FOR EDUCATIONAL PURPOSE ONLY
Written in python3, these scripts would probably have been cleaner. Feel free to hack and improve them to your liking.
Usages:
python3 exploit-lab01.py https://xxxxxxxxxx.web-security-academy.net
python3 exploit-lab01.py https://xxxxxxxxxx.web-security-academy.net <YOUR_PAYLOAD>
python3 exploit-lab01.py https://xxxxxxxxxx.web-security-academy.net SOLUTION
python3 exploit-lab01.py https://xxxxxxxxxx.web-security-academy.net "SOLUTION1"
python3 exploit-lab01.py https://xxxxxxxxxx.web-security-academy.net 'SOLUTION2'
python3 exploit-lab01.py https://xxxxxxxxxx.web-security-academy.net $(cat <YOUR_PAYLOAD_FILE>)
python3 exploit-lab01.py <TARGET> <COLLABORATOR>
python3 exploit-lab01.py https://xxxxxxxxxx.web-security-academy.net xxxxxxxxxx.oastify.com
python3 exploit-lab01.py https://xxxxxxxxxx.web-security-academy.net xxxxxxxxxx.oastify.com SOLUTION
python3 exploit-lab01.py https://xxxxxxxxxx.web-security-academy.net xxxxxxxxxx.oastify.com $(cat <YOUR_PAYLOAD_FILE>)Categories:
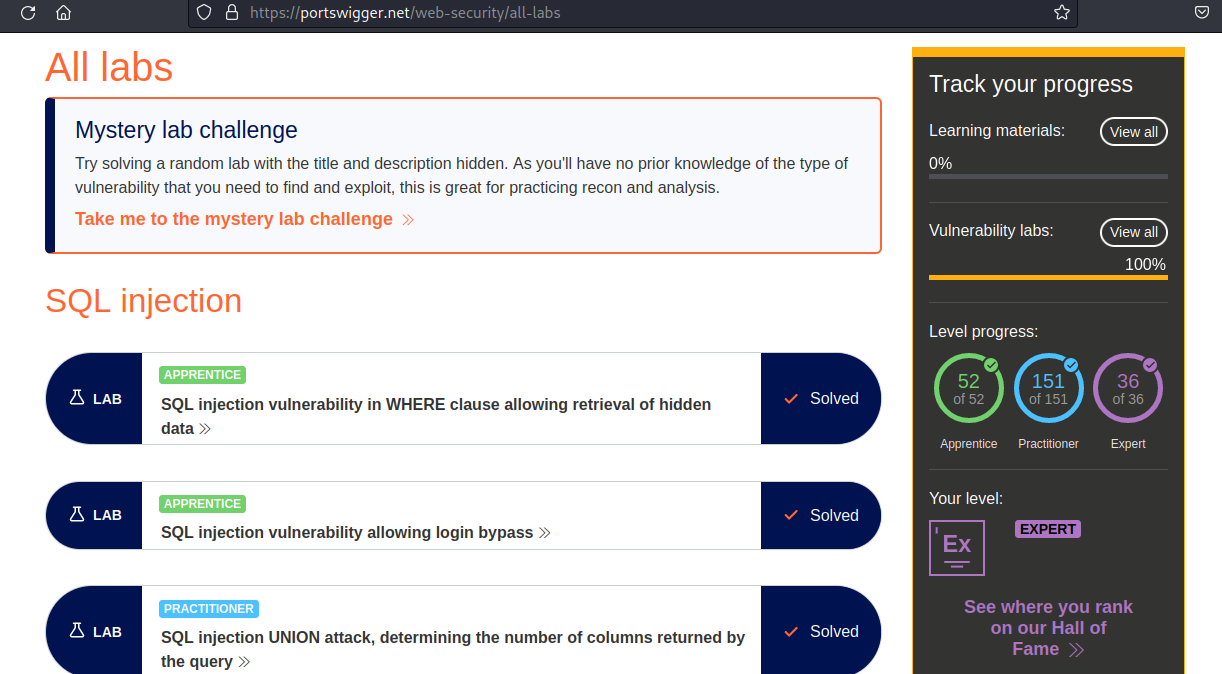
- SQL Injection: 17/17
- XSS (Cross-Site Scripting): 30/30
- CSRF (Cross-Site Request Forgery): 12/12
- ClickJacking: 5/5
- DOM-Based XSS: 7/7
- CORS (Cross-Origin Resource Sharing): 4/4
- XXE (XML External Entity injection): 9/9
- SSRF (Server-Side Request Forgery): 7/7
- HTTP Request Smuggling: 22/22
- OS Command Injection 5/5
- SSTI (Server-Side Template Injection) 7/7
- Directory Traversal 6/6
- Access Control Vulnerabilities 13/13
- Authentication 14/14
- Websockets 3/3
- Web Cache Poisoning 13/13
- Insecure Deserialization 10/10
- Information Disclosure 5/5
- Business Logic 11/11
- Host Header 7/7
- OAuth 6/6
- File Upload 7/7
- JWT (JSON Web Token) 8/8
- Essential Skills 1/2
- Prototype Pollution 10/10
- GraphQL 5/5
- NoSQL 4/4
- API testing 5/5
Lab: SQL injection vulnerability in WHERE clause allowing retrieval of hidden data
Difficulty: APPRENTICE
Lab: SQL injection vulnerability allowing login bypass
Difficulty: APPRENTICE
Lab: SQL injection UNION attack, determining the number of columns returned by the query
Difficulty: PRACTITIONER
Lab: SQL injection UNION attack, finding a column containing text
Difficulty: PRACTITIONER
Lab: SQL injection UNION attack, retrieving data from other tables
Difficulty: PRACTITIONER
Lab: SQL injection UNION attack, retrieving multiple values in a single column
Difficulty: PRACTITIONER
Lab: SQL injection attack, querying the database type and version on Oracle
Difficulty: PRACTITIONER
Lab: SQL injection attack, querying the database type and version on MySQL and Microsoft
Difficulty: PRACTITIONER
Lab: SQL injection attack, listing the database contents on non-Oracle databases
Difficulty: PRACTITIONER
Lab: SQL injection attack, listing the database contents on Oracle
Difficulty: PRACTITIONER
Lab: Blind SQL injection with conditional responses
Difficulty: PRACTITIONER
Lab: Blind SQL injection with conditional errors
Difficulty: PRACTITIONER
Lab: Visible error-based SQL injection
Difficulty: PRACTITIONER
Lab: Blind SQL injection with time delays
Difficulty: PRACTITIONER
Lab: Blind SQL injection with time delays and information retrieval
Difficulty: PRACTITIONER
Lab: Blind SQL injection with out-of-band interaction
Difficulty: PRACTITIONER
- Requires Burp Collaborator (BurpSuite Pro)
Lab: Blind SQL injection with out-of-band data exfiltration
Difficulty: PRACTITIONER
- Requires Burp Collaborator (BurpSuite Pro)
Lab: SQL injection with filter bypass via XML encoding
Difficulty: PRACTITIONER
Lab: Reflected XSS into HTML context with nothing encoded
Difficulty: APPRENTICE
Lab: Stored XSS into HTML context with nothing encoded
Difficulty: APPRENTICE
Lab: DOM XSS in document.write sink using source location.search
Difficulty: APPRENTICE
Lab: DOM XSS in innerHTML sink using source location.search
Difficulty: APPRENTICE
Lab: DOM XSS in jQuery anchor href attribute sink using location.search source
Difficulty: APPRENTICE
Lab: DOM XSS in jQuery selector sink using a hashchange event
Difficulty: APPRENTICE
Lab: Reflected XSS into attribute with angle brackets HTML-encoded
Difficulty: APPRENTICE
Lab: Stored XSS into anchor href attribute with double quotes HTML-encoded
Difficulty: APPRENTICE
Lab: Reflected XSS into a JavaScript string with angle brackets HTML encoded
Difficulty: APPRENTICE
Lab: DOM XSS in document.write sink using source location.search inside a select element
Difficulty: PRACTITIONER
Lab: DOM XSS in AngularJS expression with angle brackets and double quotes HTML-encoded
Difficulty: PRACTITIONER
Lab: Reflected DOM XSS
Difficulty: PRACTITIONER
Lab: Stored DOM XSS
Difficulty: PRACTITIONER
Lab: Exploiting cross-site scripting to steal cookies
Difficulty: PRACTITIONER
- Requires Burp Collaborator (BurpSuite Pro)
Lab: Exploiting cross-site scripting to capture passwords
Difficulty: PRACTITIONER
- Requires Burp Collaborator (BurpSuite Pro)
Lab: Exploiting XSS to perform CSRF
Difficulty: PRACTITIONER
Lab: Reflected XSS into HTML context with most tags and attributes blocked
Difficulty: PRACTITIONER
Lab: Reflected XSS into HTML context with all tags blocked except custom ones
Difficulty: PRACTITIONER
Lab: Reflected XSS with some SVG markup allowed
Difficulty: PRACTITIONER
Lab: Reflected XSS in canonical link tag
Difficulty: PRACTITIONER
Lab: Reflected XSS into a JavaScript string with single quote and backslash escaped
Difficulty: PRACTITIONER
Difficulty: PRACTITIONER
Difficulty: PRACTITIONER
Difficulty: PRACTITIONER
Lab: Reflected XSS with event handlers and href attributes blocked
Difficulty: EXPERT
Lab: Reflected XSS in a JavaScript URL with some characters blocked
Difficulty: EXPERT
Lab: Reflected XSS with AngularJS sandbox escape without strings
Difficulty: EXPERT
Lab: Reflected XSS with AngularJS sandbox escape and CSP
Difficulty: EXPERT
Lab: Reflected XSS protected by very strict CSP, with dangling markup attack
Difficulty: EXPERT
- Requires Burp Collaborator (BurpSuite Pro)
Lab: Reflected XSS protected by CSP, with CSP bypass
Difficulty: EXPERT
Lab: CSRF vulnerability with no defenses
Difficulty: APPRENTICE
Lab: CSRF where token validation depends on request method
Difficulty: PRACTITIONER
Lab: CSRF where token validation depends on token being present
Difficulty: PRACTITIONER
Lab: CSRF where token is not tied to user session
Difficulty: PRACTITIONER
Lab: CSRF where token is tied to non-session cookie
Difficulty: PRACTITIONER
Lab: CSRF where token is duplicated in cookie
Difficulty: PRACTITIONER
Lab: SameSite Lax bypass via method override
Difficulty: PRACTITIONER
Lab: SameSite Strict bypass via client-side redirect
Difficulty: PRACTITIONER
Lab: SameSite Strict bypass via sibling domain
Difficulty: PRACTITIONER
Lab: SameSite Lax bypass via cookie refresh
Difficulty: PRACTITIONER
Lab: CSRF where Referer validation depends on header being present
Difficulty: PRACTITIONER
Lab: CSRF with broken Referer validation
Difficulty: PRACTITIONER
Lab: Basic clickjacking with CSRF token protection
Difficulty: APPRENTICE
Lab: Clickjacking with form input data prefilled from a URL parameter
Difficulty: APPRENTICE
Lab: Clickjacking with a frame buster script
Difficulty: APPRENTICE
Lab: Exploiting clickjacking vulnerability to trigger DOM-based XSS
Difficulty: PRACTITIONER
Difficulty: PRACTITIONER
Lab: DOM XSS using web messages
Difficulty: PRACTITIONER
Lab: DOM XSS using web messages and a JavaScript URL
Difficulty: PRACTITIONER
Lab: DOM XSS using web messages and JSON.parse
Difficulty: PRACTITIONER
Lab: DOM-based open redirection
Difficulty: PRACTITIONER
Lab: DOM-based cookie manipulation
Difficulty: PRACTITIONER
Lab: Exploiting DOM clobbering to enable XSS
Difficulty: EXPERT
Lab: Clobbering DOM attributes to bypass HTML filters
Difficulty: EXPERT
Lab: CORS vulnerability with basic origin reflection
Difficulty: APPRENTICE
Lab: CORS vulnerability with trusted null origin
Difficulty: APPRENTICE
Lab: CORS vulnerability with trusted insecure protocols
Difficulty: PRACTITIONER
Lab: CORS vulnerability with internal network pivot attack
Difficulty: EXPERT
Lab: Exploiting XXE using external entities to retrieve files
Difficulty: APPRENTICE
Lab: Exploiting XXE to perform SSRF attacks
Difficulty: APPRENTICE
Lab: Blind XXE with out-of-band interaction
Difficulty: PRACTITIONER
Lab: Blind XXE with out-of-band interaction via XML parameter entities
Difficulty: PRACTITIONER
Lab: Exploiting blind XXE to exfiltrate data using a malicious external DTD
Difficulty: PRACTITIONER
Lab: Exploiting blind XXE to retrieve data via error messages
Difficulty: PRACTITIONER
Lab: Exploiting XInclude to retrieve files
Difficulty: PRACTITIONER
Lab: Exploiting XXE via image file upload
Difficulty: PRACTITIONER
- Requires shutil & pytesseract
python3 -m pip install pytest-shutil pytesseractLab: Exploiting XXE to retrieve data by repurposing a local DTD
Difficulty: EXPERT
Lab: Basic SSRF against the local server
Difficulty: APPRENTICE
Lab: Basic SSRF against another back-end system
Difficulty: APPRENTICE
Lab: SSRF with blacklist-based input filter
Difficulty: PRACTITIONER
Lab: SSRF with filter bypass via open redirection vulnerability
Difficulty: PRACTITIONER
Lab: Blind SSRF with out-of-band detection
Difficulty: PRACTITIONER
Lab: SSRF with whitelist-based input filter
Difficulty: EXPERT
Lab: Blind SSRF with Shellshock exploitation
Difficulty: EXPERT
- Requires Burp Collaborator (BurpSuite Pro) NOT TESTED <!>
Lab: HTTP request smuggling, basic CL.TE vulnerability
Difficulty: PRACTITIONER
Lab: HTTP request smuggling, basic TE.CL vulnerability
Difficulty: PRACTITIONER
Lab: HTTP request smuggling, obfuscating the TE header
Difficulty: PRACTITIONER
Lab: HTTP request smuggling, confirming a CL.TE vulnerability via differential responses
Difficulty: PRACTITIONER
Lab: HTTP request smuggling, confirming a TE.CL vulnerability via differential responses
Difficulty: PRACTITIONER
Lab: Exploiting HTTP request smuggling to bypass front-end security controls, CL.TE vulnerability
Difficulty: PRACTITIONER
Lab: Exploiting HTTP request smuggling to bypass front-end security controls, TE.CL vulnerability
Difficulty: PRACTITIONER
Lab: Exploiting HTTP request smuggling to reveal front-end request rewriting
Difficulty: PRACTITIONER
Lab: Exploiting HTTP request smuggling to capture other users' requests
Difficulty: PRACTITIONER
Lab: Exploiting HTTP request smuggling to deliver reflected XSS
Difficulty: PRACTITIONER
Lab: Response queue poisoning via H2.TE request smuggling
Difficulty: PRACTITIONER
Difficulty: PRACTITIONER
Lab: HTTP/2 request smuggling via CRLF injection
Difficulty: PRACTITIONER
Lab: HTTP/2 request splitting via CRLF injection
Difficulty: PRACTITIONER
Difficulty: PRACTITIONER
Lab: Exploiting HTTP request smuggling to perform web cache poisoning
Difficulty: EXPERT
Lab: Exploiting HTTP request smuggling to perform web cache deception
Difficulty: EXPERT
Lab: Bypassing access controls via HTTP/2 request tunnelling
Difficulty: EXPERT
Lab: Web cache poisoning via HTTP/2 request tunnelling
Difficulty: EXPERT
Lab: Client-side desync
Difficulty: EXPERT
Lab: Browser cache poisoning via client-side desync
Difficulty: EXPERT
Lab: Server-side pause-based request smuggling
Difficulty: EXPERT
Lab: OS command injection, simple case
Difficulty: APPRENTICE
Lab: Blind OS command injection with time delays
Difficulty: PRACTITIONER
Lab: Blind OS command injection with output redirection
Difficulty: PRACTITIONER
Lab: Blind OS command injection with out-of-band interaction
Difficulty: PRACTITIONER
Lab: Blind OS command injection with out-of-band data exfiltration
Difficulty: PRACTITIONER
- Requires Burp Collaborator (BurpSuite Pro) NOT TESTED <!>
Lab: Basic server-side template injection
Difficulty: PRACTITIONER
Lab: Basic server-side template injection (code context)
Difficulty: PRACTITIONER
Lab: Server-side template injection using documentation
Difficulty: PRACTITIONER
Lab: Server-side template injection in an unknown language with a documented exploit
Difficulty: PRACTITIONER
Lab: Server-side template injection with information disclosure via user-supplied objects
Difficulty: PRACTITIONER
Lab: Server-side template injection in a sandboxed environment
Difficulty: EXPERT
Lab: Server-side template injection with a custom exploit
Difficulty: EXPERT
Lab: File path traversal, simple case
Difficulty: APPRENTICE
Lab: File path traversal, traversal sequences blocked with absolute path bypass
Difficulty: PRACTITIONER
Lab: File path traversal, traversal sequences stripped non-recursively
Difficulty: PRACTITIONER
Lab: File path traversal, traversal sequences stripped with superfluous URL-decode
Difficulty: PRACTITIONER
Lab: File path traversal, validation of start of path
Difficulty: PRACTITIONER
Lab: File path traversal, validation of file extension with null byte bypass
Difficulty: PRACTITIONER
Lab: Unprotected admin functionality
Difficulty: APPRENTICE
Lab: Unprotected admin functionality with unpredictable URL
Difficulty: APPRENTICE
Lab: User role controlled by request parameter
Difficulty: APPRENTICE
Lab: User role can be modified in user profile
Difficulty: APPRENTICE
Lab: User ID controlled by request parameter
Difficulty: APPRENTICE
Lab: User ID controlled by request parameter, with unpredictable user IDs
Difficulty: APPRENTICE
Lab: User ID controlled by request parameter with data leakage in redirect
Difficulty: APPRENTICE
Lab: User ID controlled by request parameter with password disclosure
Difficulty: APPRENTICE
Lab: Insecure direct object references
Difficulty: APPRENTICE
Lab: URL-based access control can be circumvented
Difficulty: PRACTITIONER
Lab: Method-based access control can be circumvented
Difficulty: PRACTITIONER
Lab: Multi-step process with no access control on one step
Difficulty: PRACTITIONER
Lab: Referer-based access control
Difficulty: PRACTITIONER
Lab: Username enumeration via different responses
Difficulty: APPRENTICE
Lab: 2FA simple bypass
Difficulty: APPRENTICE
Lab: Password reset broken logic
Difficulty: APPRENTICE
Lab: Username enumeration via subtly different responses
Difficulty: PRACTITIONER
Lab: Username enumeration via response timing
Difficulty: PRACTITIONER
Lab: Broken brute-force protection, IP block
Difficulty: PRACTITIONER
Lab: Username enumeration via account lock
Difficulty: PRACTITIONER
Lab: 2FA broken logic
Difficulty: PRACTITIONER
Lab: Brute-forcing a stay-logged-in cookie
Difficulty: PRACTITIONER
Lab: Offline password cracking
Difficulty: PRACTITIONER
Lab: Password reset poisoning via middleware
Difficulty: PRACTITIONER
Lab: Password brute-force via password change
Difficulty: PRACTITIONER
Lab: Broken brute-force protection, multiple credentials per request
Difficulty: EXPERT
Lab: 2FA bypass using a brute-force attack
Difficulty: EXPERT
Lab: Manipulating WebSocket messages to exploit vulnerabilities
Difficulty: APPRENTICE
Lab: Manipulating the WebSocket handshake to exploit vulnerabilities
Difficulty: PRACTITIONER
Lab: Cross-site WebSocket hijacking
Difficulty: PRACTITIONER
Lab: Web cache poisoning with an unkeyed header
Difficulty: PRACTITIONER
Lab: Web cache poisoning with an unkeyed cookie
Difficulty: PRACTITIONER
Lab: Web cache poisoning with multiple headers
Difficulty: PRACTITIONER
Lab: Targeted web cache poisoning using an unknown header
Difficulty: PRACTITIONER
Lab: Web cache poisoning via an unkeyed query string
Difficulty: PRACTITIONER
Lab: Web cache poisoning via an unkeyed query parameter
Difficulty: PRACTITIONER
Lab: Parameter cloaking
Difficulty: PRACTITIONER
Lab: Web cache poisoning via a fat GET request
Difficulty: PRACTITIONER
Lab: URL normalization
Difficulty: PRACTITIONER
Lab: Web cache poisoning to exploit a DOM vulnerability via a cache with strict cacheability criteria
Difficulty: EXPERT
Lab: Combining web cache poisoning vulnerabilities
Difficulty: EXPERT
Lab: Cache key injection
Difficulty: EXPERT
Difficulty: EXPERT
Lab: Modifying serialized objects
Difficulty: APPRENTICE
Lab: Modifying serialized data types
Difficulty: PRACTITIONER
Lab: Using application functionality to exploit insecure deserialization
Difficulty: PRACTITIONER
Lab: Arbitrary object injection in PHP
Difficulty: PRACTITIONER
Lab: Exploiting Java deserialization with Apache Commons
Difficulty: PRACTITIONER
Lab: Exploiting PHP deserialization with a pre-built gadget chain
Difficulty: PRACTITIONER
Lab: Exploiting Ruby deserialization using a documented gadget chain
Difficulty: PRACTITIONER
Lab: Developing a custom gadget chain for Java deserialization
Difficulty: EXPERT
Lab: Developing a custom gadget chain for PHP deserialization
Difficulty: EXPERT
Lab: Using PHAR deserialization to deploy a custom gadget chain
Difficulty: EXPERT
Lab: Information disclosure in error messages
Difficulty: APPRENTICE
Lab: Information disclosure on debug page
Difficulty: APPRENTICE
Lab: Source code disclosure via backup files
Difficulty: APPRENTICE
Lab: Authentication bypass via information disclosure
Difficulty: APPRENTICE
Lab: Information disclosure in version control history
Difficulty: PRACTITIONER
Lab: Excessive trust in client-side controls
Difficulty: APPRENTICE
Lab: High-level logic vulnerability
Difficulty: APPRENTICE
Lab: High-level logic vulnerability
Difficulty: APPRENTICE
Lab: Flawed enforcement of business rules
Difficulty: APPRENTICE
Lab: Low-level logic flaw
Difficulty: PRACTITIONER
Lab: Inconsistent handling of exceptional input
Difficulty: PRACTITIONER
Lab: Weak isolation on dual-use endpoint
Difficulty: PRACTITIONER
Lab: Insufficient workflow validation
Difficulty: PRACTITIONER
Lab: Authentication bypass via flawed state machine
Difficulty: PRACTITIONER
Lab: Infinite money logic flaw
Difficulty: PRACTITIONER
Lab: Authentication bypass via encryption oracle
Difficulty: PRACTITIONER
Lab: Basic password reset poisoning
Difficulty: APPRENTICE
Lab: Host header authentication bypass
Difficulty: APPRENTICE
Lab: Web cache poisoning via ambiguous requests
Difficulty: PRACTITIONER
Lab: Routing-based SSRF
Difficulty: PRACTITIONER
Lab: SSRF via flawed request parsing
Difficulty: PRACTITIONER
Lab: Host validation bypass via connection state attack
Difficulty: PRACTITIONER
Lab: Password reset poisoning via dangling markup
Difficulty: EXPERT
Lab: Authentication bypass via OAuth implicit flow
Difficulty: APPRENTICE
Lab: Forced OAuth profile linking
Difficulty: PRACTITIONER
Lab: OAuth account hijacking via redirect_uri
Difficulty: PRACTITIONER
Lab: Stealing OAuth access tokens via an open redirect
Difficulty: PRACTITIONER
Lab: SSRF via OpenID dynamic client registration
Difficulty: PRACTITIONER
Lab: Stealing OAuth access tokens via a proxy page
Difficulty: EXPERT
Lab: Remote code execution via web shell upload
Difficulty: APPRENTICE
Lab: Web shell upload via Content-Type restriction bypass
Difficulty: APPRENTICE
Lab: Web shell upload via path traversal
Difficulty: PRACTITIONER
Lab: Web shell upload via extension blacklist bypass
Difficulty: PRACTITIONER
Lab: Web shell upload via obfuscated file extension
Difficulty: PRACTITIONER
Lab: Remote code execution via polyglot web shell upload
Difficulty: PRACTITIONER
Lab: Web shell upload via race condition
Difficulty: EXPERT
Lab: JWT authentication bypass via unverified signature
Difficulty: APPRENTICE
Lab: JWT authentication bypass via flawed signature verification
Difficulty: APPRENTICE
Lab: JWT authentication bypass via weak signing key
Difficulty: PRACTITIONER
Lab: JWT authentication bypass via jwk header injection
Difficulty: PRACTITIONER
Lab: JWT authentication bypass via jku header injection
Difficulty: PRACTITIONER
Lab: JWT authentication bypass via kid header path traversal
Difficulty: PRACTITIONER
Lab: JWT authentication bypass via algorithm confusion
Difficulty: EXPERT
Lab: JWT authentication bypass via algorithm confusion with no exposed key
Difficulty: EXPERT
Lab: Discovering vulnerabilities quickly with targeted scanning
Difficulty: PRACTITIONER
Lab: DOM XSS via client-side prototype pollution
Difficulty: PRACTITIONER
Lab: DOM XSS via an alternative prototype pollution vector
Difficulty: PRACTITIONER
Lab: Client-side prototype pollution via flawed sanitization
Difficulty: PRACTITIONER
Lab: Client-side prototype pollution in third-party libraries
Difficulty: PRACTITIONER
Lab: Client-side prototype pollution via browser APIs
Difficulty: PRACTITIONER
Lab: Privilege escalation via server-side prototype pollution
Difficulty: PRACTITIONER
Lab: Detecting server-side prototype pollution without polluted property reflection
Difficulty: PRACTITIONER
Lab: Bypassing flawed input filters for server-side prototype pollution
Difficulty: PRACTITIONER
Lab: Remote code execution via server-side prototype pollution
Difficulty: PRACTITIONER
Lab: Exfiltrating sensitive data via server-side prototype pollution
Difficulty: EXPERT
Lab: Accessing private GraphQL posts
Difficulty: APPRENTICE
Lab: Accidental exposure of private GraphQL fields
Difficulty: PRACTITIONER
Lab: Finding a hidden GraphQL endpoint
Difficulty: PRACTITIONER
Lab: Bypassing GraphQL brute force protections
Difficulty: PRACTITIONER
Lab: Performing CSRF exploits over GraphQL
Difficulty: PRACTITIONER
Lab: Detecting NoSQL injection
Difficulty: APPRENTICE
Lab: Exploiting NoSQL operator injection to bypass authentication
Difficulty: APPRENTICE
Lab: Exploiting NoSQL injection to extract data
Difficulty: PRACTITIONER
Lab: Exploiting NoSQL operator injection to extract unknown fields
Difficulty: PRACTITIONER
Lab: Exploiting an API endpoint using documentation
Difficulty: APPRENTICE
Lab: Exploiting server-side parameter pollution in a query string
Difficulty: PRACTITIONER
Lab: Finding and exploiting an unused API endpoint
Difficulty: PRACTITIONER
Lab: Exploiting a mass assignment vulnerability
Difficulty: PRACTITIONER
Lab: Exploiting server-side parameter pollution in a REST URL
Difficulty: EXPERT