functions | Status |
|---|---|---|
| HaveIBeenPwned(v3) | Number of email breaches | ✅ 🔑 |
| HaveIBeenPwned Pastes(v3) | URLs of text files mentioning targets | ✅ 🔑 |
| Hunter.io - Public | Number of related emails | ✅ |
| Hunter.io - Service (free tier) | Cleartext related emails, Chasing | ✅ 🔑 |
| WeLeakInfo - Public | Number of search-able breach results | ✅ 🔑 |
| WeLeakInfo - Service | Cleartext passwords, hashs and salts, usernames, IPs, domain | ✅ 🔑 |
| Snusbase - Service | Cleartext passwords, hashs and salts, usernames, IPs - Fast ⚡ | ✅ 🔑 |
| Leak-Lookup - Public | Number of search-able breach results | ✅ (🔑) |
| Leak-Lookup - Service | Cleartext passwords, hashs and salts, usernames, IPs, domain | ✅ 🔑 |
| Emailrep.io - Service (free) | Last seen in breaches, social media profiles | ✅ |
| Scylla.sh - Service (free) | Cleartext passwords, hashs and salts, usernames, IPs, domain | ✅ |
🔑 - API key required
🍊 Install
Requirements
h8mail 2.0 only requires the python requests module to run.
Stable release (best)
To install h8mail, run this command in your terminal:
$ pip3 install h8mailAnd that's basically it.
This is the preferred method to install h8mail, as it will always install the most recent stable release.
Please note:
If you don't have pip installed, this Python installation guide can guide
you through the process.
For troubleshooting, check the Troubleshooting section.

--user
From sources
The sources for h8mail can be downloaded from the Github repo.
You can either clone the public repository:
$ git clone git://github.com/khast3x/h8mailOr download the tarball:
$ curl -OL https://github.com/khast3x/h8mail/tarball/masterNext, decompress the downloaded archive.
Once you have a copy of the source, you can install it with:
$ cd h8mail/
$ python setup.py install
$ h8mail -hOr just running it as a module:
$ cd h8mail/
$ python -m h8mail -hUpdate
$ pip3 install --upgrade h8mailUse --user at the end if getting a permission message from pip
Docker
$ docker run -ti kh4st3x00/h8mail -h🍊 Usage
usage: h8mail [-h] [-t USER_TARGETS [USER_TARGETS ...]] [-q USER_QUERY]
[--loose] [-c CONFIG_FILE [CONFIG_FILE ...]] [-o OUTPUT_FILE]
[-bc BC_PATH] [-sk] [-k CLI_APIKEYS [CLI_APIKEYS ...]]
[-lb LOCAL_BREACH_SRC [LOCAL_BREACH_SRC ...]]
[-gz LOCAL_GZIP_SRC [LOCAL_GZIP_SRC ...]] [-sf]
[-ch [CHASE_LIMIT]] [--power-chase] [--hide] [--debug]
[--gen-config]
Email information and password lookup tool
optional arguments:
-h, --help show this help message and exit
-t USER_TARGETS [USER_TARGETS ...], --targets USER_TARGETS [USER_TARGETS ...]
Either string inputs or files. Supports email pattern
matching from input or file, filepath globing and
multiple arguments
-q USER_QUERY, --custom-query USER_QUERY
Perform a custom query. Supports username, password,
ip, hash, domain. Performs an implicit "loose" search
when searching locally
--loose Allow loose search by disabling email pattern
recognition. Use spaces as pattern seperators
-c CONFIG_FILE [CONFIG_FILE ...], --config CONFIG_FILE [CONFIG_FILE ...]
Configuration file for API keys. Accepts keys from
Snusbase, WeLeakInfo, Leak-Lookup, HaveIBeenPwned and
hunterio
-o OUTPUT_FILE, --output OUTPUT_FILE
File to write CSV output
-bc BC_PATH, --breachcomp BC_PATH
Path to the breachcompilation torrent folder. Uses the
query.sh script included in the torrent
-sk, --skip-defaults Skips HaveIBeenPwned and HunterIO check. Ideal for
local scans
-k CLI_APIKEYS [CLI_APIKEYS ...], --apikey CLI_APIKEYS [CLI_APIKEYS ...]
Pass config options. Supported format: "K=V,K=V"
-lb LOCAL_BREACH_SRC [LOCAL_BREACH_SRC ...], --local-breach LOCAL_BREACH_SRC [LOCAL_BREACH_SRC ...]
Local cleartext breaches to scan for targets. Uses
multiprocesses, one separate process per file, on
separate worker pool by arguments. Supports file or
folder as input, and filepath globing
-gz LOCAL_GZIP_SRC [LOCAL_GZIP_SRC ...], --gzip LOCAL_GZIP_SRC [LOCAL_GZIP_SRC ...]
Local tar.gz (gzip) compressed breaches to scans for
targets. Uses multiprocesses, one separate process per
file. Supports file or folder as input, and filepath
globing. Looks for 'gz' in filename
-sf, --single-file If breach contains big cleartext or tar.gz files, set
this flag to view the progress bar. Disables
concurrent file searching for stability
-ch [CHASE_LIMIT], --chase [CHASE_LIMIT]
Add related emails from hunter.io to ongoing target
list. Define number of emails per target to chase.
Requires hunter.io private API key
--power-chase Add related emails from ALL API services to ongoing
target list. Use with --chase. Requires a private API
key
--hide Only shows the first 4 characters of found passwords
to output. Ideal for demonstrations
--debug Print request debug information
--gen-config, -g Generates a configuration file template in the current
working directory & exits. Will overwrite existing
h8mail_config.ini file
🍊 Usage examples
Query for a single target
$ h8mail -t target@example.comQuery for list of targets, indicate config file for API keys, output to pwned_targets.csv
$ h8mail -t targets.txt -c config.ini -o pwned_targets.csvQuery a list of targets against local copy of the Breach Compilation, pass API keys for Snusbase from the command line
$ h8mail -t targets.txt -bc ../Downloads/BreachCompilation/ -k "snusbase_url=$snusbase_url,snusbase_token=$snusbase_token"Query without making API calls against local copy of the Breach Compilation
$ h8mail -t targets.txt -bc ../Downloads/BreachCompilation/ -skSearch every .gz file for targets found in targets.txt locally
$ h8mail -t targets.txt -gz /tmp/Collection1/ -skCheck a cleartext dump for target. Add the next 10 related emails to targets to check. Read keys from CLI
$ h8mail -t admin@evilcorp.com -lb /tmp/4k_Combo.txt -ch 10 -k "hunterio=ABCDE123"Query username. Read keys from CLI
$ h8mail -t JSmith89 -q username -k "weleakinfo_priv=ABCDE123"Query IP. Chase all related targets. Read keys from CLI
$ h8mail -t 42.202.0.42 -q ip -c h8mail_config_priv.ini -ch 2 --power-chase🍊 Configuration file & keys
h8mail can generate a template configuration file in the current working directory using -g.
h8mail can read keys by using a config.ini file with -c, or by passing keys from the command line directly with -k.
(links contain refs)
You can purchase API keys for:
The configuration file format is as follows:
[h8mail]
hunterio =
hibp =
snusbase_url =
snusbase_token =
; leak-lookup_pub = 1bf94ff907f68d511de9a610a6ff9263
leak-lookup_priv =
weleakinfo_pub =
weleakinfo_priv =In the above example, you'll notice a Leak-lookup public key, graciously generated for h8mail users. To activate, uncomment the line and make sure to pass to config file. The API can sometimes timeout. If that's the case, simply relaunch.
Keys and their respective values can also be passed from the command line, with the -k option. Format is like so:
$ h8mail -t john.smith@evilcorp.com -k "K=V, K=V" "K=V"
$ h8mail -t john.smith@evilcorp.com -k "leak-lookup_pub=1bf94ff907f68d511de9a610a6ff9263"
🍊 Supported custom queries
| username | domain | hash | password | ip | |
|---|---|---|---|---|---|
| WeLeakInfo | ✅ | ✅ | ✅ | ✅ | ✅ |
| LeakLookup | ✅ | ✅ | ✅ | ✅ | |
| Snusbase | ✅ | ✅ | ✅ | ✅ | |
| Scylla.sh | ✅ | ✅ | ✅ | ✅ | ✅ |
As of writing, some service providers are undergoing upgrades and might support additional queries.
To use a custom query, use -q followed by the appropriate keyword
🍊 Troubleshooting
Python version & Kali
- The above instructions assume you are running python3 as default. If unsure, type the following in your terminal.
It should be eitherPython 3.*orPython 2.*:
$ python --version-
If you are running python2 as default :
Make sure you have python3.6+ installed, then replacepythoncommands with explicitpython3commands. -
If you have not set your venvs, you might get a permission error saying
Consider using the --user option or check the permissions.
Simply add --user like so:
$ pip install --user h8mailWindows
h8mailuses ANSI color escape characters. Windows doesn't know how to show the colors, and will show gibberish instead.
Fortunately, you can use Cmder, which is an excellent Windows CMD prompt alternative- If you're having trouble with python and pip, chances are you need to add python to your PATH.
pipwill also need to be in yourPATHenvironment variable. - If you're still having trouble with
pip, you can do the following:
# Check python version, should be 3.6+
C:> python --version
# To have python handle installation of pip
C:> python -m ensurepip
# To launch pip as a module
C:> python -m pip install h8mail
# To launch h8mail as a module
C:> python -m h8mail --helpTo find where pip installed h8mail, use pip3 show h8mail
OSX
- As described for Windows, you might encounter issues with python if your installation is incomplete, or
pip's installation directory is not in your PATH. - If thats the case, you can try invoking
pipandh8mailwith the same command lines as Windows. - Make sure the
pythoncommand refers to Python 3 withpython --version, otherwise replacepythonwithpython3in the instructions. - Basically try this if installed and not executing, check Windows instructions for further examples:
$ python3 -m h8mail -h🍊 Thanks & Credits
- Snusbase for being developer friendly
- kodykinzie for making a nice introduction and walkthrough article and video on installing and using h8mail
- Leak-Lookup for being developer friendly
- WeLeakInfo for being developer friendly
- h8mail's Pypi integration is strongly based on the work of audreyr's CookieCutter PyPackage
- Logo generated using Hatchful by Shopify
- Jake Creps for his h8mail v2 introduction
- Alejandro Caceres for making scylla.sh available. Be sure to support him if you can
🍊 Related open source projects
- WhatBreach by Ekultek
- HashBuster by s0md3v
- BaseQuery by g666gle
- LeakLooker by woj-ciech
- buster by sham00n
- Scavenger by ndinfosecguy
- pwndb by davidtavarez
🍊 Notes
- Service providers that wish being integrated can send me an email at
k at khast3x dot club(PGP friendly) - h8mail is maintained on my free time. Feedback and war stories are welcomed.
- Licence is BSD 3 clause
- My code is signed with my Keybase PGP key. You can get it using:
# curl + gpg pro tip: import ktx's keys
curl https://keybase.io/ktx/pgp_keys.asc | gpg --import
# the Keybase app can push to gpg keychain, too
keybase pgp pull ktxIf you wish to stay updated on this project: