Chainloop is under active development and you should expect breaking changes before the first stable release. If you are interested in contributing, please take a look at our contributor guide.
Chainloop is an open source software supply chain control plane, a single source of truth for artifacts plus a declarative attestation process.
With Chainloop, SecOps teams can declaratively state the attestation and artifacts expectations for their organization’s CI/CD workflows, while also resting assured that the latest standards and best practices are put in place.
Developer teams, on the other hand, do not need to become security experts, the attestation crafting tool will guide them with guardrails and a familiar developer experience.
To learn more about the project motivation please look at this blog post and see it in action in this video.
See the getting started guide for detailed information on downloading and configuring the Chainloop Command Line Interface (CLI)
Alternatively, you can download the CLI from the releases pages or build it from source.
To install the latest version for macOS, Linux or Windows (using WSL) just choose one of the following installation methods.
curl -sfL https://raw.githubusercontent.com/chainloop-dev/docs/4a45f6ffa12bf3cc1d81fd9aa47e3cb17a499b0d/static/install.sh | bash -syou can retrieve a specific version with
curl -sfL https://raw.githubusercontent.com/chainloop-dev/docs/4a45f6ffa12bf3cc1d81fd9aa47e3cb17a499b0d/static/install.sh | bash -s -- --version v0.8.95and customize the install path (default to /usr/local/bin)
curl -sfL https://raw.githubusercontent.com/chainloop-dev/docs/4a45f6ffa12bf3cc1d81fd9aa47e3cb17a499b0d/static/install.sh | bash -s -- --path /my-pathif cosign is present in your system, in addition to the checksum check, a signature verification will be performed. This behavior can be enforced via the --force-verification flag.
curl -sfL https://raw.githubusercontent.com/chainloop-dev/docs/4a45f6ffa12bf3cc1d81fd9aa47e3cb17a499b0d/static/install.sh | bash -s -- --force-verificationBy default, Chainloop CLI points to a running instance of Chainloop.
If you are running your own instance of the Control Plane. You can make the CLI point to your instance by using the chainloop config save command.
chainloop config save \
--control-plane my-controlplane.acme.com \
--artifact-cas cas.acme.comAuthenticate to the Control Plane by running
$ chainloop auth loginOnce you've been logged in, follow these instructions to learn how to set up your account.
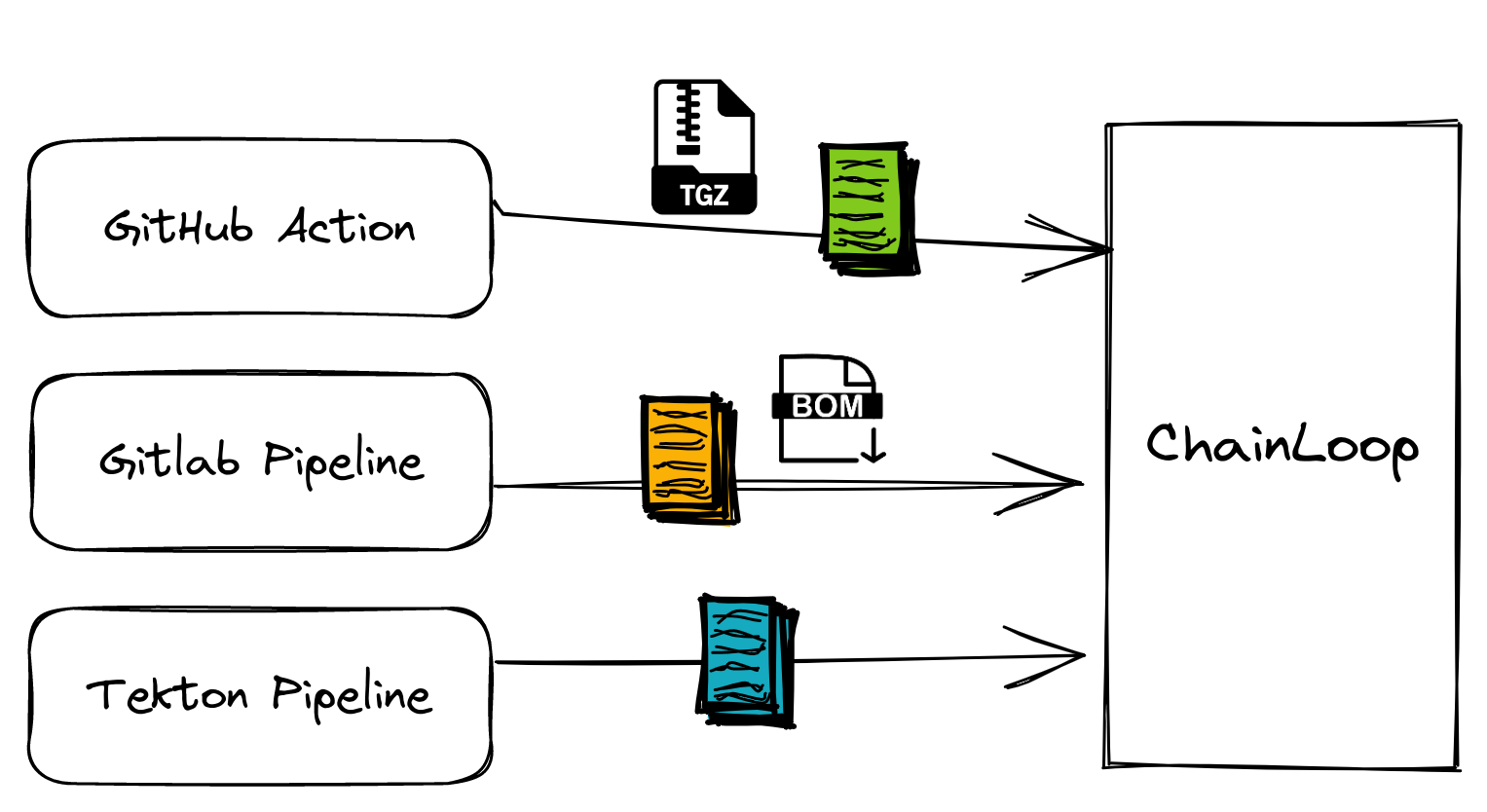
Craft and store attestation metadata and artifacts via a single integration point regardless of your CI/CD provider choice.
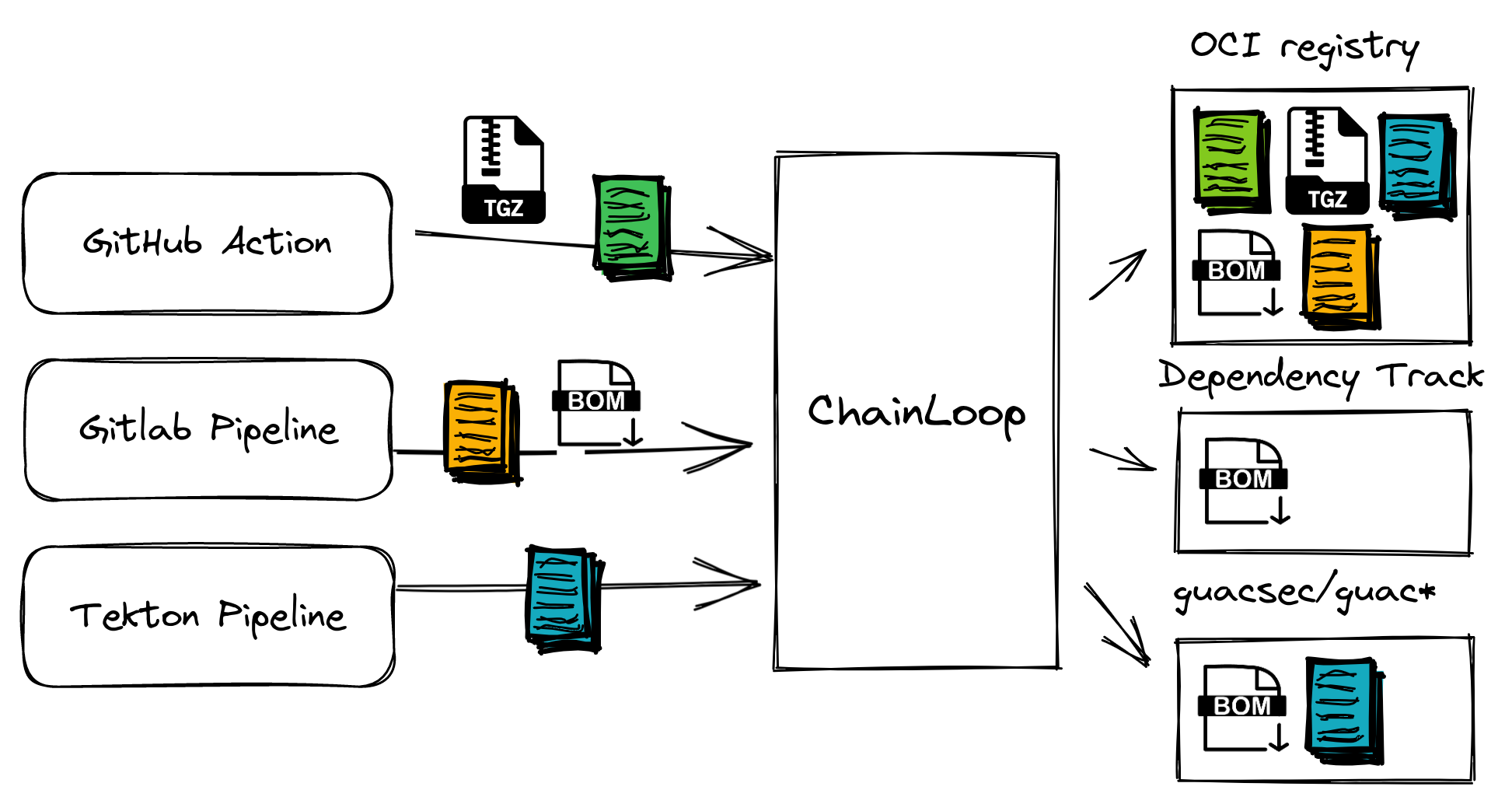
The result is having a SLSA level 3 compliant single Source of truth for artifacts and attestation built on OSS standards such as Sigstore, in-toto, SLSA and OCI.
Chainloop also makes sure the crafting of artifacts and attestation follows best practices and meets the requirements declared in their associated Workflow Contract.
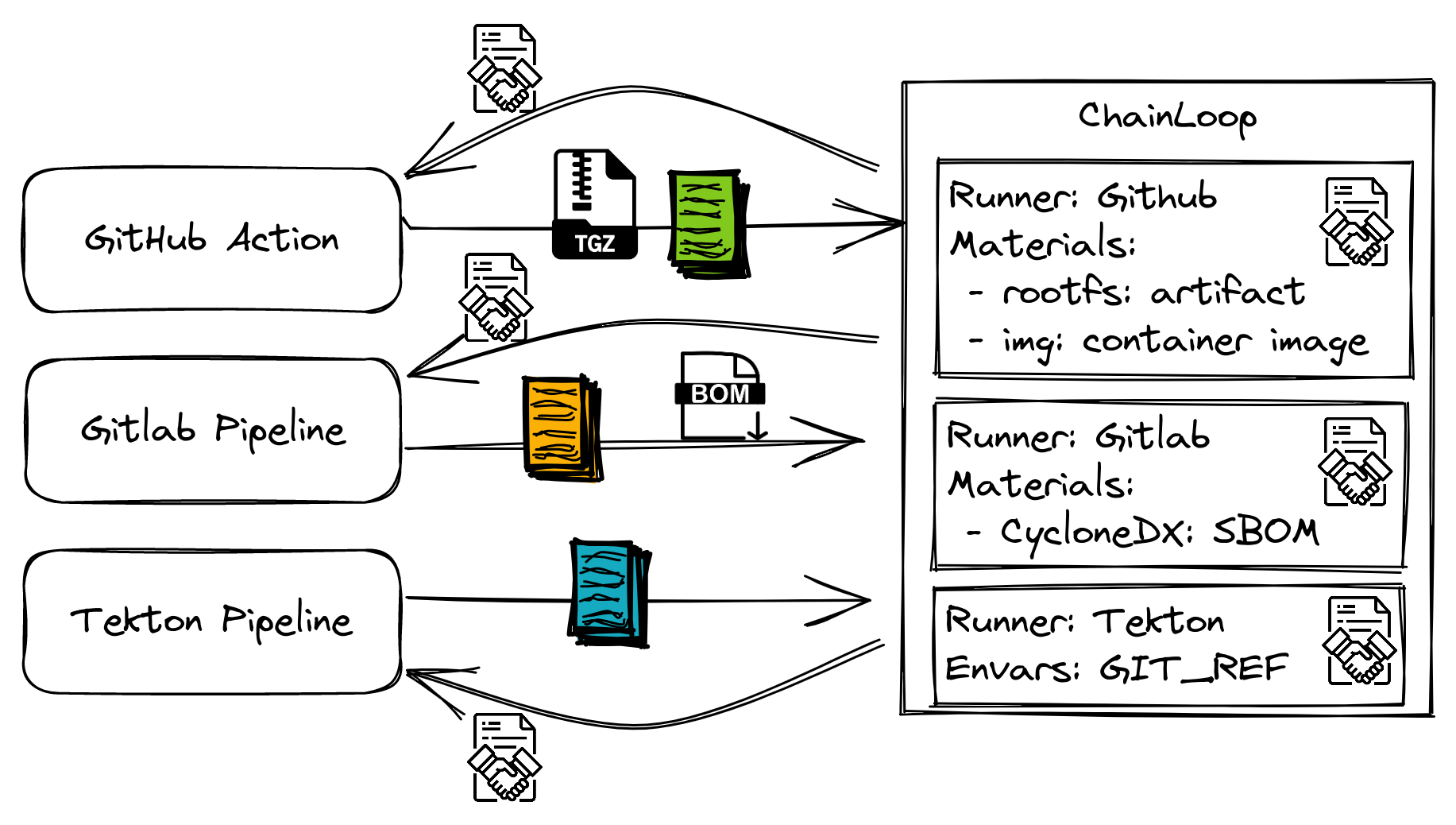
One key aspect is that in Chainloop, CI/CD integrations are declared via Workflow Contracts.
A Workflow Contract gives operators full control over what kind of data (build info, materials) must be received as part of the attestation and the environment where these workflows must be executed at. This enables an easy, and maintainable, way of propagating and enforcing requirements downstream to your organization.
You can think of it as an API for your organization's Software Supply Chain that both parties, development and SecOps teams can use to interact effectively.
Operators can set up third-party integrations such as Dependency-Track for SBOM analysis or an OCI registry for storage of the received artifacts and attestation metadata.
Ops can mix and match with different integrations while not requiring developers to make any changes on their side!
Chainloop makes sure to clearly define the responsibilities, experience and functional scope of the two main personas, Security/Operation (SecOps) and Development/Application teams.
SecOps are the ones in charge of defining the Workflow Contracts, setting up third-party integrations, or having access to the control plane where all the Software Supply Chain Security bells and whistles are exposed.
Development teams on the other hand, just need to integrate Chainloop's jargon-free crafting tool and follow the steps via a familiar DevExp to make sure they comply with the Workflow Contract defined by the SecOps team. No need to learn in-toto, signing, SLSA, OCI, APIs, nada :)
To learn more, please visit the Chainloop project's documentation website, https://docs.chainloop.dev where you will find a getting started guide, FAQ, examples, and more.
Chainloop is developed in the open and is constantly improved by our users, contributors and maintainers. Got a question, comment, or idea? Please don't hesitate to reach out via:
- GitHub Issues
- Discord Community Server
- Youtube Channel
Want to get involved? Contributions are welcome.
If you are ready to jump in and test, add code, or help with documentation, please follow the instructions on our Contribution page. At all times, follow our Code of Conduct.
See the issue tracker if you're unsure where to start, especially the Good first issue label.
Take a look at the list of releases to stay tuned for the latest features and changes.
Chainloop is released under the Apache License, Version 2.0. Please see the LICENSE file for more information.