🚑 AWS Security Survival Kit
🧠 Rationale
This AWS Security Survival Kit sets up a basic proactive monitoring and alerting environment on common suspicious activities in your AWS Account.
We know that CloudTrail is the bare minimum service to activate on a newly created AWS Account to track all activities on your AWS account. It helps, but this will not alert you to suspicious activities by itself. You still have to check periodically if something has gone wrong in multiple services and the console.
With these CloudFormation templates, you will bring proactive security monitoring and alerting to your AWS account. It's complementary to the GuardDuty service as there are no built-in alerts on GuardDuty.
💾 Suspicious Activities
Using this kit, you will deploy EventBridge (CloudWatch Event) Rules and CloudWatch Metric Filters and Alarms on select suspicious activities.
The following suspicious activities are currently supported:
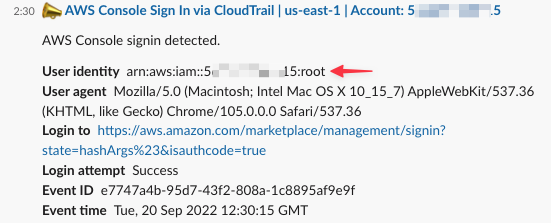
- Root User activities
- CloudTrail changes (
StopLogging,DeleteTrail,UpdateTrail) - AWS Personal Health Dashboard Events
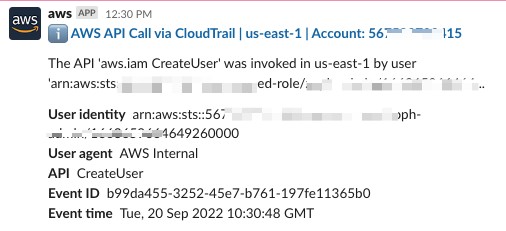
- IAM Users Changes (
Create,Delete,Update,CreateAccessKey, etc..) - MFA Monitoring (
CreateVirtualMFADeviceDeactivateMFADeviceDeleteVirtualMFADevice, etc..) - Unauthorized Operations (
Access Denied,UnauthorizedOperation) - Failed AWS Console login authentication (
ConsoleLoginFailures) - EBS Snapshots Exfiltration (
ModifySnapshotAttribute,SharedSnapshotCopyInitiatedSharedSnapshotVolumeCreated) - AMI Exfiltration (
ModifyImageAttribute) - Who Am I Calls (
GetCallerIdentity) - IMDSv1 RunInstances (
RunInstances&&optionalhttp tokens)
⌨️ Usage
Parameters
AlarmRecipient: Recipient for the alerts (e.g.: hello@zoph.io)Project: Name of the Project (e.g.: aws-security-survival-kit)Description: Description of the Project (e.g.: Bare minimum ...)LocalAWSRegion: Region where your workloads and CloudTrail are located (e.g.:eu-west-1)CTLogGroupName: Cloudtrail CloudWatch LogGroup name
Setup the correct parameters in the Makefile, then run the following command:
$ make deploy
🤖 ChatOps
Setup AWS Chatbot for best experience to get notified directly on Slack.
👨💻 Credits
- :pirate_flag: AWS Security Boutique: zoph.io
- 💌 AWS Security Digest Newsletter
- :bird: Twitter: zoph